Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Mar 13, 2016
- 1,298
Why a seperate thread?
I got a few questions in the uB0 thread settings about uMatrix. Posting about two different extensions (although both written by same developer) causes confusion. Therefore I will repost the uMatrix related post in this thread.
What is the idea behind this uMatrix configuration?
In the default configuration uMtarix uses a ' soft' third-party sources block. Gorhill calls it soft, because third-party images and stylesheets are allowed in the default rules configuration. The benefit of blocking third-party sources is that it reduces the risk of malware infection and at the same time blocks 90% of the trackers (so good for privacy also). The problem with blocking all third party scripts, (i)frames and xmlHttprequests (XHR) that functionality on most websites is broken. That is why the uMatrix wiki also contains a ALLOW ALL how to.
As published by phishtank and some DNS services some TLD's and country code have a high percentage of malware (see post). When Google Chrome was launched some smart power users started to post how to block scripts in general, allowing only a few Top Level Domains to execute scripts (block scripts by default and allow for example all domains with TLD is COM, NET, INF, ORG, GOV and a few country codes like DK is for Denmark). This whitelist on some general Top Level Domains (COM, ORG, GOV) and a few country code's makes sense since most of us only speak one or two languages.
This idea used on Google Chrome is used for the uMtarix setup "Soft third-party blockmode with whitelist to allow some TLD's" . Benefit of using uMatrix is that you apply it on other (non-chromium based) browsers also and that umatrix also block XHR (XMLHTTPRequests) and (i)frames besides scripts.
IN the Netherlands I was thought French, German and English. Because I used English and German for work, I forgot most French and only read (besides Dutch) German and English sources. So you won't find websites from France or China, North Korea, Russia and Ukraine in my bookmarks. When I normally don't visit these websites, I just as well can block those country codes in uMtarix. Since uMtraix has a default deny, in stead of blocking I am whitelisting the TLD's I use to visit.
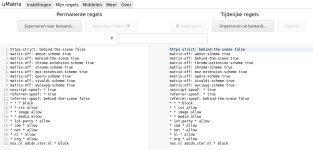
ALLOW SOME THIRD-PARTY RULE SET.
Bottom line: this is not as safe as a BLOCK ALL third-party, but is safer that a ALLOW ALL. The setup is a cross-over of the SOFT THIRD-PARTY block and ALLOW ALL (when you replace the NL country code with the country code of the country you live in and websites publishing content in a foreign language you speak. It is probably more beneficial to users who add an ALLOW ALL for websites often.
View attachment 216080
Check whether 3rd-party TLD whitelist is working
When I surf to CNN.com and use the above ruleset I can see that CNN.IO is blocked (other com, net are allowed when not blocked by my assets).View attachment 216089
-------------------------
Converted the W3techs.com most used ad & trackers in top 10 million websites (it are actually only 175 ) to uMatrix rules. Just download and open the text file and copy them into My Rules. I now run uMatrix without any blocklist assets.
) to uMatrix rules. Just download and open the text file and copy them into My Rules. I now run uMatrix without any blocklist assets.
Upside of using default blocklists us that the My Rules section remains clear and uncluttered.There is NO memory or CPU advantage in further reducing blocklist from 50K to (Peter Low, MVPS, Adguard DNS and Easylist Host) to only top 175 most used ads and trackers worldwide of Alexa top 10 million websites (derived from W3techs.com)
I got a few questions in the uB0 thread settings about uMatrix. Posting about two different extensions (although both written by same developer) causes confusion. Therefore I will repost the uMatrix related post in this thread.
What is the idea behind this uMatrix configuration?
In the default configuration uMtarix uses a ' soft' third-party sources block. Gorhill calls it soft, because third-party images and stylesheets are allowed in the default rules configuration. The benefit of blocking third-party sources is that it reduces the risk of malware infection and at the same time blocks 90% of the trackers (so good for privacy also). The problem with blocking all third party scripts, (i)frames and xmlHttprequests (XHR) that functionality on most websites is broken. That is why the uMatrix wiki also contains a ALLOW ALL how to.
As published by phishtank and some DNS services some TLD's and country code have a high percentage of malware (see post). When Google Chrome was launched some smart power users started to post how to block scripts in general, allowing only a few Top Level Domains to execute scripts (block scripts by default and allow for example all domains with TLD is COM, NET, INF, ORG, GOV and a few country codes like DK is for Denmark). This whitelist on some general Top Level Domains (COM, ORG, GOV) and a few country code's makes sense since most of us only speak one or two languages.
This idea used on Google Chrome is used for the uMtarix setup "Soft third-party blockmode with whitelist to allow some TLD's" . Benefit of using uMatrix is that you apply it on other (non-chromium based) browsers also and that umatrix also block XHR (XMLHTTPRequests) and (i)frames besides scripts.
IN the Netherlands I was thought French, German and English. Because I used English and German for work, I forgot most French and only read (besides Dutch) German and English sources. So you won't find websites from France or China, North Korea, Russia and Ukraine in my bookmarks. When I normally don't visit these websites, I just as well can block those country codes in uMtarix. Since uMtraix has a default deny, in stead of blocking I am whitelisting the TLD's I use to visit.
ALLOW SOME THIRD-PARTY RULE SET.
Bottom line: this is not as safe as a BLOCK ALL third-party, but is safer that a ALLOW ALL. The setup is a cross-over of the SOFT THIRD-PARTY block and ALLOW ALL (when you replace the NL country code with the country code of the country you live in and websites publishing content in a foreign language you speak. It is probably more beneficial to users who add an ALLOW ALL for websites often.
View attachment 216080
Check whether 3rd-party TLD whitelist is working
When I surf to CNN.com and use the above ruleset I can see that CNN.IO is blocked (other com, net are allowed when not blocked by my assets).View attachment 216089
-------------------------
Converted the W3techs.com most used ad & trackers in top 10 million websites (it are actually only 175
Upside of using default blocklists us that the My Rules section remains clear and uncluttered.There is NO memory or CPU advantage in further reducing blocklist from 50K to (Peter Low, MVPS, Adguard DNS and Easylist Host) to only top 175 most used ads and trackers worldwide of Alexa top 10 million websites (derived from W3techs.com)
Attachments
Last edited by a moderator: