- Feb 4, 2016
- 2,520
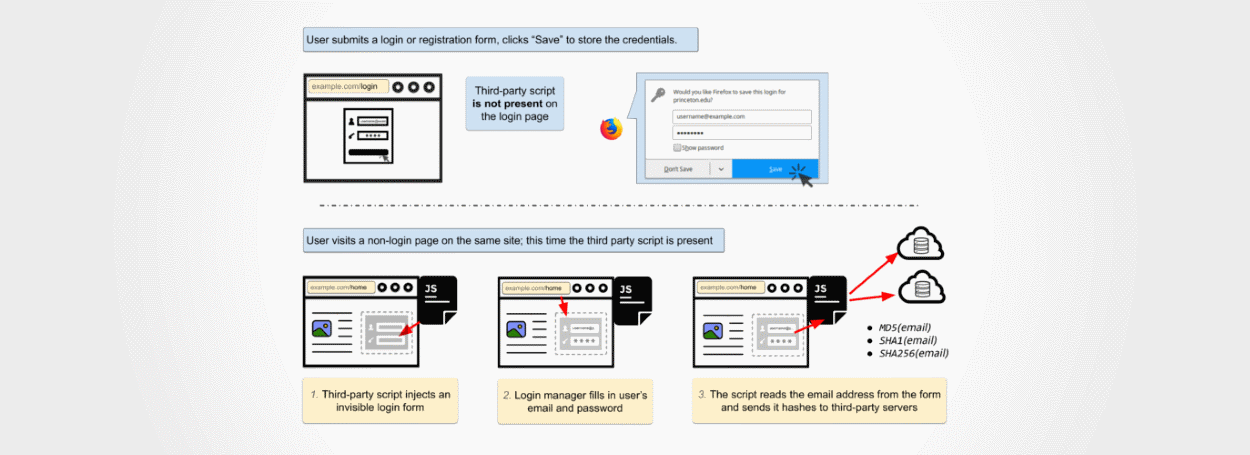
Princeton privacy experts are warning that advertising and analytics firms can secretly extract site usernames from browsers using hidden login fields and tie non-authenticated users visiting a site with their profiles or emails on that domain.
This type of abusive behavior is possible because of a design flaw in the login managers included with all browsers, login managers that allow browsers to remember a user's username and password for specific sites and auto-insert it in login fields when the user visits that site again.
Experts say that web trackers can embed hidden login forms on sites where the tracking scripts are loaded. Because of the way the login managers work, the browser will fill these fields with the user's login information, such as username and passwords.
Old browser design flaw. New abuse.
The trick is an old one, known for more than a decade [1, 2, 3, 4, 5], but until now it's only been used by hackers trying to collect login information during XSS (cross-site scripting) attacks.
Princeton researchers say they recently found two web tracking services that utilize hidden login forms to collect login information.
Fortunately, none of the two services collected password information, but only the user's username or email address —depending on what each domain uses for the login process.
The two services are Adthink (audienceinsights.net) and OnAudience (behavioralengine.com), and Princeton researchers said they identified scripts from these two that collected login info on 1,110 sites found on the Alexa Top 1 Million sites list.
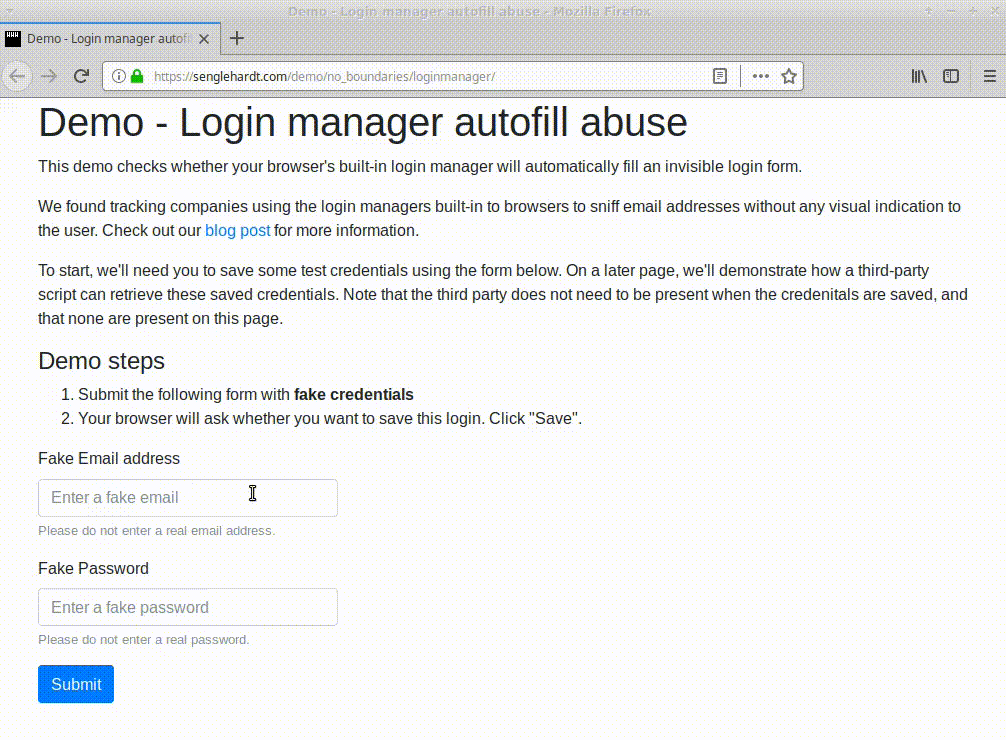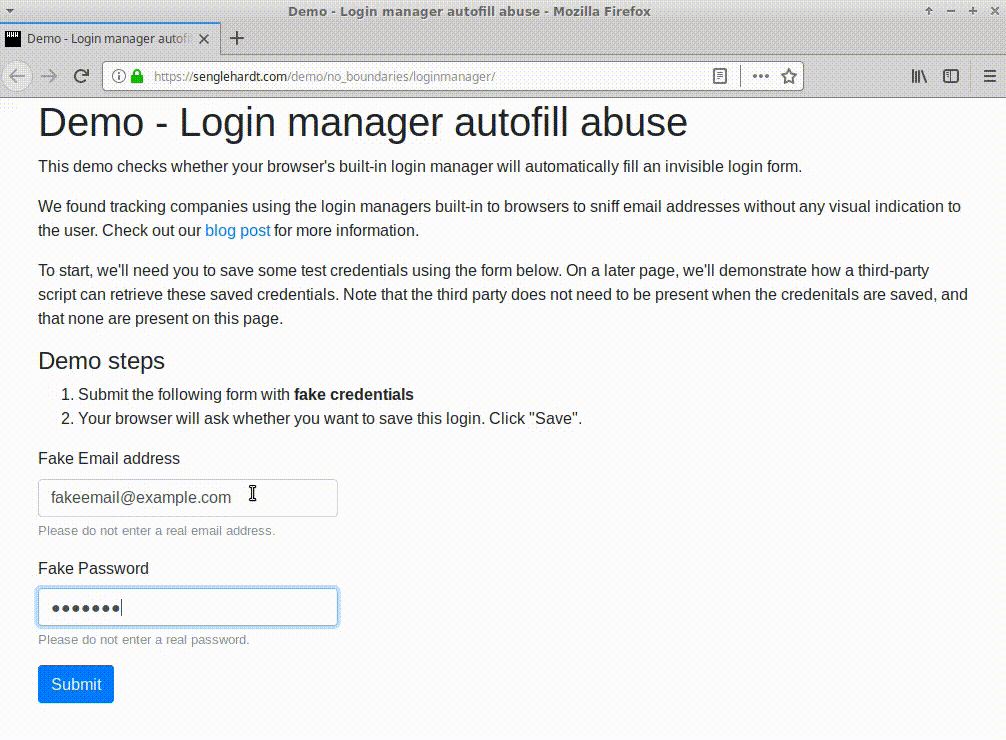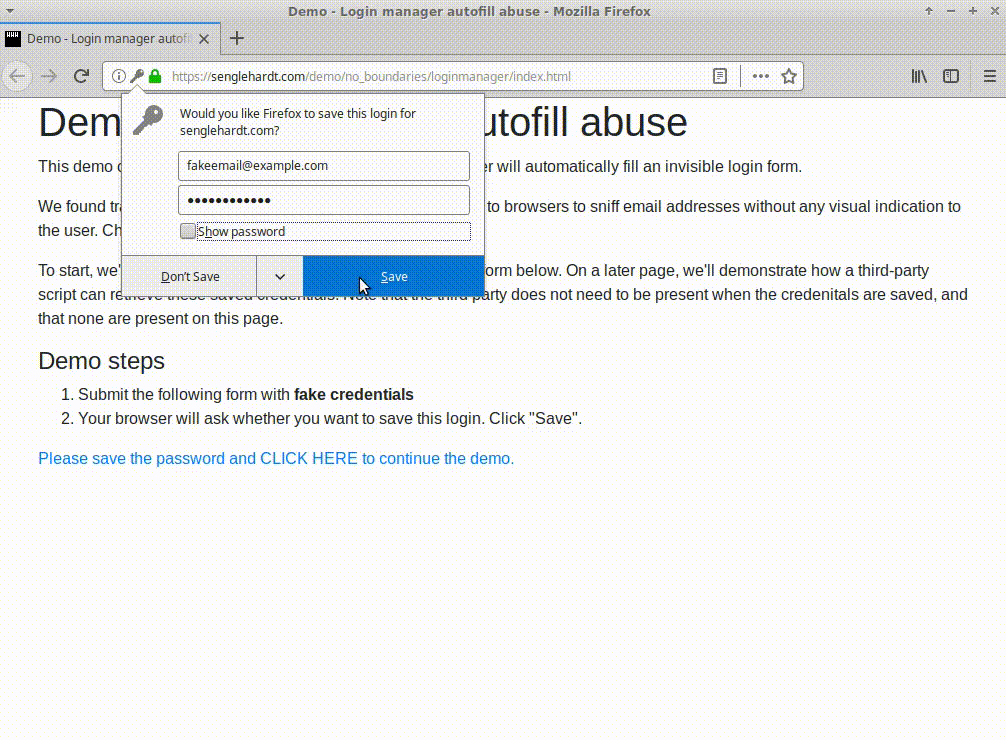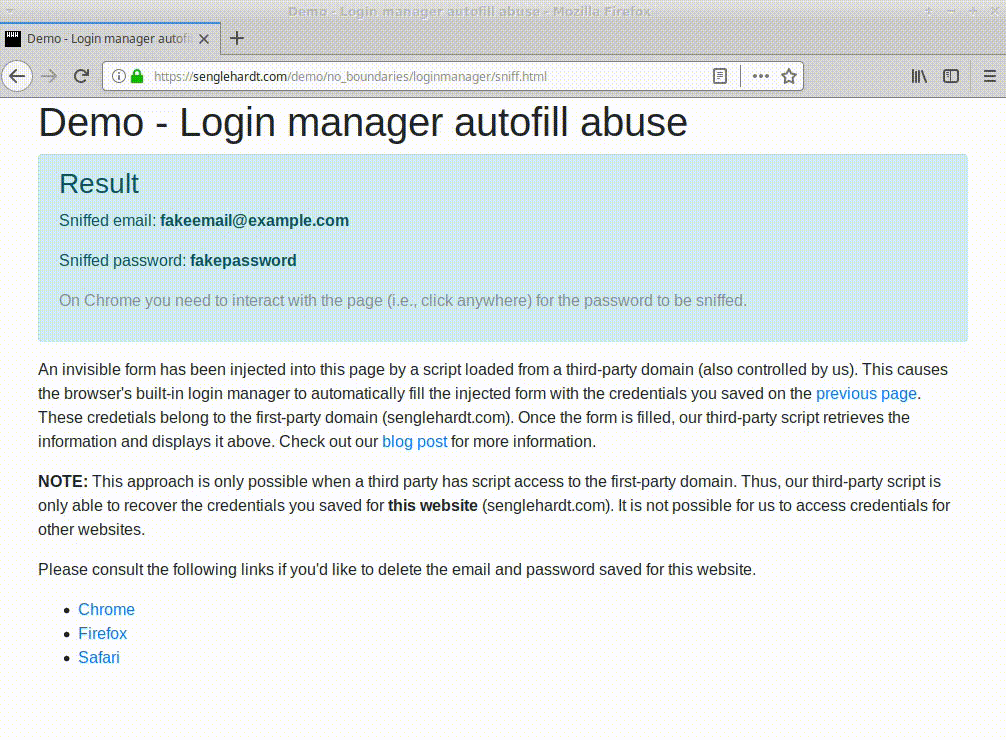
At the time of writing, all major browsers except Brave appear to be vulnerable to this type of attack, coughing up usernames and passwords from the hidden login fields.
Only Chromium-based browsers will delay the disclosure of the user's password until the user has interacted with the page via a click, albeit this is not a very secure method of protecting users, as most end up on clicking on a page.
Many site owners are probably unaware of this questionable tracking tactic, which means they are also unaware that they may be in a clear violation of the EU's upcoming GDPR regulation.
The simplest way to prevent such attacks would be if browsers would autofill the login fields only on user interaction with the actual login fields. If the fields are hidden, the user won't interact with them and this attack would become inefficient.