Leak occurs for HTTPS streams as well
According to researchers, these fingerprints are observable even if the traffic is encrypted, and an attacker can detect the download pattern even in video streams protected via HTTPS.
An attacker only needs to create a database of fingerprints for streamable video files he wants to keep an eye out.
To carry out such massive surveillance, the attacker needs to be in a position to intercept and sniff the user's traffic, such as an ISP, nation-state, traffic moderator, or malware present on smaller LANs.
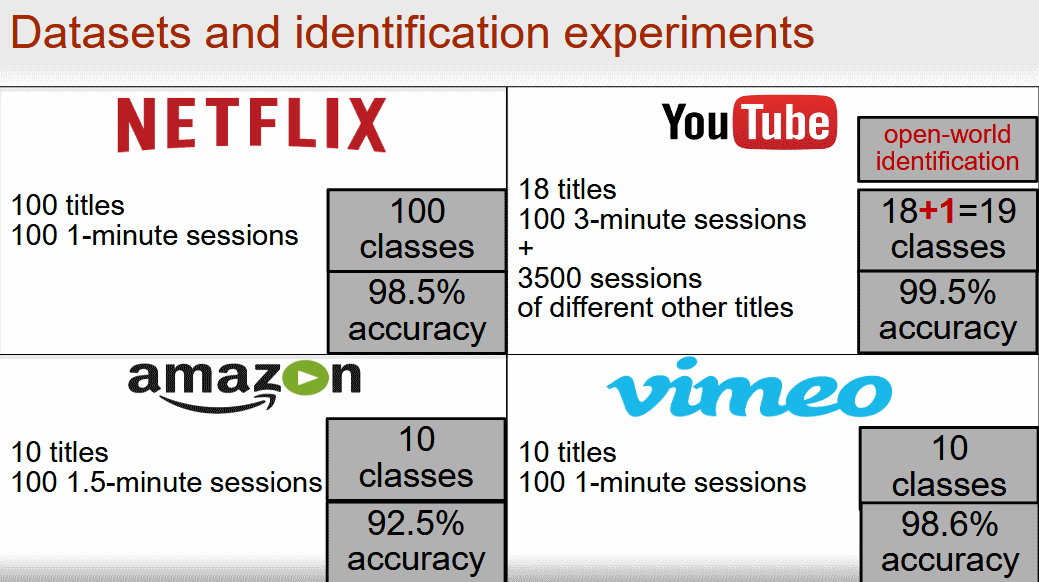
The attack's success rate is way above similar techniques, with an average success rate of over 95%. In tests, the research team says it successfully identified videos a user was watching with a 99.5% success rate for YouTube, 98.6% for Vimeo, 98.5% for Netflix, and 92.5% for Amazon.
Furthermore, researchers also demonstrated a technique that ports this attack to JavaScript code hidden in an ad, when an attacker cannot obtain a role to directly observe a stream.
MPEG-DASH leak has good and bad side
While there are clear privacy implications for this attack — such as oppressive governments keeping an eye on who watches anti-government videos — there are also good uses for the MPEG-DASH leak.
For example, law enforcement agencies could use the leak to track down people who watch child abuse or terrorist videos.
More details about the MPEG-DASH leak are available in a research paper titled "Beauty and the Burst: Remote Identification of Encrypted Video Streams," available for download
here,
here, and
here.
The research team also set up a
dedicated website and presented their work at the USENIX security conference. A video of their presentation is available below.