L
LabZero
Thread author
MD5: 08aebd590a43b2906ba678860c2b7f4c
SHA1: 16e216d541165313bd2ddf5e77a2079bd94588e3
SHA256: e9ca3f54aa5ccc3d97503435da2cc5dfb26f4c68623c3970a20fa9e86cd8d4f1
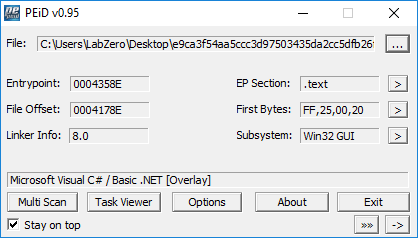
Firstly I used PEiD for identify the malware, it is a .NET file, and the linker version is 8.0.
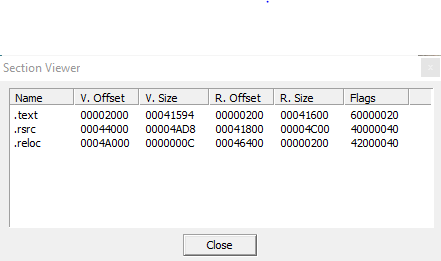
File sections:
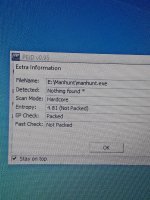
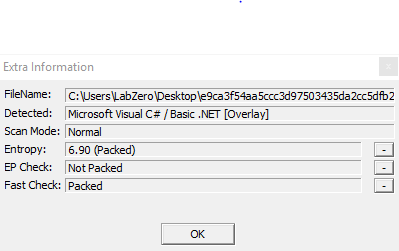
The entropy is clearly packed, as you can see in the screenshot below, that it shows also that the fast check give "packed".
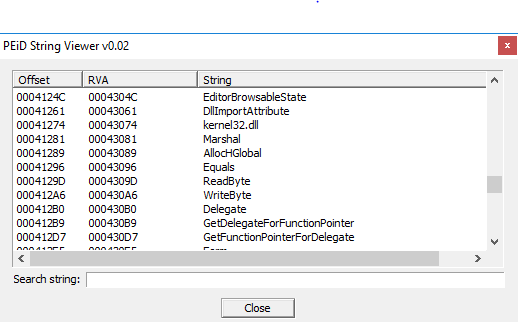
With PEiD you can see the strings inside the portable executable, in this screenshot there are the strings, that I flagged as malicious; in particular "kernel32.dll", infact in one of the functions of the code there is a -dll import- of this .dll file.
This is suspicious because with the use of kernel32.dll there could be a low level and deep infection on the OS.
Another suspicious string that I found while the analysis was "Marhsal", and this was present also in the code, used by some functions. Marshaling is the act of taking data from the environment you are in and exporting it to another environment. In the context of .NET, marhsaling refers to moving data outside of the app-domain you are in, somewhere else.
In the malware there are also strings referred to bytes operations, like "WriteByte" and "ReadByte", these operations can be intrusive and dangerous, especially because this PE works on low level (for kernel import).
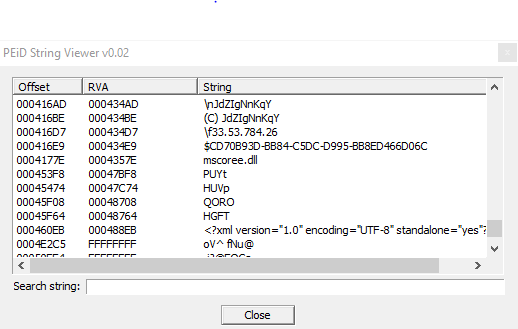
The malware uses mscoree.dll and there are in addition some strings clearly encrypted/obfuscated, as you can see in this screenshot:
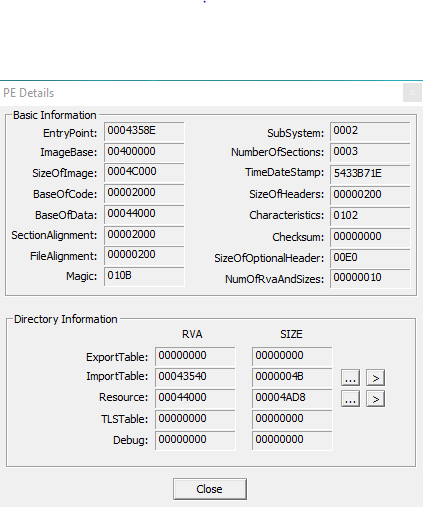
Here below are the PE details:
...but the most interesting part of this analysis is this :
:
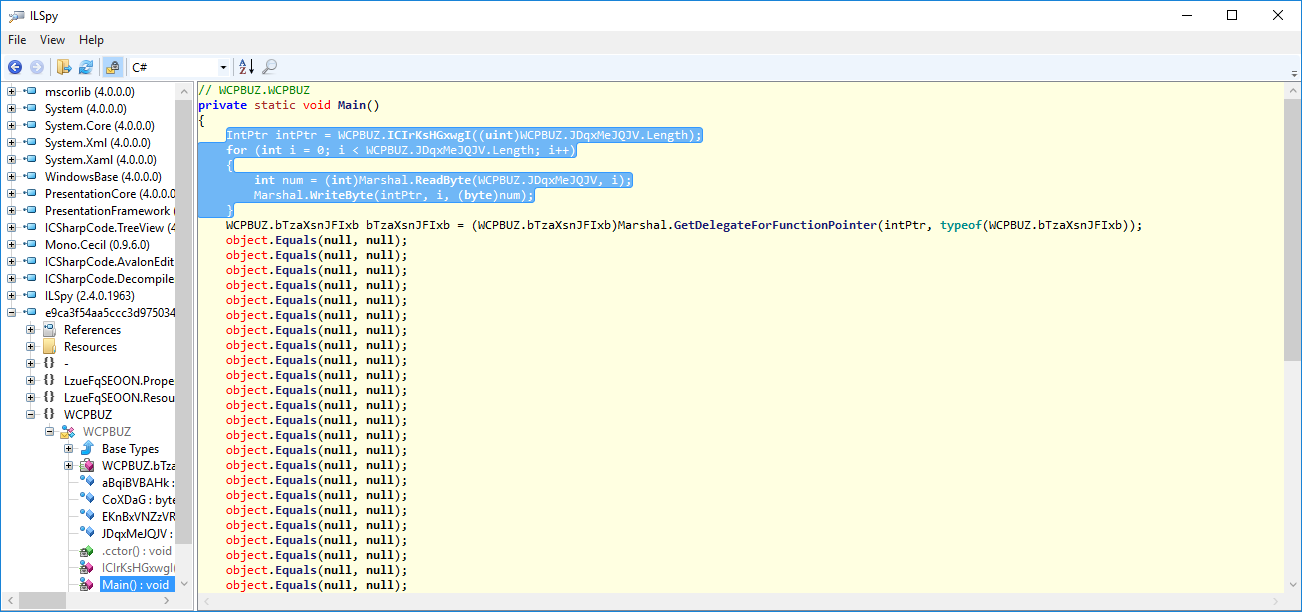
The malware uses this function, which the name is obfuscated, to marshaling bytes read from another function; this operation is done in a loop, and it means that the malware operates on all bytes got from the function called before the loop.
A repeated code line in the source is "object.Equals(null,null);", this command is for verify the equality of two objects, but in this case the objects passed as parametres are null.
Marhsal is used also on a function, which is called in the code line below.
