D
Deleted member 21043
Thread author
Hello everyone,
Thought it was time I made another Malware Analysis thread. So here I am, with another.
In this thread, it will be mainly focused on using a Web Debugger (proxy) tool whilst analysing a malware sample. The reason that a Process Monitor is included in this thread is to help get people used to knowing that a Process Monitor is important; it will allow you to know when a sample is running, when a sample is terminated... And possibly other information: if the CPU usage is high, then it must be doing something. This can include basic I/O tasks, making connections,... Of course a low CPU usage does not represent the sample is doing nothing, however seeing a process use a high CPU usage does give you a better message of if it's doing something.
The Process Monitoring tool I will be using in this thread is Sysinternals Process Explorer. You can download it at the following URL (for free): https://technet.microsoft.com/en-us/sysinternals/bb896653.aspx
You can view my thread on Process Monitoring at the following URL: http://malwaretips.com/threads/monitoring-processes-short-introduction-malware-analysis.44350/
The Web Debugger (proxy) I will be using in this thread is Fiddler, provided by Telerik. You can download it at the following URL (for free): http://www.telerik.com/fiddler
You will need to download both programs: Process Explorer is portable however Fiddler requires installation.
WARNING: In this thread I will be executing malware samples live. Please make sure that if you choose to download the malware samples and execute them, you are running a Virtual Machine. You can download the sample I will be working with in this thread from the following URL: http://malwaretips.com/threads/2015-04-02-2.44361/
The sample came from a pack which @Petrovic caught, and uploaded onto the Malware Hub. The thread URL is shown in the above warning.
I uploaded the av.exe sample to the Malware Hub since it wasn't already there after receiving it being downloaded from 1.scr from the pack @Petrovic uploaded the other day.
There are 2 samples in this pack. We will be using 1.scr. I may release a thread which will involve 2.exe somehow. (If I do I will update this thread with the link where this text is for the 2.exe analysis).
Now we've got that out of the way, let's get into the Malware Analysis!
---------------------------------------------------------------------
First, you'll need to download the sample and extract it to a folder. Preferably to the Desktop.
After the sample 1.scr has been extracted from the archive, you will need to open up Process Explorer and Fiddler.
To view what my Process Explorer and Fiddler looks like, open up the following spoiler:
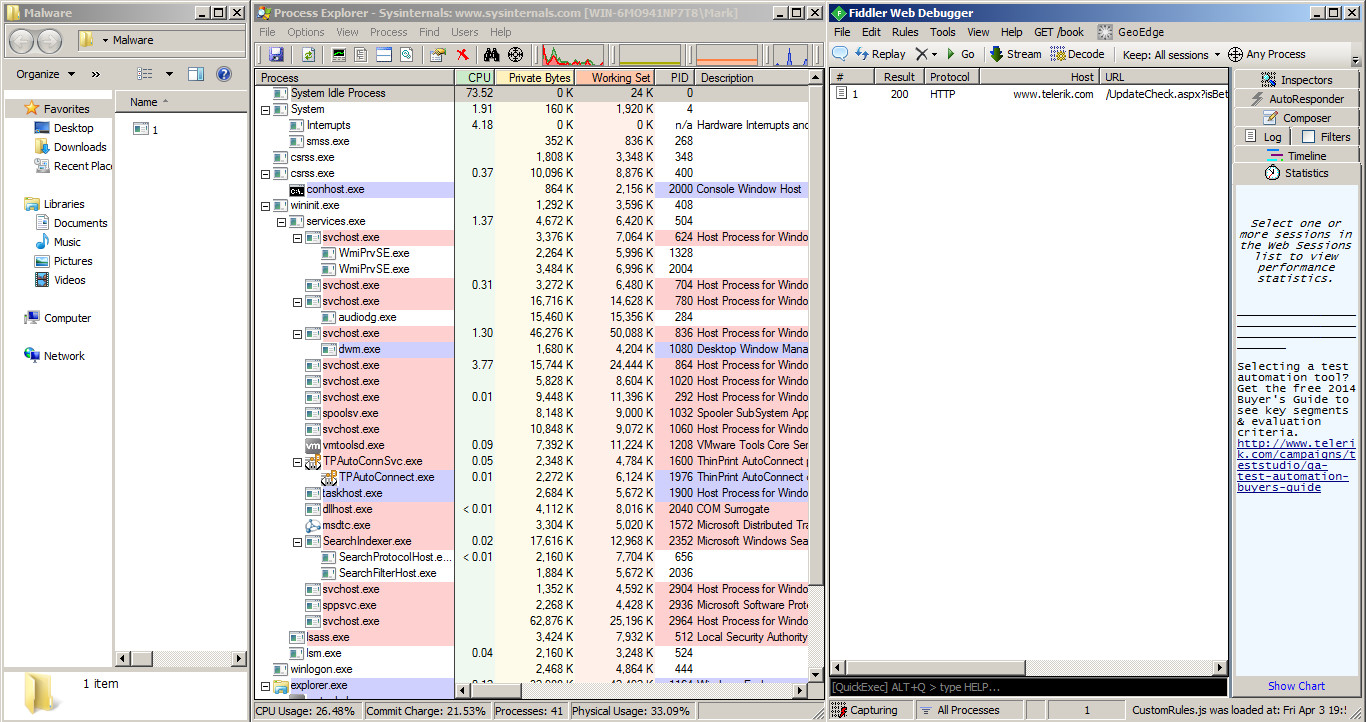
I know... My screen is a bit squashed.
