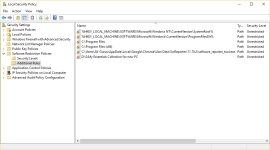
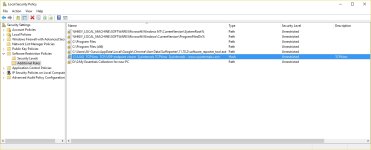
Here is the vbs script that works on my Windows 10 Home. It is in the alpha stage (not tested on other machines).
Anybody can optimize and modify it.
If You want to bypass SRP the script must be wrapped to exe file for asking admin rights.
Some executable extensions have to be removed from SRP ( BAT, CMD, JS, JSE, MSI, VBE, VBS, WSF), if You want to run them with "Run As Smartscreen". I noticed that they are still protected by SRP. The difference is that they are blocked when sponsors (cmd.exe, wscript.exe, msiexex.exe) try to get files in the User Space.
.
.
RunAsSmartScreen.vbs
****************************************************************************************************************************************
Set WshShell = CreateObject("WScript.Shell")
'****** Put the path of the file to fsoFile variable ******
Set fso = CreateObject("Scripting.FileSystemObject")
Set fsoFile = fso.GetFile(WScript.Arguments.Item(0))
'****** Check if the file is in the System Space ******
If InStr(chr(34)&fsoFile&chr(34), "C:\Windows\") = 2 Then
WshShell.Run(chr(34)&fsoFile&chr(34))
WScript.Quit
Else
If InStr(chr(34)&fsoFile&chr(34),"C:\Program Files\") = 2 Then
WshShell.Run(chr(34)&fsoFile&chr(34))
WScript.Quit
Else
If InStr(chr(34)&fsoFile&chr(34),"C:\Program Files (x86)\") = 2 Then
WshShell.Run(chr(34)&fsoFile&chr(34))
WScript.Quit
Else
'****** Clear all file attributes
fsoFile.Attributes = fsoFile.Attributes AND 0
'****** Create, run and delete another script AddZoneIdentifierToFile.vbs , that adds the proper ADS ******
Set f = fso.CreateTextFile("C:\Windows\temp\AddZoneIdentifierToFile.vbs")
f.WriteLine ("Set WshShell = CreateObject(" & chr(34) & "WScript.Shell" & chr(34)&")")
f.WriteLine ("Set fso = CreateObject(" & chr(34) & "Scripting.FileSystemObject" & chr(34)&")")
f.WriteLine ("Set f = fso.CreateTextFile(" & chr(34) & fsoFile & ":Zone.Identifier" & chr(34)&")")
f.WriteLine ("f.WriteLine " & chr(34) & "[ZoneTransfer]" & chr(34))
f.WriteLine ("f.WriteLine " & chr(34) & "ZoneId=3" & chr(34))
f.WriteLine ("f.close")
WshShell.Run ("C:\Windows\Temp\AddZoneIdentifierToFile.vbs")
Set f = fs

penTextFile("C:\Windows\Temp\AddZoneIdentifierToFile.vbs", 1)
f.Close
WScript.Sleep 1000
fso.DeleteFile("C:\Windows\Temp\AddZoneIdentifierToFile.vbs")
'****** Run the file ******
WshShell.Run(chr(34)&fsoFile&chr(34))
End If
End If
End If
Set WshShell = Nothing
WScript.Quit
****************************************************************************************************************************************
I do not know why there is the yellow face in the vbs code. You must replace it by dotOdot, similarly to the fso.DeleteFile command.
.
.
Run_As_SmartScreen.reg
***************************************************************************************
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\*\shell\Run As SmartScreen]
"Icon"="%windir%\\system32\\SmartScreenSettings.exe"
[HKEY_CLASSES_ROOT\*\shell\Run As SmartScreen\command]
@="C:\\Windows\\RunAsSmartscreen.exe \"%1\" %*"
***************************************************************************************
.
.
Installation:
Wrap RunAsSmartscreen.vbs to RunAsSmartscreen.exe
Copy RunAsSmartscreen.exe to the "C:\Windows\" folder.
Import Run_As_SmartScreen.reg to the Windows Registry.
.
.
Deinstallation:
Remove RunAsSmartscreen.exe from "C:\Windows\" folder.
Delete the registry key: [HKEY_CLASSES_ROOT\*\shell\Run with SmartScreen]
.
.
This is the more convenient "Run As SmartScreen" solution. I also tried solutions with RunAsSmartscreen.bat or RunAsSmartscreen.vbs without wrapping, but then the launcher is needed, to run the file from the script with admin rights, to bypass SRP. On my machine, the Nirsoft program "nircmd.exe" worked well.