Hi Everyone,
I am not an expert malware reverse engineering.
I have been struggling with one sample.
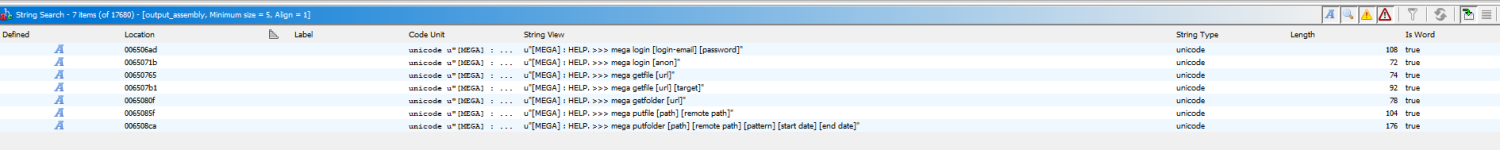
Opening it in ghidra shows me many usefull strings like "psexec", "mega login" (may be for data exfiltration)
But when i load the sample in x32dbg and try to search for strings (all modules) i cannot see the strings i saw in ghidra. (may be they are being dynamically generated)
My plan was to put a break point on them and try to analyze the stack and maybe figure our what it is doing.
Can anyone help me on how to find the strings??
I am not an expert malware reverse engineering.
I have been struggling with one sample.
Opening it in ghidra shows me many usefull strings like "psexec", "mega login" (may be for data exfiltration)
But when i load the sample in x32dbg and try to search for strings (all modules) i cannot see the strings i saw in ghidra. (may be they are being dynamically generated)
My plan was to put a break point on them and try to analyze the stack and maybe figure our what it is doing.
Can anyone help me on how to find the strings??