D
Basic Security Windows_Security's Security Config
- Thread starter Windows_Security
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Last updated
- Nov 11, 2018
- Windows Edition
- Enterprise
- Security updates
- Allow security updates and latest features
- User Access Control
- Always notify
- Real-time security
- Windows Firewall also blocking outbound by default (rules locked by GPO)
AppLocker with granular whitelist rules (only signed trusted vendors)
F-Secure provided by my ISP (comes with broadband/internet subscription
- Firewall security
- Microsoft Defender Firewall
- Periodic malware scanners
- Only Process Explorer and Autoruns, because AppLocker only allows whitelisted vendors per folder (e.g. only allow Microsoft signed in Windows and only allow Google signed in Chrome, etc).
- Malware sample testing
- I do not participate in malware testing
- Browser(s) and extensions
- Firefox with Avira Browser Safety and Chrome with Bitdefender Trafficlight
- Maintenance tools
- CleanMgr (dumped CCleaner)
- File and Photo backup
- Weekly NAS, during the day using Synback Free (quick) backup to additional harddisk to which only Business Documents and Mail is backed up running as different (basic user) called Backup_User. Only Backup_User has CWX-rights on quick backup disk (Syncback Free starts as another -basis- user).
- System recovery
- Windows build in
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
i said Applocker is a basic SRP, not the setup.
True my friend, but the intresting element was to combine it all with Joanna's idea to use different users:
AppLocker is more advanced than SRP, it also allows rules on signature and has exceptions. Also the signature check is more advanced comapred to SRP's certificate rules. The big plus are the user based rules and the fact that power user was demoted to ordinary standard user in Windows 7. This gives me the option to play with AppLocker rules when making the Admin (UAC protected user) member of Power Users group. Thus allowing to restrict freedon of (other) ordinary users when using the runas command. That is what I tried to explain for firefox:
- Firefox runs in a Medium IL rights container using RunAs (/user) Secure_Surfer (with UAC set to deny elevation request of basic users. Running as other user makes a securiy difference as Cruel Sister has proven in some of her videos (showing difference of running basic user versus UAC protected user). The reason is that running as another user starts the process in another session. This provides additional (memory) protection mechanisms (same as Re:HIPS does by running under other Re:HIPS user and simular (not same) Chome does by running in its processes in Alternate Desktop with User Object limitation.
- AppLocker puts Secure_Surfer in default DENY execution restriction and sets an explicte deny on Secure_Surfer user folders and other data partitions/disks
- AccessControlList put an extra default DENY (traverse folder/execute) on all user folders and other data partitions with an additional option to prevent Secure_Surfer creating, writing, deleting files in Kees User folders (which makes it hard for ransomware to encrypt and destoy files).
- Finally Parental control adds Software Restriction Policies (PC is using SRP mechanism, implemented in different service). Normally AppLocker overrules SRP, but PC works in parallel, narrowing down to executables to be run as Secure_Surfer. The cherry on the cake is the AppLocker rule to deny execution for Secure_Surfer to Windows folder (parental control always allows access to executables in Windows folder). So Secure Surfer user can only execute Firefox, Outlook, Windows Media Player, Office Picture Manager and FileZilla (all process exexuted as secure_surfer).
- The addditional MemProtect rule to block memory access from user space to Explorer and firefox only allowed to acccess memory of processes in own installation folder, closes the door for hollow process attacks and traps all firefox exploit in their own (installation folder container).
So protection from 5 different angles (Integrity level, process, ACL - folder access, ParentalControl and Memory access), should protect me from any off-the-shelve malware. Having a 'rare and crazy' setup makes it commericially uninteresting to be targeted by 'regular' malware.
Last edited:
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Won't the demo time expire?
Edit: I misread, for private non commercial use demo doesn't have limits but its beta and can be buggy.
Demo is time limited and applies a size limitation for its configuration file. Demo survived Windows 10 updates withOUT needing any change, ask @WildByDesign he is a continues user from first beta (few years now), so he can tell something on its compatibility in practise with other security.
I personally only use it when no other third-party monitor processes (call backs), because it simply is to powerfull (when starting in safe mode, driver is not loaded, so in theory one should always have an option to de-install the MemProtect driver in safe mode). I don't have had any incompatibility issues with MemProtect. I just have an irrational (intuïtion) feel that this kind of powerfull sofware should not run with other (exploit) protection software. When they bite each other it could lock down your machine or cause BSOD's
@Windows_Security
I know you started a thread here
Q&A - MemProtect
So any chance of answers to my post #8?
Thanks
I know you started a thread here
Q&A - MemProtect
So any chance of answers to my post #8?
Thanks
Last edited:
Just to clarify, for those unfamiliar with Excubits products: The time limitation on the demo version means you need to reinstall the driver every year. (Easy to do, once you know how to do it.) But your config file is perpetual.
@Windows_Security, regarding other security software potentially conflicting with memprotect, why can't you just make an exception rule for it?
For instance, this is my whitelist rule to allow MS Office to interact with Windows Defender
!*Office1?\*>*MsMpEng.exe
@Windows_Security, regarding other security software potentially conflicting with memprotect, why can't you just make an exception rule for it?
For instance, this is my whitelist rule to allow MS Office to interact with Windows Defender
!*Office1?\*>*MsMpEng.exe
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Sorry @HarborFront thought I had answered at least one: no I would not use it with AV with anti-exploit protection.
MemProtect blocks all exploit tests from HMPalert testtool. With the rules I am using it does not prevent exploits, it just traps them into to the process they exploited. Exploits can attack firefox but they cant jump over to ány other process (explorer for example).
MemProtect blocks all exploit tests from HMPalert testtool. With the rules I am using it does not prevent exploits, it just traps them into to the process they exploited. Exploits can attack firefox but they cant jump over to ány other process (explorer for example).
OK so presuming I don't use with ESET IS can it protect browser-based botnet/rootkit attacks?Sorry @HarborFront thought I had answered at least one: no I would not use it with AV with anti-exploit protection.
MemProtect blocks all exploit tests from HMPalert testtool. With the rules I am using it does not prevent exploits, it just traps them into to the process they exploited. Exploits can attack firefox but they cant jump over to ány other process (explorer for example).
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
OK so presuming I don't use with ESET IS can it protect browser-based botnet/rootkit attacks?
Yes: nothing gets out of the browser when you use these rules
Piority whitelist (with !) - allow all processes in browser folder to call/access processes in that folder
!*\Installation folder of browser\*>*\Installation folder of browser\*
Normal blacklist - block all processes in that folder messing with memory/calling other processes
*\Installation folder of browser\*>*
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Just to clarify, for those unfamiliar with Excubits products: The time limitation on the demo version means you need to reinstall the driver every year. (Easy to do, once you know how to do it.) But your config file is perpetual.
@Windows_Security, regarding other security software potentially conflicting with memprotect, why can't you just make an exception rule for it?
For instance, this is my whitelist rule to allow MS Office to interact with Windows Defender
!*Office1?\*>*MsMpEng.exe
Good solution, as said my opinion is not rational, It feels like driving a car with two passengers on the back bench with big colts in their pockets. When I have two of those agressive guys in my car, they might start a fight (i know does not make any sense, but that is the, maybe stupid, idea I have on exploit prevention/protection sofware).
Thanks. Your intuition is probably at least as good as most people's knowledgeGood solution, as said my opinion is not rational, It feels like driving a car with two passengers on the back bench with big colts in their pockets. When I have two of those agressive guys in my car, they might start a fight (i know does not make any sense, but that is the, maybe stupid, idea I have on exploit prevention/protection sofware).
I realized after posting that the exception rule I wrote could be made shorter and wider, for those working with the demo limits:
!*>*MsMpEng.exe
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Some explanation by OpC0de (once a member of this forum) about MemProtect
________________________________________________________________________________
I did look at MemProtect which is how I know it uses ObRegisterCallbacks.To my knowledge from when I tested MemProtect out it strips access rights for protected processes to prevent the following access rights being granted to a protected process (or its threads):
- PROCESS_CREATE_PROCESS
- PROCESS_TERMINATE
- PROCESS_VM_OPERATION
- PROCESS_VM_READ
- PROCESS_CREATE_THREAD
- PROCESS_VM_WRITE
- PROCESS_SUSPEND_RESUME
- PROCESS_QUERY_INFORMATION
- PROCESS_ALL_ACCESS
- DELETE
- READ_CONTROL
- WRITE_DAC
- WRITE_OWNER
- SYNCHRONIZE
- PROCESS_DUP_HANDLE
- PROCESS_SET_QUOTA
ObRegisterCallbacks is registered using callback registration data which is contained within a kernel-mode structure known as OB_CALLBACK_REGISTRATION. The structure passed in contains an entry to another structure known as OB_OPERATION_REGISTRATION which holds data regarding the callback routines for the even notifications. The kernel-mode callback supports a Pre and Post callback notification for handle open/duplication requests; access rights stripping is performed on the Pre callback notification via bit-mask modification (e.g. a variable containing multiple flags for access rights -> you strip the ones you are interested in blocking only -> access denied is returned to the caller because the request failed).
The access rights data is stripped from a pointer structure passed to the Pre operation notification callback routine known as OB_PRE_OPERATION_INFORMATION (entries within that structure which is passed as a pointer contain data for the notification).
MemProtect will check if the process being targeted for handle creation/duplication has the same image file path as any programs set to be protected via the configuration file.
To make things as easily as possible to be understood, MemProtect basically protects processes using a technique that most traditional security software will use protect their own processes. This is why you cannot terminate one of the MemProtect protected processes from the Details tab on software such as Task Manager, but can still attack the processes via other attack vectors such as their windows if they have one.
I think that this is all a good thing because this also means that MemProtect is stable to run on Windows Vista - 10 systems for both 32-bit and 64-bit.
__________________________________
When I understand above text well, I would rather add a pririty rule giving your AV access to all other processes
!*\Installation folder of your AntiVirus\*>*
________________________________________________________________________________
I did look at MemProtect which is how I know it uses ObRegisterCallbacks.To my knowledge from when I tested MemProtect out it strips access rights for protected processes to prevent the following access rights being granted to a protected process (or its threads):
- PROCESS_CREATE_PROCESS
- PROCESS_TERMINATE
- PROCESS_VM_OPERATION
- PROCESS_VM_READ
- PROCESS_CREATE_THREAD
- PROCESS_VM_WRITE
- PROCESS_SUSPEND_RESUME
- PROCESS_QUERY_INFORMATION
- PROCESS_ALL_ACCESS
- DELETE
- READ_CONTROL
- WRITE_DAC
- WRITE_OWNER
- SYNCHRONIZE
- PROCESS_DUP_HANDLE
- PROCESS_SET_QUOTA
ObRegisterCallbacks is registered using callback registration data which is contained within a kernel-mode structure known as OB_CALLBACK_REGISTRATION. The structure passed in contains an entry to another structure known as OB_OPERATION_REGISTRATION which holds data regarding the callback routines for the even notifications. The kernel-mode callback supports a Pre and Post callback notification for handle open/duplication requests; access rights stripping is performed on the Pre callback notification via bit-mask modification (e.g. a variable containing multiple flags for access rights -> you strip the ones you are interested in blocking only -> access denied is returned to the caller because the request failed).
The access rights data is stripped from a pointer structure passed to the Pre operation notification callback routine known as OB_PRE_OPERATION_INFORMATION (entries within that structure which is passed as a pointer contain data for the notification).
MemProtect will check if the process being targeted for handle creation/duplication has the same image file path as any programs set to be protected via the configuration file.
To make things as easily as possible to be understood, MemProtect basically protects processes using a technique that most traditional security software will use protect their own processes. This is why you cannot terminate one of the MemProtect protected processes from the Details tab on software such as Task Manager, but can still attack the processes via other attack vectors such as their windows if they have one.
I think that this is all a good thing because this also means that MemProtect is stable to run on Windows Vista - 10 systems for both 32-bit and 64-bit.
__________________________________
When I understand above text well, I would rather add a pririty rule giving your AV access to all other processes
!*\Installation folder of your AntiVirus\*>*
Last edited:
I remember this user from before, particularly for their excellent and thorough understanding of low level technical Windows kernel functionality. I did not realize that this member is no longer here though, unfortunately. Definitely someone who understands technical details well and was also very good at explaining those details to other users as well. I recall other conversations previously regarding ObRegisterCallbacks but personally I don't quite understand that deeply. Just a brief question, was this member's overall view point of MemProtect positive or negative?Some explanation by OpC0de (once a member of this forum) about MemProtect
I hope that you are having a wonderful summer, Kees.
I apologize but I may not be able to be very active this summer at all on any forums as I used to. At least, not until September. I should have more time then.
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
@WildByDesign family and friends comes first, so take care
He was positive about it, because MemProtect uses existing doumented mechanisms to remove access rights based on caller's path and/or and process name (depending use of the wildcards). It is a good example of out of the box thinking. A lot of HIPS vendors complained about Vista's (64 bits) kernel protection, no one looked at the option to use access rights reduction to achieve simular protection with much simpler mechanisms (Windows itself does the heavy lifting, that is why MemProtect driver is so tiny and uses so little CPU).
Regards Kees
He was positive about it, because MemProtect uses existing doumented mechanisms to remove access rights based on caller's path and/or and process name (depending use of the wildcards). It is a good example of out of the box thinking. A lot of HIPS vendors complained about Vista's (64 bits) kernel protection, no one looked at the option to use access rights reduction to achieve simular protection with much simpler mechanisms (Windows itself does the heavy lifting, that is why MemProtect driver is so tiny and uses so little CPU).
Regards Kees
Last edited:
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Update:
Set a deny execute AppLocker rulefor Power Users on all internet facing programs (so Kees is not allowed to execute Firefox in Admin UAC protected account, only Limited user Secure_Surfer is). So had to add SumutraPDF to read Pdf's and added Firefox extension to save webpage as PDF, because my PDF printer did not work due to ApplOcker rule to deny execute everything from Windows folder for user Secure_Folder. Changed SumatraPDF.exe to run as LOW integrity with icacls and added MemProtect rule as backup
UAC on full, deny basic users to elevate (e.g. Secure_Surfer) and deny elevation of unsigned also (using reg file to switch on and off). Firefox and Windows (7) update without problems automatcally from Admin/Kees (UAC) account.
Set a deny execute AppLocker rulefor Power Users on all internet facing programs (so Kees is not allowed to execute Firefox in Admin UAC protected account, only Limited user Secure_Surfer is). So had to add SumutraPDF to read Pdf's and added Firefox extension to save webpage as PDF, because my PDF printer did not work due to ApplOcker rule to deny execute everything from Windows folder for user Secure_Folder. Changed SumatraPDF.exe to run as LOW integrity with icacls and added MemProtect rule as backup
UAC on full, deny basic users to elevate (e.g. Secure_Surfer) and deny elevation of unsigned also (using reg file to switch on and off). Firefox and Windows (7) update without problems automatcally from Admin/Kees (UAC) account.
Windows_Security
Level 24
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Updated my setup, see first post: SECURE: Basic - Windows_Security's Security Config
Replaced (paid) MemProtect with (rebranded) F-Secure of my ISP (I get it for 'free' with my Internet subscription)
AppLocker rules
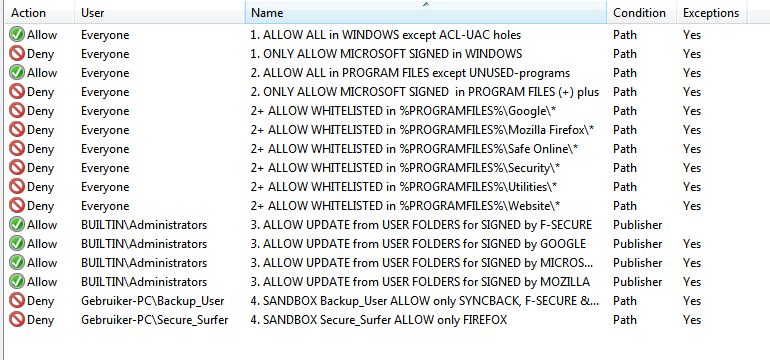
Replaced (paid) MemProtect with (rebranded) F-Secure of my ISP (I get it for 'free' with my Internet subscription)
AppLocker rules
Last edited:
You may also like...
-
App Review Testing Orion Malware Cleaner Designed by Me
- Started by Trident
- Replies: 8
-
Serious Discussion Simple Steps to Secure Your Windows 11 PC
- Started by Divergent
- Replies: 0
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
Serious Discussion Orion Malware Cleaner (OMC) - By Trident
- Started by Trident
- Replies: 23