Hello Everybody,
This is my new BitDefender Endpoint Detection Response (EDR) test box. ( free trial 1 month )
It has the usual executive summary - which includes: Modules Installed, Risk Score, Incident Status, Top 5 Blocked Threats ...
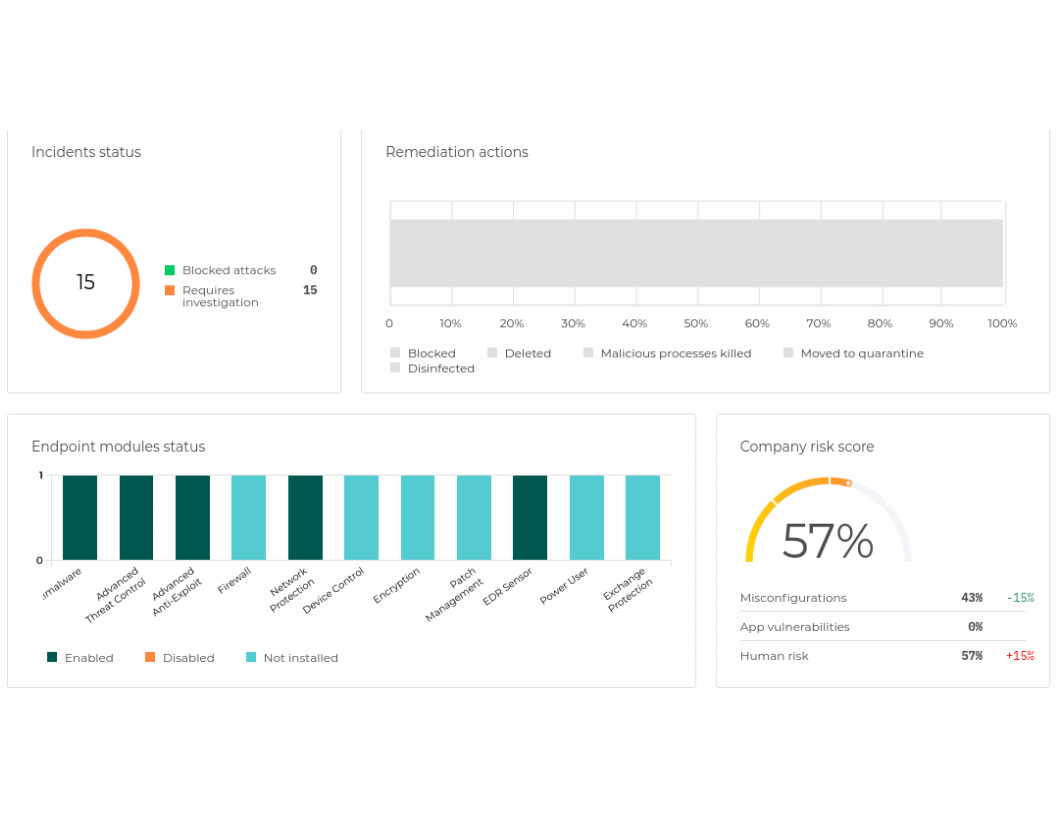
The client/agent has no features to toggle or play with. So I won't show it here.
It has a Incidents section.
