- Feb 25, 2017
- 2,639
Hey guys,
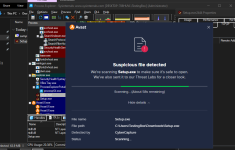
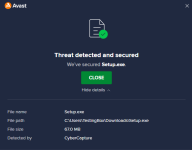
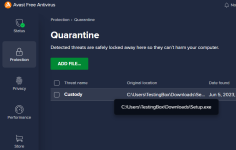
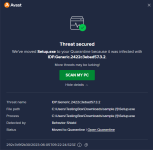
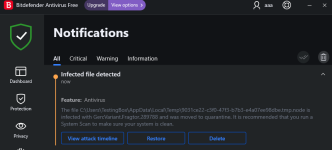
Just stumbled upon this video and thought why not checking out the file by myself. By now the malware should be at least two months old and still isn't detected by any AV on VirusTotal except ESET. Normally malicious PE files are detected easily by AI-based AV solutions and considering that it's at least 2 months old I expect it to be detected by multiple engines.
Can anyone take a closer look at it?
Triage: Triage | Malware sandboxing report by Hatching Triage
VirusTotal: VirusTotal
FileScan: FileScan.IO - Next-Gen Malware Analysis Platform