Hi friends,
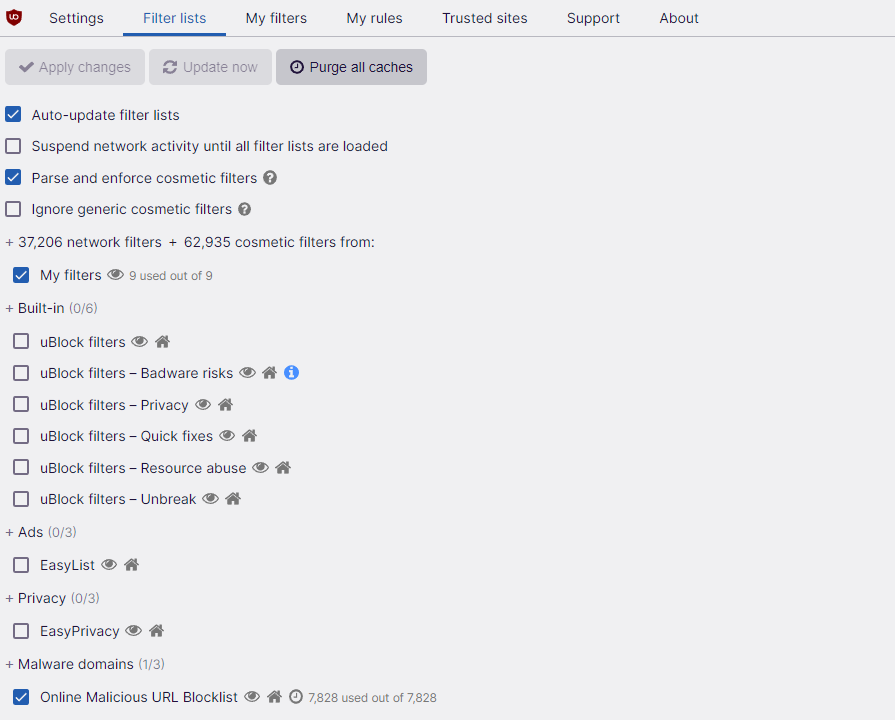
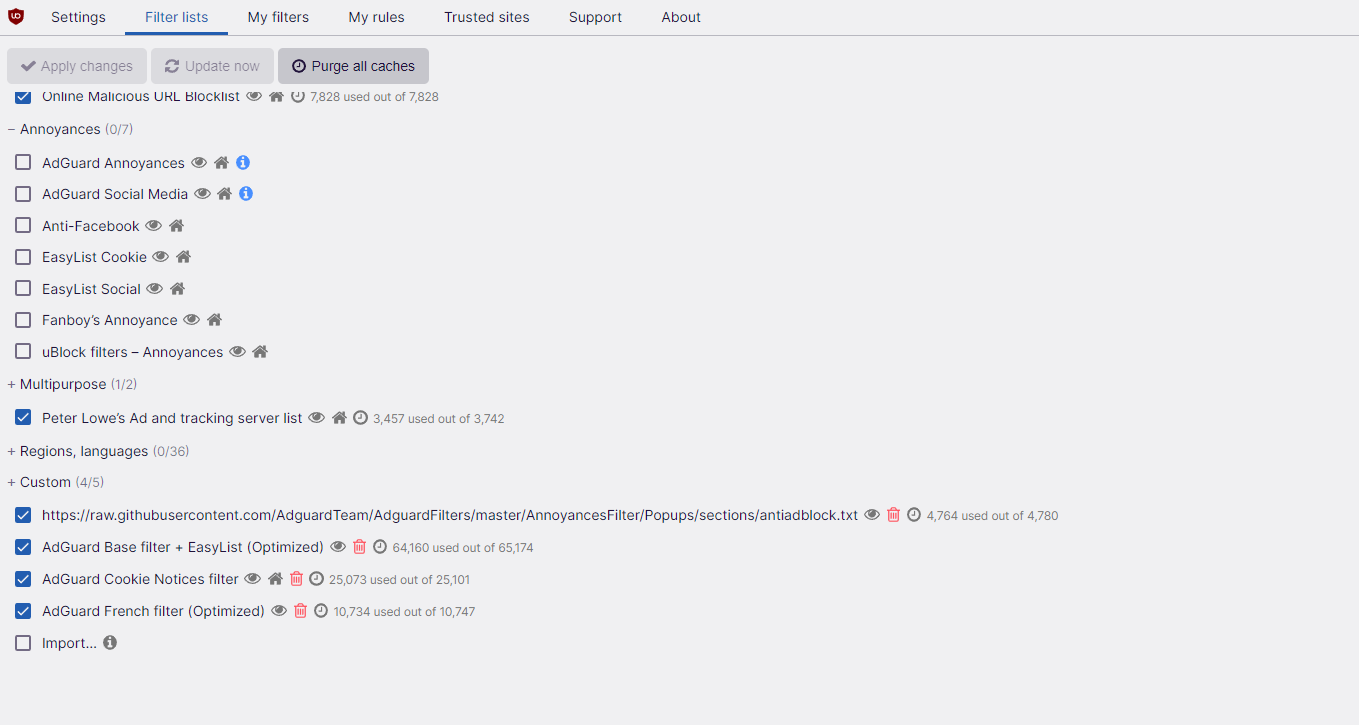 This is an update to a previous thread here about Ubo filters lists.
This is an update to a previous thread here about Ubo filters lists.
These are my UBO filter lists.
Any comments or recommendations are welcome.
Thanks you for your contribution.
These are my UBO filter lists.
Any comments or recommendations are welcome.
Thanks you for your contribution.
