Even if you didn’t find that USB drive at some random place, can you trust it completely?
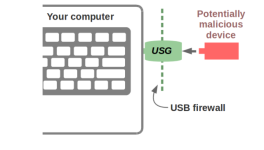
To use the said USG device (firewall for USB ports), you need to put its one end to your PC and the suspected USB device into the other. It automatically scans the USB device for BadUSB attacks, which can harm you via USB driver exploits and hidden/visible evil functionality.
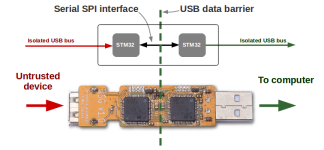
The USG uses two STM32F4 microprocessors communicating over a high-speed serial link which allows only a restricted set of commands to pass. So, a malicious host is barred from corrupting the USB drive’s firmware.
The USG supports mass storage devices, flash drives, keyboard, and mice. In future updates, you can expect to see some extra devices. Talking about the speed, USG Version 1 uses 12Mbps hardware, so the storage transfer should run around 1MBytes per second.
You should note that the USG protects you from low-level USB attacks, but it can’t save you from viruses stored in the drive’s file system. Also, it wasn’t designed to resist physical voltage overload attacks. So, it doesn’t claim to protect you fully from the USB Killer.
Can this be a worthy tool for the privacy-oriented people who are habitual of adding extra layers of security?
To use the said USG device (firewall for USB ports), you need to put its one end to your PC and the suspected USB device into the other. It automatically scans the USB device for BadUSB attacks, which can harm you via USB driver exploits and hidden/visible evil functionality.

The USG uses two STM32F4 microprocessors communicating over a high-speed serial link which allows only a restricted set of commands to pass. So, a malicious host is barred from corrupting the USB drive’s firmware.
The USG supports mass storage devices, flash drives, keyboard, and mice. In future updates, you can expect to see some extra devices. Talking about the speed, USG Version 1 uses 12Mbps hardware, so the storage transfer should run around 1MBytes per second.
You should note that the USG protects you from low-level USB attacks, but it can’t save you from viruses stored in the drive’s file system. Also, it wasn’t designed to resist physical voltage overload attacks. So, it doesn’t claim to protect you fully from the USB Killer.
Can this be a worthy tool for the privacy-oriented people who are habitual of adding extra layers of security?