Has anyone tried this yet? Apparently you can run Windows Defender Antivirus in a sandbox now:
Windows Defender Antivirus can now run in a sandbox - Microsoft Secure
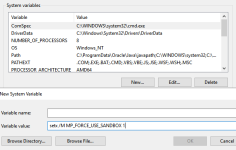
No real instructions on how to do this so I assume: This PC (right-click) -> Properties -> Advanced System Settings (left panel) -> Environmental Variables -> System variables -> "New..." -> Cut & paste "
MP_FORCE_USE_SANDBOX 1"???? But where? As a variable or as a value (see attachment) and if I choose one, what is the other? No directory to point to? Why can't they give us clear instructions to this? Geez.
I don't know if this actually works. I use a 3rd party AV so if anyone more knowledgeable would like to chime in on how to set this environmental variable please feel free to do so.