D
Deleted member 21043
Thread author
Hi everyone,
This thread will be quite simple. About at least 90-95% of the people reading this will know how to monitor processes on the system, however that last 5% may not which is why I am making this thread.
A very important thing during Malware Analysis is to monitor the processes. This helps I see when the target sample is executing, when it is terminated, watch for any other processes which it may start up and as well as this, we can also see the CPU usage to the process which does give us a idea of if it's doing something at that time.
For example, if it's writing files to the disk then the CPU% for that process will increase. Or if it's constantly checking if another process (let's say it drops another process which does the work) is open and if not to start it then the CPU will increase.
We will be using Process Explorer for the purpose of this thread. I'd like to note that there are many process monitors out there (there is one in the Malcode Analysts Pack, there is Process Hacker,... I am sure you can all find a lot and many different ones out there), however we will be using Sysinternals Process Explorer for this thread to get started.
You need to download Sysinternals Process Explorer from Microsoft TechNet from the following URL: https://technet.microsoft.com/en-us/sysinternals/bb896653.aspx
Once it has completed downloading, extract it. I recommend placing it somewhere on the Desktop for easy access. Or a folder combined with many different Analysis tools called "AnalysisTools".
After the extraction is complete, open up the extracted folder. There should be a executable in that folder called "procexp.exe". Open it up (as Administrator).
The first time you run Process Explorer you will be shown License Agreement for using the program. If you want to use Process Explorer you must Agree to it. Read through the License Agreement and then choose to Accept or not.
Process Explorer should look like as below:
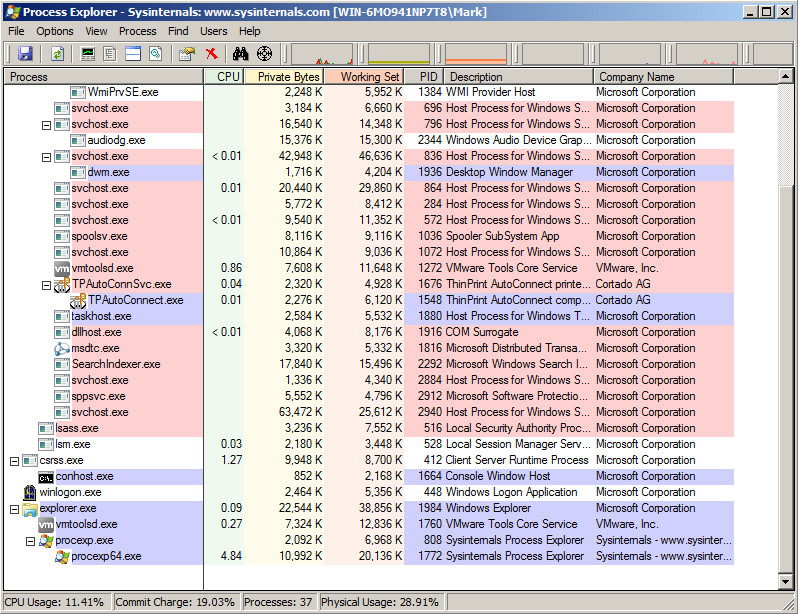
The Process Explorer UI is quite simple and straight forward. You are shown the processes, along with other information corrosponding to them such as: CPU, Private Bytes, Working Set, PID, Description and the Company Name (based on the File Information). You can add and remove colums if you wish. To do this, see the following spoiler.
Now customization is out the way, let's actually see if we can find some information out on a new process being created with Sysinternals Process Explorer!
Scroll down to the end of Process Explorer processes list. Any new processes will be made at the end.
Open up any program on the system. This could be Internet Explorer, for example. I will open Internet Explorer.
As we can see, Internet Explorer will be added to the processes list:
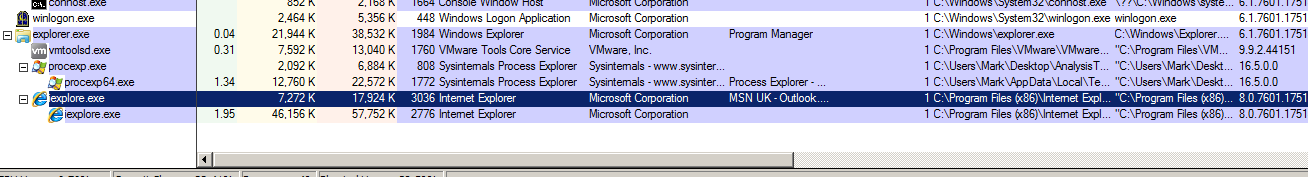
Due to my configuration with the customized columns list, I can see other information such as the file path the executable was started from. This is very useful.
By right clicking on a process, you get a whole new set of options. They will be displayed in the following screenshot:
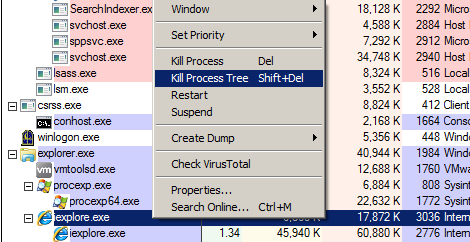
If you ever want to try to terminate a sample executing, you can try the "Kill Process" or "Kill Process Tree" options. You can also check it's VirusTotal detection, try to terminate and then have it Restarted with the Restart option... The Suspend option is a way of "pausing" it's execution - basically where the sample is not terminated so it's still technically running on the system however it is not executing any actions.
NOTE: If the sample is protected (as in it may have injected into processes or loaded a kernel mode driver and use this to it's advantage to protect itself) the termination/suspension on the process may fail. For example a user mode rootkit may try to prevent it's termination. Also watch out for any processes which may start up which may watch for if the target sample is killed to try to restart it. It may also add itself to start up to have itself restarted after booting into Windows again (and signing in), or created a Task with the Windows Task Scheduler to have itself launched again.
Process Explorer is a very useful tool. Don't think that it can just do as I mentioned here, as there is more. This thread is just a quick and short introduction. As we progress with dynamic malware analysis, you'll want to monitoring Processes a lot. You may find a better alternative you prefer, whereas some will keep using Process Explorer and will explore and find the new possibilities it offers.
Just a short thread... Hopefully at least someone will find it useful, though.
Cheers.
This thread will be quite simple. About at least 90-95% of the people reading this will know how to monitor processes on the system, however that last 5% may not which is why I am making this thread.
A very important thing during Malware Analysis is to monitor the processes. This helps I see when the target sample is executing, when it is terminated, watch for any other processes which it may start up and as well as this, we can also see the CPU usage to the process which does give us a idea of if it's doing something at that time.
For example, if it's writing files to the disk then the CPU% for that process will increase. Or if it's constantly checking if another process (let's say it drops another process which does the work) is open and if not to start it then the CPU will increase.
We will be using Process Explorer for the purpose of this thread. I'd like to note that there are many process monitors out there (there is one in the Malcode Analysts Pack, there is Process Hacker,... I am sure you can all find a lot and many different ones out there), however we will be using Sysinternals Process Explorer for this thread to get started.
You need to download Sysinternals Process Explorer from Microsoft TechNet from the following URL: https://technet.microsoft.com/en-us/sysinternals/bb896653.aspx
Once it has completed downloading, extract it. I recommend placing it somewhere on the Desktop for easy access. Or a folder combined with many different Analysis tools called "AnalysisTools".
After the extraction is complete, open up the extracted folder. There should be a executable in that folder called "procexp.exe". Open it up (as Administrator).

