The sample is written in C++, since it is very difficult to gather the original source code, in this analysis I used PEiD to perform an initial inspection of the PE (but above all a string analysis) and Snowman to perform a simple code analysis (but not the real original source code of the sample).
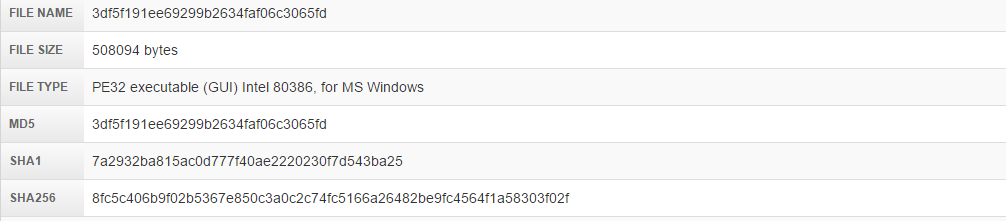
We can assume that it has 5 file sections: .text, .rdata, .data, .555, .rsrc, as we can see in the analysis of Malwr.com
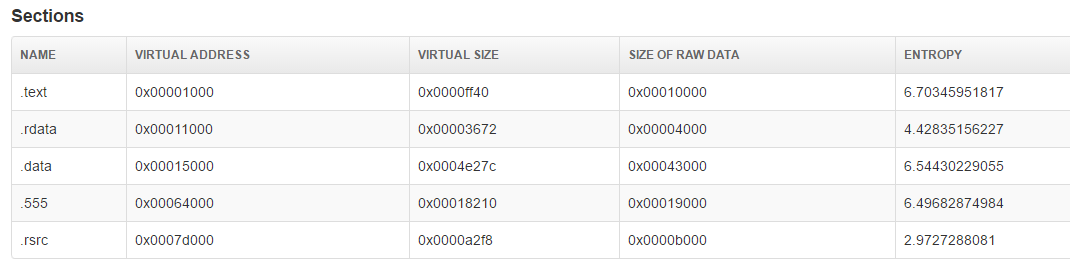
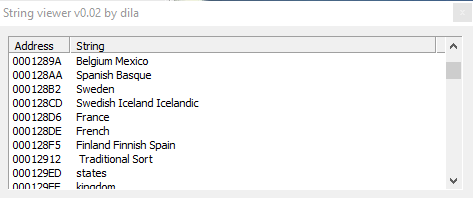
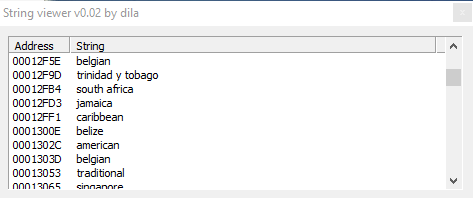
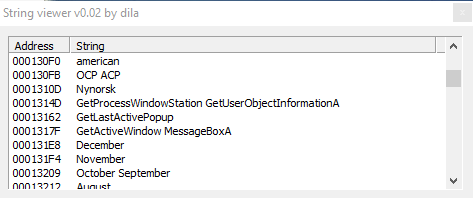
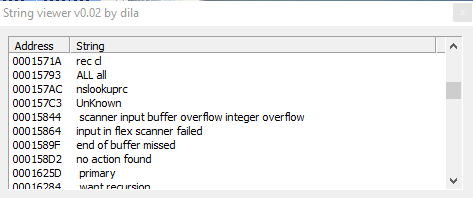
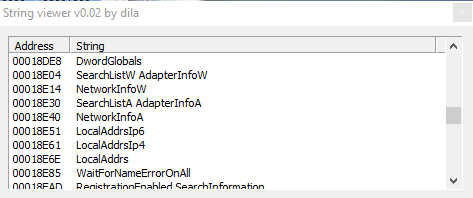
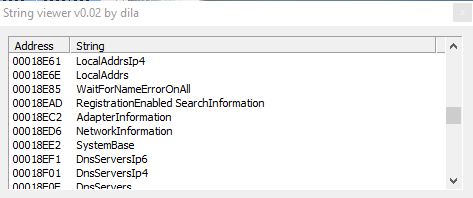
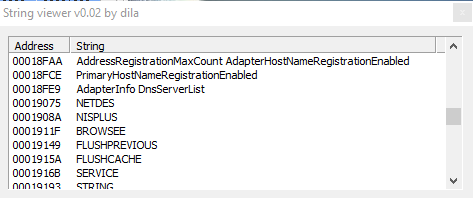
These 3 screenshots show us the malware uses strange strings related to various geographical areas.
In the third image we can assume that the sample perform a GetProcessWindowStation, but once again, stranger strings are strings related to months, such as "December", "November", "October September".
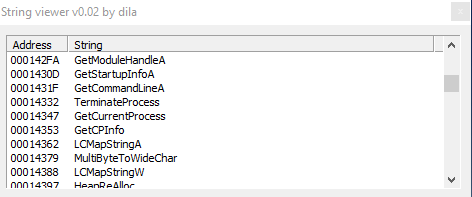
In the following screenshots we can assume the malware performs a lot of operations related to processes, such as "GetCurrentProcess", "TerminateProcess", but also "GetCpInfo", which is used to gather info about avalaible code pages, and another interesting malicious string: "GetCommandLineA", that can compromise the security of your application. Another function used by the sample is "MultiByteToWideChar", calling this method can cause a buffer overrun because the size of the input buffer is the same of the number of bytes in the string, and the size of the output buffer is the same of the number of characters.
Then "HeapReAlloc", which reallocates a block of memory from a heap. This method allows you to resize a memory block and change other memory block properties.
Also "QueryPerformanceCounter", which is able to obtain the current value of the clock of the CPU, it is probably used to check the presence of a virtual environment (VM).
Others interesting strings are "GetCurrentThreadId", GetCurrentProcessId", but also GetSystemTimeAsFileName", used to gather the time of the system and save it to a file.
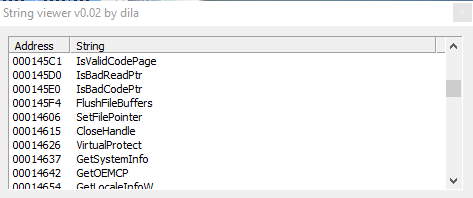
But also "HeapDestroy" and "HeapCreate"; and "VirtualQuery", that gets info about pages in the virtual address space of the calling process.

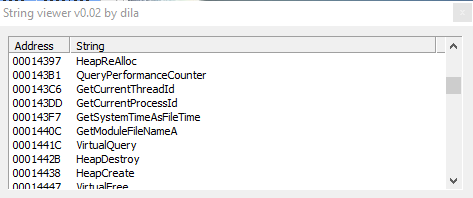
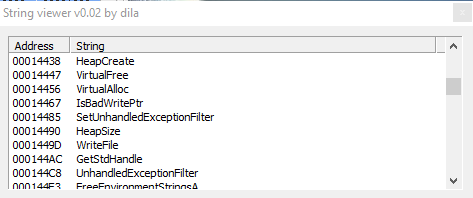
Then, in then following screenshots we have "VirtualFree", "VirtualAlloc", "HeapSize",etc. to manage info about heap, and virtual address space of the calling process.
It also uses "WriteFile" probably to save info in a persistent way.
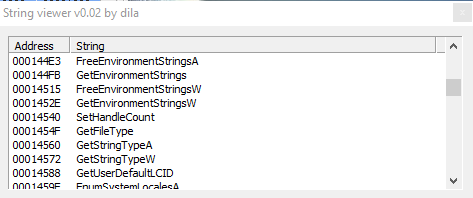
The sample gets environment variables from the current process via specific functions, for example: "GetEnvironmentStrings", then "GetFileType" and "GetUserDefaultLCID", which gives the locale identifier for the user default locale.
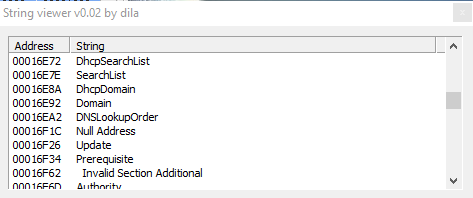
Other interesting strings are "GetSystemInfo", but also "nslookuprc", and obviously "server", "write", "connect", "socket","DNSSEC", "MD5 internal type for both IP4 ad IPv6 Addresses"; so clearly functions realted to the connection to the remote server, to establish a connection and create a socket, probably to send also sensitive and important info about the system gathered to already mentioned functions.
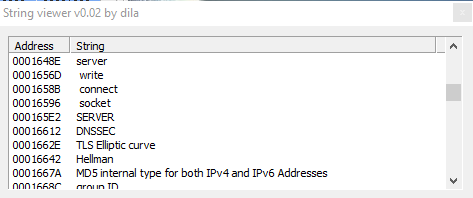
Then we have also "WINS reverse lookup info", "WINS lookup info", "Service location", "SRV IPv6 Address", and also "Geographic position GPOS", then other references to the connection: "IPv6 address", "route through", "X25 address x25 database server AFSDB", and also, probably, functions used by the malware to steal info about mailbox of the infected victim: "mailbox information MINFO", "mail forwarder", "mail destination", "mail rename MR", "mail group member", "mailbox MB", "host information".
Other connection related strings are: "name server NS", "Server failed", "No response server", etc.
But also strings (methods) related to database connection and operations: "select", "connect", "failed", "write failed", "read failed connect failed".
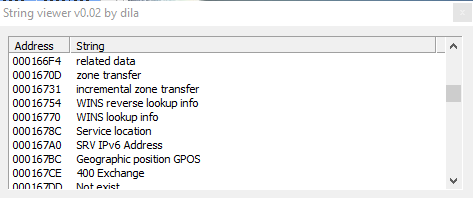
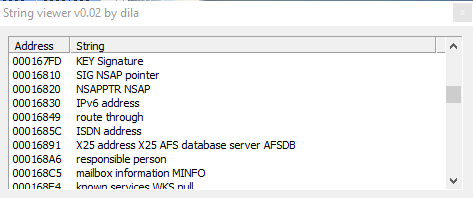
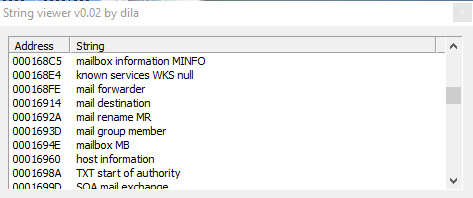
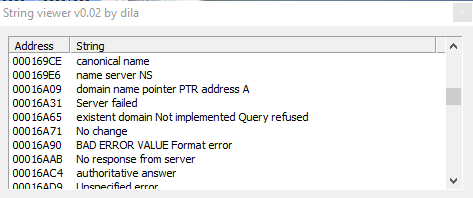
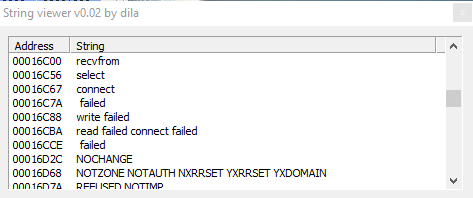
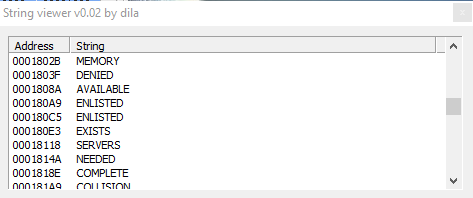
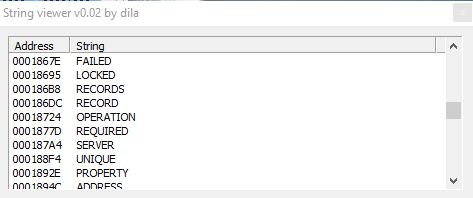
Further more we have strings referred to DHCP, and DNS lookup; and strings like "LOCKED", "ARGUMENTS", "PARAMETRES", "MEMORY", "DENIED", "AVALAIBLE", "ENLISTED" "EXISTS", "SERVERS", "OPERATION", "REQUIRED", "SERVER", "ADDRESS", and then also info about network of the infected host: "SearchListW AdapterInfoW", "NetworkInfoA", etc. and info about DNS.

Now, let's see some code retrieved with Snowman.
