Trojan BCMiner
- Thread starter LandonH
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Ok,looks like Combofix got the hard-core part of this infection......
NEXT,please follow the below steps:
STEP 1: Run a HitmanPro scan
<ol>
<li><>Download the latest official version of HitmanPro</>.
<a href="http://www.surfright.nl/en/hitmanpro/" rel="nofollow" target="_blank"> <>HITMANPRO DOWNLOAD LINK</></a> <em>(This link will open a download page in a new window from where you can download HitmanPro)</em></li>
<li>Start HitmanPro by <>double clicking on the previously downloaded file.</> and then following the prompts.
<img src="http://malwaretips.com/images/removalguide/hpro4.png" alt="[Image: hitmanproscan4.png]" border="0" /></li>
<li>Once the scan is complete, a screen displaying all the malicious files that the program found will be shown as seen in the image below.After reviewing each malicious object click <>Next</> .
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/02/rsz_hpro5.png" alt="[Image: hitmanproscan5.png]" border="0" /></li>
<li>Click <>Activate free license</> to start the free 30 days trial and remove the malicious files.
<img src="http://malwaretips.com/images/removalguide/hpro6.png" alt="[Image: hitmanproscan6.png]" border="0" /></li>
<li>HitmanPro will now start removing the infected objects, and in some instances, may suggest a reboot in order to completely remove the malware from your system. In this scenario, always confirm the reboot action to be on the safe side.
</ol>
Add to your next reply, any log that HitmanPro might generate.
<hr />
STEP 2: Run a scan with Kaspersky TDSSKiller
<ol>
<li>Please <>download</> the latest official version of Kaspersky TDSSKiller and then double click on it to start this utility.
<a href="http://support.kaspersky.com/downloads/utils/tdsskiller.exe" rel="nofollow" target="_blank"><>KASPERSKY TDSSKILLER DOWNLOAD LINK</></a> <em>(This link will automatically download Kaspersky TDSSKiller on your computer.)</em></li>
<li>Kaspersky TDSSKiller will now start and display the welcome screen as shown below.In order to start a system scan , <>press the 'Start Scan' button</>.
<img title="Start a Kaspersky TDSSKiller scan" src="http://malwaretips.com/images/removalguide/tdsskiller2.png" alt="Start a Kaspersky scan" width="367" height="337" border="0" /></li>
<li>Kaspersky TDSSKiller will now scan your computer for rootkits.
<img title="" src="http://malwaretips.com/images/removalguide/tdsskiller3.png" alt="Kaspersky TDSSKiller scanning" width="367" height="337" border="0" /></li>
<li>When the scan has finished it will display a result screen stating whether or not the infection was found on your computer. If it was found it will display a screen similar to the one below.
<img title="Kaspersky TDSKiller scan results" src="http://malwaretips.com/images/removalguide/tdsskiller4.png" alt="Kaspersky TDSSKiller results" width="450" height="349" border="0" /></li>
<li>To remove the infection simply click on the <>Continue</> button and TDSSKiller will attempt to clean the infection.A reboot might be require to completely remove this rootkit from your system.</li>
<li>Whether an infection is found or not, a log file should have already been created on your C: drive (or whatever drive you boot from) in the root folder named something like TDSSKiller.2.1.1_27.12.2009_14.17.04_log.txt which is based on the program version # and date and time run.Please add this log in your next reply.</li>
</ol>
<hr />
STEP 3: Run a scan with RogueKiller
<ol>
<li>Please <>download the latest official version of </><>RogueKiller</>.
<a href="http://www.sur-la-toile.com/RogueKiller/RogueKiller.exe" rel="nofollow" target="_blank">RogueKiller Download Link</a> <em>(This link will automatically download RogueKiller on your computer)</em></li>
<li><>Double click on RogueKiller.exe</> to start this utility and then <>wait for the Prescan to complete</>.This should take only a few seconds and then you can <>click the Start button</> to perform a system scan.
<img title="Click on the Start button to perform a system scan" src="http://malwaretips.com/blogs/wp-content/uploads/2012/04/roguek-1.png" alt="[Image: roguekiller-1.png]" width="600" height="450" border="0" /></li>
<li>After the scan has completed, <>press the Delete button</> to remove any malicious registry keys.
<img title="Press Delete to remove the malicious registry keys" src="http://malwaretips.com/blogs/wp-content/uploads/2012/04/roguek-2.png" alt="[Image: roguekiller-2.png]" width="600" height="450" border="0" /></li>
<li>Next we will need to restore your shortcuts, <>so click on the ShortcutsFix button </>and allow the program to run.
<img title="Click on the Start button to perform a system scan" src="http://malwaretips.com/blogs/wp-content/uploads/2012/04/roguek-3.png" alt="[Image: roguekiller-1.png]" width="600" height="450" border="0" /></li>
</ol>
The report has been created on the desktop.In your next reply please post:
All RKreport.txt text files located on your desktop.
<hr />
STEP 4: Run a scan with ESET Online Scanner
<ol>
<li>Download ESET Online Scanner utility.
<><a title="External link" href="http://download.eset.com/special/eos/esetsmartinstaller_enu.exe" rel="nofollow">ESET Online Scanner Download Link</a></> <em>(This link will automatically download ESET Online Scanner on your computer.)</em></li>
<li>Double click on the Eset installer program (esetsmartinstaller_enu.exe).</li>
<li>Check <>Yes, I accept the Terms of Use</></li>
<li>Click the <>Start</> button.</li>
<li>Check <>Scan archives</></li>
<li>Push the <>Start</> button.</li>
<li>ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.</li>
<li>When the scan completes, push <>List of found threats</></li>
<li>Push <>Export to Text file </> and save the file to your desktop using a unique name, such as <>ESET Scan</>. Include the contents of this report in your next reply.Note - when ESET doesn't find any threats, no report will be created.</li>
<li>Push the <>back</> button.</li>
<li>Push <>Finish</></li>
</ol>
<hr />
STEP 5: Reset Internet Explorer to default settings
<ol>
<li>Open Internet Explorer '<>Internet Options</>
<>For Internet Explorer 9</> : Click on the <>gear icon </> <img src="http://malwaretips.com/images/removalguide/icongear.jpg" alt="[Image: icongear.jpg]" border="0" /> at the top (far right) and click again on <>Internet Options</>
<img src="http://malwaretips.com/images/removalguide/ie9.png" alt="[Image: restoreie.png]" border="0" /></li>
<li>Now in the Internet Options dialog box, click on the <>Advanced</> tab, click <>Reset</>
<img src="http://malwaretips.com/images/removalguide/ine1.png" alt="[Image: restoreie2.png]" border="0" /></li>
<li>In the Reset Internet Explorer settings section. Click <>Reset</> again in the information dialog box.
<img src="http://malwaretips.com/images/removalguide/ine2.png" alt="[Image: restoreie1.png]" border="0" /></li>
<li>When Internet Explorer finishes resetting, click<> Close</> in the confirmation dialogue box and then click <>OK</>.</li>
<li><>Close and open Internet Explorer</> again.</li>
</ol>
<hr />
STEP 6: Run Temp File Cleaner by OldTimer
<ol>
<li>You can download the TFC utility from the below link
<a title="External link" href="http://oldtimer.geekstogo.com/TFC.exe" rel="nofollow external"><>TFC DOWNLOAD LINK</></a> <em>(This link will automatically download Temp File Cleaner on your computer)</em></li>
<li>Please double-click <>TFC.exe</> to run it. (<>Note:</> If you are running on Vista or 7, right-click on the file and choose <>Run As Administrator</>).</li>
<li>It <>will close all programs</> when run, so make sure you have <>saved all your work</> before you begin.</li>
<li>Click the <>Start</> button to begin the process. Depending on how often you clean temp files, execution time should be anywhere from a few seconds to a minute or two. <>Let it run uninterrupted to completion</>.</li>
<li>Once it's finished it should <>reboot your machine</>. If it does not, please <>manually reboot the machine</> yourself to ensure a complete clean.</li>
</ol>
<hr />
What's next?
Attach the following logs to your post (You can find here details on how to use the Attachment System):
1.HitmanPro logs
2.Kaspersky TDSSKiller log
3.RogueKiller logs
4.ESET log
5.Let me know if you had any problems with the above instructions and also let me know how things are running now!
NEXT,please follow the below steps:
STEP 1: Run a HitmanPro scan
<ol>
<li><>Download the latest official version of HitmanPro</>.
<a href="http://www.surfright.nl/en/hitmanpro/" rel="nofollow" target="_blank"> <>HITMANPRO DOWNLOAD LINK</></a> <em>(This link will open a download page in a new window from where you can download HitmanPro)</em></li>
<li>Start HitmanPro by <>double clicking on the previously downloaded file.</> and then following the prompts.
<img src="http://malwaretips.com/images/removalguide/hpro4.png" alt="[Image: hitmanproscan4.png]" border="0" /></li>
<li>Once the scan is complete, a screen displaying all the malicious files that the program found will be shown as seen in the image below.After reviewing each malicious object click <>Next</> .
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/02/rsz_hpro5.png" alt="[Image: hitmanproscan5.png]" border="0" /></li>
<li>Click <>Activate free license</> to start the free 30 days trial and remove the malicious files.
<img src="http://malwaretips.com/images/removalguide/hpro6.png" alt="[Image: hitmanproscan6.png]" border="0" /></li>
<li>HitmanPro will now start removing the infected objects, and in some instances, may suggest a reboot in order to completely remove the malware from your system. In this scenario, always confirm the reboot action to be on the safe side.
</ol>
Add to your next reply, any log that HitmanPro might generate.
<hr />
STEP 2: Run a scan with Kaspersky TDSSKiller
<ol>
<li>Please <>download</> the latest official version of Kaspersky TDSSKiller and then double click on it to start this utility.
<a href="http://support.kaspersky.com/downloads/utils/tdsskiller.exe" rel="nofollow" target="_blank"><>KASPERSKY TDSSKILLER DOWNLOAD LINK</></a> <em>(This link will automatically download Kaspersky TDSSKiller on your computer.)</em></li>
<li>Kaspersky TDSSKiller will now start and display the welcome screen as shown below.In order to start a system scan , <>press the 'Start Scan' button</>.
<img title="Start a Kaspersky TDSSKiller scan" src="http://malwaretips.com/images/removalguide/tdsskiller2.png" alt="Start a Kaspersky scan" width="367" height="337" border="0" /></li>
<li>Kaspersky TDSSKiller will now scan your computer for rootkits.
<img title="" src="http://malwaretips.com/images/removalguide/tdsskiller3.png" alt="Kaspersky TDSSKiller scanning" width="367" height="337" border="0" /></li>
<li>When the scan has finished it will display a result screen stating whether or not the infection was found on your computer. If it was found it will display a screen similar to the one below.
<img title="Kaspersky TDSKiller scan results" src="http://malwaretips.com/images/removalguide/tdsskiller4.png" alt="Kaspersky TDSSKiller results" width="450" height="349" border="0" /></li>
<li>To remove the infection simply click on the <>Continue</> button and TDSSKiller will attempt to clean the infection.A reboot might be require to completely remove this rootkit from your system.</li>
<li>Whether an infection is found or not, a log file should have already been created on your C: drive (or whatever drive you boot from) in the root folder named something like TDSSKiller.2.1.1_27.12.2009_14.17.04_log.txt which is based on the program version # and date and time run.Please add this log in your next reply.</li>
</ol>
<hr />
STEP 3: Run a scan with RogueKiller
<ol>
<li>Please <>download the latest official version of </><>RogueKiller</>.
<a href="http://www.sur-la-toile.com/RogueKiller/RogueKiller.exe" rel="nofollow" target="_blank">RogueKiller Download Link</a> <em>(This link will automatically download RogueKiller on your computer)</em></li>
<li><>Double click on RogueKiller.exe</> to start this utility and then <>wait for the Prescan to complete</>.This should take only a few seconds and then you can <>click the Start button</> to perform a system scan.
<img title="Click on the Start button to perform a system scan" src="http://malwaretips.com/blogs/wp-content/uploads/2012/04/roguek-1.png" alt="[Image: roguekiller-1.png]" width="600" height="450" border="0" /></li>
<li>After the scan has completed, <>press the Delete button</> to remove any malicious registry keys.
<img title="Press Delete to remove the malicious registry keys" src="http://malwaretips.com/blogs/wp-content/uploads/2012/04/roguek-2.png" alt="[Image: roguekiller-2.png]" width="600" height="450" border="0" /></li>
<li>Next we will need to restore your shortcuts, <>so click on the ShortcutsFix button </>and allow the program to run.
<img title="Click on the Start button to perform a system scan" src="http://malwaretips.com/blogs/wp-content/uploads/2012/04/roguek-3.png" alt="[Image: roguekiller-1.png]" width="600" height="450" border="0" /></li>
</ol>
The report has been created on the desktop.In your next reply please post:
All RKreport.txt text files located on your desktop.
<hr />
STEP 4: Run a scan with ESET Online Scanner
<ol>
<li>Download ESET Online Scanner utility.
<><a title="External link" href="http://download.eset.com/special/eos/esetsmartinstaller_enu.exe" rel="nofollow">ESET Online Scanner Download Link</a></> <em>(This link will automatically download ESET Online Scanner on your computer.)</em></li>
<li>Double click on the Eset installer program (esetsmartinstaller_enu.exe).</li>
<li>Check <>Yes, I accept the Terms of Use</></li>
<li>Click the <>Start</> button.</li>
<li>Check <>Scan archives</></li>
<li>Push the <>Start</> button.</li>
<li>ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.</li>
<li>When the scan completes, push <>List of found threats</></li>
<li>Push <>Export to Text file </> and save the file to your desktop using a unique name, such as <>ESET Scan</>. Include the contents of this report in your next reply.Note - when ESET doesn't find any threats, no report will be created.</li>
<li>Push the <>back</> button.</li>
<li>Push <>Finish</></li>
</ol>
<hr />
STEP 5: Reset Internet Explorer to default settings
<ol>
<li>Open Internet Explorer '<>Internet Options</>
<>For Internet Explorer 9</> : Click on the <>gear icon </> <img src="http://malwaretips.com/images/removalguide/icongear.jpg" alt="[Image: icongear.jpg]" border="0" /> at the top (far right) and click again on <>Internet Options</>
<img src="http://malwaretips.com/images/removalguide/ie9.png" alt="[Image: restoreie.png]" border="0" /></li>
<li>Now in the Internet Options dialog box, click on the <>Advanced</> tab, click <>Reset</>
<img src="http://malwaretips.com/images/removalguide/ine1.png" alt="[Image: restoreie2.png]" border="0" /></li>
<li>In the Reset Internet Explorer settings section. Click <>Reset</> again in the information dialog box.
<img src="http://malwaretips.com/images/removalguide/ine2.png" alt="[Image: restoreie1.png]" border="0" /></li>
<li>When Internet Explorer finishes resetting, click<> Close</> in the confirmation dialogue box and then click <>OK</>.</li>
<li><>Close and open Internet Explorer</> again.</li>
</ol>
<hr />
STEP 6: Run Temp File Cleaner by OldTimer
<ol>
<li>You can download the TFC utility from the below link
<a title="External link" href="http://oldtimer.geekstogo.com/TFC.exe" rel="nofollow external"><>TFC DOWNLOAD LINK</></a> <em>(This link will automatically download Temp File Cleaner on your computer)</em></li>
<li>Please double-click <>TFC.exe</> to run it. (<>Note:</> If you are running on Vista or 7, right-click on the file and choose <>Run As Administrator</>).</li>
<li>It <>will close all programs</> when run, so make sure you have <>saved all your work</> before you begin.</li>
<li>Click the <>Start</> button to begin the process. Depending on how often you clean temp files, execution time should be anywhere from a few seconds to a minute or two. <>Let it run uninterrupted to completion</>.</li>
<li>Once it's finished it should <>reboot your machine</>. If it does not, please <>manually reboot the machine</> yourself to ensure a complete clean.</li>
</ol>
<hr />
What's next?
Attach the following logs to your post (You can find here details on how to use the Attachment System):
1.HitmanPro logs
2.Kaspersky TDSSKiller log
3.RogueKiller logs
4.ESET log
5.Let me know if you had any problems with the above instructions and also let me know how things are running now!
Last edited:
Jack,
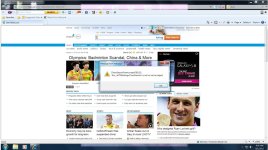
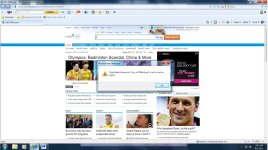
Thank you for the assistance. The requested reports are attached. There is also a screen shot of a message generating when first opening IE. IE works once those are closed.
Kaspersky did not find anything, hence the lack of a report.
Thank you for the assistance. The requested reports are attached. There is also a screen shot of a message generating when first opening IE. IE works once those are closed.
Kaspersky did not find anything, hence the lack of a report.
Attachments
Can you please run this file from Microsoft: http://support.microsoft.com/mats/ie_performance_and_safety/en-us
Can you please go to the Add or Remove Programs feature and remove the Yahoo Toolbar and see if this will fix your problem.
You may also like...
-
-
'Klopatra' Trojan Makes Bank Transfers While You Sleep
- Started by Brownie2019
- Replies: 1
-
Malware News Trojanized ESET Installers Drop Kalambur Backdoor in Phishing Attacks on Ukraine
- Started by Khushal
- Replies: 18
-
Astaroth banking trojan use GitHub Images to stay active after takedowns
- Started by Brownie2019
- Replies: 1