Why the Next Botnet May Be Built From an Army of Web Browsers
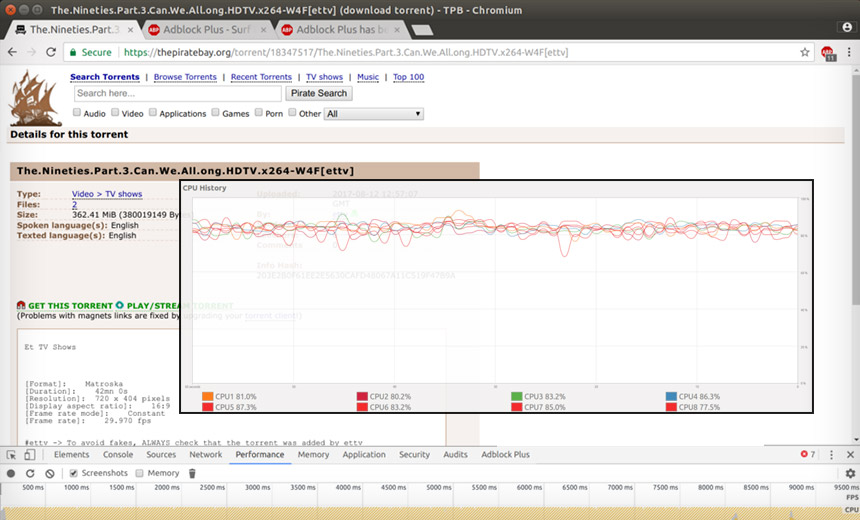
Last year, The Pirate Bay was caught using code to borrow CPU power from website visitors. (Source: Brannon Dorsey)
In September, users of The Pirate Bay, a search engine for small files called torrents that enable the downloading of content over the BitTorrent peer-to-peer network, noticed that their CPU usage spiked.
See Also: IoT is Happening Now: Are You Prepared?
It was no anomaly: As a test, The Pirate Bay had inserted code from Coinhive that borrowed computer power from users that visited their sites to mine monero cryptocurrency. The mining occurred in the background, but was noticed and rankled many, news site TorrentFreak reported.
The idea of using browsers as a botnet has been kicking around since at least 2013, when application security experts Jeremiah Grossman and Matt Johansen presented research they dubbed "Million Browser Botnet," about how a few lines of JavaScript - perhaps hidden in an online advertisement - could be used to make thousands or millions of browsers handle someone's processing needs.
Now, a new experiment shows how this type of powerful and distributed computing network could be assembled both quickly and cheaply.
Such schemes require no malware to be delivered to a computer, trigger no anti-virus alerts and would, in theory, be difficult to deflect or defend against. The resulting botnet could then be used for cracking passwords, mining cryptocurrencies or conducting distributed denial-of-service attacks.
If such schemes become common, "it could be a very nasty experience to browse the web in a few years," says Brannon Dorsey, a Chicago-based technology artist, programmer and researcher. "This is inherently the way the web works. It isn't a vulnerability per se."
Dodgy Banner Ad
Dorsey wanted to find out how much power he could harness from computers on the web, as well as how cheaply and anonymously he could do it.
Web browser security has improved tremendously over the years. But still, a web browser is an execution environment that runs code.
Rather than create a web page and try to lure people to it to run his code, Dorsey instead turned to a tried-and-true mechanism to reaching large numbers of users: a tainted advertisement. This type of technique is known as malvertising (see Online Ad Industry Threatened by Security Issues).
He bought a banner ad with a Russian advertising network with relatively loose security controls and the flexibility to upload iframe-based advertisements, which can draw on HTML, CSS and JavaScript source code.
To stay as anonymous as possible, he registered an email address with ProtonMail, a Switzerland-based email provider with a focus on privacy and security. The Russian ad network, PopUnder, also accepts the virtual currency bitcoin as payment.
The PopUnder website's homepage.
The ad industry is increasingly trying to push ad networks to scan for malicious ads, but the initiative remains a work in progress. And PopUnder is quite liberal, Dorsey says: It allows ads to be uploaded as .zip files full of HTML files, which offered opportunities for deception.
"Because you're uploading basically a zip of HTML files, you can serve an ad that is reviewed," Dorsey says "As long as you're requesting out another file, once the ad was reviewed I could just switch out what it is serving."
Browser Power
What Dorsey initially delivered was a JavaScript bot via an ad that logged IP addresses, user agent strings and visit duration.
"I was shocked at how effective it was," Dorsey says. "After like three hours there were 100,000 clients that had connected to it."
