- Jun 26, 2020
- 440
Hello
I discover this application, it looks interesting, anyone has used? It's trustable?
Its look good and it's free.
Site: Suricata
I discover this application, it looks interesting, anyone has used? It's trustable?
Its look good and it's free.
Site: Suricata
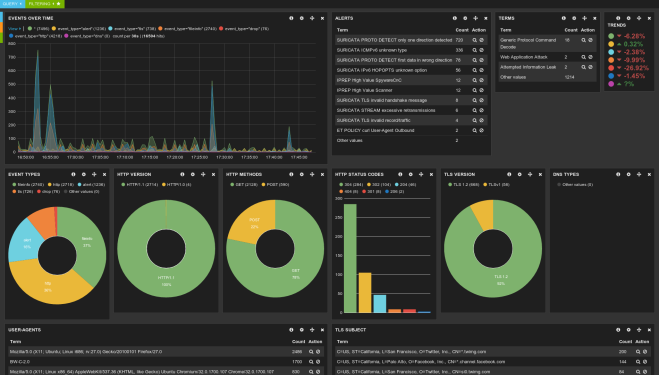
Suricata
Suricata is a free and open source, mature, fast and robust network threat detection engine.
The Suricata engine is capable of real time intrusion detection (IDS), inline intrusion prevention (IPS), network security monitoring (NSM) and offline pcap processing.
Suricata inspects the network traffic using a powerful and extensive rules and signature language, and has powerful Lua scripting support for detection of complex threats.
With standard input and output formats like YAML and JSON integrations with tools like existing SIEMs, Splunk, Logstash/Elasticsearch, Kibana, and other database become effortless.
Suricata’s fast paced community driven development focuses on security, usability and efficiency.
The Suricata project and code is owned and supported by the Open Information Security Foundation (OISF), a non-profit foundation committed to ensuring Suricata’s development and sustained success as an open source project.
Features
IDS / IPS
Suricata implements a complete signature language to match on known threats, policy violations and malicious behaviour. Suricata will also detect many anomalies in the traffic it inspects. Suricata is capable of using the specialized Emerging Threats Suricata ruleset and the VRT ruleset.
High Performance
A single Suricata instance is capable of inspecting multi-gigabit traffic. The engine is built around a multi threaded, modern, clean and highly scalable code base. There is native support for hardware acceleration from several vendors and through PF_RING and AF_PACKET.
Automatic protocol detection
Suricata will automatically detect protocols such as HTTP on any port and apply the proper detection and logging logic. This greatly helps with finding malware and CnC channels.
NSM: More than an IDS
Suricata can log HTTP requests, log and store TLS certificates, extract files from flows and store them to disk. The full pcap capture support allows easy analysis. All this makes Suricata a powerful engine for your Network Security Monitoring (NSM) ecosystem.
TLS/SSL Logging and Analysis: Not only can you match against most aspects of an SSL/TLS exchange within the ruleset laguage thanks to Suricata’s TLS Parser, you can also log all key exchanges for analysis. Great way to make sure your network is not the victim of a less than reputable certificate authority.
HTTP Logging: Why add more hardware into your network just to log http activity when your IDS already sees it? Suricata will log all HTTP connections on any port to file for later analysis.
DNS Logging: Suricata will log all DNS queries and responses.
Lua scripting
Advanced analysis and functionality available to detect things not possible within the ruleset syntax.
Industry standard outputs
Our main logging output is called “Eve”, our all JSON event and alert output. This allows for easy integration with Logstash and similar tools.


Additionally, through the Unified2 output format and the Barnyard2 tool, Suricata can be used with BASE, Snorby, Sguil, SQueRT and all other tools out there.