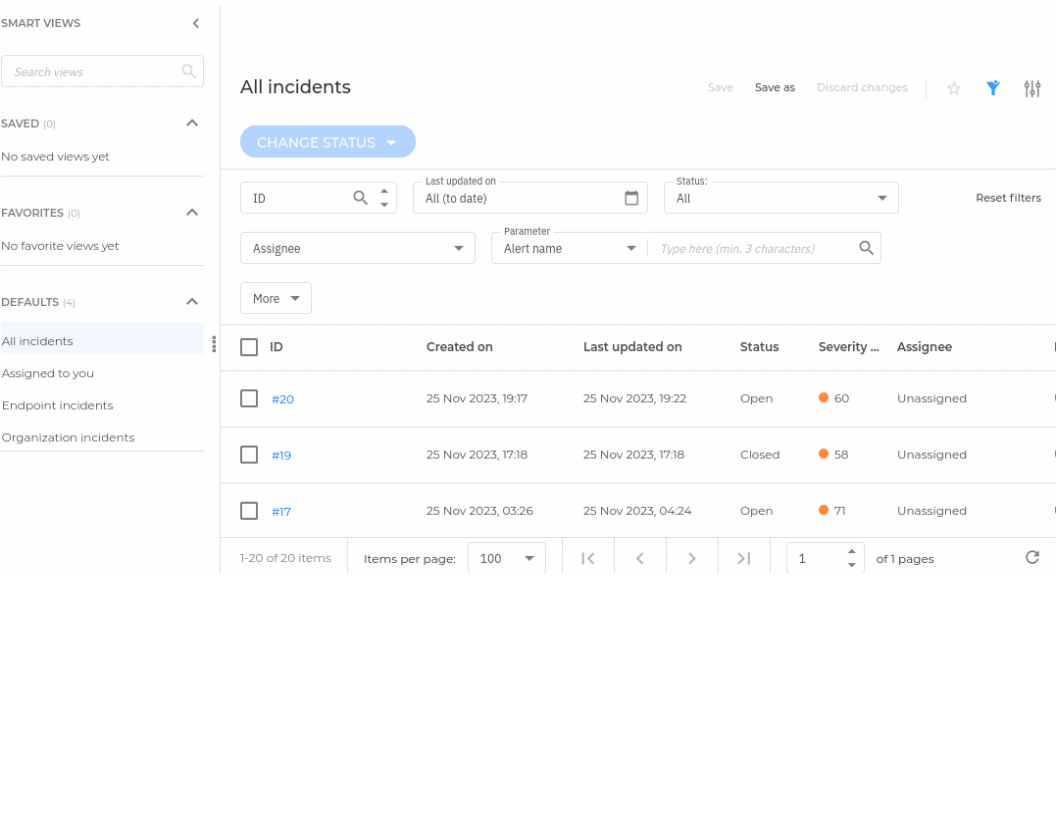
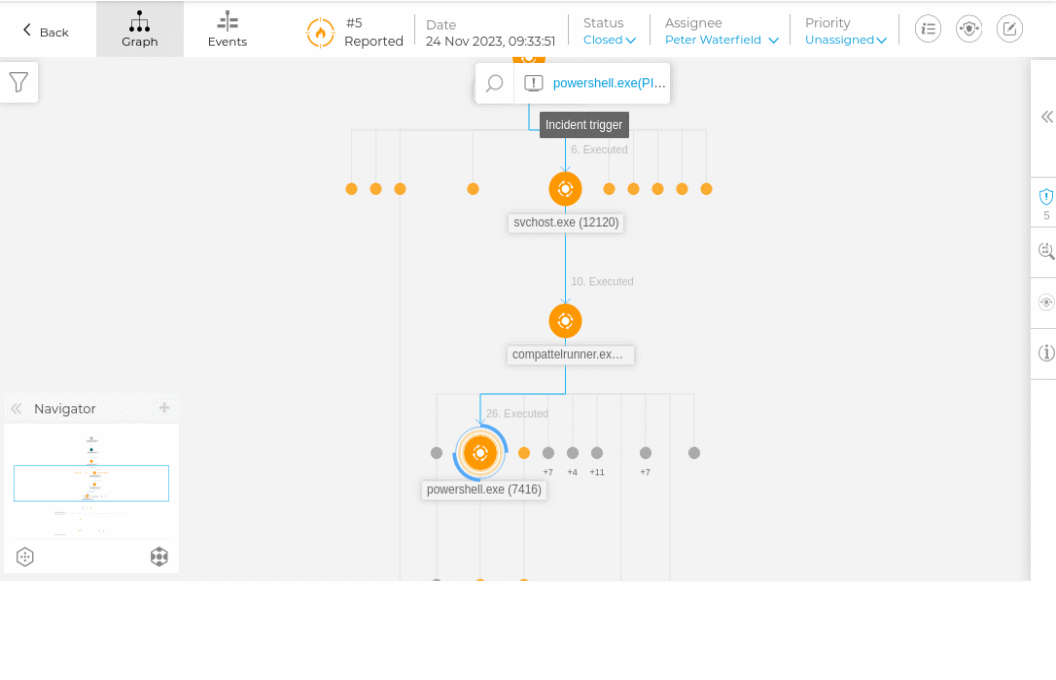
And here is a screenshot of a real incident.
