- Aug 6, 2014
- 1,044
On April 2, 2016, Proofpoint researchers discovered that the Magnitude exploit kit (EK) [1] was successfully exploiting Adobe Flash version 20.0.0.306. Because the Magnitude EK in question did not direct any exploits to Flash 21.0.0.182, we initially suspected that the exploit was for CVE-2016-1001 as in Angler [2], the combination exploit "CVE-2016-0998/CVE-2016-0984" [3], or CVE-2016-1010.
In the course of our investigation, we shared our findings with fellow researchers in the security community in order to accelerate identification of the exploit. A colleague at FireEye determined [4] that the exploited vulnerability was unknown. Adobe was promptly notified of the issue, and they verified that although a mitigation integrated in 21.0.0.182 appeared to cause the exploit to fail, it was a previously unreported vulnerability and assigned it CVE-2016-1019. An emergency patch for the vulnerability was released on April 7 [5].
Despite the fact that this new exploit could potentially work on any version of Adobe Flash, including a fully patched instance of Flash, the threat actors implemented it in a manner that only targeted older versions of Flash. In other words, equipped with a weapon that could pierce even the latest armor, they only used it against old armor, and in doing so exposed to security researchers a previously unreported vulnerability. We refer to this type of faulty implementation as a “degraded” mode, and it is something that we have observed in the past with CVE-2014-8439 [6] [7] and CVE-2015-0310 [8] in Angler. While there will be a period of time when systems are not yet patched for CVE-2016-1019 and thus vulnerable to new exploits, “degraded” implementations of potential zero-day exploits offer security researchers and vendors a valuable opportunity to identify and mitigate previously unknown vulnerabilities.
Let’s look at this ‘degraded’ implementation of CVE-2016-1019 in action:
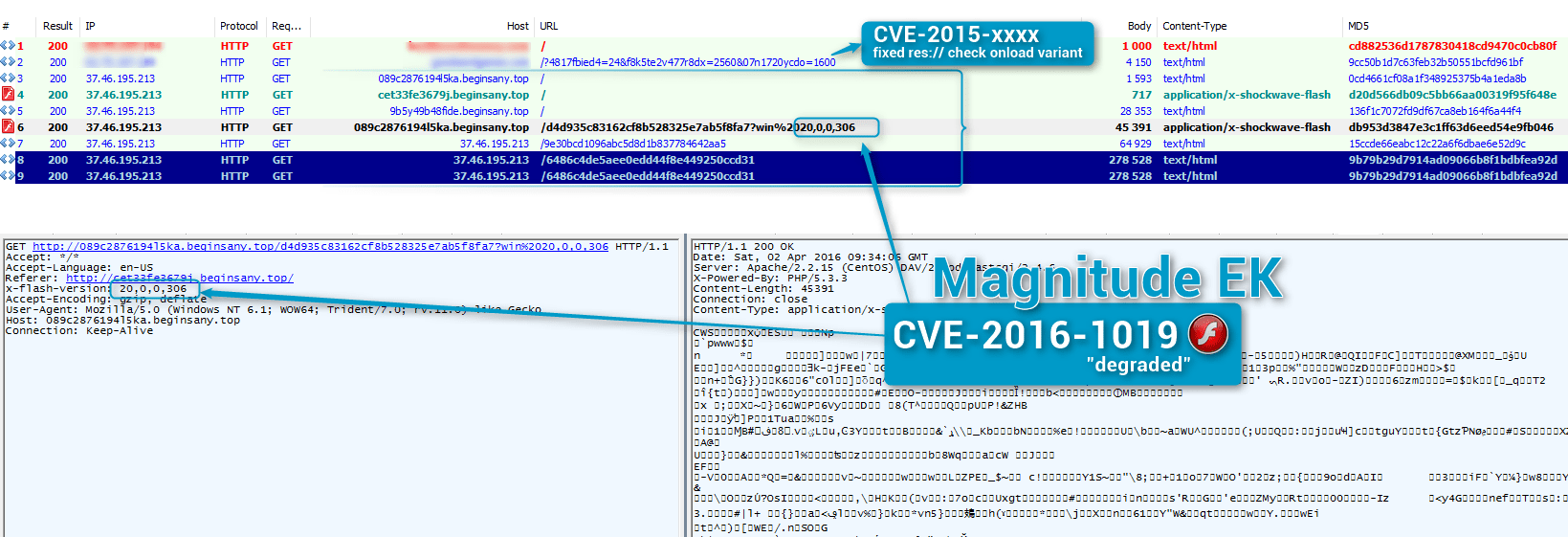
Figure 1: 2016-04-02 Magnitude exploiting CVE-2016-1019 in “degraded” mode to spread Cerber ransomware
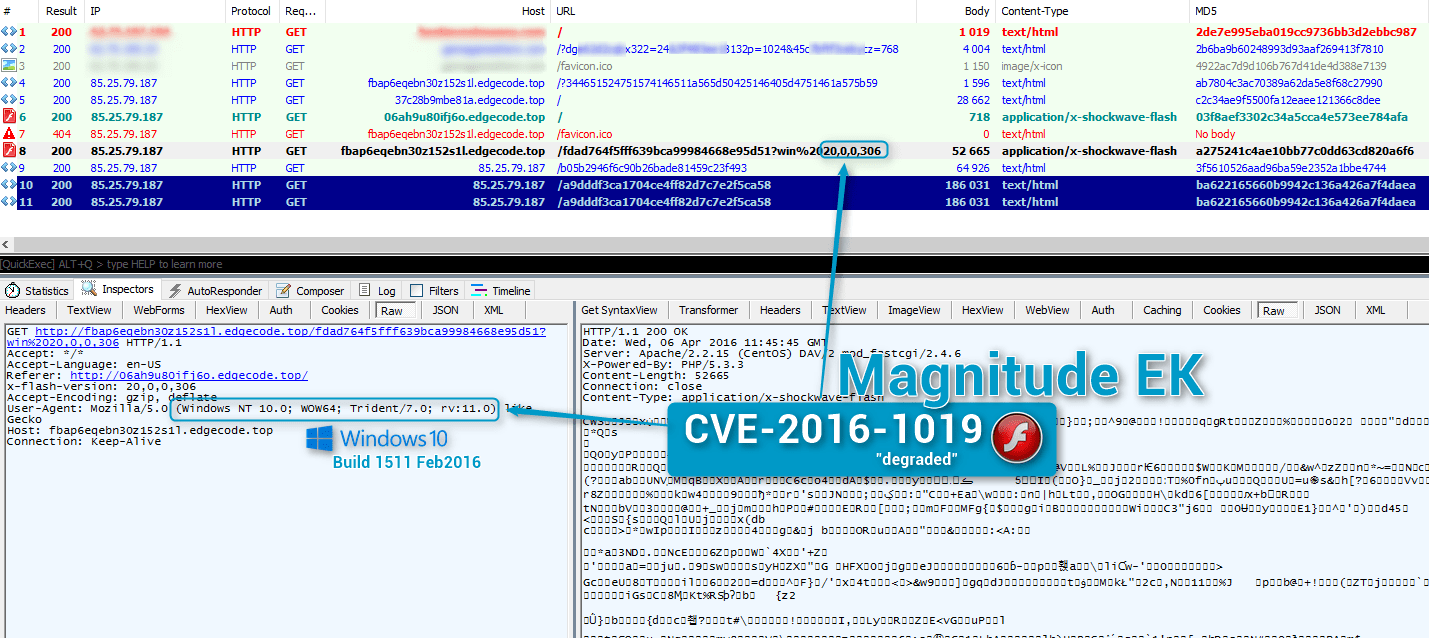
Figure 2 : 2016-04-06 Magnitude exploiting CVE-2016-1019 in “degraded” mode on Windows 10 build 1511 (Feb 2016) with Flash 20.0.0.306
Payloads
In recent months, Magnitude seems to be used by only one actor, who was spreading Cryptowall crypt1001 until the middle of March 2016. The actor then switched to distributing Teslacrypt ID=39, and since the end of March has switched to distributing Cerber [9].
We looked back at a Nuclear Pack Flash exploit move we spotted on March 31, 2016. As we did not witness a new Flash version being exploited, we did not investigate before but the embedded exploit is the same as that discovered in Magnitude (CVE-2016-1019) according to Anton Ivanov (Kaspersky), and researchers at ESET and FireEye.
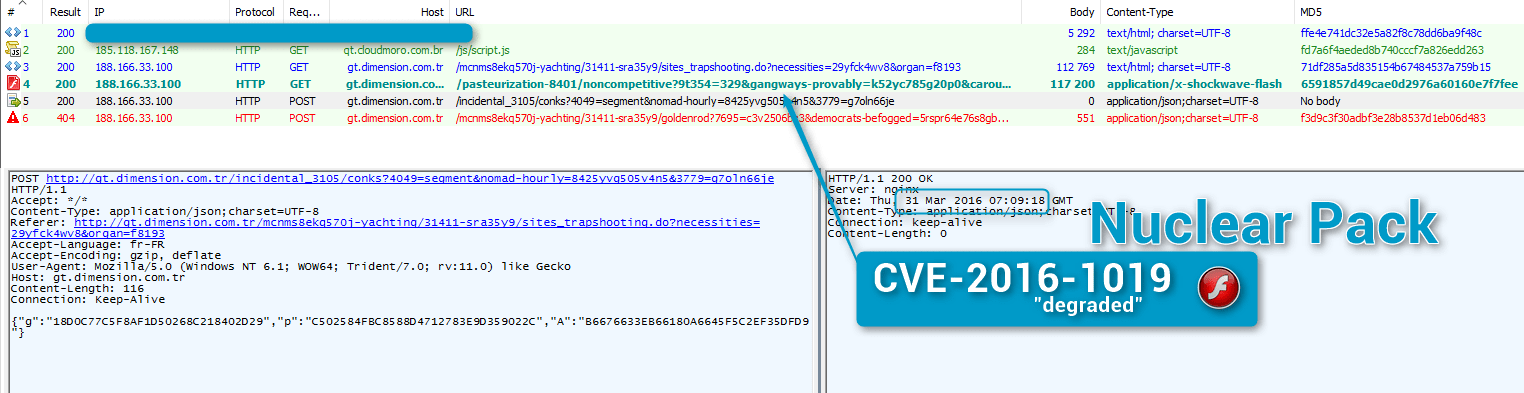
Figure 3: 2016-03-31 Nuclear Pack not exploiting Flash 20.0.0.306 despite integrating CVE-2016-1019 code (that is, not dropping the expected Locky or Necurs from the actor behind this infection chain [10])
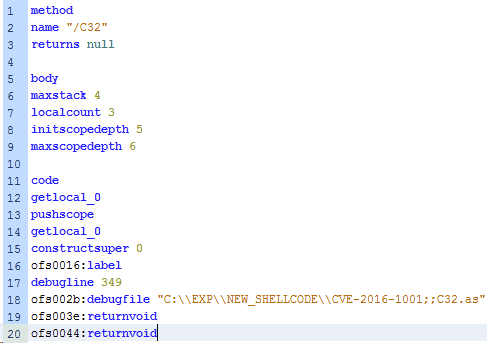
Figure 4: Intriguing CVE-2016-1001 string spotted by Denis O'Brien (Malwageddon), the 2016-04-05 in Nuclear Pack exploit
Summarizing the main findings of this analysis:
In the course of our investigation, we shared our findings with fellow researchers in the security community in order to accelerate identification of the exploit. A colleague at FireEye determined [4] that the exploited vulnerability was unknown. Adobe was promptly notified of the issue, and they verified that although a mitigation integrated in 21.0.0.182 appeared to cause the exploit to fail, it was a previously unreported vulnerability and assigned it CVE-2016-1019. An emergency patch for the vulnerability was released on April 7 [5].
Despite the fact that this new exploit could potentially work on any version of Adobe Flash, including a fully patched instance of Flash, the threat actors implemented it in a manner that only targeted older versions of Flash. In other words, equipped with a weapon that could pierce even the latest armor, they only used it against old armor, and in doing so exposed to security researchers a previously unreported vulnerability. We refer to this type of faulty implementation as a “degraded” mode, and it is something that we have observed in the past with CVE-2014-8439 [6] [7] and CVE-2015-0310 [8] in Angler. While there will be a period of time when systems are not yet patched for CVE-2016-1019 and thus vulnerable to new exploits, “degraded” implementations of potential zero-day exploits offer security researchers and vendors a valuable opportunity to identify and mitigate previously unknown vulnerabilities.
Let’s look at this ‘degraded’ implementation of CVE-2016-1019 in action:

Figure 1: 2016-04-02 Magnitude exploiting CVE-2016-1019 in “degraded” mode to spread Cerber ransomware

Figure 2 : 2016-04-06 Magnitude exploiting CVE-2016-1019 in “degraded” mode on Windows 10 build 1511 (Feb 2016) with Flash 20.0.0.306
Payloads
In recent months, Magnitude seems to be used by only one actor, who was spreading Cryptowall crypt1001 until the middle of March 2016. The actor then switched to distributing Teslacrypt ID=39, and since the end of March has switched to distributing Cerber [9].
We looked back at a Nuclear Pack Flash exploit move we spotted on March 31, 2016. As we did not witness a new Flash version being exploited, we did not investigate before but the embedded exploit is the same as that discovered in Magnitude (CVE-2016-1019) according to Anton Ivanov (Kaspersky), and researchers at ESET and FireEye.

Figure 3: 2016-03-31 Nuclear Pack not exploiting Flash 20.0.0.306 despite integrating CVE-2016-1019 code (that is, not dropping the expected Locky or Necurs from the actor behind this infection chain [10])

Figure 4: Intriguing CVE-2016-1001 string spotted by Denis O'Brien (Malwageddon), the 2016-04-05 in Nuclear Pack exploit
Summarizing the main findings of this analysis:
- Magnitude EK was found to be exploiting a previously unreported vulnerability in Adobe Flash, now assigned CVE-2016-1019.
- Due to a faulty implementation of the exploit, it was not targeting the latest, fully patched versions of Adobe Flash in a way that could result in infection.
- The exploit has been in the wild since at least March 31, 2016.
- The exploit was observed spreading the Cerber and Locky ransomware, among others.
- There is evidence that Nuclear Pack was also equipped with code to exploit CVE-2016-1019 but did not run it against fully patched systems.
- Adobe has issued an emergency patch and advisory (APSA16-01) for this vulnerability.