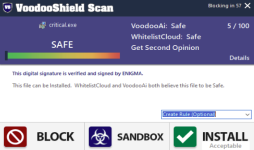
Yeah, it looks like tretg45 blew right past everything, including SS. Like I was saying in post #9, signed files that are valid and verified are extremely difficult to detect as malware pre-execution. Especially if you are running VS on AutoPilot, it really needs to be paired with a robust AV with post-execution mitigations. This file probably would have bypassed AutoPilot even on the Aggressive security posture. If you guys happen to test this as well, please let me know.
The good news is... at least this confirms that malware detection has not sufficiently advanced to the point to where we do not need to lock our computers (with an initial non-affirmative mini prompt of course)

.
We could test VS in the default aggressive modes and security postures, but how much fun would that be?

. I imagine most people are curious how well VS does when set to the least aggressive modes and security postures, but if this is not the case, maybe users can suggest how they would like to see VS configured while testing. Thank you guys for testing! If anyone testing needs a Pro license, please PM me.