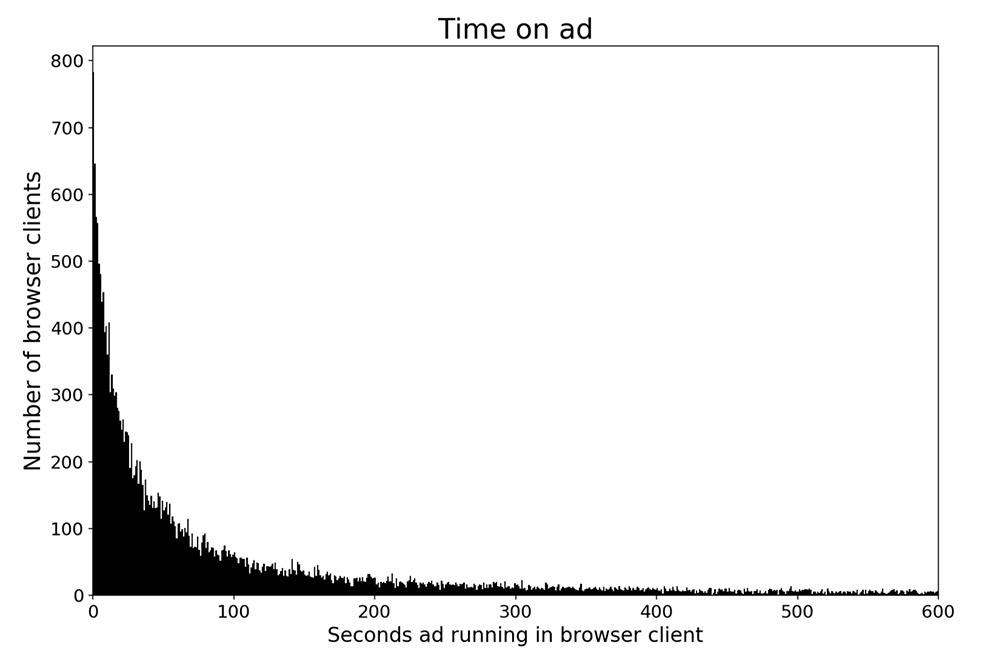
"Total time on ad was the equivalent of more than 327 days of compute," Dorsey says. "Mean time was over 15 minutes." (Source: Dorsey)
That exercise merely cost him $15 in bitcoin. In another test, Dorsey created a bot that created SHA-1 hashes for random numbers. At one point, 324 clients were connected, creating 8.5 million SHA-1 hashes per second.
While that wasn't a particularly high hash rate, "the speed of the network offered a 100 times increase from my home workstation for a nominal cost," Dorsey writes in a blog post.
Dorsey used JavaScript for some of his tests, and it's often not the most elegant or fast way to get a job done. But he predicts that attackers using WebAssembly could increase efficiency by an order of magnitude.
WebAssembly is primed to change the web: it's a binary file format that allows multiple types of programming languages to run at near-native speeds within web browsers. Of course malicious actors might put such capabilities to work too, and a test run by Dorsey using WebAssembly to create a monero miner showed how effective it can be. "For situations like this - when you're trying to harvest CPU - it can be devastatingly fast," Dorsey says.
Jerome Segura, lead malware intelligence analyst with Malwarebytes, says Dorsey's work is a "cool piece of research." But one weakness with a browser-based botnet is that a bot will go offline if someone closes a tab or the browser application.
"But browser habits are such that many people actually keep a multitude of tabs open and rarely ever completely close them all," Segura says. "And even if they tried, crooks have already found ways to keep at least some open, by cleverly hiding them."
Monitor CPU Usage
Detecting such attacks remains tricky. Most users wouldn't notice an uptick in their CPU usage, particularly if such use wasn't disruptive. Security software isn't going to set off an alarm. But Dorsey recommends that users keep an eye on their CPU usage or resource monitors, as that would be the first clue that something is amiss.
Perhaps the best defense against a rogue online advertisement that's abusing CPU power, however, is to run ad-blocking software. The online advertising industry's focus on security appears to be designed at least in part to try to keep people from using ad blockers.
Online advertisements, however, aren't the only potential attack vector. Attackers might also plant code in websites or plugins for WordPress. Other possibilities include injecting code into non-HTTPS traffic or taking advantage of cross-site scripting vulnerabilities in websites.
But there are other, more direct routes that users may be powerless to stop unless they cease using a service altogether. "If Facebook decides they're going to do this, and they're serving you code that isn't an ad network, your ad blocker isn't going to block that code," Dorsey says.