Anyway, before I execute the sample I want to mention some things about Fiddler. Not everything since I will be covering more as we use it in other threads, but only the necessary parts for the purpose of this thread:
Fiddler is a Web Debugging tool. Fiddler will be able to record sessions from the running processes created a HTTP proxy. It's linked to wininet.dll (this is also used by Internet Explorer...).
Feel free to open up your webbrowser and navigate to a URL, let's use https://www.google.co.uk as an example. As you will see in Fiddler, the session will be captured and logged into the Session view. In the below spoiler I will show you an screenshot of this session being captured. The "session view", is where the colums are and the information is logged in that white space:
That's all I will mention in this thread about Fiddler. In future threads where Fiddler is used I will mention and make use of the other features (if it is used).
Let's continue to where we left off:
Execute the sample 1.scr.
In Process Explorer you should see 1.scr execute (see spoiler)

Hold on, if you checked the spoiler you should see something strange. 1.scr did execute, however there is another process started by 1.scr called "winmgr.exe"? Yes, this was dropped by the sample. We can see it was dropped by looking at the file path shown in Process Explorer:
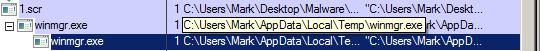
As we saw in the screenshot in the spoiler directly above, there are now 2 instances of winmgr.exe running.
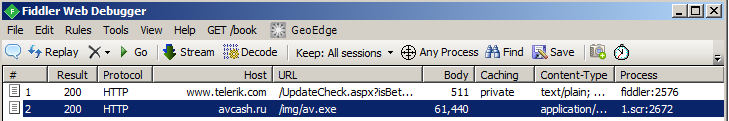
Let's take a look back over at our Fiddler Web Debugging logs... You should see a new session logged (protocl should be HTTP) going to the host: avcash.ru. The full URL is: hxxp://xxx.avcash.ru/img/av.exe (replace xxx with w)
It will download this executable. av.exe
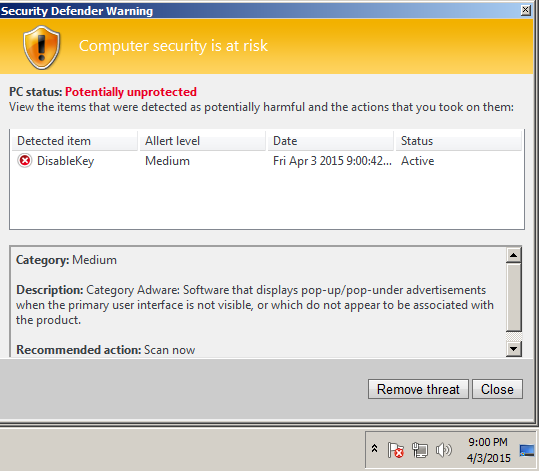
If we let the processes work for a few minutes, you should see a popup like this afterwards:
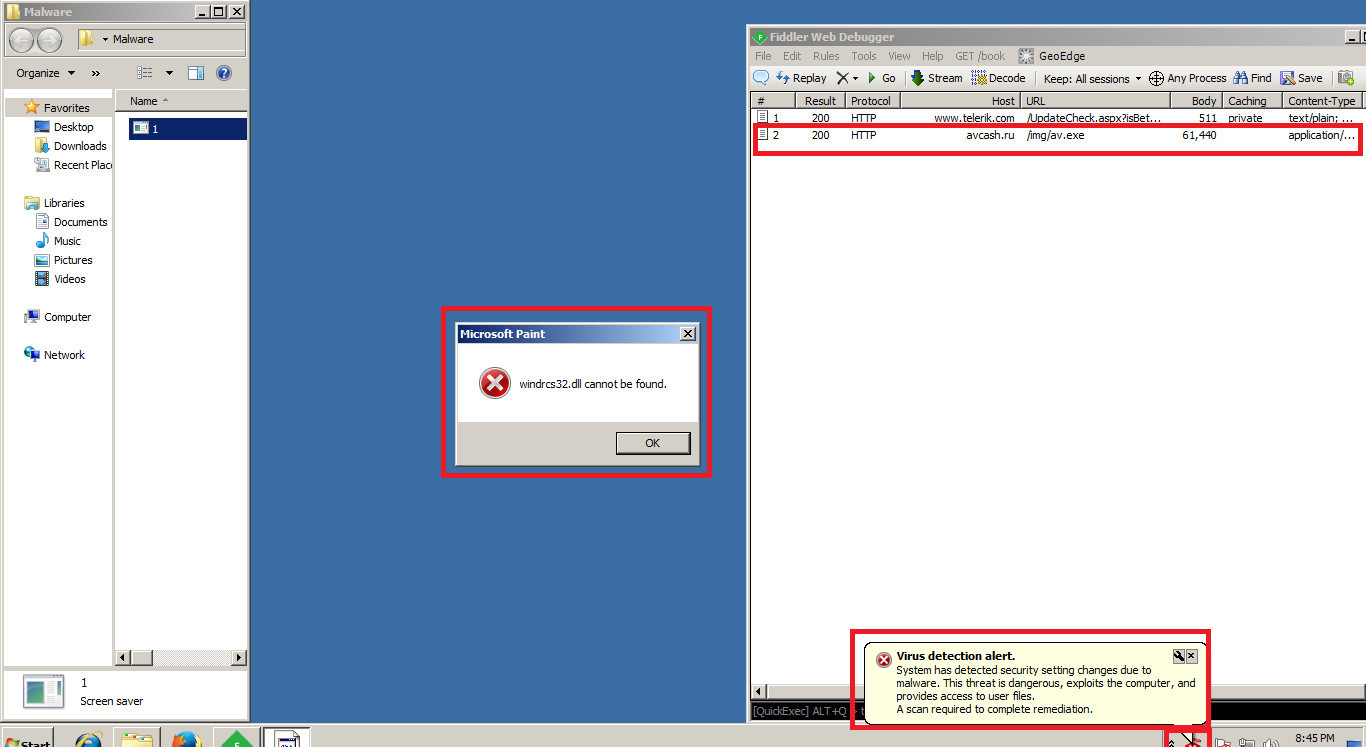
Process Explorer should have been terminated. As well as this, it should have been deleted. This is a reason why you should always have a backup process monitor, also. However, such actions are already suspicious.
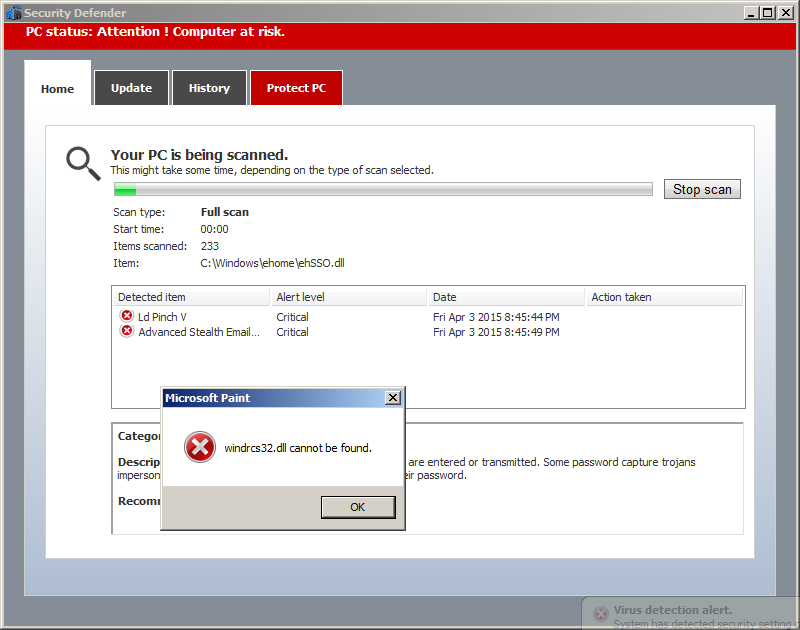
The alert at the bottom is not Windows Defender. If you thought it was, well welcome to the world of Malware (this time we are dealing with a Fake Antivirus (Trojan).
As we can see another alert with the caption "Microsoft Paint", and the contents about a file not being able to be found. This time it's a MsgBoxA alert (in other words, a Message Box is what we call this alert (the one with the error icon regarding Microsoft Paint)).
