Virtual Rootkit
- Thread starter Aaron25g
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hello,
I think you're kinda paranoid but let's talk anyway.
What do you mean by X: that you cannot remove?
Where did you see that you have unknown MBR?
I do not see 2048gb hidden drive that you mentioned.
What anti rootkit tools you used that showed you infection?
 Scan with TDSSKiller
Scan with TDSSKiller
Please download TDSSKiller by Kaspersky and save it to your desktop.
If anything will be found follow this guidelines:
A report will be created in your root directory, (usually C:\ drive) in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt. Please include the contents of that file in your next post.
I think you're kinda paranoid but let's talk anyway.
What do you mean by X: that you cannot remove?
Where did you see that you have unknown MBR?
I do not see 2048gb hidden drive that you mentioned.
What anti rootkit tools you used that showed you infection?

Please download TDSSKiller by Kaspersky and save it to your desktop.
- Right-click on icon and select
 Run as Administrator to start the tool.
Run as Administrator to start the tool.
- Click on Change parameters and put a checkmark beside Loaded modules. A reboot will be needed to apply the changes, allow it to do so.
- Your machine may appear very slow and unusable after that - it's normal.
- TDSSKiller will run automaticaly. Click on Change parameters and click OK.
- Click the Start Scan button and wait patiently.
If anything will be found follow this guidelines:
- If a suspicious object is detected, the default action will be Skip, click on Continue.
- If malicious objects are found, they will show in the Scan results - Select action for found objects and offer three options.
Ensure Cure (default) is selected, then click Continue > Reboot now to finish the cleaning process.
If Cure is not available, please choose Skip instead. - Do not choose Delete unless instructed!
A report will be created in your root directory, (usually C:\ drive) in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt. Please include the contents of that file in your next post.
Thank you for your fast reply.
I really hope you are correct that it is paranoia but I don't think it is the case.
The X: that I am referring to is after I do a complete wipe and go into a command prompt just before initiating the windows 10 reinstallation, I find that I can open a X: drive in the command prompt that appears to contain all memory of my activity back to July 9 this year, I can force delete most of the files except a few that always remain and appear to be encrypted.
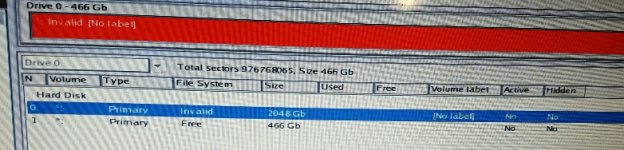
I have attached an image containing the scan that found the 2048GB drive.
Mbar finds an infection only in the first scan after a complete wipe but when it prompts to restart to clean infection all I have is a black screen with the cursor that I can move around.
I just tried scanning with mbam chameleon and like all other anti rootkit software it cannot load the anti rootkit drivers possibly due to rootkit infection. The scripts that I am finding throughout my computer are definitely related to this issue, I have attached a few small logs I have found that I feel are in someway related to this issue.
I will now perform a scan using Kaspersky TDSS killer if you feel that I should, I have used this many times before though and if I scan with checking the option to scan loaded modules, my computer will not reboot and I will have to do a reinstallation of windows 10. should I still continue with this scan?
theres one log named setupAct_offline.log that contains all the info on whats happening but its too big to upload.
I really hope you are correct that it is paranoia but I don't think it is the case.
The X: that I am referring to is after I do a complete wipe and go into a command prompt just before initiating the windows 10 reinstallation, I find that I can open a X: drive in the command prompt that appears to contain all memory of my activity back to July 9 this year, I can force delete most of the files except a few that always remain and appear to be encrypted.
I have attached an image containing the scan that found the 2048GB drive.
Mbar finds an infection only in the first scan after a complete wipe but when it prompts to restart to clean infection all I have is a black screen with the cursor that I can move around.
I just tried scanning with mbam chameleon and like all other anti rootkit software it cannot load the anti rootkit drivers possibly due to rootkit infection. The scripts that I am finding throughout my computer are definitely related to this issue, I have attached a few small logs I have found that I feel are in someway related to this issue.
I will now perform a scan using Kaspersky TDSS killer if you feel that I should, I have used this many times before though and if I scan with checking the option to scan loaded modules, my computer will not reboot and I will have to do a reinstallation of windows 10. should I still continue with this scan?
theres one log named setupAct_offline.log that contains all the info on whats happening but its too big to upload.
