When it comes to malware, untrained eyes may struggle to figure out whether a file is malicious or not. The svchost.exe virus, in particular, falls under this umbrella of ambiguity — while the virus attached to this file is obviously bad, the svchost.exe by itself is really a core Windows file.So many times we hear about svchost being a suspicious file in the Malware Reporting Forum, and there is a reason for that.
The authentic svchost.exe file is located in C:\Windows\System32, but numerous viruses and trojans use the same file and process name to hide their activities.
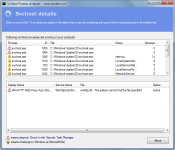
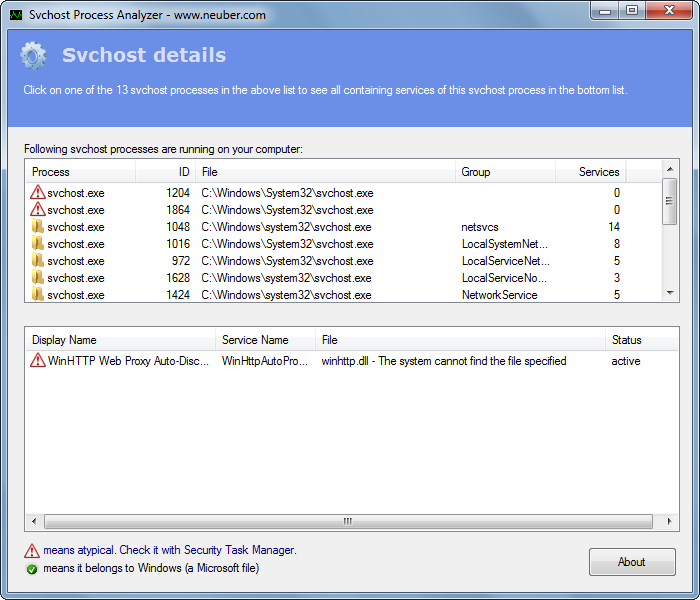
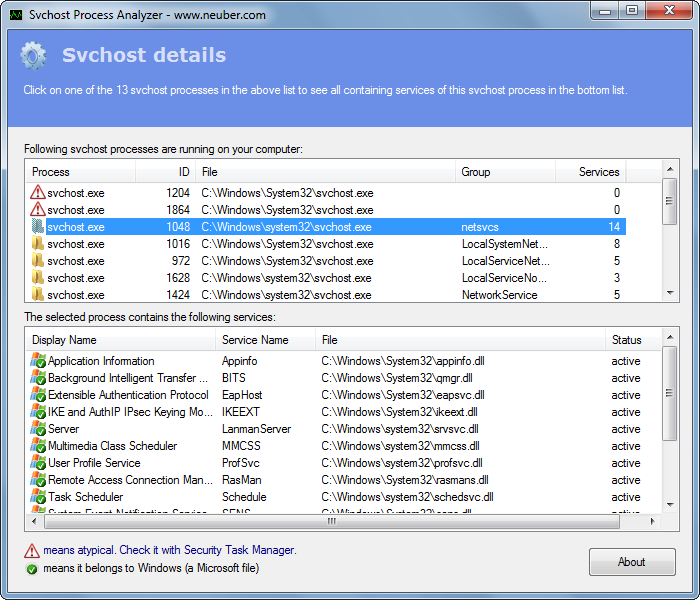
How to check svchost status quickly? The free Svchost Process Analyzer makes it easy by listing all svchost instances and checks the services they contain.This makes it easy to uncover Svchost worms like the infamous Conficker worm.

All clean
The authentic svchost.exe file is located in C:\Windows\System32, but numerous viruses and trojans use the same file and process name to hide their activities.
How to check svchost status quickly? The free Svchost Process Analyzer makes it easy by listing all svchost instances and checks the services they contain.This makes it easy to uncover Svchost worms like the infamous Conficker worm.
- 100% freeware
- doesn't require runtimes
- doesn't require installation
- doesn't write to the registry
- doesn't modify files outside of its own directories
All clean