As it was said, on Monday many workers will come to work and find their computers encrypted. I wanted to check if they will pay hackers. I had a look on three Bitcoin wallets of WanaCry and noticed that during Monday the amount of money significantly increased.
One of the wallets even increased by almost a half before the noon.
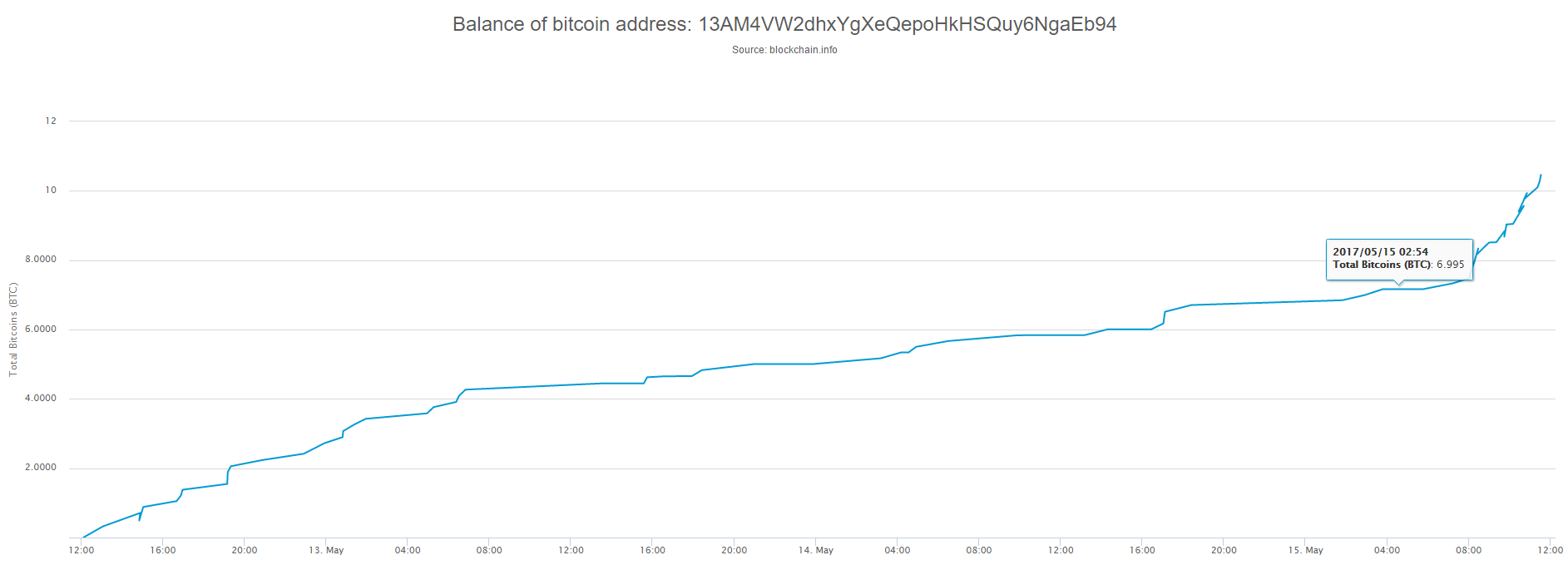
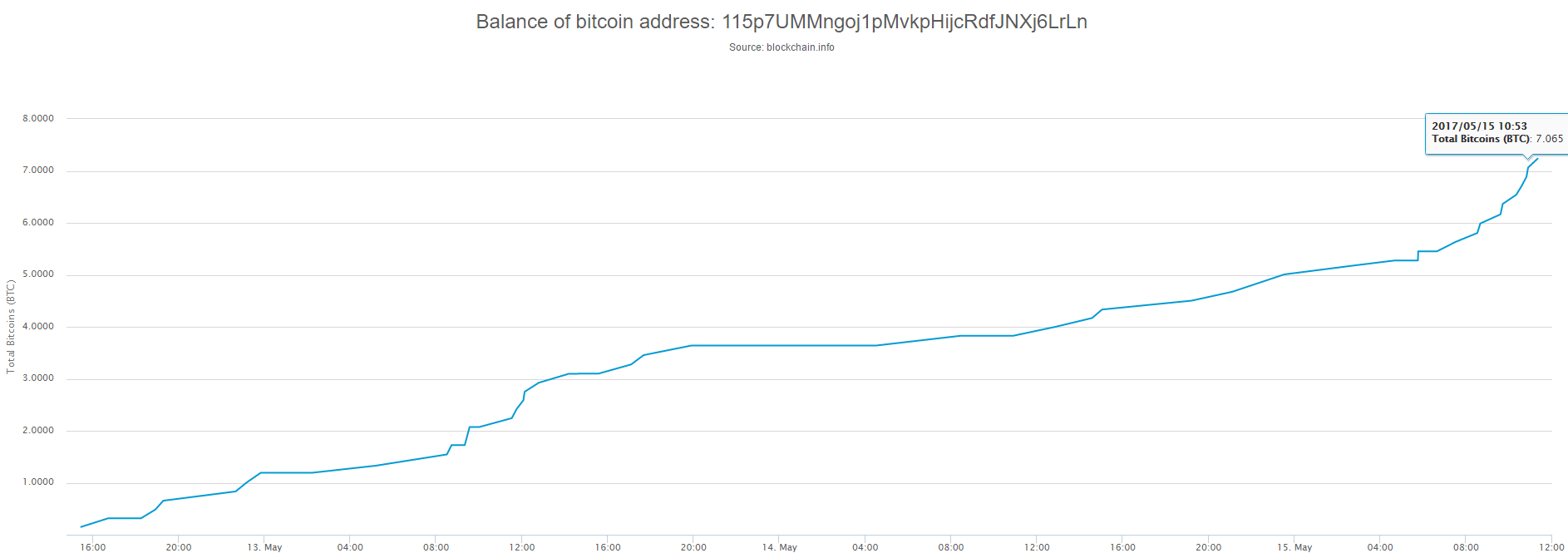
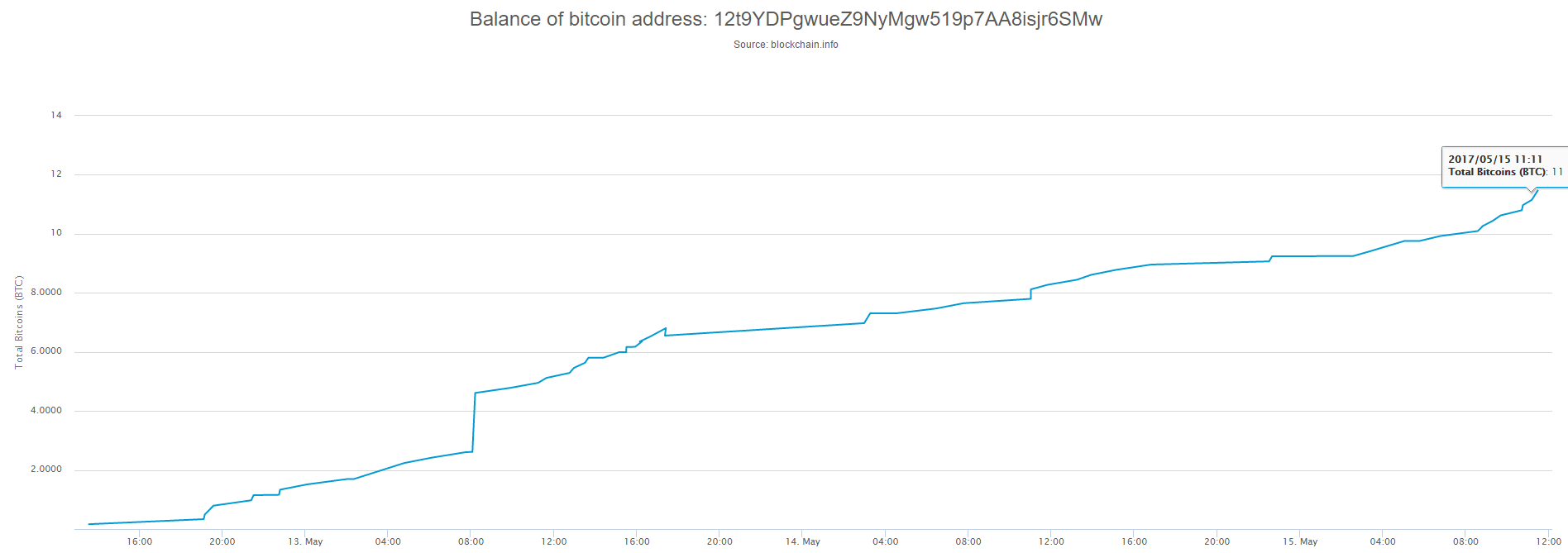
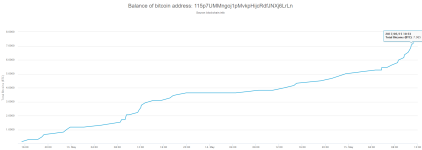
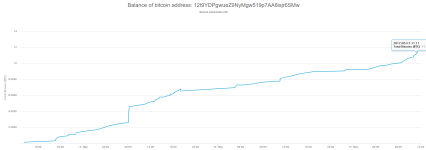
One of the wallets even increased by almost a half before the noon.