Attachments
The X: that I am referring to is after I do a complete wipe and go into a command prompt just before initiating the windows 10 reinstallation, I find that I can open a X: drive in the command prompt that appears to contain all memory of my activity back to July 9 this year, I can force delete most of the files except a few that always remain and appear to be encrypted.
I have this too on my Windows 10 notebook too. Don't know for sure what it is, but I suppose it is System Reserved partition or some kind of Windows bootloader. Whatever it is, it is not malware 100%.
I have attached an image containing the scan that found the 2048GB drive.
It seems to be non-operational. Do you have this drive in your computer?
Mbar finds an infection only in the first scan after a complete wipe but when it prompts to restart to clean infection all I have is a black screen with the cursor that I can move around.
I just tried scanning with mbam chameleon and like all other anti rootkit software it cannot load the anti rootkit drivers possibly due to rootkit infection. The scripts that I am finding throughout my computer are definitely related to this issue, I have attached a few small logs I have found that I feel are in someway related to this issue.
I would like to see a picture what exactly MBAR finds.
Message about failure to load anti rootkit software is quite common and doesn't mean you actually have rootkit.
I will now perform a scan using Kaspersky TDSS killer if you feel that I should, I have used this many times before though and if I scan with checking the option to scan loaded modules, my computer will not reboot and I will have to do a reinstallation of windows 10. should I still continue with this scan?
Please scan with it, but remove nothing. If something is found change action to Skip. Then attach report.
theres one log named setupAct_offline.log that contains all the info on whats happening but its too big to upload.
Such logs are very common on all computers. They belong to your software, often they are created during drivers installation. Nothing to worry about, you can delete them, but they are not malicious and do not contain any hidden scripts.
Thank you again for your fast response.
Thank you that's good to know.
No this drive is definitely has nothing to do with my computer, my drive is only 500GB.
I have also attached a scan from aswmbr from a few days ago, I have lost the logs in all the wipes I have since done.
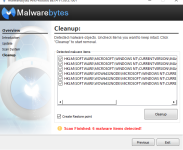
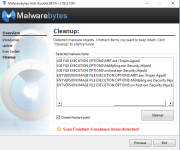
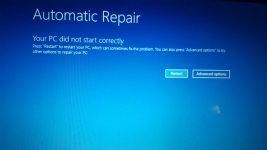
I just performed a mbar scan, as I cant get the log file until I do the suggested reboot I have attached screenshots of the problems found.
I will now do the scan with Kaspersky TDSS killer and post the log.
the thing that worries me is everytime I reinstall windows, the screen flashes for 1second which I feel is the script starting up, it also restarts approximately 4-5 times before I can actually use windows. I also noticed all the scripts are set to disappear after 1 second and don't think this is a coincidence. also things such as all 6 usb ports on my smart tv are disabled and greyed out along with 3d viewing, I found a script that says to disable 3dviewing and a usb root hub keeps connecting to my computer through device management.
I am also currently disputing with my phone company the $2500 phone bill for last month that according to them I have been making non stop calls through the internet. I can sometimes hear talking and breathing when using my home phone. I have also found instructions on what programs to use on my computer, such as only to use 7zip for some reason and descriptions of what people can and cant do etc...The worst thing is this all started 2 weeks before my thesis was due, my thesis has now disappeared.
your help is really appreciated
Thank you that's good to know.
No this drive is definitely has nothing to do with my computer, my drive is only 500GB.
I have also attached a scan from aswmbr from a few days ago, I have lost the logs in all the wipes I have since done.
I just performed a mbar scan, as I cant get the log file until I do the suggested reboot I have attached screenshots of the problems found.
I will now do the scan with Kaspersky TDSS killer and post the log.
the thing that worries me is everytime I reinstall windows, the screen flashes for 1second which I feel is the script starting up, it also restarts approximately 4-5 times before I can actually use windows. I also noticed all the scripts are set to disappear after 1 second and don't think this is a coincidence. also things such as all 6 usb ports on my smart tv are disabled and greyed out along with 3d viewing, I found a script that says to disable 3dviewing and a usb root hub keeps connecting to my computer through device management.
I am also currently disputing with my phone company the $2500 phone bill for last month that according to them I have been making non stop calls through the internet. I can sometimes hear talking and breathing when using my home phone. I have also found instructions on what programs to use on my computer, such as only to use 7zip for some reason and descriptions of what people can and cant do etc...The worst thing is this all started 2 weeks before my thesis was due, my thesis has now disappeared.
your help is really appreciated
Attachments
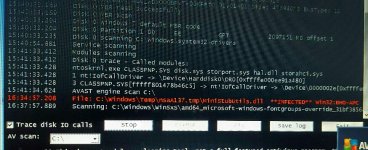
No I never deleted nothing, I never even had the chance to. I checked the boxes you said to check, TDSS killer said it will now reboot to start the scan, computer restarted to the screen I provided in the last message. This happens everytime I run either TDSS killer or GMER. The only option I have is to either do a full reinstall or reset the computer.
When my computer restarted I did a scan with Sophos which found a virus in the TDSS killer file I had just downloaded. I also found that even though TDSS killer did nothing there is a short log in my directory which I have attached.
I then ran a OTL scan an uploaded the results, the main scan is too big to upload so I have attached the extras part.
When my computer restarted I did a scan with Sophos which found a virus in the TDSS killer file I had just downloaded. I also found that even though TDSS killer did nothing there is a short log in my directory which I have attached.
I then ran a OTL scan an uploaded the results, the main scan is too big to upload so I have attached the extras part.
Attachments
I ran the scan but it never found anything. Then when trying to upload the file it would keep saying error the file is empty, so i made a copy in notepad and uploaded it.
I have received an email from Microsoft last night letting me know of unusual sign in activity.
I also ran a scan with spyhunter which found 60 possible infections, the infection that caught my eye was the "adaptv_uniquie_user_cookie.WMGHJPCN.txt, I have not cleaned anything i only ran the scan.
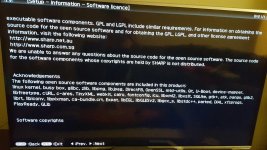
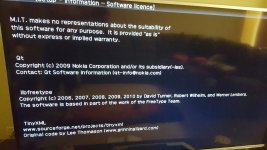
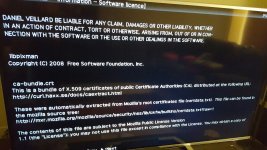
This must have something to do with TV. So i then looked at the licenses on my tv and it contains all the same things as on my computers and phones, linux and lib files etc I dont understand much of it except i know none of it should be there, it goes on for 86 pages.
I have received an email from Microsoft last night letting me know of unusual sign in activity.
I also ran a scan with spyhunter which found 60 possible infections, the infection that caught my eye was the "adaptv_uniquie_user_cookie.WMGHJPCN.txt, I have not cleaned anything i only ran the scan.
This must have something to do with TV. So i then looked at the licenses on my tv and it contains all the same things as on my computers and phones, linux and lib files etc I dont understand much of it except i know none of it should be there, it goes on for 86 pages.
Attachments
-
 20160101_090655_resized.jpg454.8 KB · Views: 6
20160101_090655_resized.jpg454.8 KB · Views: 6 -
 20160101_090754_resized.jpg420.7 KB · Views: 5
20160101_090754_resized.jpg420.7 KB · Views: 5 -
 20160101_090834_resized.jpg492.9 KB · Views: 6
20160101_090834_resized.jpg492.9 KB · Views: 6 -
 20160101_091857_resized.jpg451.2 KB · Views: 5
20160101_091857_resized.jpg451.2 KB · Views: 5 -
TDSSKILLER.txt115.6 KB · Views: 3
-
setupact.offline.log28.2 KB · Views: 3
-
DDACL.sys1.log28.2 KB · Views: 3
All of this is okay. Spyhunter just like every malware removal tool shouldn't be trusted 100%, especially some less reputable tools.
TDSSKiller log is clean. Let's make one more scan with MawareBytes:
 Scan with Malwarebytes' Anti-Malware
Scan with Malwarebytes' Anti-Malware
Please download Malwarebytes Anti-Malware and save it to your desktop.
TDSSKiller log is clean. Let's make one more scan with MawareBytes:

Please download Malwarebytes Anti-Malware and save it to your desktop.
- Install the progam and select update.
- Once updated, click the Settings tab, in the left panel choose Detection & Protection and tick Scan for rootkits.
- In the same tab, under PUP and PUM detections make sure it is set to Treat detections as malware.
- Click the Scan tab, choose Threat Scan is checked and click Start Scan.
- If threats are detected, click the Apply Actions button. You will now be prompted to reboot. Click Yes.
- Upon completion of the scan (or after the reboot), click the History tab.
- Click Application Logs and double-click the Scan Log.
- At the bottom click Export and choose Text file.
Are you sure that's all normal? Do you know why my smart tv now contains the same files as all my computers and mobiles? and how all the devices acquired these files at the exact date and time? my tv should have nothing to do with a Linux OS or open license software. This would explain all the instructions I have been finding lately.
I should also let you know that every file I download is significantly larger when the download completes than what it says when confirming the download, almost every security certificate I find was installed on either the 9th or 10th of July this year, around the same time I noticed all Japanese fonts on my computer.
I also feel there is no reason why I should be having issues in regards to all CA certs on all systems if they wernt corrupt. All the issues seem to stem from corrupt certs I don't even think the ps4 uses them, but over the last few months it nearly always starts with an error regarding CA certs, and that play ready thing in the last image on my tv is apparently a way to create a virtual system and virtual games on a ps4 for advanced Linux users. Half the CMD options are missing and doskeys are always changing etc, keyboard stops working, everything I do is countered with a reaction.
I understand why you feel I'm paranoid, at first so did i, but there is so much data on all my systems to dispute I have no idea where to start, Even my BIOS is no longer the same as what it used to be. There is no doubt what so ever I have either a severe infection and the infection is preventing me from installing an authentic version of windows.
I should also let you know that every file I download is significantly larger when the download completes than what it says when confirming the download, almost every security certificate I find was installed on either the 9th or 10th of July this year, around the same time I noticed all Japanese fonts on my computer.
I also feel there is no reason why I should be having issues in regards to all CA certs on all systems if they wernt corrupt. All the issues seem to stem from corrupt certs I don't even think the ps4 uses them, but over the last few months it nearly always starts with an error regarding CA certs, and that play ready thing in the last image on my tv is apparently a way to create a virtual system and virtual games on a ps4 for advanced Linux users. Half the CMD options are missing and doskeys are always changing etc, keyboard stops working, everything I do is countered with a reaction.
I understand why you feel I'm paranoid, at first so did i, but there is so much data on all my systems to dispute I have no idea where to start, Even my BIOS is no longer the same as what it used to be. There is no doubt what so ever I have either a severe infection and the infection is preventing me from installing an authentic version of windows.
Attachments
If your phone is running on Android operating system then it is normal to have such files. Smart TVs are running on open source software too, so this is quite normal.
No, there is no such thing. Your PC isn't infected. There are rumors about hardware built in malware, but I think it is nonsense and I've never seen anything like it. If you formatted your complete hard drive, infection and all files are wiped out.
I don't know what else to say that has some value. We can go all day like this, but I assure you there is nothing wrong with your PC.
If you still do not trust it, then I suggest to buy a new computer one with pre-installed operating system, so that you can stop worrying about some nonsense.
I respect your opinion and there are cases when people are paranoid, but it is a waste of your time and waste of mine also.
I understand why you feel I'm paranoid, at first so did i, but there is so much data on all my systems to dispute I have no idea where to start, Even my BIOS is no longer the same as what it used to be. There is no doubt what so ever I have either a severe infection and the infection is preventing me from installing an authentic version of windows.
No, there is no such thing. Your PC isn't infected. There are rumors about hardware built in malware, but I think it is nonsense and I've never seen anything like it. If you formatted your complete hard drive, infection and all files are wiped out.
I don't know what else to say that has some value. We can go all day like this, but I assure you there is nothing wrong with your PC.
If you still do not trust it, then I suggest to buy a new computer one with pre-installed operating system, so that you can stop worrying about some nonsense.
I respect your opinion and there are cases when people are paranoid, but it is a waste of your time and waste of mine also.
You may also like...
-
-
Malware News Cracking ValleyRAT: From Builder Secrets to Kernel Rootkits
- Started by Khushal
- Replies: 1
-
anyone could help me with FRST ?
- Started by nazrinlsl
- Replies: 3
-
-
Serious Discussion Norton Full and Quick scans speed does not improve over time.
- Started by Divine_Barakah
- Replies: 14