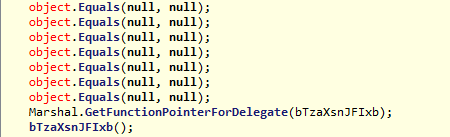
In this screenshot you can see the [DllImport] of kernel32.dll
And it is initialized a variable called VirtualProtect, which is static and external, and it is used also in another function, look that it returns an output of type uint (unsigned integer)
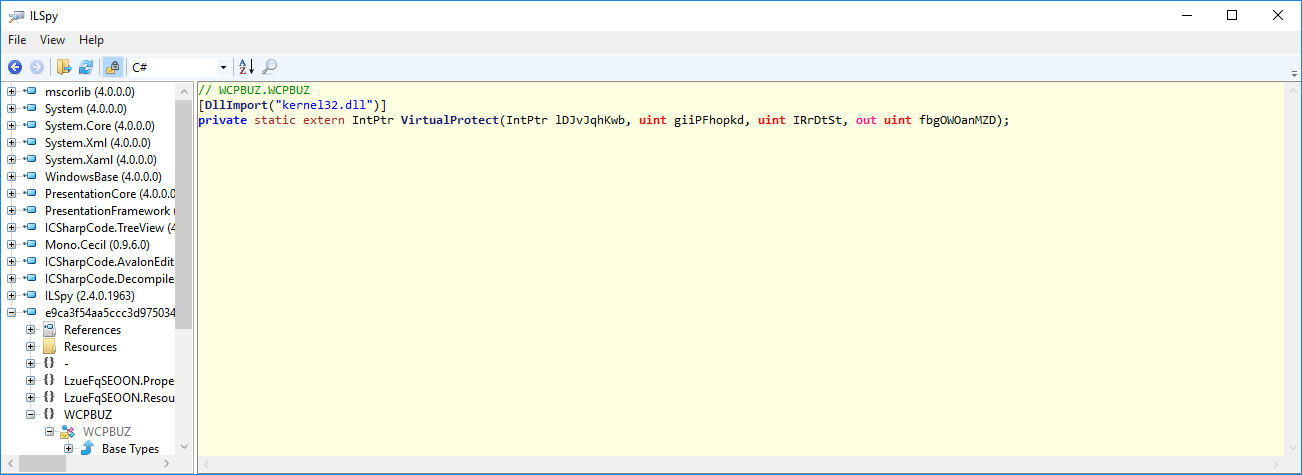
Below is the usage of the variable called "VirtualProtect".
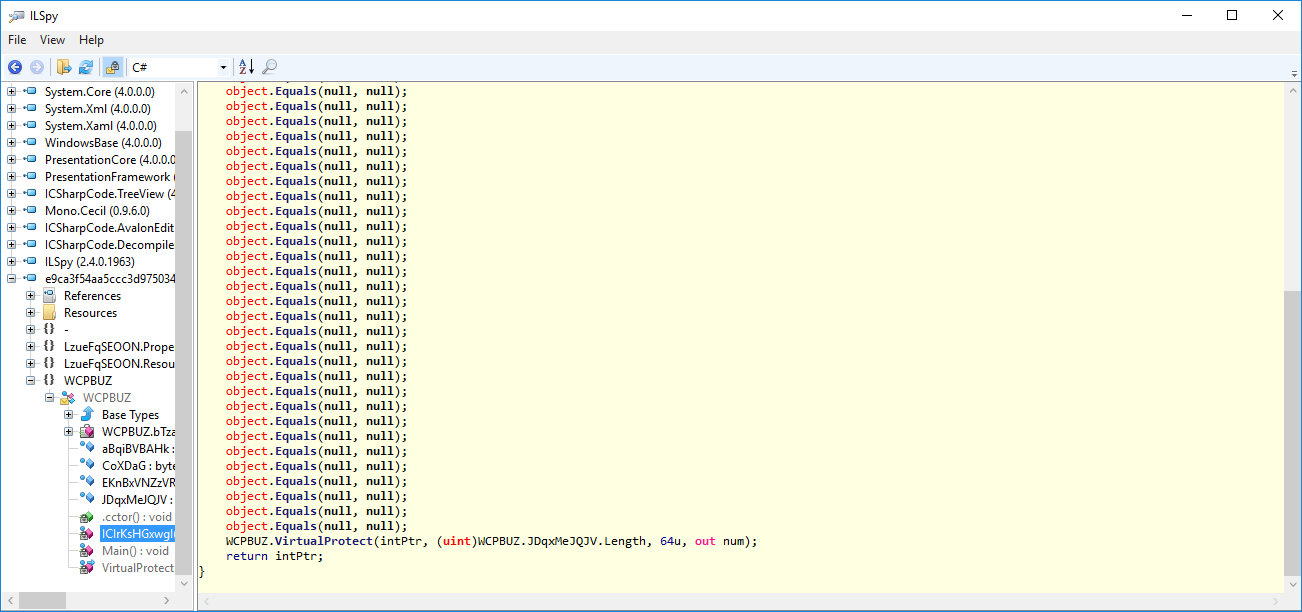
Look especially at the return function and that the VirtualProtect output; so the output of VirtualProtect is returned by this function.
