MedusaLocker is a ransomware family that has been observed being deployed since its discovery in 2019. Since its introduction to the threat landscape, there have been several variants observed. However, most of the functionality remains consistent. The most notable differences are changes to the file extension used for encrypted files and the look and feel of the ransom note that is left on systems following the encryption process. While most of MedusaLocker's functionality is consistent with other modern ransomware families, there are features that set MedusaLocker apart from many of the other ransomware families commonly observed.
MedusaLocker can also perform ICMP sweeping to identify other systems on the same network. If the malware is able to locate them, MedusaLocker then attempts to leverage the SMB protocol to discover accessible network locations and if files are discovered in those locations, they are also encrypted and ransomed in the same manner as other locally stored data.
- MedusaLocker can encrypt the contents of mapped network drives that may be present on infected systems.
- It manipulates Windows functionality to force network drives to be remapped so that their contents can also be encrypted.
- The malware uses ICMP sweeping to profile the network to identify other systems that can be used to maximize the likelihood of a ransom payment.
MedusaLocker features characteristics typical of ransomware that is commonly seen across the threat landscape. Upon execution, it copies itself to the %APPDATA%\Roaming\ directory.
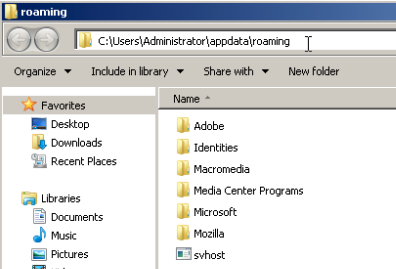
To achieve persistence, the malware creates scheduled tasks within Windows to execute the PE32 that was previously stored in %APPDATA%\Roaming.
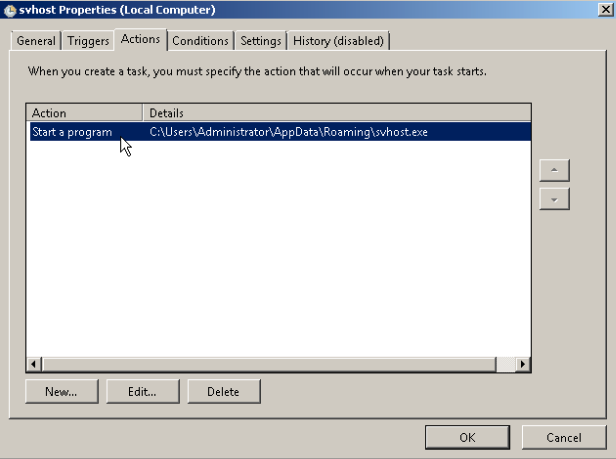
Interestingly, the scheduled task is also configured to be executed every 15 minutes after the initial infection process, likely as a way to continue to maintain the ability to impact files and other data after the initial run of the ransomware.

As previously mentioned, the malware is configured to iterate through disk partitions that may be present and accessible on the infected system and encrypting the contents.

Files that are encrypted have a new file extension appended to them. As there are several variants currently being observed across the threat landscape this file extension varies. In the case of the sample analyzed that file extension was ".encrypted."

Threat Spotlight: MedusaLocker
By Edmund Brumaghin, with contributions from Amit Raut. Overview MedusaLocker is a ransomware family that has been observed being deployed since its discovery in 2019. Since its introduction to the threat landscape, there have been several variants observed. However, most of the...
 blog.talosintelligence.com
blog.talosintelligence.com