- Aug 8, 2016
- 35
A real quick and dirty look-see into the CCleaner malware:
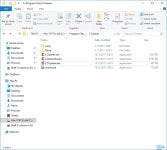
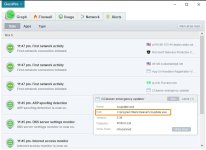
Hey! I had this on one of my machines. The CCleaner malware was actually pretty benign in what it did. It's freaking insane that somebody was actually able to get Piriform to sign infected versions of their software FROM THEIR WEBSITE, but that aside it wasn't too bad. First, the malware was only downloaded around August. I don't remember when exactly, but it was only on Piriform's site for a month or two. Also, the infected version was ccleaner.exe, but ccleaner installed ccleaner.exe AND ccleaner64.exe onto the computer-- ccleaner64 was not infected. So, on all 64-bit machines, clicking CCleaner from the Start menu or desktop would open ccleaner64.exe by default. Luckily I was one of those ones and didn't get infected. So, unless you had a 32-bit machine or deliberately went into ccleaer's ProgramFiles directory and clicked the 32-bit version, you wouldn't have been infected. And lastly, from what I have heard the attackers used the malware to collect personally identifiable information from machines, not drop payloads.