The first time you run Process Explorer you will be shown License Agreement for using the program. If you want to use Process Explorer you must Agree to it. Read through the License Agreement and then choose to Accept or not.
Process Explorer should look like as below:

The Process Explorer UI is quite simple and straight forward. You are shown the processes, along with other information corrosponding to them such as: CPU, Private Bytes, Working Set, PID, Description and the Company Name (based on the File Information). You can add and remove colums if you wish. To do this, see the following spoiler.
You can add and remove colums from the area in which information is shown on the Processes. To do this:
1). Right click on the menu where it displays information such as the Company Name. You will be presented with a dropdown. Click from the dropdown menu which appears, "Select Columns...".
2). From the window which appears, check and untick any items you want/do not want. I will check some items I want and will be using throughout the use of Process Explorer, and you can decide if you want to use the same ones as me:
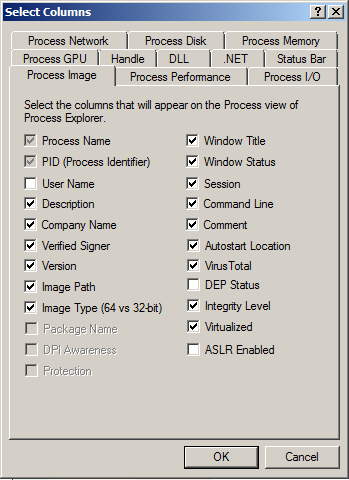
(I ticked a lot. There are other tabs to modify the configuration of the columns on, so feel free to go through them and get checking and unchecking... ... Just be aware, with my config for the columns you will have A LOT of columns to read...).
... Just be aware, with my config for the columns you will have A LOT of columns to read...).
1). Right click on the menu where it displays information such as the Company Name. You will be presented with a dropdown. Click from the dropdown menu which appears, "Select Columns...".

2). From the window which appears, check and untick any items you want/do not want. I will check some items I want and will be using throughout the use of Process Explorer, and you can decide if you want to use the same ones as me:

(I ticked a lot. There are other tabs to modify the configuration of the columns on, so feel free to go through them and get checking and unchecking...
Now customization is out the way, let's actually see if we can find some information out on a new process being created with Sysinternals Process Explorer!
Scroll down to the end of Process Explorer processes list. Any new processes will be made at the end.
Open up any program on the system. This could be Internet Explorer, for example. I will open Internet Explorer.
As we can see, Internet Explorer will be added to the processes list:

Due to my configuration with the customized columns list, I can see other information such as the file path the executable was started from. This is very useful.
By right clicking on a process, you get a whole new set of options. They will be displayed in the following screenshot:

If you ever want to try to terminate a sample executing, you can try the "Kill Process" or "Kill Process Tree" options. You can also check it's VirusTotal detection, try to terminate and then have it Restarted with the Restart option... The Suspend option is a way of "pausing" it's execution - basically where the sample is not terminated so it's still technically running on the system however it is not executing any actions.
NOTE: If the sample is protected (as in it may have injected into processes or loaded a kernel mode driver and use this to it's advantage to protect itself) the termination/suspension on the process may fail. For example a user mode rootkit may try to prevent it's termination. Also watch out for any processes which may start up which may watch for if the target sample is killed to try to restart it. It may also add itself to start up to have itself restarted after booting into Windows again (and signing in), or created a Task with the Windows Task Scheduler to have itself launched again.
Process Explorer is a very useful tool. Don't think that it can just do as I mentioned here, as there is more. This thread is just a quick and short introduction. As we progress with dynamic malware analysis, you'll want to monitoring Processes a lot. You may find a better alternative you prefer, whereas some will keep using Process Explorer and will explore and find the new possibilities it offers.
If a process is created after executing a malware sample claiming to be winlogon.exe, explorer.exe, svchost.exe (or another term referring to it in a way like svhost.exe or schost.exe even) or any Windows known process name, that can be taken as suspicious for further analysis on the sample.
As well as this, if the sample has the filename referring to it being a archive when it is a executable, this is also suspicious and a known way for a malware writer to try to trick the target. (double extensions)..
The sample may also pretend to be by another company e.g. Microsoft, Adobe, Piriform, Google, Yahoo, Opera, ... List can go on. Even Antivirus vendors. So make sure to check the Digital Signature/if it is signed to be validated to be by those companies. Suspicious to pretend to be another company.
Sometimes even the icon can refer to if a sample is suspicious. E.g. WinRAR icon when it isn't a RAR archive.
Of course the above doesn't decide if it's malicious or not, however suspicious traits are good to find.
As well as this, if the sample has the filename referring to it being a archive when it is a executable, this is also suspicious and a known way for a malware writer to try to trick the target. (double extensions)..
The sample may also pretend to be by another company e.g. Microsoft, Adobe, Piriform, Google, Yahoo, Opera, ... List can go on. Even Antivirus vendors. So make sure to check the Digital Signature/if it is signed to be validated to be by those companies. Suspicious to pretend to be another company.
Sometimes even the icon can refer to if a sample is suspicious. E.g. WinRAR icon when it isn't a RAR archive.
Of course the above doesn't decide if it's malicious or not, however suspicious traits are good to find.
Just a short thread... Hopefully at least someone will find it useful, though.
Cheers.
Last edited by a moderator: