I read that for security you need to disable Windows Script Host, since many malicious programs use this mechanism. However, people also write that after disabling Windows Script Host there will be problems with system updates and the system recovery mechanism. So is it worth disabling Windows Script Host or not?
Windows Script Host: disable or enable?
- Thread starter Zorro
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Some software still uses it, but new ones use powershell, NET Framework and such. Windows updates work fine, but not not sure about store apps, they should use UWP. Windows upgrade also performs normally without WSH, but when I tested 3rd party backup software, it used it for tasks.However, people also write that after disabling Windows Script Host there will be problems with system updates and the system recovery mechanism.

A closer look at the Locky ransomware
A deep and technical look into the latest ransomware called Locky.
WSH is usually the way malware enters the system, without user's interaction.
I rarely need it, mostly for some user generated stuff/scripts, like for games.
When it is needed a user should be notified, either via an error or directly.
Attachments
The question as presented in the poll is black and white: disable it or not. I voted to disable. But there is a middle position: restrict Windows Script Host. That is the best option, in my opinion.
F
ForgottenSeer 823865
This is config dependent, if the user has programs that requires it, it cant be disabled.
i second @shmu26 with restricting it.
i second @shmu26 with restricting it.
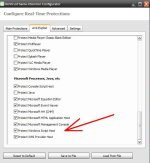
There is a point in Syshardener - turn off the Windows Script Host. There is an orange mark as a warning that scripts will not work. If you activate this item, will the Windows Script Host completely shut down or will it work in restrict mode?
How to start restricted mode?The question as presented in the poll is black and white: disable it or not. I voted to disable. But there is a middle position: restrict Windows Script Host. That is the best option, in my opinion.
It will shut it down completely. SysHardener doesn't allow you to restrict or monitor it, although OSArmor and a number of other security softs do give you such a functionality.There is a point in Syshardener - turn off the Windows Script Host. There is an orange mark as a warning that scripts will not work. If you activate this item, will the Windows Script Host completely shut down or will it work in restrict mode?
It's the kind of thing that you never know when you might need it. Just a little example: let's say you installed Comodo Firewall, decided it's not for you, and uninstall it. When you reboot, a little cleanup script will run, and remove the Comodo leftovers pretty effectively. If you disabled Windows Script Host, you are left with all the garbage.
OK. What other items in OSArmor, other than those noted by Samprei Nihira, are responsible for limiting the Windows Script Host?although OSArmor and a number of other security softs do give you such a functionality.
IDK. Haven't looked at it in a long time. Others following this thread can tell you if there are any other items like that.OK. What other items in OSArmor, other than those noted by Samprei Nihira, are responsible for limiting the Windows Script Host?
Last edited:
I doubt it would be very " smart " turn this off/disable for actual Home/common users. In the Geek world, it's of course different.
At least try avoid fiddle with this on your grandparents pc.
At least try avoid fiddle with this on your grandparents pc.
I disable it on every computer I get my hands on, especially on my grandparents.At least try avoid fiddle with this on your grandparents pc.
Symantec offered the tool to enable/disable it with one click, but it was removed recently.
Some mention it, but they do not want users to disable it . Who would need theirs AV then?!
How to disable Windows Script Host | F‑Secure
Learn how to disable Windows Script Host to protect your PC from malware and unauthorized scripts. Step-by-step guide included.

Disable Windows Script Host (WSH) to block .VBS malware
Windows Script Host (or WSH) (also known as Windows Scripting Host) is a scripting language shipped with all major Windows and Windows Server distributions sinc
2019 - That’s it for now: given the widespread distribution of VBS viruses and malwares attached to e-mails throughout the whole Europe, we can only recommend to preventively disable WSH to all system administrators, unless explicitly required by specific scenarios.
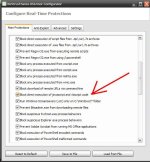
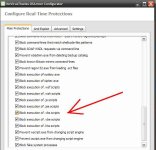
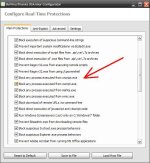
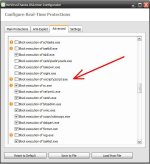
Hard_Configurator offers two ways of controlling Windows Script Host. It can be blocked completely, similar to SysHardener, or it can be restricted. When it is restricted, that means it can be run only with elevated privileges.
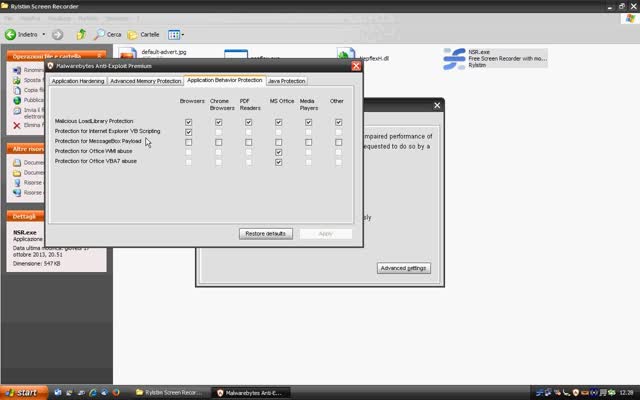
If any MT user is interested in my old vbs test with I.E.8 and MBAE intervention.
MBAE intervention for a VBS exploit has a different layout than other exploits:
 sendvid.com
sendvid.com
Good night to you all .
MBAE intervention for a VBS exploit has a different layout than other exploits:

I E 8 VB Script
Upload and share videos instantly. It's free and simple. No signup required.
Good night to you all .
In H_C Windows Script Host can be disabled by Windows policy or restricted by SRP.Hard_Configurator offers two ways of controlling Windows Script Host. It can be blocked completely, similar to SysHardener, or it can be restricted. When it is restricted, that means it can be run only with elevated privileges.
The SRP in H_C settings can restrict it as follows:
- Block script Interpreter with standard privileges and allow it with higher privileges. No whitelisting available.
- Allow script Interpreter, but block script files with standard privileges and allow script files with higher privileges. Blocked scripts can be whitelisted by the user.
This tool did not disable Windows Script Host, but only script files by file extensions (similarly to SysHardener). The scripts could be still run from the command-line, for example:I disable it on every computer I get my hands on, especially on my grandparents.
Symantec offered the tool to enable/disable it with one click, but it was removed recently.
wscript /e:vbscript ....
The reg tweaks proposed in both articles are incomplete for Windows 64-bit. The block can be bypassed by using a command-line with 32-bit versions of script Interpreters from the "c:\Windows\SysWOW64" folder.How to disable Windows Script Host | F‑Secure
Learn how to disable Windows Script Host to protect your PC from malware and unauthorized scripts. Step-by-step guide included.blog.f-secure.com

Disable Windows Script Host (WSH) to block .VBS malware
Windows Script Host (or WSH) (also known as Windows Scripting Host) is a scripting language shipped with all major Windows and Windows Server distributions sincwww.ryadel.com
Last edited:
You may also like...
-
Serious Discussion Orion Malware Cleaner (OMC) - By Trident
- Started by Trident
- Replies: 23
-
Serious Discussion Windows 11 Recall — Productivity Perk or Privacy Disaster?
- Started by Bot
- Replies: 5
-
First AI-powered ransomware, using OpenAI models to generate scripts that target Windows, Linux and macOS.
- Started by Brownie2019
- Replies: 0
-
Serious Discussion LockBit 5.0 Is Back — Stronger, Sneakier, More Dangerous
- Started by Bot
- Replies: 5