- Feb 4, 2016
- 2,520

A security researcher has identified thousands of Serial-to-Ethernet devices connected online that leak Telnet passwords that could be used to attack the equipment that is placed behind them.
The leaky devices are various Serial-to-Ethernet "device servers" manufactured by Lantronix, a California-based hardware vendor.
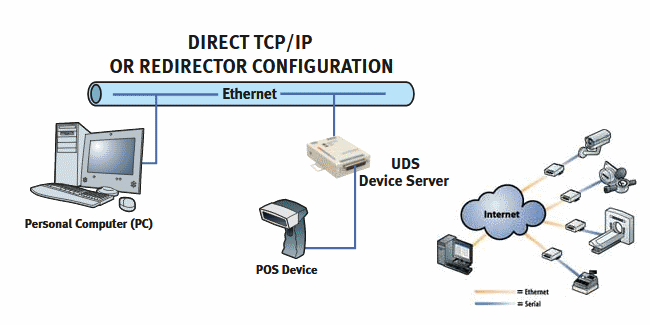
Companies buy these "device servers" and use them as a way to connect to remote equipment that only comes with serial interfaces.
Products such as Lantronix UDS or xDirect allow companies to plug an RS-XXX serial connector in one end, and an RJ-45 Ethernet connector in the other, and then manage the device via a LAN or WAN connection.
According to one product's description, "the UDS1100-IAP is a rugged and powerful tool which enables users to connect, manage and control just about any piece of industrial equipment from virtually anywhere over Ethernet or the Internet," while another product's description claims it provides "quick and easy Ethernet connectivity to virtually any device or machine with a serial interface."
The "device servers" are very popular in the ICS (Industrial Control Systems) sector, where companies use them to control old equipment that features only serial ports.
Leaky devices have not received firmware updates
"Nobody cared to fix these devices," the expert said. These can be a gateway to breach connected products."
Since the vulnerable devices act as a proxy between TCP and serial commands, an attacker that takes control over the device via Telnet can then use his privileged access to send serial commands to the connected devices.
With almost 6,500 targets to choose from, and with passwords already on Shodan, attackers only have to put in the time and find a Lantronix device server connecting to the ICS equipment of their liking.
Last edited:
