- Jan 4, 2016
- 1,022
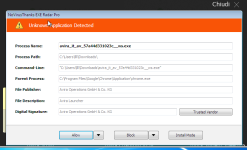
Good morning, I'm looking for a Good free security software, that should be used with Windows defender to prevent inexperienced users to get infected (basically, locking down the computer). I'm looking for a secure product (it should protect against zero-day ransomware, other malware,adware and also office macros). The product should be light, no great impact on boot-time and computer performance. Considering this will be used by inexperienced people, once set, the product should work mostly automatically without puzzling the user . I chose Voodooshield, Secure A plus and COMODO firewall, which seem the most secure to me. If you would like to recommend an other product, please tell me. Waiting for your suggestions, Thanks in advance
Last edited: