Self-Made Fortran Malware Analysis
- Thread starter HydraDragonAntivirus
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
Still amazed virus scope catched it
Got it enabled only in the container on my system but maybe if it gets better I could enable it globally
Not at first site but by manuallyIs Kaspersky able to detect?
And maybe the behavior components , hips can prevent the infection itself
K
Kaspersky?
VirusScope is amazing at analyzing unknown apps in sandbox it uses Static Analysis and Dynamic Analysis to do thatStill amazed virus scope catched it
Got it enabled only in the container on my system but maybe if it gets better I could enable it globally
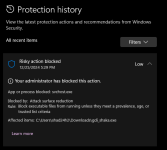
Please check KasperskyMS Defender configured
View attachment 286859View attachment 286860
But once I reset it to default in DefenderUI, it passes without reaction (which was to be expected).
View attachment 286861
Sorry I missed. @harlan4096 could you please reply again??@harlan4096 has already done so and mentioned
VirusTotal What about Zillya?Interesting, hadn't heard previously that Rising uses the cloud from Kaspersky.
View attachment 286845
- Apr 28, 2015
- 9,397
- 1
- 84,815
- 8,389
I see You got no bootable systems, but in the case of Kaspersky, system was not destroyed up to that point, in fact I could reboot without issues, but all my custom settings in my local account were changed to default or removed, for example the taskbar icons pinned, the order of the icons in the desktop, the color theme of the session, things like that, but system was completely usable.
Last edited:
Shaka when walls fellLest Eset's dynamic analysis isn't sad alone, Sophos also totally lost this battle. While its screens show significant damage to the system.
View attachment 286842
View attachment 286843
Temba his arms wide
The emulation from the extension failed but pretty sure if you actually executed the sample the behavior components would have stopped it and probably the same with ksn , liveguard both failed but if you actually executed the sample it just might have stopped the infection using some behavior componentsZone alarm?
Above harlan showed that actually execution ofthe sample would cause behavior components to defend at least some damage and the same will happen with some other avsI see You got no bootable systems, but in the case of Kaspersky, system was not destroyed up to that point, in fact I could reboot without issues, but all my custom settings in my local account were changed to default or removed, for example the taskbar icons pinned, the order of the icons in the desktop, the color theme of the session, things like that, but system was completely usable.
(Edit Harlan below showed that it was actually the hips component that blocked some of the malicious activity)
Last edited:
- Apr 28, 2015
- 9,397
- 1
- 84,815
- 8,389
Hum actually the sample did not trigger any behavior component (although KOTIP service tagged it as malware in 1st execution), but probably Intrusion Prevention, putting it in Low Restricted group, minimized in part, the malicious activities, and avoided to completely destroy the system.
I don't think it was in the first execution in the opentip sandbox but changing the hash is probably enough to find outHum actually the sample did not trigger any behavior component (although KOTIP service tagged it as malware in 1st execution), but probably Intrusion Prevention, putting it in Low Restricted group, minimized in part, the malicious activities, and avoided to completely destroy the system.
It's easy to evade sophos anyway as they literally load services of sophos software into the sandbox of intelixLest Eset's dynamic analysis isn't sad alone, Sophos also totally lost this battle. While its screens show significant damage to the system.
View attachment 286842
View attachment 286843
Not just that new gaming engine languages and even rust to some extent
- Status
- Not open for further replies.
You may also like...
-
-
-
Malware News Emojis in PureRAT’s Code Point to AI-Generated Malware Campaign
- Started by Brownie2019
- Replies: 11
-
AVLab.pl Analysis of system protection against active online malware – July 2025
- Started by Adrian Ścibor
- Replies: 165