- Apr 28, 2015
- 9,397
- 1
- 84,816
- 8,389
That is great. You will not find anybody coming to this thread and praising Comodo. I would not be surprised if the response was "The detection by Comodo is a bug. Not a feature."View attachment 286847
Detected by VirusScope as Generic.Trojan.C@1@1
Analysis taking too long system infected is at least partially failed if not failed at the ksn part and total results was partial damage to the machine , lost of some settings ,filesYes, it was, since the analysis took very long, field Fist Seen, some hours ago was showing 13:43 or so, when I just upload it, some minutes later this thread was created.
Only people who use comodo like me will praise it when it somehow works at detection XDThat is great. You will not find anybody coming to this thread and praising Comodo. I would not be surprised if the response was "The detection by Comodo is a bug. Not a feature."
With the rise of AI, threat actors can use those to build the base code, and their job is to debug. They can use any language. Using this method is not new. It has been used for a long time. The difference now is the convenience of rapid build using AI.Not just that new gaming engine languages and even rust to some extent
I don't want to derail this thread, but that is Melih's point:Only people who use comodo like me will praise it when it somehow works at detection XD
But at prevention it can stop most malware (that's why I use it )
You can nowadays code undetected malware without even knowing to codeWith the rise of AI, threat actors can use those to build the base code, and their job is to debug. They can use any language. Using this method is not new. It has been used for a long time. The difference now is the convenience of rapid build using AI.
Change the hahs and try againHere comes the detection! Not as fast as Kaspersky, but still pretty good.
View attachment 286866
It hasn't come to VT yet.
Blocked too in checkpoint but when I change the hash it bypassed it againHere comes the detection! Not as fast as Kaspersky, but still pretty good.
View attachment 286866
It hasn't come to VT yet.
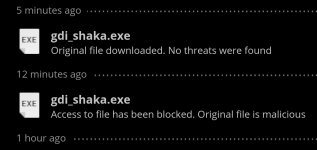
Changing the hash and it's clean againBlocked too in checkpoint but when I change the hash it bypassed it again View attachment 286867
Try changing the hash and be amazed by it being undetected again XD

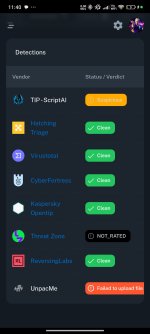
Opentip didn't detect it with a changed hash so if a hash change is enough then it's awfulYes, it was 1st upload to OPENTIP, since the analysis took very long, field Fist Seen, some hours ago was showing 13:43 or so, when I just upload it, some minutes later this thread was created.
Its detected by VirusScope(Static and dynamic behavioral analysis)Changing the hash and it's clean again

Kaspersky Threat Intelligence Portal
Kaspersky Threat Intelligence Portal allows you to scan files, domains, IP addresses, and URLs for threats, malware, virusesopentip.kaspersky.com
Comodo didn't detect it too (sent to human analysis so it might get detected by the time you're reading this)
View attachment 286868
Cloud Verdict Customer Login | Xcitium Cloud Verdict
Sign in to your Comodo Valkyrie account to access your account and use the File analysis system. Not registered,Create an account here.verdict.xcitium.com
No its not a bug i tested it again and again VirusScope detected it as Generic.Trojan.C@1@1That is great. You will not find anybody coming to this thread and praising Comodo. I would not be surprised if the response was "The detection by Comodo is a bug. Not a feature."
can you test after changing the hashNo its not a bug i tested it again and again VirusScope detected it as Generic.Trojan.C@1@1
Open the exe in notepad and add something in the end of the file. After changing the hash then recheck.you mean the name?