In the following scr
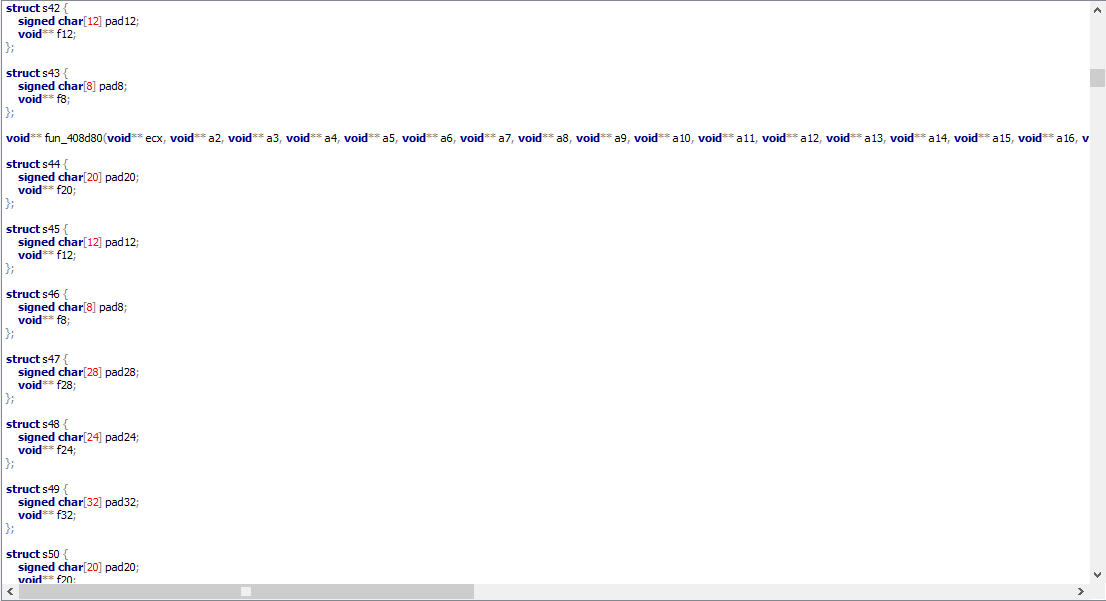
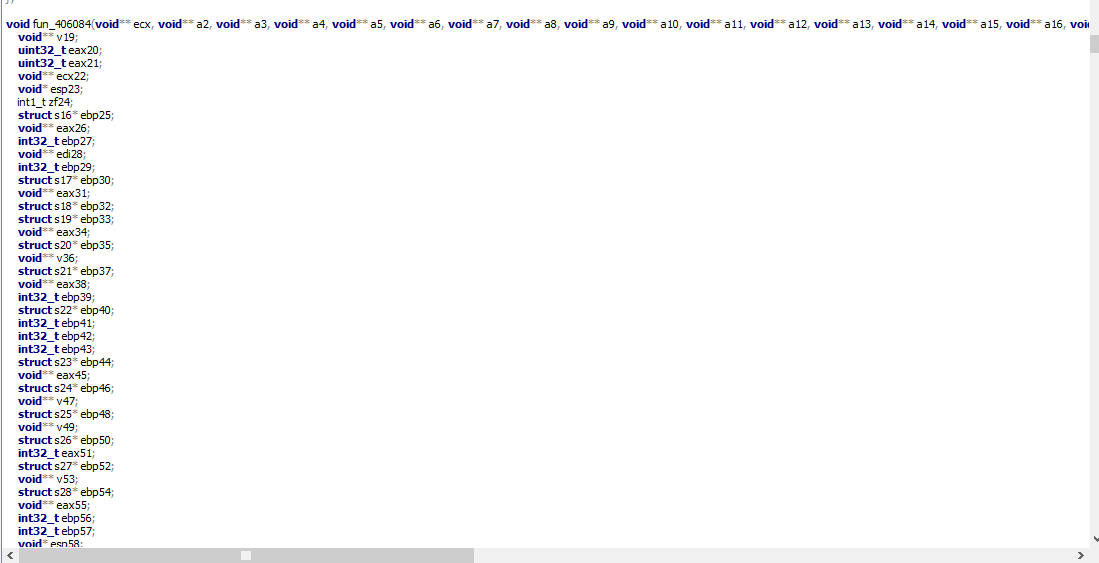
you can see the sample initializes a lot of functions and it passes many void** pointers, but also a lot of structs of type char, perhaps to log also pressed keys.
In this screenshot, instead,
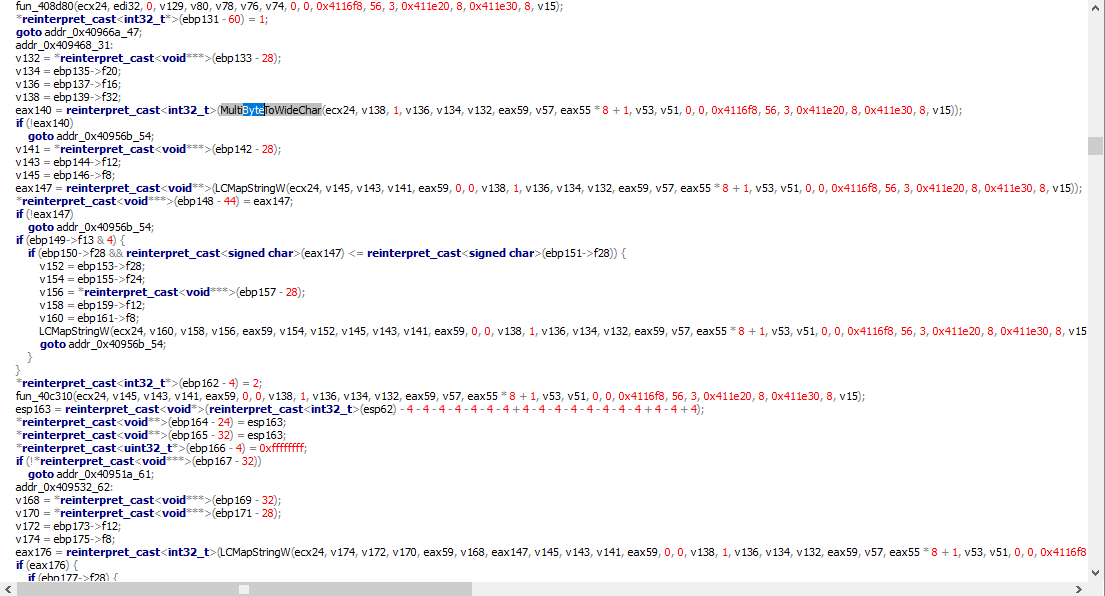
you can see that the sample calls "MultiByteToWideChar" and it uses the returned result to set the value of a variable ("eax140").
There are many functions initialized with a lot of void** pointers as parametres.
Finally, in this scr:
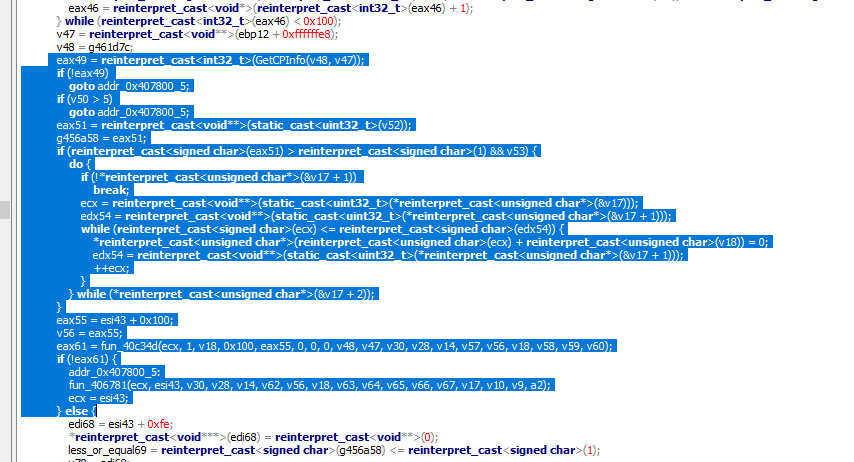
you can see how the malware calls GetCPInfo method (which has also two parametres (one of the two is a void** pointer), and, then, it performs some if conditions to go to a specific part of the code if the conditions are verified.
There are a lot of "*reinterpret_cast" calls, and others functions called.
CONCLUSION:
From the detections by AVs we can see that the sample is detected as ransomware Cerber (Zerber), but from the analysis done I can say it performs a lot of connection operations, also to a database (installed on a remote server). So, in conclusion it is certainly a ransomware because from the behaviour detections and signatures is identified as the same, but it also gets info and send them remotely, so it has, in addition, a similar behaviour as BackDoors, etc.
Thank you and Merry Xmas!
We can assume that it has 5 file sections: .text, .rdata, .data, .555, .rsrc, as we can see in the analysis of Malwr.com
These 3 screenshots show us the malware uses strange strings related to various geographical areas.
In the third image we can assume that the sample perform a GetProcessWindowStation, but once again, stranger strings are strings related to months, such as "December", "November", "October September".
In the following screenshots we can assume the malware performs a lot of operations related to processes, such as "GetCurrentProcess", "TerminateProcess", but also "GetCpInfo", which is used to gather info about avalaible code pages, and another interesting malicious string: "GetCommandLineA", that can compromise the security of your application. Another function used by the sample is "MultiByteToWideChar", calling this method can cause a buffer overrun because the size of the input buffer is the same of the number of bytes in the string, and the size of the output buffer is the same of the number of characters.
Then "HeapReAlloc", which reallocates a block of memory from a heap. This method allows you to resize a memory block and change other memory block properties.
Also "QueryPerformanceCounter", which is able to obtain the current value of the clock of the CPU, it is probably used to check the presence of a virtual environment (VM).
Others interesting strings are "GetCurrentThreadId", GetCurrentProcessId", but also GetSystemTimeAsFileName", used to gather the time of the system and save it to a file.
But also "HeapDestroy" and "HeapCreate"; and "VirtualQuery", that gets info about pages in the virtual address space of the calling process.
Then, in then following screenshots we have "VirtualFree", "VirtualAlloc", "HeapSize",etc. to manage info about heap, and virtual address space of the calling process.
It also uses "WriteFile" probably to save info in a persistent way.
The sample gets environment variables from the current process via specific functions, for example: "GetEnvironmentStrings", then "GetFileType" and "GetUserDefaultLCID", which gives the locale identifier for the user default locale.
Other interesting strings are "GetSystemInfo", but also "nslookuprc", and obviously "server", "write", "connect", "socket","DNSSEC", "MD5 internal type for both IP4 ad IPv6 Addresses"; so clearly functions realted to the connection to the remote server, to establish a connection and create a socket, probably to send also sensitive and important info about the system gathered to already mentioned functions.
Then we have also "WINS reverse lookup info", "WINS lookup info", "Service location", "SRV IPv6 Address", and also "Geographic position GPOS", then other references to the connection: "IPv6 address", "route through", "X25 address x25 database server AFSDB", and also, probably, functions used by the malware to steal info about mailbox of the infected victim: "mailbox information MINFO", "mail forwarder", "mail destination", "mail rename MR", "mail group member", "mailbox MB", "host information".
Other connection related strings are: "name server NS", "Server failed", "No response server", etc.
But also strings (methods) related to database connection and operations: "select", "connect", "failed", "write failed", "read failed connect failed".
Further more we have strings referred to DHCP, and DNS lookup; and strings like "LOCKED", "ARGUMENTS", "PARAMETRES", "MEMORY", "DENIED", "AVALAIBLE", "ENLISTED" "EXISTS", "SERVERS", "OPERATION", "REQUIRED", "SERVER", "ADDRESS", and then also info about network of the infected host: "SearchListW AdapterInfoW", "NetworkInfoA", etc. and info about DNS.
Now, let's see some code retrieved with Snowman.
In the following scr
you can see the sample initializes a lot of functions and it passes many void** pointers, but also a lot of structs of type char, perhaps to log also pressed keys.
In this screenshot, instead,
you can see that the sample calls "MultiByteToWideChar" and it uses the returned result to set the value of a variable ("eax140").
There are many functions initialized with a lot of void** pointers as parametres.
Finally, in this scr:
you can see how the malware calls GetCPInfo method (which has also two parametres (one of the two is a void** pointer), and, then, it performs some if conditions to go to a specific part of the code if the conditions are verified.
There are a lot of "*reinterpret_cast" calls, and others functions called.
CONCLUSION:
From the detections by AVs we can see that the sample is detected as ransomware Cerber (Zerber), but from the analysis done I can say it performs a lot of connection operations, also to a database (installed on a remote server). So, in conclusion it is certainly a ransomware because from the behaviour detections and signatures is identified as the same, but it also gets info and send them remotely, so it has, in addition, a similar behaviour as BackDoors, etc.
Thank you and Merry Xmas!