Here below is another function, that uses another time Marshal feature; in particular the function "AllocHGlobal", which takes as parameter the length of an attribute variable.
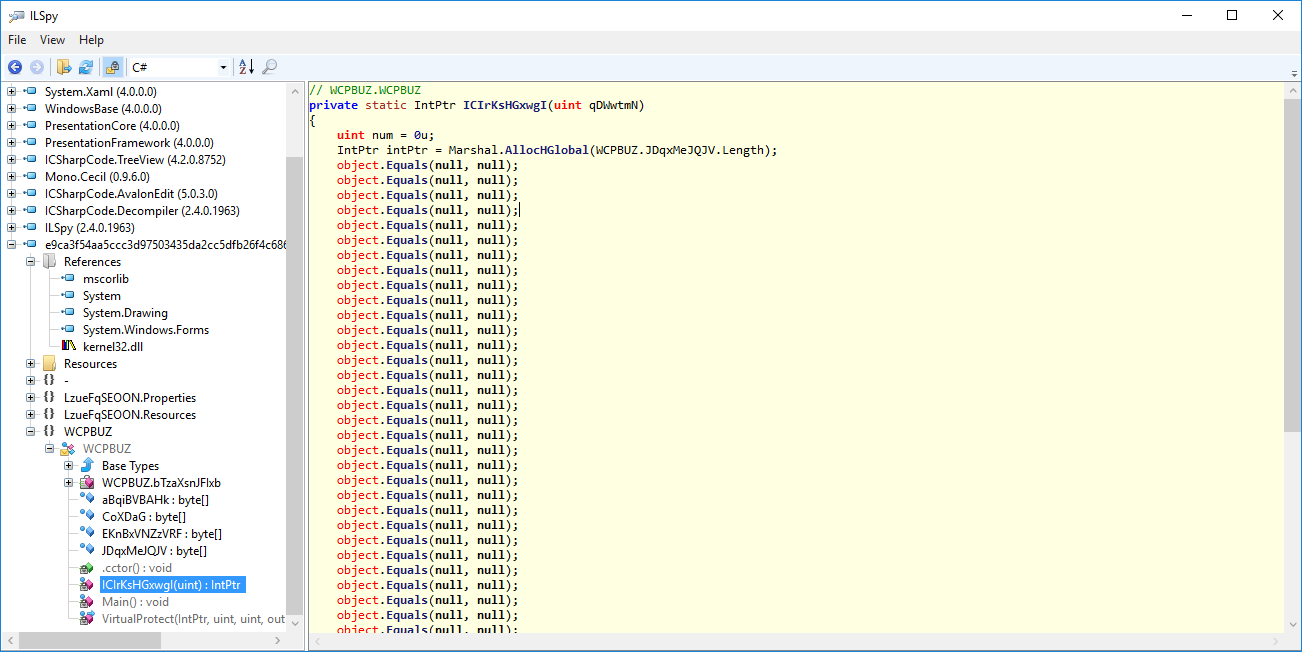
The malware initializes also some byte arrays, this is one of them:
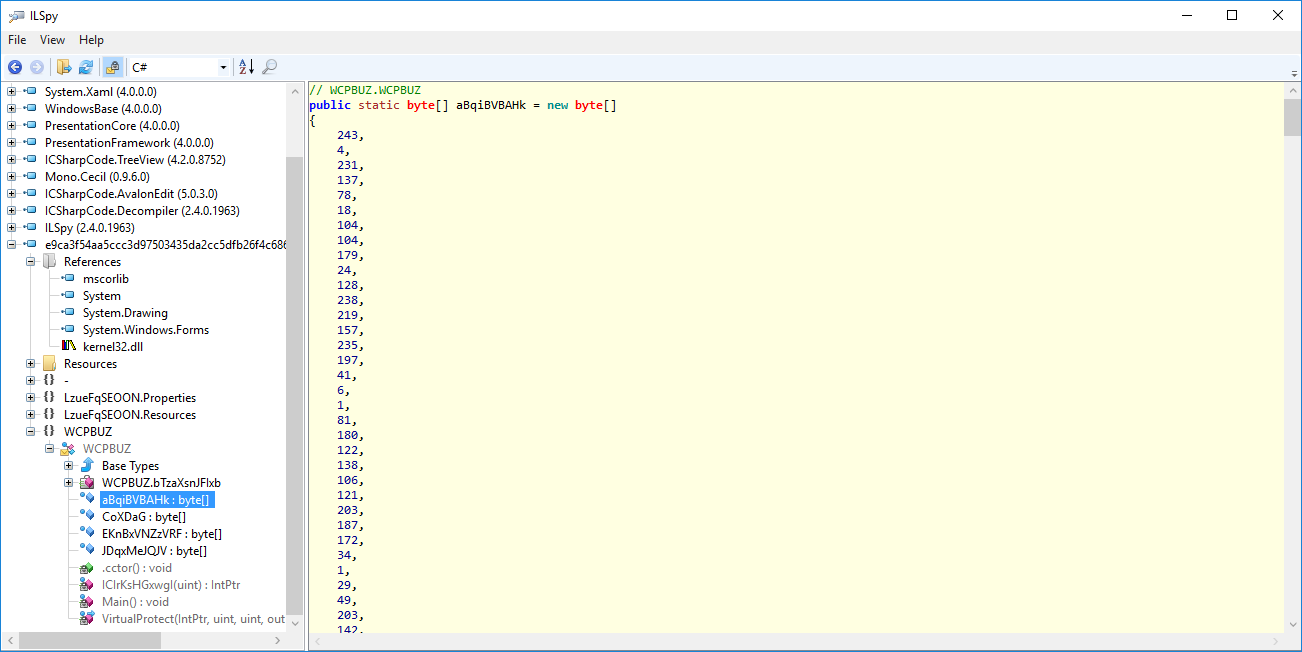
The other arrays contains lots of elements(bytes), used for write/read bytes operations.
Malware references:
SHA1: 16e216d541165313bd2ddf5e77a2079bd94588e3
SHA256: e9ca3f54aa5ccc3d97503435da2cc5dfb26f4c68623c3970a20fa9e86cd8d4f1
Firstly I used PEiD for identify the malware, it is a .NET file, and the linker version is 8.0.
File sections:
The entropy is clearly packed, as you can see in the screenshot below, that it shows also that the fast check give "packed".
With PEiD you can see the strings inside the portable executable, in this screenshot there are the strings, that I flagged as malicious; in particular "kernel32.dll", infact in one of the functions of the code there is a -dll import- of this .dll file.
This is suspicious because with the use of kernel32.dll there could be a low level and deep infection on the OS.
Another suspicious string that I found while the analysis was "Marhsal", and this was present also in the code, used by some functions. Marshaling is the act of taking data from the environment you are in and exporting it to another environment. In the context of .NET, marhsaling refers to moving data outside of the app-domain you are in, somewhere else.
In the malware there are also strings referred to bytes operations, like "WriteByte" and "ReadByte", these operations can be intrusive and dangerous, especially because this PE works on low level (for kernel import).
The malware uses mscoree.dll and there are in addition some strings clearly encrypted/obfuscated, as you can see in this screenshot:
Here below are the PE details:
...but the most interesting part of this analysis is this
The malware uses this function, which the name is obfuscated, to marshaling bytes read from another function; this operation is done in a loop, and it means that the malware operates on all bytes got from the function called before the loop.
A repeated code line in the source is "object.Equals(null,null);", this command is for verify the equality of two objects, but in this case the objects passed as parametres are null.
Marhsal is used also on a function, which is called in the code line below.
In this screenshot you can see the [DllImport] of kernel32.dll
And it is initialized a variable called VirtualProtect, which is static and external, and it is used also in another function, look that it returns an output of type uint (unsigned integer)
Below is the usage of the variable called "VirtualProtect".
Look especially at the return function and that the VirtualProtect output; so the output of VirtualProtect is returned by this function.
Here below is another function, that uses another time Marshal feature; in particular the function "AllocHGlobal", which takes as parameter the length of an attribute variable.
The malware initializes also some byte arrays, this is one of them:
The other arrays contains lots of elements(bytes), used for write/read bytes operations.
Malware references:
Last edited by a moderator: