- Dec 23, 2014
- 8,970
I prepared the profile "Windows_10_MT_Windows_Security_hardening.hdc" which uses the new option <Validate Admin Code Signatures>.
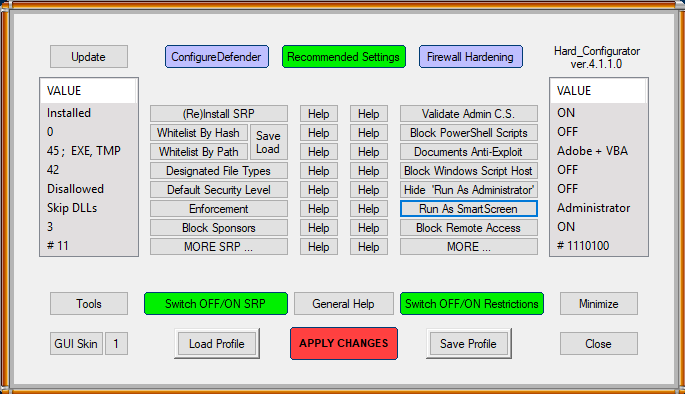
It can be used both on SUA or Admin account (no difference with restrictions). When loading the profile to H_C, the below info will be displayed:
************************************************************
Harden Windows 10 while maintaining maximum functionality and compatibility (proposed on MalwareTips forum by @Windows_Security).
Please note: this profile allows the user to run EXE files, except unsigned files which require Administrative rights. MSI installation packages are more restricted - they can be run only via the "Run as administrator" option in the Explorer context menu and only digitally signed packages will be allowed.
It is recommended to use this profile with ConfigureDefender High Protection Level and "Recommended H_C" firewall outbound block rules (see <FirewallHardening> option).
The profile works best when the user installs digitally signed applications (EXE / MSI), or unsigned EXE applications which do not require Administrative rights.
When the unsigned EXE file is blocked, then the Error message is displayed, which ends with:
"... A referral was returned from the server".
**************************************************************
Any suggestions to improve the above info text?
It can be used both on SUA or Admin account (no difference with restrictions). When loading the profile to H_C, the below info will be displayed:
************************************************************
Harden Windows 10 while maintaining maximum functionality and compatibility (proposed on MalwareTips forum by @Windows_Security).
Please note: this profile allows the user to run EXE files, except unsigned files which require Administrative rights. MSI installation packages are more restricted - they can be run only via the "Run as administrator" option in the Explorer context menu and only digitally signed packages will be allowed.
It is recommended to use this profile with ConfigureDefender High Protection Level and "Recommended H_C" firewall outbound block rules (see <FirewallHardening> option).
The profile works best when the user installs digitally signed applications (EXE / MSI), or unsigned EXE applications which do not require Administrative rights.
When the unsigned EXE file is blocked, then the Error message is displayed, which ends with:
"... A referral was returned from the server".
**************************************************************
Any suggestions to improve the above info text?