After this, another window should open. You can see some more screenshots (multiple screenshots) in the following spoiler:
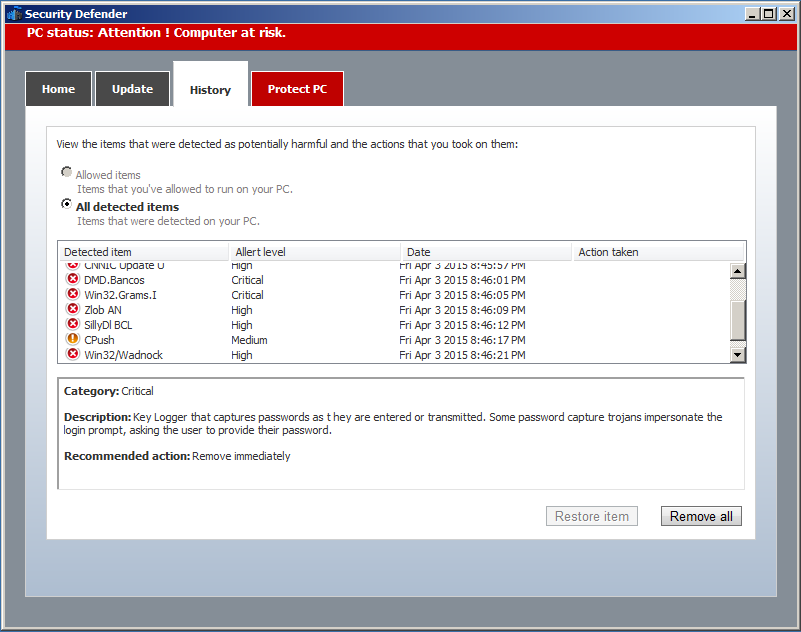
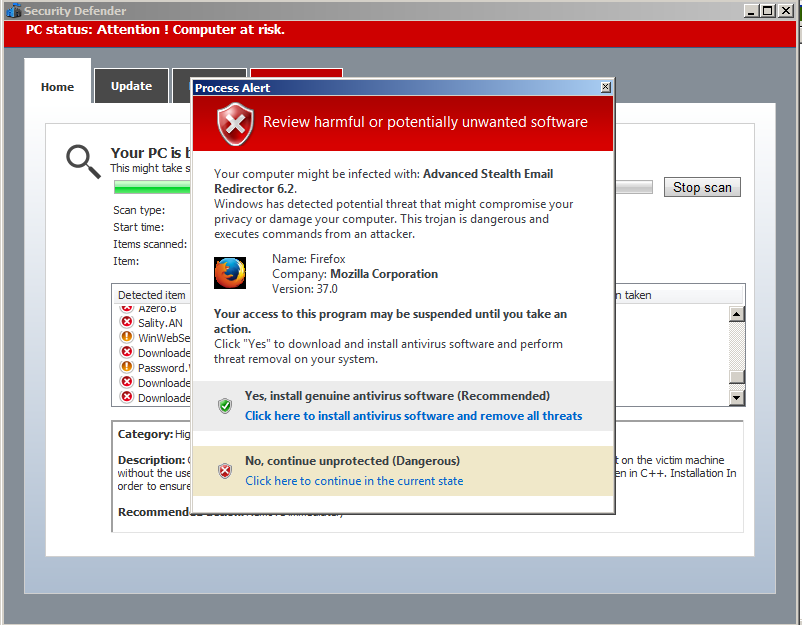
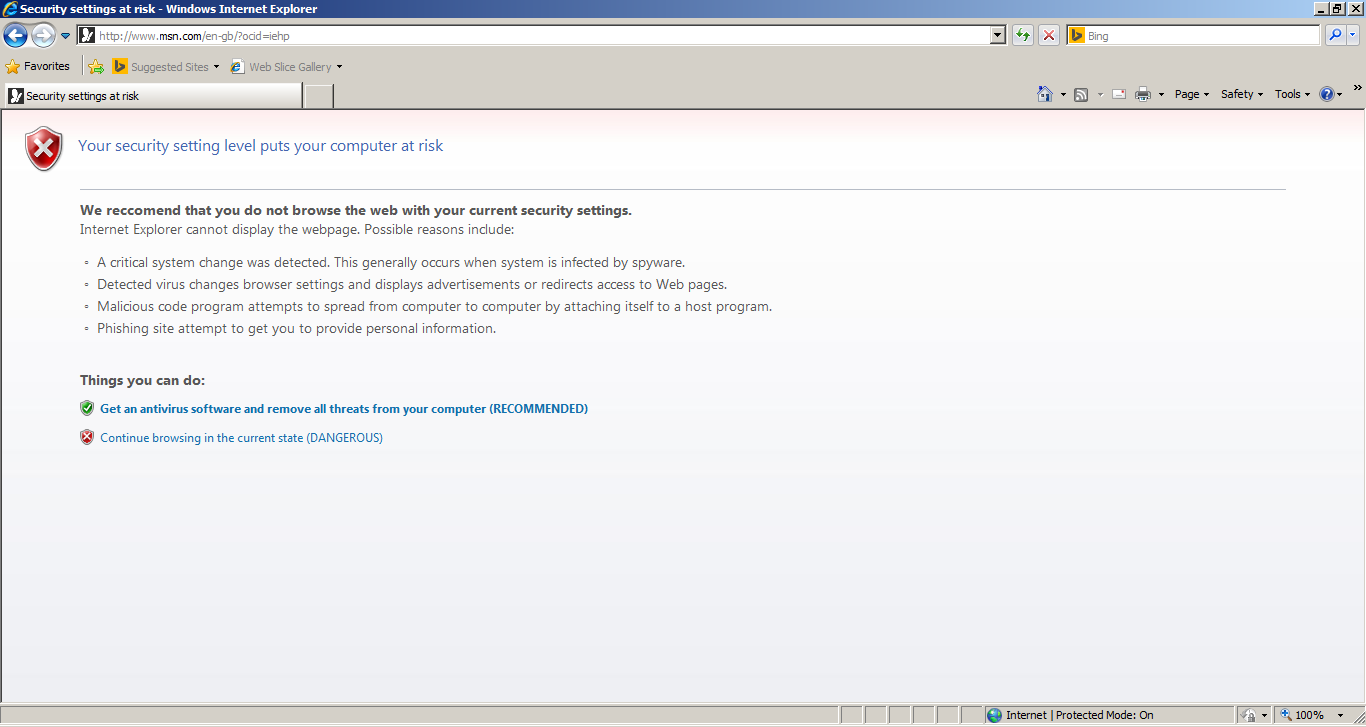
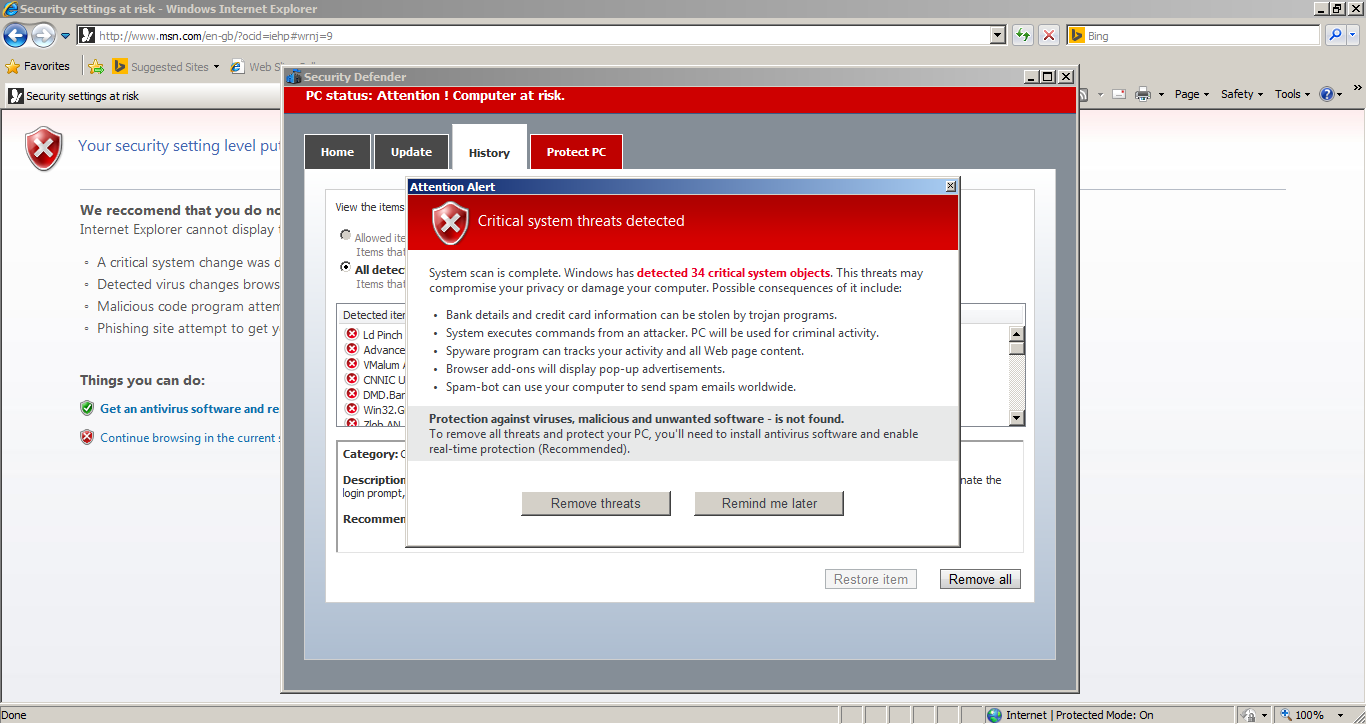
As we saw in the screenshots above... It will also try to prevent you from opening some applications, and display an alert about how they are 'harmful or potentially unwanted'. Haha, maybe the developer messed up with that one and was talking about his own program... We can also see other things such as fake detections. Check the screenshots above for more information.
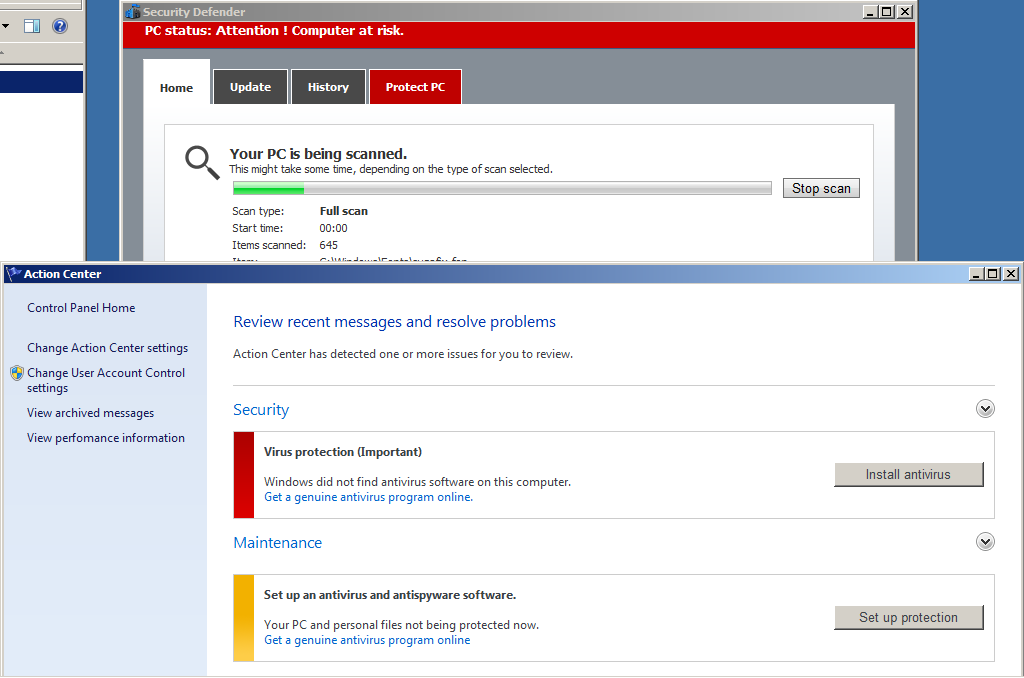
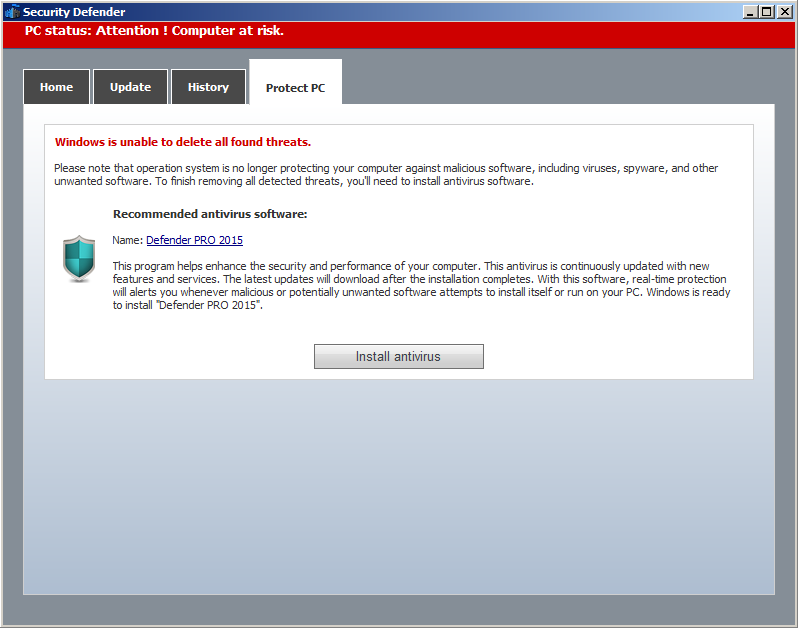
We also see it hijacked the webbrowser. It will try to prevent you from using the web (unless it's to purchase the fake AV it promotes called Defender Pro 2015 (soon I will make a thread on this - analysis of course... And when I do, introducing new Malware Analysis tools...).
This fake AV will also clear out files on your system. For example, my whole folder of analysis tools, and various other areas. This is why you should have a read-only (write protected) USB device containing all the necessary analysis tools for the VM. I will also make a thread about how you can do this. Don't worry, I have a few more threads to make and they should be out within the next few days. : )
NOTE: It will try to keep certain programs closed to prevent you from closing it's processes.
Well, all well and good... I shall be using that snapshot on the Virtual Machine made before this thread.
Before I leave today, I will like to say that I hope this thread was helpful to some (of course some may already know everything in this thread which I have written) and that Fiddler can be very useful. Fiddler is especially useful when trying to identify if a sample is a Trojan Clicker.
Cheers.
Thought it was time I made another Malware Analysis thread. So here I am, with another.
In this thread, it will be mainly focused on using a Web Debugger (proxy) tool whilst analysing a malware sample. The reason that a Process Monitor is included in this thread is to help get people used to knowing that a Process Monitor is important; it will allow you to know when a sample is running, when a sample is terminated... And possibly other information: if the CPU usage is high, then it must be doing something. This can include basic I/O tasks, making connections,... Of course a low CPU usage does not represent the sample is doing nothing, however seeing a process use a high CPU usage does give you a better message of if it's doing something.
The Process Monitoring tool I will be using in this thread is Sysinternals Process Explorer. You can download it at the following URL (for free): https://technet.microsoft.com/en-us/sysinternals/bb896653.aspx
You can view my thread on Process Monitoring at the following URL: http://malwaretips.com/threads/monitoring-processes-short-introduction-malware-analysis.44350/
The Web Debugger (proxy) I will be using in this thread is Fiddler, provided by Telerik. You can download it at the following URL (for free): http://www.telerik.com/fiddler
You will need to download both programs: Process Explorer is portable however Fiddler requires installation.
WARNING: In this thread I will be executing malware samples live. Please make sure that if you choose to download the malware samples and execute them, you are running a Virtual Machine. You can download the sample I will be working with in this thread from the following URL: http://malwaretips.com/threads/2015-04-02-2.44361/
The sample came from a pack which @Petrovic caught, and uploaded onto the Malware Hub. The thread URL is shown in the above warning.
I uploaded the av.exe sample to the Malware Hub since it wasn't already there after receiving it being downloaded from 1.scr from the pack @Petrovic uploaded the other day.
There are 2 samples in this pack. We will be using 1.scr. I may release a thread which will involve 2.exe somehow. (If I do I will update this thread with the link where this text is for the 2.exe analysis).
Now we've got that out of the way, let's get into the Malware Analysis!
---------------------------------------------------------------------
First, you'll need to download the sample and extract it to a folder. Preferably to the Desktop.
After the sample 1.scr has been extracted from the archive, you will need to open up Process Explorer and Fiddler.
To view what my Process Explorer and Fiddler looks like, open up the following spoiler:

I know... My screen is a bit squashed.
Anyway, before I execute the sample I want to mention some things about Fiddler. Not everything since I will be covering more as we use it in other threads, but only the necessary parts for the purpose of this thread:
Fiddler is a Web Debugging tool. Fiddler will be able to record sessions from the running processes created a HTTP proxy. It's linked to wininet.dll (this is also used by Internet Explorer...).
Feel free to open up your webbrowser and navigate to a URL, let's use https://www.google.co.uk as an example. As you will see in Fiddler, the session will be captured and logged into the Session view. In the below spoiler I will show you an screenshot of this session being captured. The "session view", is where the colums are and the information is logged in that white space:
I expanded my Fiddler window and went to https://www.google.co.uk using Firefox. This was the result:
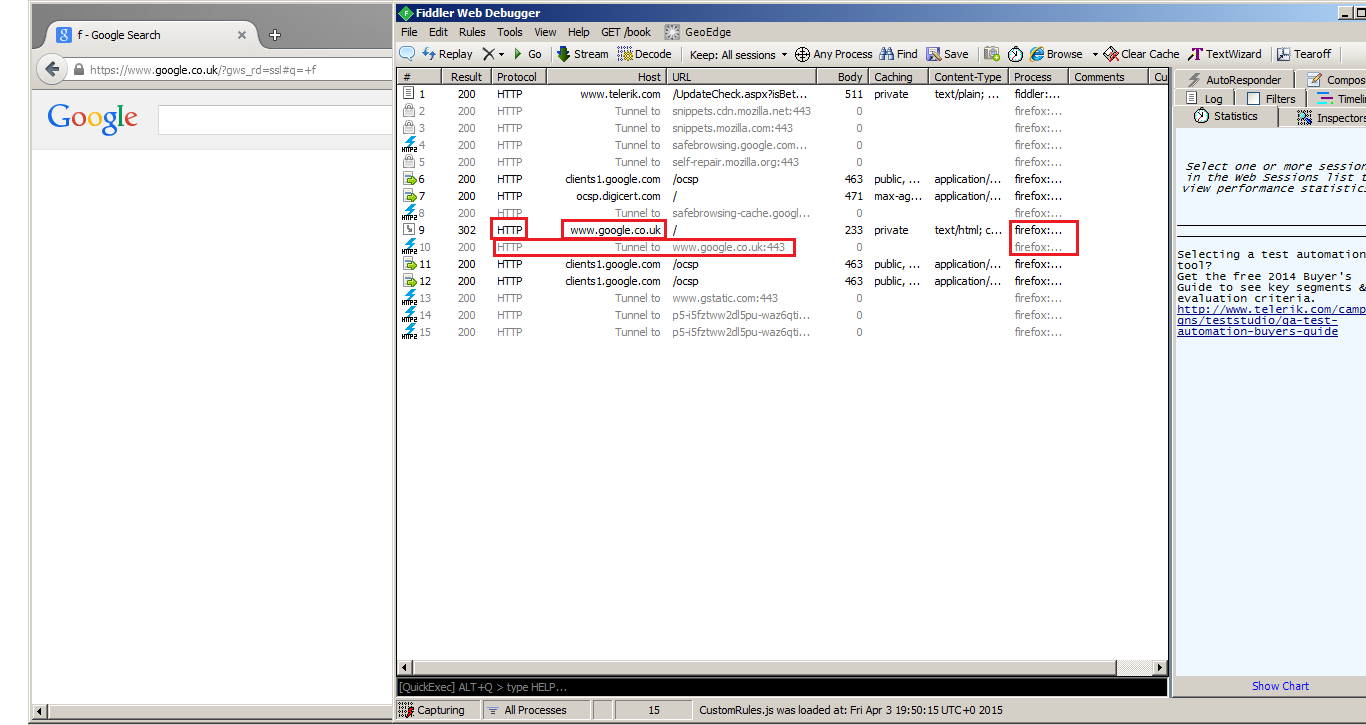
As we can see in the above screenshot, Fiddler captured the session between the Firefox browser and the website. It managed to record that there was a HTTP Protocol ongoing, the Host/URL was www.google.co.uk/ and the Process behind it (which in this case is firefox process name).
On the right you will find things like the AutoResponder (where you can send back to the server), the Statistics (which will show statistic information such as the Bytes sent and Received),...

As we can see in the above screenshot, Fiddler captured the session between the Firefox browser and the website. It managed to record that there was a HTTP Protocol ongoing, the Host/URL was www.google.co.uk/ and the Process behind it (which in this case is firefox process name).
On the right you will find things like the AutoResponder (where you can send back to the server), the Statistics (which will show statistic information such as the Bytes sent and Received),...
That's all I will mention in this thread about Fiddler. In future threads where Fiddler is used I will mention and make use of the other features (if it is used).
Let's continue to where we left off:
Execute the sample 1.scr.
In Process Explorer you should see 1.scr execute (see spoiler)

Hold on, if you checked the spoiler you should see something strange. 1.scr did execute, however there is another process started by 1.scr called "winmgr.exe"? Yes, this was dropped by the sample. We can see it was dropped by looking at the file path shown in Process Explorer:

As we saw in the screenshot in the spoiler directly above, there are now 2 instances of winmgr.exe running.
Let's take a look back over at our Fiddler Web Debugging logs... You should see a new session logged (protocl should be HTTP) going to the host: avcash.ru. The full URL is: hxxp://xxx.avcash.ru/img/av.exe (replace xxx with w)
It will download this executable. av.exe

If we let the processes work for a few minutes, you should see a popup like this afterwards:

Process Explorer should have been terminated. As well as this, it should have been deleted. This is a reason why you should always have a backup process monitor, also. However, such actions are already suspicious.
The alert at the bottom is not Windows Defender. If you thought it was, well welcome to the world of Malware (this time we are dealing with a Fake Antivirus (Trojan).
As we can see another alert with the caption "Microsoft Paint", and the contents about a file not being able to be found. This time it's a MsgBoxA alert (in other words, a Message Box is what we call this alert (the one with the error icon regarding Microsoft Paint)).
After this, another window should open. You can see some more screenshots (multiple screenshots) in the following spoiler:








As we saw in the screenshots above... It will also try to prevent you from opening some applications, and display an alert about how they are 'harmful or potentially unwanted'. Haha, maybe the developer messed up with that one and was talking about his own program... We can also see other things such as fake detections. Check the screenshots above for more information.
We also see it hijacked the webbrowser. It will try to prevent you from using the web (unless it's to purchase the fake AV it promotes called Defender Pro 2015 (soon I will make a thread on this - analysis of course... And when I do, introducing new Malware Analysis tools...).
This fake AV will also clear out files on your system. For example, my whole folder of analysis tools, and various other areas. This is why you should have a read-only (write protected) USB device containing all the necessary analysis tools for the VM. I will also make a thread about how you can do this. Don't worry, I have a few more threads to make and they should be out within the next few days. : )
NOTE: It will try to keep certain programs closed to prevent you from closing it's processes.
Well, all well and good... I shall be using that snapshot on the Virtual Machine made before this thread.
Before I leave today, I will like to say that I hope this thread was helpful to some (of course some may already know everything in this thread which I have written) and that Fiddler can be very useful. Fiddler is especially useful when trying to identify if a sample is a Trojan Clicker.
Cheers.
Last edited by a moderator: