Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Mar 13, 2016
- 1,298
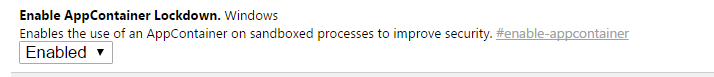
Windows 10 introduced some strong mitigations to reduce the attack surface of vulnarable applications. On Windows 10, about flags of Chrome offers an option to enable the Win32k-lockdown to prevent access to large part of the kernel (hence reducing the risk of exploits doing something malicious to your system).
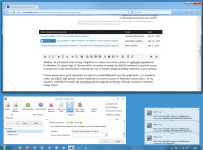
Firefox always had a good reputation in regard to compatibility with security applications, so I wondered could I use EMET's ASR (Attack Surface Reduction) to prevent access to important system DLL's. To my surprise I could block kernel32.dll, kernelbase.dll and ntdll.dll and firefox still kept working as attached image shows?
Browsing with rich media (video, sound) and downloading of files (liek PDF) seems to work OK, the only thing that does not work (as far as I noticed) is uploading of files (firefox becomes inresponsive and seems to crash). Strangy Chrome does crash while it had options in about://flags to enable this Windows 10 mitigation.
I also tried to block ole32.dll, but than sound does not work (remains silent) and firefox won't download files (won't crash).
Firefox always had a good reputation in regard to compatibility with security applications, so I wondered could I use EMET's ASR (Attack Surface Reduction) to prevent access to important system DLL's. To my surprise I could block kernel32.dll, kernelbase.dll and ntdll.dll and firefox still kept working as attached image shows?
Browsing with rich media (video, sound) and downloading of files (liek PDF) seems to work OK, the only thing that does not work (as far as I noticed) is uploading of files (firefox becomes inresponsive and seems to crash). Strangy Chrome does crash while it had options in about://flags to enable this Windows 10 mitigation.
I also tried to block ole32.dll, but than sound does not work (remains silent) and firefox won't download files (won't crash).
Attachments
Last edited: