Technical Analysis & Remediation
MITRE ATT&CK Mapping
T1059.001 (Command and Scripting Interpreter) usage of PowerShell and Batch scripts (0a1a98b5f9fc7c62.bat).
T1055 (Process Injection)
Uses Donut to generate shellcode and inject payloads into explorer.exe to run purely in memory.
T1562.001 (Impair Defenses)
Disables Task Manager and UAC prompts to prevent user termination.
T1056.001 (Keylogging) & T1125 (Video Capture)
Pulsar RAT capabilities include webcam/mic surveillance and keystroke logging.
T1611 (Escape to Host)
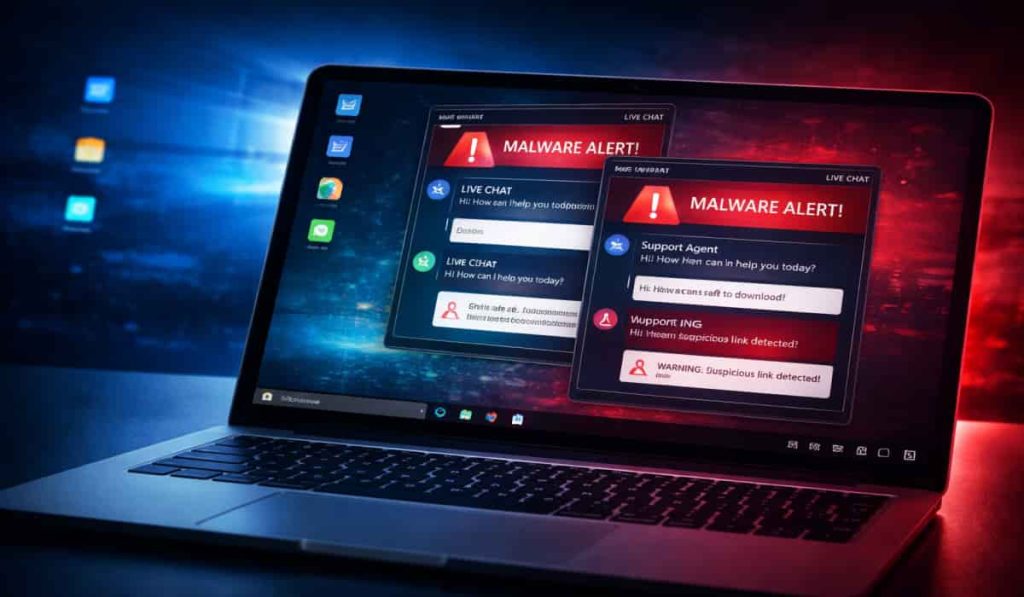
While not a VM escape, the "Live Chat" feature represents a breaking of the "fourth wall" between attacker and victim.
CVE Profile
Pending NVD Analysis
As a zero-day campaign leveraging open-source toolkits (Pulsar/Quasar forks), specific CVEs for the delivery method are TBD.
Active Exploitation
Confirmed active in the wild (CISA KEV criteria met for "Active Exploitation" definition, though specific CVE assignment is pending).
Forensic Indicators (IOCs)
File Path %APPDATA%\Microsoft\0a1a98b5f9fc7c62.bat (Batch file dropper).
Behavior
Unexpected explorer.exe network connections; system fan spin-up due to high CPU usage from in-memory .NET assemblies.
Network
Exfiltration traffic to Discord and Telegram API endpoints.
Tools
Presence of Donut shellcode artifacts or Stealerv37 signatures.
Remediation - THE ENTERPRISE TRACK (SANS PICERL)
Identification & Containment
Isolate
Immediately VLAN-isolate any endpoint exhibiting unauthorized "Live Chat" windows or flagging 0a1a98b5f9fc7c62.bat.
Hunt
Query SIEM for PowerShell execution strings referencing %APPDATA%\Microsoft and unexpected traffic to discord.com/api or api.telegram.org from non-user subnets.
Process Block
Use EDR to suspend (not just kill) explorer.exe instances with unbacked memory regions (floating code) indicative of Donut injection.
Eradication
Memory Analysis
The malware resides in memory. A simple reboot may clear the active injection, but persistence mechanisms (Registry Run Keys/Scheduled Tasks) will reinfect.
Purge
Remove the specific batch file 0a1a98b5f9fc7c62.bat and audit Task Scheduler for tasks created within the infection window.
Reset
Force a global password reset for all users on the infected machine due to the Stealerv37 component.
Recovery
Reimage
Due to the RAT's deep system integration (UAC disablement, Task Manager tampering), reimaging is the only safe option for enterprise assets.
Patch
Ensure ASR (Attack Surface Reduction) rules block obfuscated scripts and child process creation from Office/PDF apps.
Lessons Learned
Update threat intelligence feeds to track "Pulsar RAT" variants.
Conduct user training on the "Live Chat" tactic; users should be trained to disconnect power immediately rather than engage with attackers.
Remediation - THE HOME USER TRACK
Priority 1: Safety (The "Disconnect" Protocol)
If a chat window pops up or your mouse moves on its own, physically disconnect the computer from the internet immediately (unplug the Ethernet cable or disable Wi-Fi via hardware switch). Do NOT engage with the chat.
Cold Boot
Shut down the computer completely. Wait 30 seconds. Turn it back on without reconnecting to the internet.
Priority 2: Persistence Removal
Boot into Safe Mode (Hold Shift while clicking Restart -> Troubleshoot -> Advanced Options -> Startup Settings -> Restart -> Press 4).
Check specifically for the file 0a1a98b5f9fc7c62.bat in your AppData folder (Type %APPDATA% in the file explorer bar) and delete it if found.
Run a full offline scan using Microsoft Defender or a reputable second-opinion scanner (e.g., Malwarebytes) transferred via USB from a clean machine.
Priority 3: Identity Triage
Assume Compromise: The "Stealerv37" component targets Chrome/Edge passwords and cookies.
Using a different, clean device (like your phone on cellular data), change passwords for:
Email accounts (Primary target).
Banking/Crypto wallets.
Gaming accounts (Steam/Roblox).
Enable 2FA (Two-Factor Authentication) everywhere immediately.
Hardening & References
Baseline
Enable "Controlled Folder Access" in Windows Security to prevent unauthorized changes to system folders.
Framework
NIST SP 800-61r2 (Incident Handling) - Phase 2 (Detection & Analysis).
Tactical
Visual guide recommended for Home Users trying to enter Safe Mode.
System Note
This malware uses psychological pressure (Live Chat). Do not let panic dictate your response. Disconnect, Isolate, and Clean.
Source
Point Wild (Lat61 Threat Intelligence Team)
Hackread
Technical References (Contextual)
Attack Vector
"Living-off-the-land" via PowerShell
Injection Tool
Donut (Shellcode Generator)
Targeted Platforms
Discord & Telegram (Exfiltration channels)
Steam & Roblox (Gaming accounts)
NordVPN & Crypto Wallets
 hackread.com
hackread.com


