Hey there!!
KnowBe4 is one of those tests I like to run from a while to while on different scenarios and with different AVs. My choice is to run the AVs signaturless, to simulate a real 0-day attack. Blocking the exes which launch the ransomware tests is not valid for me, since it doesn't prove any sort of behavioural blocking.
Until today, the only AV which has managed to get a clean sheet out of the box is Kaspersky, both Free and Premium ones, thanks to System Watcher. Not even BitDefender when it turns to the ransomware shield itself (although it passes with AV shield).
WiseVectorX v305 out of the box blocks the launch of the test, so it is needed to exclude them.
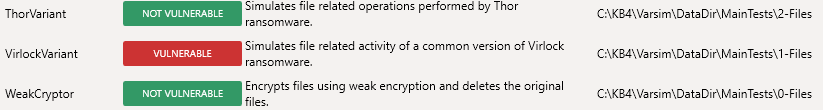
1. Once that's done, if test runs, It gets all the threats (exe and cxp) via the malware engine. They are targeted as these ones:
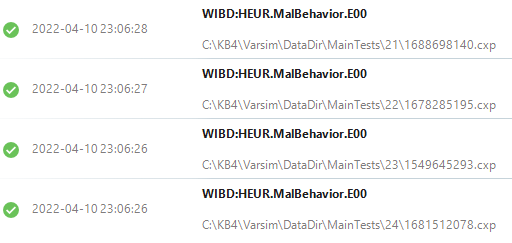
It gets a clean sheet. All non vulerable!!
I think it is a sort of signature based engine as well (since I tested it some days ago and it failed against every non .exe, all .cxp were missed).
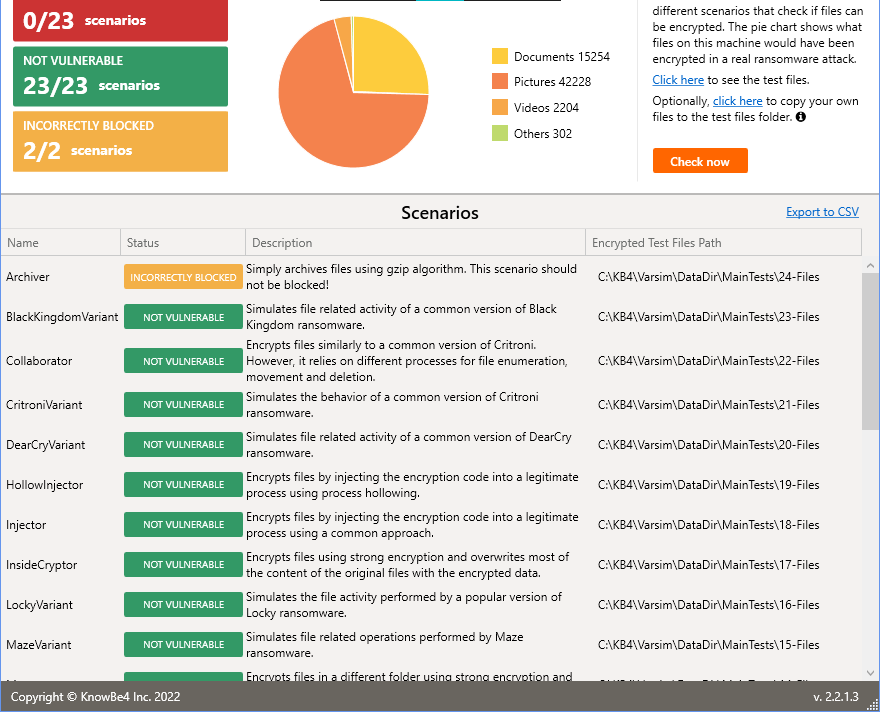
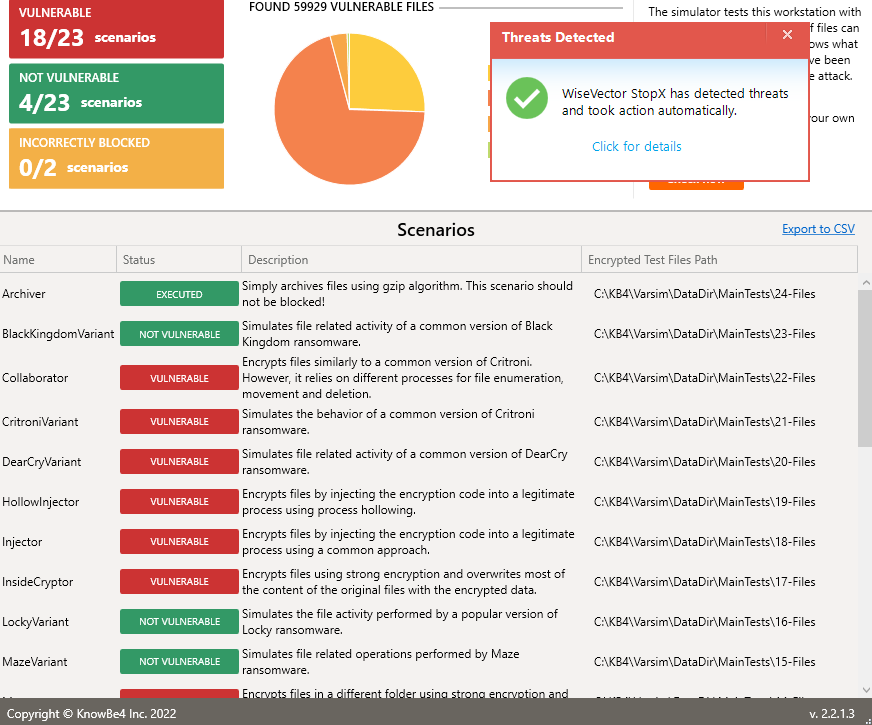
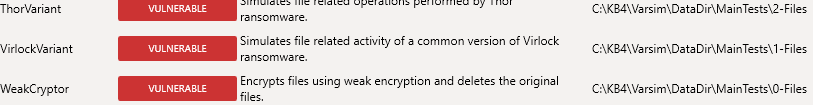
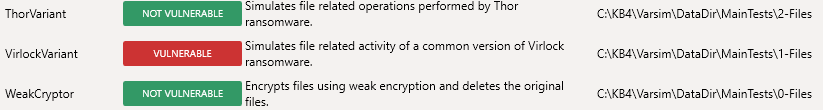
2. Seen that, If i disable malware engine and rely on pure ransomware shields, it just manages to block 4 ransomwares:
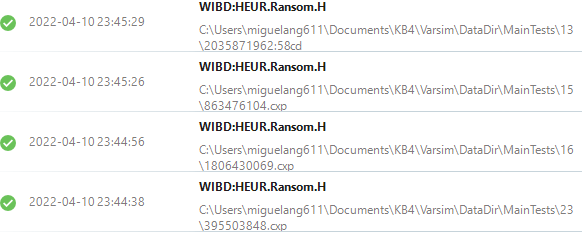
3. However, using deception based ransomware shield, which relies on 2 random folders with some test files, to compare if those are changed in any way, results will differ.
If I copy those 2 folders under one of the test folders and add them to deception protection...
1. Before test begins --> the folders are deleted by the test, and therefore, deception shield is bypassed. I guess because I excluded MainRunner and RanStart on malware shield? And also affects ransomware ones?
2. Once the test has started and the original KnowBe4 docx, txt, xlsx are copied --> WiseVector catches it and prompts me to restore the files.
However, in case the user misclick I don't find the way to restore them (as in the opposite way you have quarantine, but not for ransom rollback).
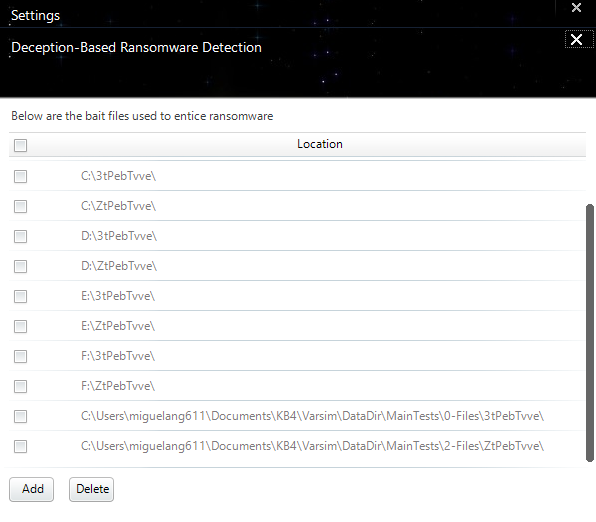
-IMPORTANT NOTE: I moved KB4 to my Documents folder, which is supposed to be protected by Deception shield by defualt (that SS is from that folder itself). HOWEVER, WiseVector won't detect the changes if are made on subfolders!!!!- (except manually recopied and included in WV settings as described in these 2nd option)-
Using that 2nd otpion on 2 test folders (0 and 2), we will move from this...
To this:
Test just began:
Ransom executed:

Rollback prompt:
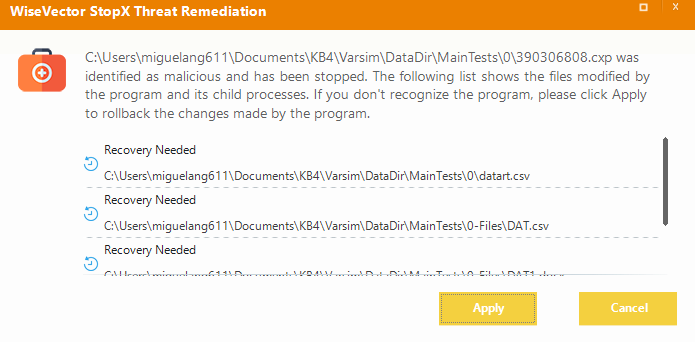
Result after "apply":

On logs it is marked as ransom : D (WV log doesn't work properly and even without a reboot it got flushed :/ )
Anothe side note, while test is executing WiseVector interface usually becomes unresponsive and even closes. Fortunately, WV service still runs on background and is able to protect the PC.
Also, the deception protection is included by default on admin documents folder, but not on other users one! Important if you run a non-priviledged account as I use to do, since you will need to manually add them.
Hope you find this little test interesting!! I think WV concepts are strong, deception protection is powerful, but the exclusions and subfolder problems should be addressed!!
See you!
KnowBe4 is one of those tests I like to run from a while to while on different scenarios and with different AVs. My choice is to run the AVs signaturless, to simulate a real 0-day attack. Blocking the exes which launch the ransomware tests is not valid for me, since it doesn't prove any sort of behavioural blocking.
Until today, the only AV which has managed to get a clean sheet out of the box is Kaspersky, both Free and Premium ones, thanks to System Watcher. Not even BitDefender when it turns to the ransomware shield itself (although it passes with AV shield).
WiseVectorX v305 out of the box blocks the launch of the test, so it is needed to exclude them.
1. Once that's done, if test runs, It gets all the threats (exe and cxp) via the malware engine. They are targeted as these ones:
It gets a clean sheet. All non vulerable!!
I think it is a sort of signature based engine as well (since I tested it some days ago and it failed against every non .exe, all .cxp were missed).
2. Seen that, If i disable malware engine and rely on pure ransomware shields, it just manages to block 4 ransomwares:
3. However, using deception based ransomware shield, which relies on 2 random folders with some test files, to compare if those are changed in any way, results will differ.
If I copy those 2 folders under one of the test folders and add them to deception protection...
1. Before test begins --> the folders are deleted by the test, and therefore, deception shield is bypassed. I guess because I excluded MainRunner and RanStart on malware shield? And also affects ransomware ones?
2. Once the test has started and the original KnowBe4 docx, txt, xlsx are copied --> WiseVector catches it and prompts me to restore the files.
However, in case the user misclick I don't find the way to restore them (as in the opposite way you have quarantine, but not for ransom rollback).
-IMPORTANT NOTE: I moved KB4 to my Documents folder, which is supposed to be protected by Deception shield by defualt (that SS is from that folder itself). HOWEVER, WiseVector won't detect the changes if are made on subfolders!!!!- (except manually recopied and included in WV settings as described in these 2nd option)-
Using that 2nd otpion on 2 test folders (0 and 2), we will move from this...
To this:
Test just began:
Ransom executed:
Rollback prompt:
Result after "apply":
On logs it is marked as ransom : D (WV log doesn't work properly and even without a reboot it got flushed :/ )
Anothe side note, while test is executing WiseVector interface usually becomes unresponsive and even closes. Fortunately, WV service still runs on background and is able to protect the PC.
Also, the deception protection is included by default on admin documents folder, but not on other users one! Important if you run a non-priviledged account as I use to do, since you will need to manually add them.
Hope you find this little test interesting!! I think WV concepts are strong, deception protection is powerful, but the exclusions and subfolder problems should be addressed!!
See you!
Attachments
Last edited: