L
LabZero
Thread author
-Introduction
Today I'm going to analyze Morto.A
It's a worm that allows unauthorized access to an infected computer and tries to compromise administrator
passwords for Remote Desktop connections, through RDP protocol, on a network.
-Malware Identification
https://www.virustotal.com/it/file/...67572f74c6fca339021f32ef844c14afff0/analysis/
SHA256: 650581122b09c12cdc2741e369fa067572f74c6fca339021f32ef844c14afff0
file name: e.ppift_com_net_in
ratio: 48 / 57
Date : 2015-03-08 10:52:34 UTC
-Tools
• CFF Explorer
• SysAnalyzer
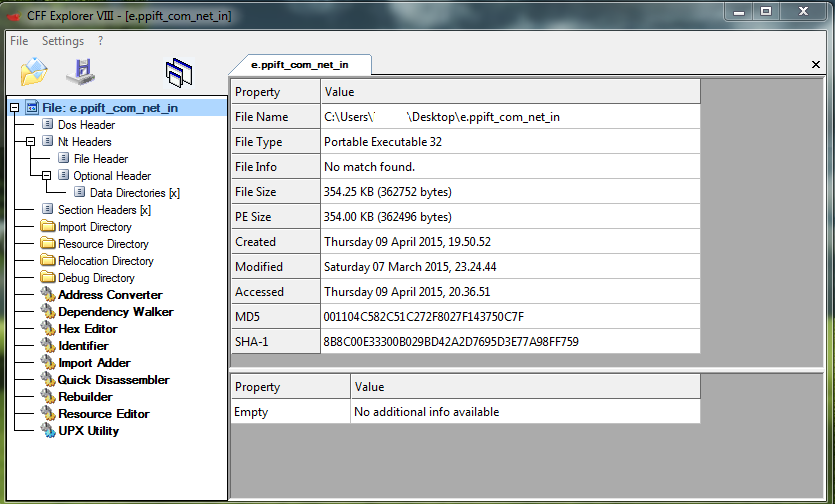
Before I run malware and make a dynamic analysis with SySAnalyzer,I open morto.exe in CFF Explorer to
see if it give us some interesting information.
As you can see :
Morto it's compiled with Microsoft Visual C++ 6.0 (but in this case you see No Match Found).
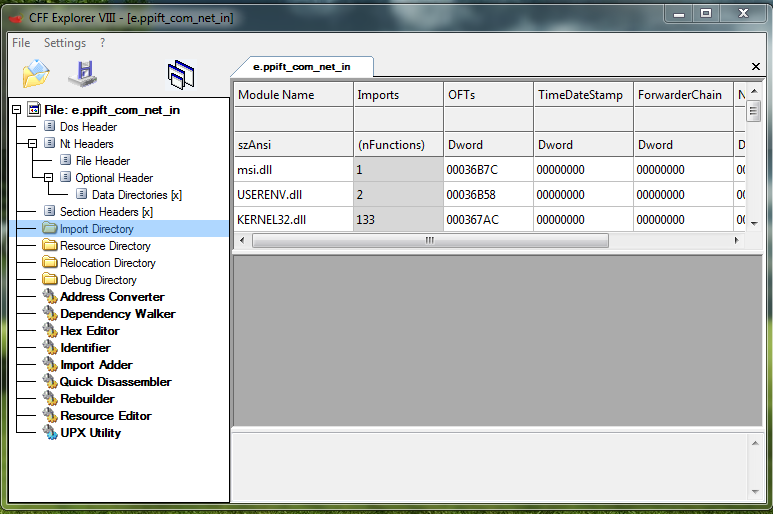
Than let's go to the Import Directory and you notice 3 imported libraries:
• msi.dll
• USERENEV.dll
• Kernel32.dll
There isn't doubt that this malware was built with MFC framework. If you don't know what is MFC framework see here :
http://en.wikipedia.org/wiki/Microsoft_Foundation_Class_Library
It isn't really good news because applications builted with MFC Framework are very boring to reverse.
Open SysAnalyzer, choose morto.exe and Start; morto.exe is running.
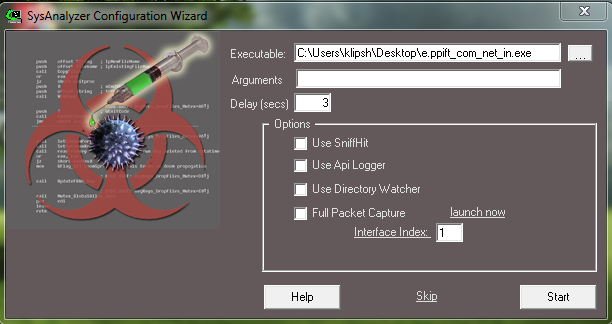
-In short:
1. morto.exe is launched;
2. Creates: 1. clb.dll in C:\WINDOWS ( this is the payload );
2. ntshrui.dll in C:\WINDOWS\temp;
3. Sens32.dll in C:\WINDOWS\system32;
4. 1.40_TestDdos in C:\WINDOWS\Offline Web Pages;
5. cache.txt in C:\WINDOWS\Offline Web Pages;
6. ~MTMP<4RandomDigits>.exe, example ~MTMP657C.exe.
3. Operates some Registry modifications: 1. rename at next reboot Sens32.dll to cache.txt through
key HKLM\SYSTEM\ControlSet001\Control\Session Manager
\PendingFileRenameOperations;
2. hides any type of error message thorugh key HKLM\SYSTEM\ControlSet001
\Control\Windows\NoPopUpsOnBoot;
3. install ntshrui.dll and Sens32.dll as service;
4. write some encrypted code in HKLM\SYSTEM\WPA\ ( This code is used then by clb.dll ).
Just for information and to clarify, clb library is a legitimate and benign Microsoft system dll which is used with regedit.exe to perform operations in Windows Registry, so the name has been chosen for this reason.
The new Morto variant mainly has added file infection capability through Code Injection but the goal is the same of the first variant; compromise RDP connections with weak Admin password.
Morto Injects its code to svchost.exe Windows OS file system, then creates a Mutex, to avoid multiple
injections to the same file, named Global\_PPIftSvc. The file
infected, after injection, has in the MZ Header PPIF string as Infection Marker.
Malicious domains contacted by Morto to download other files, updates, etc are:
--d.ppns.info e.ppift.net e.ppift.com e.ppift.in
In addition to these operations, there are no significant changes compared to the previous variant of the
malware, so this is all.
Hello, enjoy with malware analisys
Today I'm going to analyze Morto.A
It's a worm that allows unauthorized access to an infected computer and tries to compromise administrator
passwords for Remote Desktop connections, through RDP protocol, on a network.
-Malware Identification
https://www.virustotal.com/it/file/...67572f74c6fca339021f32ef844c14afff0/analysis/
SHA256: 650581122b09c12cdc2741e369fa067572f74c6fca339021f32ef844c14afff0
file name: e.ppift_com_net_in
ratio: 48 / 57
Date : 2015-03-08 10:52:34 UTC
-Tools
• CFF Explorer
• SysAnalyzer
Before I run malware and make a dynamic analysis with SySAnalyzer,I open morto.exe in CFF Explorer to
see if it give us some interesting information.
As you can see :
Morto it's compiled with Microsoft Visual C++ 6.0 (but in this case you see No Match Found).
Than let's go to the Import Directory and you notice 3 imported libraries:
• msi.dll
• USERENEV.dll
• Kernel32.dll
There isn't doubt that this malware was built with MFC framework. If you don't know what is MFC framework see here :
http://en.wikipedia.org/wiki/Microsoft_Foundation_Class_Library
It isn't really good news because applications builted with MFC Framework are very boring to reverse.
Open SysAnalyzer, choose morto.exe and Start; morto.exe is running.
-In short:
1. morto.exe is launched;
2. Creates: 1. clb.dll in C:\WINDOWS ( this is the payload );
2. ntshrui.dll in C:\WINDOWS\temp;
3. Sens32.dll in C:\WINDOWS\system32;
4. 1.40_TestDdos in C:\WINDOWS\Offline Web Pages;
5. cache.txt in C:\WINDOWS\Offline Web Pages;
6. ~MTMP<4RandomDigits>.exe, example ~MTMP657C.exe.
3. Operates some Registry modifications: 1. rename at next reboot Sens32.dll to cache.txt through
key HKLM\SYSTEM\ControlSet001\Control\Session Manager
\PendingFileRenameOperations;
2. hides any type of error message thorugh key HKLM\SYSTEM\ControlSet001
\Control\Windows\NoPopUpsOnBoot;
3. install ntshrui.dll and Sens32.dll as service;
4. write some encrypted code in HKLM\SYSTEM\WPA\ ( This code is used then by clb.dll ).
Just for information and to clarify, clb library is a legitimate and benign Microsoft system dll which is used with regedit.exe to perform operations in Windows Registry, so the name has been chosen for this reason.
The new Morto variant mainly has added file infection capability through Code Injection but the goal is the same of the first variant; compromise RDP connections with weak Admin password.
Morto Injects its code to svchost.exe Windows OS file system, then creates a Mutex, to avoid multiple
injections to the same file, named Global\_PPIftSvc. The file
infected, after injection, has in the MZ Header PPIF string as Infection Marker.
Malicious domains contacted by Morto to download other files, updates, etc are:
--d.ppns.info e.ppift.net e.ppift.com e.ppift.in
In addition to these operations, there are no significant changes compared to the previous variant of the
malware, so this is all.
Hello, enjoy with malware analisys