Here is a screenshot of all my machines (1), located in Network menu.
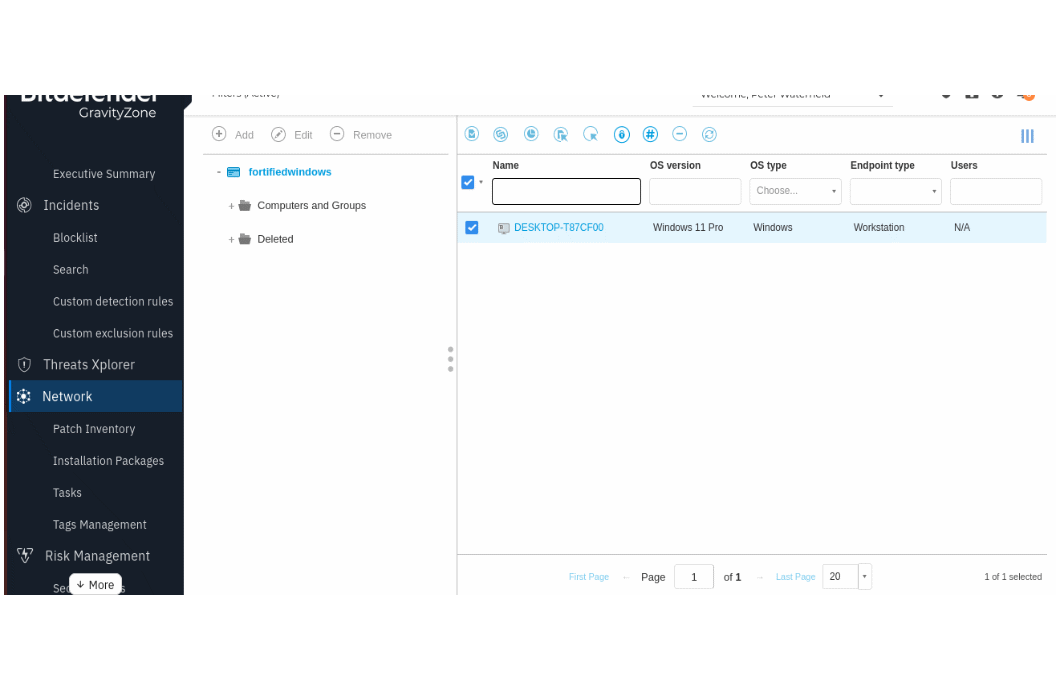
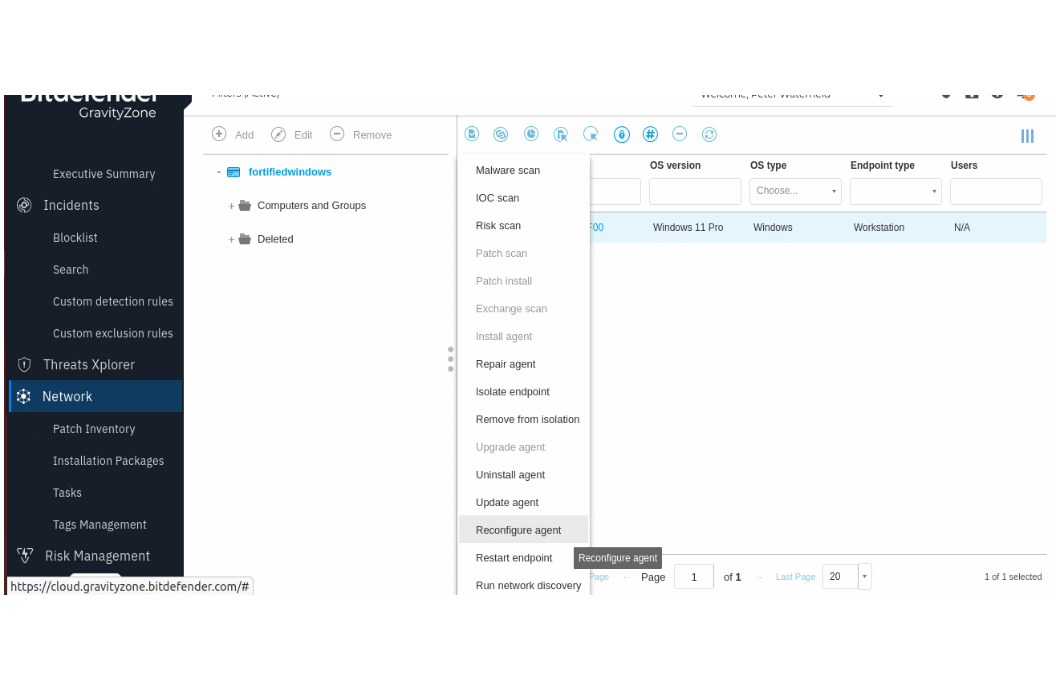
And here is where you add modules to the agent, from Network, checkmark machine, click on Task button on top, and choose Reconfigure Agent.
The Advanced Anti Exploit module is Not part of the default configuration of an agent, and must be manually added this way.
I find that BitDefender EDR's native detection rules don't detect much. So I added my own rules, at Incident > Custom Detection Rules. It basically adds a detection rule by keyword.
BitDefender EDR, like all EDR's, is primarily an anti-malware. When it's arsenal can't stop an attack, the EDR portion has one more weapon, and that is the EDR's block list. It can block a file by file hash.
However, if the attacker is using a Windows native tool, like compattelagent.exe as shown in the screenshot above; there isn't much it can do if you can't block it. So you NEED other layers of defense.
I have chosen Comodo Firewall with it Auto Containment and Host Intrusion Detection System as my second layer. And used the HIDS to contain compattagent.exe. I haven't noticed any Windows malfunction so far.
In order to use Comodo Firewall, I removed BitDefender's firewall module, because having 2 firewalls with each's own rules is a cause for confusion. This was done using the above Reconfigure Agent task.
This is my new BitDefender Endpoint Detection Response (EDR) test box. ( free trial 1 month )
It has the usual executive summary - which includes: Modules Installed, Risk Score, Incident Status, Top 5 Blocked Threats ...
The client/agent has no features to toggle or play with. So I won't show it here.
It has a Incidents section.
And here is a screenshot of a real incident.
Here is a screenshot of all my machines (1), located in Network menu.
And here is where you add modules to the agent, from Network, checkmark machine, click on Task button on top, and choose Reconfigure Agent.
The Advanced Anti Exploit module is Not part of the default configuration of an agent, and must be manually added this way.
I find that BitDefender EDR's native detection rules don't detect much. So I added my own rules, at Incident > Custom Detection Rules. It basically adds a detection rule by keyword.
BitDefender EDR, like all EDR's, is primarily an anti-malware. When it's arsenal can't stop an attack, the EDR portion has one more weapon, and that is the EDR's block list. It can block a file by file hash.
However, if the attacker is using a Windows native tool, like compattelagent.exe as shown in the screenshot above; there isn't much it can do if you can't block it. So you NEED other layers of defense.
I have chosen Comodo Firewall with it Auto Containment and Host Intrusion Detection System as my second layer. And used the HIDS to contain compattagent.exe. I haven't noticed any Windows malfunction so far.
In order to use Comodo Firewall, I removed BitDefender's firewall module, because having 2 firewalls with each's own rules is a cause for confusion. This was done using the above Reconfigure Agent task.
Last edited: