Idea background
1. OS_Armor.
Use OS_Armor in default settings to block known malware execution patterns of legitimate (Windows) programs. I only excluded some script execution block rules, because the Software Protection Rules enforced by Hard_Configurato already block them in user folders (which offers similar protection with less compatibility risk). OS_Armor block rules are very granular.. Basically OS-Armor blocks legitimate programs to execute when they are used in way often seen by malware and ransomware.
2. Hard_Configurator
Use Hard-Configurator to block dangerous file extensions in user folders, but allow execution of programs for compatibility by loading the profile: Windows_10_MT_Windows_Security_hardening.hdc. I disabled UAC Validate Admin Code Signature, because I hope/guess Windows_Defender in MAX will block unsigned programs with poor reputation to execute.
3.Configure_Defender
Use Configure Defender to use Windows Defender in MAXimum protection. One of the benefits is that it blocks unknown programs with poor reputation in this MAXimum setting. In stead of all blocking programs with SRP, this allow/block decision is now transfered to the Windows Defender cloud mechanism. My guess is that most average PC users don't install a lot of software, so this false positive risk (blocking to much) is minimal.
4. Firewall Hardening
Enabled to block LOLbins also, just as an extra layer,in case the execution of a LOLbin slips through OS_Armor.
Running it for a few days now on my Windows10 partition. What do seasoned members think of this freebie combo? I tweaked as little as possible to the default settings, because Andreas and Andy know a lot more about security than me. Keeping this combo close to the defaults , is my best bet to achieve maximum protection with maximum compatibility and maximum usability.
___________________ disabling some default OS_Armor rules to block execution of scripts (anywhere) ____________________
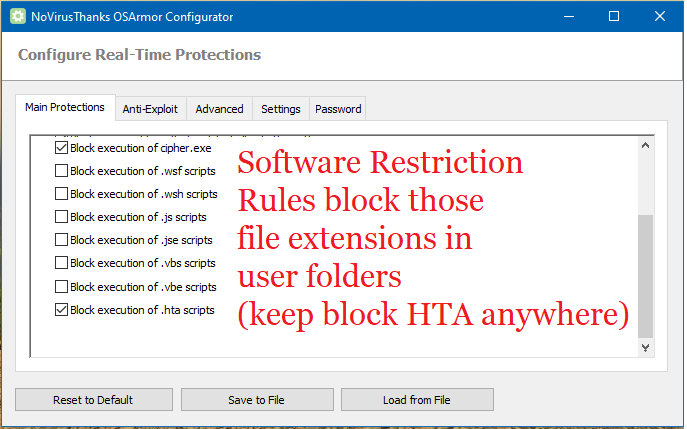
1. OS_Armor.
Use OS_Armor in default settings to block known malware execution patterns of legitimate (Windows) programs. I only excluded some script execution block rules, because the Software Protection Rules enforced by Hard_Configurato already block them in user folders (which offers similar protection with less compatibility risk). OS_Armor block rules are very granular.. Basically OS-Armor blocks legitimate programs to execute when they are used in way often seen by malware and ransomware.
2. Hard_Configurator
Use Hard-Configurator to block dangerous file extensions in user folders, but allow execution of programs for compatibility by loading the profile: Windows_10_MT_Windows_Security_hardening.hdc. I disabled UAC Validate Admin Code Signature, because I hope/guess Windows_Defender in MAX will block unsigned programs with poor reputation to execute.
3.Configure_Defender
Use Configure Defender to use Windows Defender in MAXimum protection. One of the benefits is that it blocks unknown programs with poor reputation in this MAXimum setting. In stead of all blocking programs with SRP, this allow/block decision is now transfered to the Windows Defender cloud mechanism. My guess is that most average PC users don't install a lot of software, so this false positive risk (blocking to much) is minimal.
4. Firewall Hardening
Enabled to block LOLbins also, just as an extra layer,in case the execution of a LOLbin slips through OS_Armor.
Running it for a few days now on my Windows10 partition. What do seasoned members think of this freebie combo? I tweaked as little as possible to the default settings, because Andreas and Andy know a lot more about security than me. Keeping this combo close to the defaults , is my best bet to achieve maximum protection with maximum compatibility and maximum usability.
___________________ disabling some default OS_Armor rules to block execution of scripts (anywhere) ____________________
Last edited:

