shmu26
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
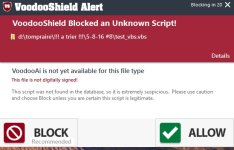
the dev recently revealed a little bit about how VS handles this.
This is the gist of it:
"the way vulnerable processes are handled in VS is ... every executable file in windows was considered a vulnerable process (along with the other standard vulnerable processes, like java and flash), and these vulnerable process are only blocked when they are child processes of web apps. "
(bold is from me, not from original quote)
VoodooShield ?
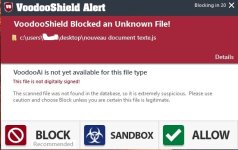
second link is the dev's further clarifications:
VoodooShield ?
I would be interested to hear what people think about this approach.
I personally am a little concerned, as it seems that VS is not protecting these processes as vigilantly as other anti-exe programs do. I am interested in your thoughts.
This is the gist of it:
"the way vulnerable processes are handled in VS is ... every executable file in windows was considered a vulnerable process (along with the other standard vulnerable processes, like java and flash), and these vulnerable process are only blocked when they are child processes of web apps. "
(bold is from me, not from original quote)
VoodooShield ?
second link is the dev's further clarifications:
VoodooShield ?
I would be interested to hear what people think about this approach.
I personally am a little concerned, as it seems that VS is not protecting these processes as vigilantly as other anti-exe programs do. I am interested in your thoughts.