Zeroaccess!cfg unrepairable
- Thread starter lshendee
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hi and welcome to MalwareTips! 
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
<hr>
Download TDSSkiller from here
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
Download & SAVE to your Desktop RogueKiller or from here
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.
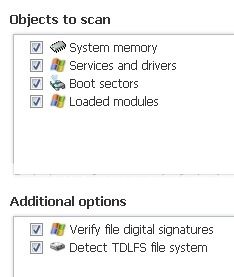
- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Good morning, Fiery. I'm buckled in and ready for the long haul. Attaching the log from TDSS. Meanwhile, I'm moving on to the next steps. Enjoy your Sunday!
~Lynne
~Lynne
Fiery said:Hi and welcome to MalwareTips!
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.

- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Attachments
Okay, Fiery. Step 2 completed and Mbar logs attached (three were created for some reason, not two). ~ Lynne
Fiery, attachment quota was exceeded so I will try to attach them to separate posts. ~ Lynne
Fiery, the larger log, "system log" appears to put me over the 1MB quota. I'll attach the smaller log then perhaps I'll need to create a new message/post in order to receive a new 1MB quota. Will try that ...
~ Lynne
Fiery, attachment quota was exceeded so I will try to attach them to separate posts. ~ Lynne
Fiery, the larger log, "system log" appears to put me over the 1MB quota. I'll attach the smaller log then perhaps I'll need to create a new message/post in order to receive a new 1MB quota. Will try that ...
~ Lynne
lshendee said:Good morning, Fiery. I'm buckled in and ready for the long haul. Attaching the log from TDSS. Meanwhile, I'm moving on to the next steps. Enjoy your Sunday!
~Lynne
Fiery said:Hi and welcome to MalwareTips!
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.

- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Attachments
While waiting to hear back about attachment quota problem, ran into problem while downloading Roguekiller. No scan window appeared but found folder on desktop "RK_quarantine" which contained the following:
[00:00:0016] ***** Global Init *****
[00:00:0016] Has crashed before : 1
[00:00:0016] Create mutex : RogueKiller
[00:00:0032] Mutex Created : 0x27c
[00:00:0032] Fill lists
Will check back in later.
~ Lynne
[00:00:0016] ***** Global Init *****
[00:00:0016] Has crashed before : 1
[00:00:0016] Create mutex : RogueKiller
[00:00:0032] Mutex Created : 0x27c
[00:00:0032] Fill lists
Will check back in later.
~ Lynne
Fiery said:Hi and welcome to MalwareTips!
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.

- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Hi again - to bypass the attachment quota issue, here is a copy/paste of the 3rd Mbar log (2 were attached earlier this morning) :
Malwarebytes Anti-Rootkit BETA 1.07.0.1005
www.malwarebytes.org
Database version: v2013.09.08.02
Windows 8 x64 NTFS
Internet Explorer 10.0.9200.16660
Lynne :: LYNNEHENDEE [administrator]
9/8/2013 8:59:20 AM
mbar-log-2013-09-08 (08-59-20).txt
Scan type: Quick scan
Scan options enabled: Anti-Rootkit | Drivers | MBR | Physical Sectors | Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken
Scan options disabled:
Objects scanned: 282187
Time elapsed: 15 minute(s), 36 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 2
HKLM\SOFTWARE\MICROSOFT\INTERNET EXPLORER\LOW RIGHTS\ELEVATIONPOLICY\{A078F691-9C07-4AF2-BF43-35E79EECF8B7} (Adware.Softomate) -> Delete on reboot.
HKLM\SYSTEM\CURRENTCONTROLSET\SERVICES\etadpug (Trojan.Zaccess) -> Delete on reboot.
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 7
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \... (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛ (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22} (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\l (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\u (Trojan.0Access) -> Delete on reboot.
C:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22} (Trojan.0Access) -> Delete on reboot.
Files Detected: 4
c:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\@ (Trojan.0Access) -> Delete on reboot.
c:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\U\00000002.@ (Trojan.0Access) -> Delete on reboot.
c:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\U\80000000.@ (Trojan.0Access) -> Delete on reboot.
c:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\U\800000cb.@ (Trojan.0Access) -> Delete on reboot.
Physical Sectors Detected: 0
(No malicious items detected)
(end)
Malwarebytes Anti-Rootkit BETA 1.07.0.1005
www.malwarebytes.org
Database version: v2013.09.08.02
Windows 8 x64 NTFS
Internet Explorer 10.0.9200.16660
Lynne :: LYNNEHENDEE [administrator]
9/8/2013 8:59:20 AM
mbar-log-2013-09-08 (08-59-20).txt
Scan type: Quick scan
Scan options enabled: Anti-Rootkit | Drivers | MBR | Physical Sectors | Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken
Scan options disabled:
Objects scanned: 282187
Time elapsed: 15 minute(s), 36 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 2
HKLM\SOFTWARE\MICROSOFT\INTERNET EXPLORER\LOW RIGHTS\ELEVATIONPOLICY\{A078F691-9C07-4AF2-BF43-35E79EECF8B7} (Adware.Softomate) -> Delete on reboot.
HKLM\SYSTEM\CURRENTCONTROLSET\SERVICES\etadpug (Trojan.Zaccess) -> Delete on reboot.
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 7
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \... (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛ (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22} (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\l (Trojan.0Access) -> Delete on reboot.
c:\program files (x86)\google\desktop\install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\u (Trojan.0Access) -> Delete on reboot.
C:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22} (Trojan.0Access) -> Delete on reboot.
Files Detected: 4
c:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\@ (Trojan.0Access) -> Delete on reboot.
c:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\U\00000002.@ (Trojan.0Access) -> Delete on reboot.
c:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\U\80000000.@ (Trojan.0Access) -> Delete on reboot.
c:\Program Files (x86)\Google\Desktop\Install\{4112d941-17ca-6eee-05f7-febb54fe5c22}\ \...\ﯹ๛\{4112d941-17ca-6eee-05f7-febb54fe5c22}\U\800000cb.@ (Trojan.0Access) -> Delete on reboot.
Physical Sectors Detected: 0
(No malicious items detected)
(end)
lshendee said:Okay, Fiery. Step 2 completed and Mbar logs attached (three were created for some reason, not two). ~ Lynne
Fiery, attachment quota was exceeded so I will try to attach them to separate posts. ~ Lynne
Fiery, the larger log, "system log" appears to put me over the 1MB quota. I'll attach the smaller log then perhaps I'll need to create a new message/post in order to receive a new 1MB quota. Will try that ...
~ Lynne
lshendee said:Good morning, Fiery. I'm buckled in and ready for the long haul. Attaching the log from TDSS. Meanwhile, I'm moving on to the next steps. Enjoy your Sunday!
~Lynne
Fiery said:Hi and welcome to MalwareTips!
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.

- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Hi,
Don't worry about the system log, we can do without that one.
Please download AdwCleaner by Xplode onto your desktop.
Next, Download Farbar Recovery Scan Tool from the below link:
<ul><li>For 64 bit systems download <a title="External link" href="http://download.bleepingcomputer.com/farbar/FRST64.exe" rel="nofollow external"><>Farbar Recovery Scan Tool x64</></a> and save it to a USB/flash drive.</li>
<li>Plug the flashdrive into the infected PC and double click on it.</li>
<li>When the tool opens click <>Yes</> to disclaimer.</li>
<li>Press <>Scan</> button.</li>
<li><>FRST</> will let you know when the scan is complete and has written the <>FRST.txt</> to file, close the message.
<li>Please copy and paste FRST.txt in your next reply</li></li>
</ol>
</ul>
Don't worry about the system log, we can do without that one.
Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
- Please post the content of that logfile with your next reply.
- You can find the logfile at C:\AdwCleaner[S1].txt
Next, Download Farbar Recovery Scan Tool from the below link:
<ul><li>For 64 bit systems download <a title="External link" href="http://download.bleepingcomputer.com/farbar/FRST64.exe" rel="nofollow external"><>Farbar Recovery Scan Tool x64</></a> and save it to a USB/flash drive.</li>
<li>Plug the flashdrive into the infected PC and double click on it.</li>
<li>When the tool opens click <>Yes</> to disclaimer.</li>
<li>Press <>Scan</> button.</li>
<li><>FRST</> will let you know when the scan is complete and has written the <>FRST.txt</> to file, close the message.
<li>Please copy and paste FRST.txt in your next reply</li></li>
</ol>
</ul>
Last edited by a moderator:
Hello Fiery - should I also click on "Fix" after the Farbar scan?I'm following exact instructions so want to be sure ...
Thanks,
~Lynne
Thanks,
~Lynne
Fiery said:Hi,
Don't worry about the system log, we can do without that one.
Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
- Please post the content of that logfile with your next reply.
- You can find the logfile at C:\AdwCleaner[S1].txt
Next, Download Farbar Recovery Scan Tool from the below link:
<ul><li>For 64 bit systems download <a title="External link" href="http://download.bleepingcomputer.com/farbar/FRST64.exe" rel="nofollow external"><>Farbar Recovery Scan Tool x64</></a> and save it to a USB/flash drive.</li>
<li>Plug the flashdrive into the infected PC and double click on it.</li>
<li>When the tool opens click <>Yes</> to disclaimer.</li>
<li>Press <>Scan</> button.</li>
<li><>FRST</> will let you know when the scan is complete and has written the <>FRST.txt</> to file, close the message.
<li>Please copy and paste FRST.txt in your next reply</li></li>
</ol>
</ul>
Last edited by a moderator:
Here are the AdwCleaner files (it stopped responding during the first clean so rescanned). ~Lynne
# AdwCleaner v3.003 - Report created 09/09/2013 at 06:08:41
# Updated 07/09/2013 by Xplode
# Operating System : Windows 8 (64 bits)
# Username : Lynne - LYNNEHENDEE
# Running from : C:\Users\Lynne\Downloads\AdwCleaner.exe
# Option : Scan
***** [ Services ] *****
***** [ Files / Folders ] *****
File Found : C:\END
File Found : C:\Users\Lynne\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\iLivid.lnk
File Found : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\user.js
File Found : C:\Users\Lynne\Desktop\iLivid.lnk
Folder Found : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Folder Found C:\Program Files (x86)\Giant Savings Extension
Folder Found C:\ProgramData\Ask
Folder Found C:\Users\Lynne\AppData\Local\DownloadTerms
Folder Found C:\Users\Lynne\AppData\Local\Giant Savings Extension
Folder Found C:\Users\Lynne\AppData\Local\Ilivid
***** [ Shortcuts ] *****
***** [ Registry ] *****
Key Found : HKCU\Software\AppDataLow\Software\Crossrider
Key Found : HKCU\Software\AppDataLow\Software\Giant Savings Extension
Key Found : HKCU\Software\Cr_Installer
Key Found : HKCU\Software\ilivid
Key Found : HKCU\Software\InstalledBrowserExtensions
Key Found : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Found : HKCU\Software\Softonic
Key Found : [x64] HKCU\Software\Cr_Installer
Key Found : [x64] HKCU\Software\ilivid
Key Found : [x64] HKCU\Software\InstalledBrowserExtensions
Key Found : [x64] HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Found : [x64] HKCU\Software\Softonic
Key Found : HKLM\SOFTWARE\Classes\Applications\ilividsetup.exe
Key Found : HKLM\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Found : HKLM\SOFTWARE\Classes\Interface\{79FB5FC8-44B9-4AF5-BADD-CCE547F953E5}
Key Found : HKLM\SOFTWARE\Google\Chrome\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Giant Savings Extension
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ilivid
Key Found : [x64] HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{A5AA24EA-11B8-4113-95AE-9ED71DEAF12A}
***** [ Browsers ] *****
-\\ Internet Explorer v10.0.9200.16660
-\\ Mozilla Firefox v20.0.1 (en-US)
[ File : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\prefs.js ]
-\\ Google Chrome v29.0.1547.66
[ File : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\preferences ]
Found : icon_url
Found : search_url
Found : suggest_url
Found : keyword
Found : search_url
Found : suggest_url
[ File : C:\Users\Mackinaw\AppData\Local\Google\Chrome\User Data\Default\preferences ]
# AdwCleaner v3.003 - Report created 09/09/2013 at 06:15:00
# Updated 07/09/2013 by Xplode
# Operating System : Windows 8 (64 bits)
# Username : Lynne - LYNNEHENDEE
# Running from : C:\Users\Lynne\Downloads\AdwCleaner.exe
# Option : Scan
***** [ Services ] *****
***** [ Files / Folders ] *****
File Found : C:\END
File Found : C:\Users\Lynne\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\iLivid.lnk
File Found : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\user.js
File Found : C:\Users\Lynne\Desktop\iLivid.lnk
Folder Found : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Folder Found C:\Users\Lynne\AppData\Local\Ilivid
***** [ Shortcuts ] *****
***** [ Registry ] *****
Key Found : HKCU\Software\AppDataLow\Software\Crossrider
Key Found : HKCU\Software\AppDataLow\Software\Giant Savings Extension
Key Found : HKCU\Software\Cr_Installer
Key Found : HKCU\Software\ilivid
Key Found : HKCU\Software\InstalledBrowserExtensions
Key Found : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Found : HKCU\Software\Softonic
Key Found : [x64] HKCU\Software\Cr_Installer
Key Found : [x64] HKCU\Software\ilivid
Key Found : [x64] HKCU\Software\InstalledBrowserExtensions
Key Found : [x64] HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Found : [x64] HKCU\Software\Softonic
Key Found : HKLM\SOFTWARE\Classes\Applications\ilividsetup.exe
Key Found : HKLM\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Found : HKLM\SOFTWARE\Classes\Interface\{79FB5FC8-44B9-4AF5-BADD-CCE547F953E5}
Key Found : HKLM\SOFTWARE\Google\Chrome\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Giant Savings Extension
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ilivid
Key Found : [x64] HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{A5AA24EA-11B8-4113-95AE-9ED71DEAF12A}
***** [ Browsers ] *****
-\\ Internet Explorer v10.0.9200.16660
-\\ Mozilla Firefox v20.0.1 (en-US)
[ File : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\prefs.js ]
-\\ Google Chrome v29.0.1547.66
[ File : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\preferences ]
Found : icon_url
Found : search_url
Found : suggest_url
Found : keyword
Found : search_url
Found : suggest_url
[ File : C:\Users\Mackinaw\AppData\Local\Google\Chrome\User Data\Default\preferences ]
*************************
AdwCleaner[R0].txt - [3176 octets] - [09/09/2013 06:08:41]
AdwCleaner[R1].txt - [2854 octets] - [09/09/2013 06:15:00]
AdwCleaner[S0].txt - [547 octets] - [09/09/2013 06:10:48]
########## EOF - C:\AdwCleaner\AdwCleaner[R1].txt - [2973 octets] ##########
# AdwCleaner v3.003 - Report created 09/09/2013 at 06:10:48
# Updated 07/09/2013 by Xplode
# Operating System : Windows 8 (64 bits)
# Username : Lynne - LYNNEHENDEE
# Running from : C:\Users\Lynne\Downloads\AdwCleaner.exe
# Option : Clean
***** [ Services ] *****
***** [ Files / Folders ] *****
Folder Deleted : C:\ProgramData\Ask
Folder Deleted : C:\Program Files (x86)\Giant Savings Extension
Folder Deleted : C:\Users\Lynne\AppData\Local\DownloadTerms
Folder Deleted : C:\Users\Lynne\AppData\Local\Giant Savings Extension
# AdwCleaner v3.003 - Report created 09/09/2013 at 06:15:40
# Updated 07/09/2013 by Xplode
# Operating System : Windows 8 (64 bits)
# Username : Lynne - LYNNEHENDEE
# Running from : C:\Users\Lynne\Downloads\AdwCleaner.exe
# Option : Clean
***** [ Services ] *****
***** [ Files / Folders ] *****
Folder Deleted : C:\Users\Lynne\AppData\Local\Ilivid
Folder Deleted : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\halffneccaebicfdfajnbfgpglahfgoe
File Deleted : C:\END
File Deleted : C:\Users\Lynne\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\iLivid.lnk
File Deleted : C:\Users\Lynne\Desktop\iLivid.lnk
File Deleted : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\user.js
***** [ Shortcuts ] *****
***** [ Registry ] *****
Key Deleted : HKLM\SOFTWARE\Google\Chrome\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Key Deleted : HKLM\SOFTWARE\Classes\Applications\ilividsetup.exe
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Deleted : HKLM\SOFTWARE\Classes\Interface\{79FB5FC8-44B9-4AF5-BADD-CCE547F953E5}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Deleted : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Deleted : [x64] HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{A5AA24EA-11B8-4113-95AE-9ED71DEAF12A}
Key Deleted : HKCU\Software\Cr_Installer
Key Deleted : HKCU\Software\ilivid
Key Deleted : HKCU\Software\InstalledBrowserExtensions
Key Deleted : HKCU\Software\Softonic
Key Deleted : HKCU\Software\AppDataLow\Software\Crossrider
Key Deleted : HKCU\Software\AppDataLow\Software\Giant Savings Extension
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Giant Savings Extension
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ilivid
***** [ Browsers ] *****
-\\ Internet Explorer v10.0.9200.16660
-\\ Mozilla Firefox v20.0.1 (en-US)
[ File : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\prefs.js ]
-\\ Google Chrome v29.0.1547.66
[ File : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\preferences ]
Deleted : icon_url
Deleted : search_url
Deleted : suggest_url
Deleted : keyword
[ File : C:\Users\Mackinaw\AppData\Local\Google\Chrome\User Data\Default\preferences ]
*************************
AdwCleaner[R0].txt - [3176 octets] - [09/09/2013 06:08:41]
AdwCleaner[R1].txt - [3077 octets] - [09/09/2013 06:15:00]
AdwCleaner[S0].txt - [547 octets] - [09/09/2013 06:10:48]
AdwCleaner[S1].txt - [2704 octets] - [09/09/2013 06:15:40]
########## EOF - C:\AdwCleaner\AdwCleaner[S1].txt - [2764 octets] ##########
# AdwCleaner v3.003 - Report created 09/09/2013 at 06:08:41
# Updated 07/09/2013 by Xplode
# Operating System : Windows 8 (64 bits)
# Username : Lynne - LYNNEHENDEE
# Running from : C:\Users\Lynne\Downloads\AdwCleaner.exe
# Option : Scan
***** [ Services ] *****
***** [ Files / Folders ] *****
File Found : C:\END
File Found : C:\Users\Lynne\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\iLivid.lnk
File Found : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\user.js
File Found : C:\Users\Lynne\Desktop\iLivid.lnk
Folder Found : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Folder Found C:\Program Files (x86)\Giant Savings Extension
Folder Found C:\ProgramData\Ask
Folder Found C:\Users\Lynne\AppData\Local\DownloadTerms
Folder Found C:\Users\Lynne\AppData\Local\Giant Savings Extension
Folder Found C:\Users\Lynne\AppData\Local\Ilivid
***** [ Shortcuts ] *****
***** [ Registry ] *****
Key Found : HKCU\Software\AppDataLow\Software\Crossrider
Key Found : HKCU\Software\AppDataLow\Software\Giant Savings Extension
Key Found : HKCU\Software\Cr_Installer
Key Found : HKCU\Software\ilivid
Key Found : HKCU\Software\InstalledBrowserExtensions
Key Found : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Found : HKCU\Software\Softonic
Key Found : [x64] HKCU\Software\Cr_Installer
Key Found : [x64] HKCU\Software\ilivid
Key Found : [x64] HKCU\Software\InstalledBrowserExtensions
Key Found : [x64] HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Found : [x64] HKCU\Software\Softonic
Key Found : HKLM\SOFTWARE\Classes\Applications\ilividsetup.exe
Key Found : HKLM\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Found : HKLM\SOFTWARE\Classes\Interface\{79FB5FC8-44B9-4AF5-BADD-CCE547F953E5}
Key Found : HKLM\SOFTWARE\Google\Chrome\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Giant Savings Extension
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ilivid
Key Found : [x64] HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{A5AA24EA-11B8-4113-95AE-9ED71DEAF12A}
***** [ Browsers ] *****
-\\ Internet Explorer v10.0.9200.16660
-\\ Mozilla Firefox v20.0.1 (en-US)
[ File : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\prefs.js ]
-\\ Google Chrome v29.0.1547.66
[ File : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\preferences ]
Found : icon_url
Found : search_url
Found : suggest_url
Found : keyword
Found : search_url
Found : suggest_url
[ File : C:\Users\Mackinaw\AppData\Local\Google\Chrome\User Data\Default\preferences ]
# AdwCleaner v3.003 - Report created 09/09/2013 at 06:15:00
# Updated 07/09/2013 by Xplode
# Operating System : Windows 8 (64 bits)
# Username : Lynne - LYNNEHENDEE
# Running from : C:\Users\Lynne\Downloads\AdwCleaner.exe
# Option : Scan
***** [ Services ] *****
***** [ Files / Folders ] *****
File Found : C:\END
File Found : C:\Users\Lynne\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\iLivid.lnk
File Found : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\user.js
File Found : C:\Users\Lynne\Desktop\iLivid.lnk
Folder Found : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Folder Found C:\Users\Lynne\AppData\Local\Ilivid
***** [ Shortcuts ] *****
***** [ Registry ] *****
Key Found : HKCU\Software\AppDataLow\Software\Crossrider
Key Found : HKCU\Software\AppDataLow\Software\Giant Savings Extension
Key Found : HKCU\Software\Cr_Installer
Key Found : HKCU\Software\ilivid
Key Found : HKCU\Software\InstalledBrowserExtensions
Key Found : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Found : HKCU\Software\Softonic
Key Found : [x64] HKCU\Software\Cr_Installer
Key Found : [x64] HKCU\Software\ilivid
Key Found : [x64] HKCU\Software\InstalledBrowserExtensions
Key Found : [x64] HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Found : [x64] HKCU\Software\Softonic
Key Found : HKLM\SOFTWARE\Classes\Applications\ilividsetup.exe
Key Found : HKLM\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Found : HKLM\SOFTWARE\Classes\Interface\{79FB5FC8-44B9-4AF5-BADD-CCE547F953E5}
Key Found : HKLM\SOFTWARE\Google\Chrome\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Giant Savings Extension
Key Found : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ilivid
Key Found : [x64] HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{A5AA24EA-11B8-4113-95AE-9ED71DEAF12A}
***** [ Browsers ] *****
-\\ Internet Explorer v10.0.9200.16660
-\\ Mozilla Firefox v20.0.1 (en-US)
[ File : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\prefs.js ]
-\\ Google Chrome v29.0.1547.66
[ File : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\preferences ]
Found : icon_url
Found : search_url
Found : suggest_url
Found : keyword
Found : search_url
Found : suggest_url
[ File : C:\Users\Mackinaw\AppData\Local\Google\Chrome\User Data\Default\preferences ]
*************************
AdwCleaner[R0].txt - [3176 octets] - [09/09/2013 06:08:41]
AdwCleaner[R1].txt - [2854 octets] - [09/09/2013 06:15:00]
AdwCleaner[S0].txt - [547 octets] - [09/09/2013 06:10:48]
########## EOF - C:\AdwCleaner\AdwCleaner[R1].txt - [2973 octets] ##########
# AdwCleaner v3.003 - Report created 09/09/2013 at 06:10:48
# Updated 07/09/2013 by Xplode
# Operating System : Windows 8 (64 bits)
# Username : Lynne - LYNNEHENDEE
# Running from : C:\Users\Lynne\Downloads\AdwCleaner.exe
# Option : Clean
***** [ Services ] *****
***** [ Files / Folders ] *****
Folder Deleted : C:\ProgramData\Ask
Folder Deleted : C:\Program Files (x86)\Giant Savings Extension
Folder Deleted : C:\Users\Lynne\AppData\Local\DownloadTerms
Folder Deleted : C:\Users\Lynne\AppData\Local\Giant Savings Extension
# AdwCleaner v3.003 - Report created 09/09/2013 at 06:15:40
# Updated 07/09/2013 by Xplode
# Operating System : Windows 8 (64 bits)
# Username : Lynne - LYNNEHENDEE
# Running from : C:\Users\Lynne\Downloads\AdwCleaner.exe
# Option : Clean
***** [ Services ] *****
***** [ Files / Folders ] *****
Folder Deleted : C:\Users\Lynne\AppData\Local\Ilivid
Folder Deleted : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\halffneccaebicfdfajnbfgpglahfgoe
File Deleted : C:\END
File Deleted : C:\Users\Lynne\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\iLivid.lnk
File Deleted : C:\Users\Lynne\Desktop\iLivid.lnk
File Deleted : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\user.js
***** [ Shortcuts ] *****
***** [ Registry ] *****
Key Deleted : HKLM\SOFTWARE\Google\Chrome\Extensions\halffneccaebicfdfajnbfgpglahfgoe
Key Deleted : HKLM\SOFTWARE\Classes\Applications\ilividsetup.exe
Key Deleted : HKLM\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Deleted : HKLM\SOFTWARE\Classes\Interface\{79FB5FC8-44B9-4AF5-BADD-CCE547F953E5}
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}
Key Deleted : HKCU\Software\Microsoft\Internet Explorer\SearchScopes\{171DEBEB-C3D4-40B7-AC73-056A5EBA4A7E}
Key Deleted : [x64] HKLM\SOFTWARE\Microsoft\Internet Explorer\Low Rights\ElevationPolicy\{A5AA24EA-11B8-4113-95AE-9ED71DEAF12A}
Key Deleted : HKCU\Software\Cr_Installer
Key Deleted : HKCU\Software\ilivid
Key Deleted : HKCU\Software\InstalledBrowserExtensions
Key Deleted : HKCU\Software\Softonic
Key Deleted : HKCU\Software\AppDataLow\Software\Crossrider
Key Deleted : HKCU\Software\AppDataLow\Software\Giant Savings Extension
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Giant Savings Extension
Key Deleted : HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\ilivid
***** [ Browsers ] *****
-\\ Internet Explorer v10.0.9200.16660
-\\ Mozilla Firefox v20.0.1 (en-US)
[ File : C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default\prefs.js ]
-\\ Google Chrome v29.0.1547.66
[ File : C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\preferences ]
Deleted : icon_url
Deleted : search_url
Deleted : suggest_url
Deleted : keyword
[ File : C:\Users\Mackinaw\AppData\Local\Google\Chrome\User Data\Default\preferences ]
*************************
AdwCleaner[R0].txt - [3176 octets] - [09/09/2013 06:08:41]
AdwCleaner[R1].txt - [3077 octets] - [09/09/2013 06:15:00]
AdwCleaner[S0].txt - [547 octets] - [09/09/2013 06:10:48]
AdwCleaner[S1].txt - [2704 octets] - [09/09/2013 06:15:40]
########## EOF - C:\AdwCleaner\AdwCleaner[S1].txt - [2764 octets] ##########
Fiery said:Hi,
Don't worry about the system log, we can do without that one.
Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
- Please post the content of that logfile with your next reply.
- You can find the logfile at C:\AdwCleaner[S1].txt
Next, Download Farbar Recovery Scan Tool from the below link:
<ul><li>For 64 bit systems download <a title="External link" href="http://download.bleepingcomputer.com/farbar/FRST64.exe" rel="nofollow external"><>Farbar Recovery Scan Tool x64</></a> and save it to a USB/flash drive.</li>
<li>Plug the flashdrive into the infected PC and double click on it.</li>
<li>When the tool opens click <>Yes</> to disclaimer.</li>
<li>Press <>Scan</> button.</li>
<li><>FRST</> will let you know when the scan is complete and has written the <>FRST.txt</> to file, close the message.
<li>Please copy and paste FRST.txt in your next reply</li></li>
</ol>
</ul>
Last edited by a moderator:
Scan result of Farbar Recovery Scan Tool (FRST.txt) (x64) Version: 09-09-2013
Ran by Lynne (administrator) on LYNNEHENDEE on 09-09-2013 06:32:11
Running from E:\
Windows 8 (X64) OS Language: English(US)
Internet Explorer Version 10
Boot Mode: Normal
==================== Processes (Whitelisted) =================
(IvoSoft) C:\Program Files\Classic Shell\ClassicShellService.exe
() C:\Program Files (x86)\Roxio\BackOnTrack\App\SaibSVC.exe
(ArcSoft Inc.) C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACService.exe
(Apple Inc.) C:\Program Files (x86)\Common Files\Apple\Mobile Device Support\AppleMobileDeviceService.exe
(Apple Inc.) C:\Program Files\Bonjour\mDNSResponder.exe
() C:\Program Files (x86)\Roxio\BackOnTrack\App\BService.exe
(Microsoft Corporation) C:\Windows\system32\dashost.exe
(Juniper Networks) C:\Program Files (x86)\Juniper Networks\Common Files\dsNcService.exe
(LogMeIn Inc.) C:\Program Files (x86)\LogMeIn Hamachi\hamachi-2.exe
(Intel(R) Corporation) c:\Program Files\Intel\iCLS Client\HeciServer.exe
(Intel Corporation) C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\DAL\jhi_service.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe
(McAfee, Inc.) C:\Windows\system32\mfevtps.exe
() C:\Program Files (x86)\CyberLink\Shared files\RichVideo.exe
(IvoSoft) C:\Program Files\Classic Shell\ClassicStartMenu.exe
(Sendori) C:\Program Files (x86)\Sendori\sndappv2.exe
(TeamViewer GmbH) C:\Program Files (x86)\TeamViewer\Version8\TeamViewer_Service.exe
(Atheros) C:\Program Files (x86)\Dell Wireless\Ath_WlanAgent.exe
(Sendori, Inc.) C:\Program Files (x86)\Sendori\SendoriSvc.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\AMCore\mcshield.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\SystemCore\mfefire.exe
(sendori) C:\Program Files (x86)\Sendori\Sendori.Service.exe
(Sendori, Inc.) C:\Program Files (x86)\Sendori\SendoriUp.exe
(McAfee, Inc.) C:\PROGRA~1\McAfee\MSC\McAPExe.exe
(Microsoft Corporation) C:\Program Files\WindowsApps\microsoft.windowscommunicationsapps_16.4.4206.722_x64__8wekyb3d8bbwe\LiveComm.exe
(Intel Corporation) C:\Program Files (x86)\Intel\Intel(R) Rapid Storage Technology\IAStorDataMgrSvc.exe
(Intel Corporation) C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\LMS\LMS.exe
() C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Roxio Burn\RoxioBurnLauncher.exe
(SoftThinks SAS) C:\Program Files (x86)\Dell Backup and Recovery\SftService.exe
(Intel Corporation) C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\UNS\UNS.exe
(Microsoft Corporation) C:\Windows\system32\prevhost.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\Platform\mcuicnt.exe
(Microsoft Corporation) C:\Program Files\Common Files\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE
(McAfee, Inc.) c:\PROGRA~2\mcafee\SITEAD~1\saui.exe
(SoftThinks - Dell) C:\Program Files (x86)\Dell Backup and Recovery\TOASTER.EXE
(SoftThinks - Dell) C:\Program Files (x86)\Dell Backup and Recovery\Components\DBRUpdate\DBRUpd.exe
(McAfee, Inc.) c:\PROGRA~1\mcafee\VIRUSS~1\mcvsshld.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\Platform\Core\mchost.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\Platform\Core\mchost.exe
(Microsoft Corporation) C:\Windows\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_6.2.9200.16613_none_6273bd8950d6cae2\TiWorker.exe
==================== Registry (Whitelisted) ==================
HKLM\...\Run: [HotKeysCmds] - C:\Windows\system32\hkcmd.exe [ ] ()
HKLM\...\Run: [CanonMyPrinter] - C:\Program Files\Canon\MyPrinter\BJMyPrt.exe [2726728 2010-03-24] (CANON INC.)
HKLM\...\Policies\Explorer: [NoActiveDesktop] 1
HKLM\...\Policies\Explorer: [NoControlPanel] 0
HKCU\...\Run: [MyTomTomSA.exe] - C:\Program Files (x86)\MyTomTom 3\MyTomTomSA.exe [451656 2013-01-07] (TomTom)
HKCU\...\Run: [GoogleChromeAutoLaunch_6A12F0BBFE608579AB07135F9DFD76FE] - C:\Program Files (x86)\Google\Chrome\Application\chrome.exe [829392 2013-09-02] (Google Inc.)
MountPoints2: {67ec6cba-6534-11e2-be78-7845c4380f68} - "H:\MI.exe"
HKLM-x32\...\Run: [IMSS] - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IMSS\PIconStartup.exe [133440 2012-07-19] (Intel Corporation)
HKLM-x32\...\Run: [IAStorIcon] - C:\Program Files (x86)\Intel\Intel(R) Rapid Storage Technology\IAStorIcon.exe [277504 2012-07-09] (Intel Corporation)
HKLM-x32\...\Run: [CLMLServer_For_P2G8] - C:\Program Files (x86)\CyberLink\Power2Go8\CLMLSvc_P2G8.exe [111120 2012-06-07] (CyberLink)
HKLM-x32\...\Run: [CLVirtualDrive] - C:\Program Files (x86)\CyberLink\Power2Go8\VirtualDrive.exe [491120 2012-07-04] (CyberLink Corp.)
HKLM-x32\...\Run: [RemoteControl10] - C:\Program Files (x86)\CyberLink\PowerDVD10\PDVD10Serv.exe [143888 2012-06-01] (CyberLink Corp.)
HKLM-x32\...\Run: [BCSSync] - C:\Program Files (x86)\Microsoft Office\Office14\BCSSync.exe [91520 2010-03-13] (Microsoft Corporation)
HKLM-x32\...\Run: [Sendori Tray] - C:\Program Files (x86)\Sendori\SendoriTray.exe [83232 2013-07-01] (Sendori, Inc.)
HKLM-x32\...\Run: [APSDaemon] - C:\Program Files (x86)\Common Files\Apple\Apple Application Support\APSDaemon.exe [59720 2013-01-28] (Apple Inc.)
HKLM-x32\...\Run: [Adobe ARM] - C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe [946352 2012-12-18] (Adobe Systems Incorporated)
HKLM-x32\...\Run: [ArcSoft Connection Service] - C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACDaemon.exe [207424 2010-10-27] (ArcSoft Inc.)
HKLM-x32\...\Run: [QuickTime Task] - C:\Program Files (x86)\QuickTime\QTTask.exe [421888 2012-10-25] (Apple Inc.)
HKLM-x32\...\Run: [iTunesHelper] - C:\Program Files (x86)\iTunes\iTunesHelper.exe [152392 2013-02-20] (Apple Inc.)
HKLM-x32\...\Run: [ISUSPM] - C:\ProgramData\FLEXnet\Connect\11\\isuspm.exe [324976 2010-05-21] (Flexera Software, Inc.)
HKLM-x32\...\Run: [RoxWatchTray] - C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Common\RoxWatchTray14.exe [294032 2012-11-29] (Corel Corporation)
HKLM-x32\...\Run: [CanonSolutionMenuEx] - C:\Program Files (x86)\Canon\Solution Menu EX\CNSEMAIN.EXE [1185112 2010-04-02] (CANON INC.)
HKLM-x32\...\Run: [LogMeIn Hamachi Ui] - C:\Program Files (x86)\LogMeIn Hamachi\hamachi-2-ui.exe [2255184 2013-05-15] (LogMeIn Inc.)
HKLM-x32\...\Run: [SunJavaUpdateSched] - C:\Program Files (x86)\Common Files\Java\Java Update\jusched.exe [253816 2013-03-12] (Oracle Corporation)
HKLM-x32\...\Run: [mcpltui_exe] - C:\Program Files\McAfee.com\Agent\mcagent.exe [454600 2013-02-28] (McAfee, Inc.)
HKU\Mackinaw\...\Run: [MyTomTomSA.exe] - C:\Program Files (x86)\MyTomTom 3\MyTomTomSA.exe [451656 2013-01-07] (TomTom)
IMEO\sidebar.exe: [Debugger] C:\Program Files (x86)\Windows Sidebar\8GadgetPack.exe -run
Startup: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\Adobe Gamma Loader.lnk
ShortcutTarget: Adobe Gamma Loader.lnk -> C:\Program Files (x86)\Common Files\Adobe\Calibration\Adobe Gamma Loader.exe (Adobe Systems, Inc.)
==================== Internet (Whitelisted) ====================
HKCU\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://dell13.msn.com
HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://dell13.msn.com/
HKCU\Software\Microsoft\Internet Explorer\Main,Start Page Redirect Cache = http://www.msn.com/?ocid=iehp
SearchScopes: HKLM - DefaultScope {0633EE93-D776-472f-A0FF-E1416B8B2E3A} URL = http://search.live.com/results.aspx?q={searchTerms}&src={referrer:source?}
SearchScopes: HKLM - {0633EE93-D776-472f-A0FF-E1416B8B2E3A} URL = http://search.live.com/results.aspx?q={searchTerms}&src={referrer:source?}
SearchScopes: HKLM - {7E492935-6215-4766-95F8-83CA18516A2B} URL = http://www.bing.com/search?q={searchTerms}&form=IE10TR&src=IE10TR&pc=MDDCJS
SearchScopes: HKLM-x32 - {7E492935-6215-4766-95F8-83CA18516A2B} URL = http://www.bing.com/search?q={searchTerms}&form=IE10TR&src=IE10TR&pc=MDDCJS
SearchScopes: HKCU - {7E492935-6215-4766-95F8-83CA18516A2B} URL =
SearchScopes: HKCU - {FA533155-F2FE-4486-842E-089EA28D3653} URL = http://search.yahoo.com/search?fr=mcafee&p={SearchTerms}
BHO: ExplorerBHO Class - {449D0D6E-2412-4E61-B68F-1CB625CD9E52} - C:\Program Files\Classic Shell\ClassicExplorer64.dll (IvoSoft)
BHO: Groove GFS Browser Helper - {72853161-30C5-4D22-B7F9-0BBC1D38A37E} - C:\Program Files\Microsoft Office\Office14\GROOVEEX.DLL (Microsoft Corporation)
BHO: Java(tm) Plug-In SSV Helper - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files\Java\jre7\bin\ssv.dll (Oracle Corporation)
BHO: McAfee SiteAdvisor BHO - {B164E929-A1B6-4A06-B104-2CD0E90A88FF} - C:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.)
BHO: Office Document Cache Handler - {B4F3A835-0E21-4959-BA22-42B3008E02FF} - C:\Program Files\Microsoft Office\Office14\URLREDIR.DLL (Microsoft Corporation)
BHO: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre7\bin\jp2ssv.dll (Oracle Corporation)
BHO: ClassicIE9BHO Class - {EA801577-E6AD-4BD5-8F71-4BE0154331A4} - C:\Program Files\Classic Shell\ClassicIE9DLL_64.dll (IvoSoft)
BHO-x32: Adobe PDF Link Helper - {18DF081C-E8AD-4283-A596-FA578C2EBDC3} - C:\Program Files (x86)\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelperShim.dll (Adobe Systems Incorporated)
BHO-x32: ExplorerBHO Class - {449D0D6E-2412-4E61-B68F-1CB625CD9E52} - C:\Program Files\Classic Shell\ClassicExplorer32.dll (IvoSoft)
BHO-x32: Groove GFS Browser Helper - {72853161-30C5-4D22-B7F9-0BBC1D38A37E} - C:\Program Files (x86)\Microsoft Office\Office14\GROOVEEX.DLL (Microsoft Corporation)
BHO-x32: Java(tm) Plug-In SSV Helper - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files (x86)\Java\jre7\bin\ssv.dll (Oracle Corporation)
BHO-x32: McAfee SiteAdvisor BHO - {B164E929-A1B6-4A06-B104-2CD0E90A88FF} - C:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.)
BHO-x32: Office Document Cache Handler - {B4F3A835-0E21-4959-BA22-42B3008E02FF} - C:\Program Files (x86)\Microsoft Office\Office14\URLREDIR.DLL (Microsoft Corporation)
BHO-x32: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files (x86)\Java\jre7\bin\jp2ssv.dll (Oracle Corporation)
BHO-x32: ClassicIE9BHO Class - {EA801577-E6AD-4BD5-8F71-4BE0154331A4} - C:\Program Files\Classic Shell\ClassicIE9DLL_32.dll (IvoSoft)
Toolbar: HKLM - Classic Explorer Bar - {553891B7-A0D5-4526-BE18-D3CE461D6310} - C:\Program Files\Classic Shell\ClassicExplorer64.dll (IvoSoft)
Toolbar: HKLM - McAfee SiteAdvisor Toolbar - {0EBBBE48-BAD4-4B4C-8E5A-516ABECAE064} - C:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.)
Toolbar: HKLM-x32 - Classic Explorer Bar - {553891B7-A0D5-4526-BE18-D3CE461D6310} - C:\Program Files\Classic Shell\ClassicExplorer32.dll (IvoSoft)
Toolbar: HKLM-x32 - McAfee SiteAdvisor Toolbar - {0EBBBE48-BAD4-4B4C-8E5A-516ABECAE064} - C:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.)
DPF: HKLM {AA570693-00E2-4907-B6F1-60A1199B030C} https://juniper.net/dana-cached/sc/JuniperSetupClient64.cab
DPF: HKLM-x32 {F27237D7-93C8-44C2-AC6E-D6057B9A918F} https://juniper.net/dana-cached/sc/JuniperSetupClient.cab
Handler: dssrequest - {5513F07E-936B-4E52-9B00-067394E91CC5} - C:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.)
Handler: sacore - {5513F07E-936B-4E52-9B00-067394E91CC5} - C:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.)
Handler-x32: dssrequest - {5513F07E-936B-4E52-9B00-067394E91CC5} - C:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.)
Handler-x32: sacore - {5513F07E-936B-4E52-9B00-067394E91CC5} - C:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.)
Filter: application/x-mfe-ipt - {3EF5086B-5478-4598-A054-786C45D75692} - C:\Program Files\McAfee\MSC\McSnIePl64.dll (McAfee, Inc.)
Filter-x32: application/x-mfe-ipt - {3EF5086B-5478-4598-A054-786C45D75692} - C:\Program Files (x86)\McAfee\MSC\McSnIePl.dll (McAfee, Inc.)
FireFox:
========
FF ProfilePath: C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default
FF Plugin: @adobe.com/FlashPlayer - C:\Windows\system32\Macromed\Flash\NPSWF64_11_5_502_146.dll ()
FF Plugin: @java.com/DTPlugin,version=10.11.2 - C:\Windows\system32\npDeployJava1.dll (Oracle Corporation)
FF Plugin: @java.com/JavaPlugin,version=10.11.2 - C:\Program Files\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation)
FF Plugin: @mcafee.com/MSC,version=10 - c:\PROGRA~1\mcafee\msc\NPMCSN~1.DLL ()
FF Plugin: @microsoft.com/OfficeAuthz,version=14.0 - C:\PROGRA~1\MICROS~1\Office14\NPAUTHZ.DLL (Microsoft Corporation)
FF Plugin-x32: @adobe.com/FlashPlayer - C:\Windows\SysWOW64\Macromed\Flash\NPSWF32_11_5_502_146.dll ()
FF Plugin-x32: @adobe.com/ShockwavePlayer - C:\Windows\SysWOW64\Adobe\Director\np32dsw_1203133.dll (Adobe Systems, Inc.)
FF Plugin-x32: @Apple.com/iTunes,version=1.0 - C:\Program Files (x86)\iTunes\Mozilla Plugins\npitunes.dll ()
FF Plugin-x32: @canon.com/EPPEX - C:\Program Files (x86)\Canon\Easy-PhotoPrint EX\NPEZFFPI.DLL (CANON INC.)
FF Plugin-x32: @intel-webapi.intel.com/Intel WebAPI ipt;version=2.1.42 - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IPT\npIntelWebAPIIPT.dll (Intel Corporation)
FF Plugin-x32: @intel-webapi.intel.com/Intel WebAPI updater - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IPT\npIntelWebAPIUpdater.dll (Intel Corporation)
FF Plugin-x32: @java.com/DTPlugin,version=10.25.2 - C:\Windows\SysWOW64\npDeployJava1.dll (Oracle Corporation)
FF Plugin-x32: @java.com/JavaPlugin,version=10.25.2 - C:\Program Files (x86)\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation)
FF Plugin-x32: @mcafee.com/MSC,version=10 - c:\PROGRA~2\mcafee\msc\NPMCSN~1.DLL ()
FF Plugin-x32: @mcafee.com/SAFFPlugin - C:\Program Files (x86)\McAfee\SiteAdvisor\npmcffplg32.dll (McAfee, Inc.)
FF Plugin-x32: @microsoft.com/OfficeAuthz,version=14.0 - C:\PROGRA~2\MICROS~1\Office14\NPAUTHZ.DLL (Microsoft Corporation)
FF Plugin-x32: @microsoft.com/SharePoint,version=14.0 - C:\PROGRA~2\MICROS~1\Office14\NPSPWRAP.DLL (Microsoft Corporation)
FF Plugin-x32: @microsoft.com/WLPG,version=16.4.3505.0912 - C:\Program Files (x86)\Windows Live\Photo Gallery\NPWLPG.dll (Microsoft Corporation)
FF Plugin-x32: @tools.google.com/Google Update;version=3 - C:\Program Files (x86)\Google\Update\1.3.21.153\npGoogleUpdate3.dll (Google Inc.)
FF Plugin-x32: @tools.google.com/Google Update;version=9 - C:\Program Files (x86)\Google\Update\1.3.21.153\npGoogleUpdate3.dll (Google Inc.)
FF Plugin-x32: Adobe Reader - C:\Program Files (x86)\Adobe\Reader 11.0\Reader\AIR\nppdf32.dll (Adobe Systems Inc.)
FF Plugin HKCU: @nsroblox.roblox.com/launcher - C:\Users\Lynne\AppData\Local\Roblox\Versions\version-759151294bb84441\\NPRobloxProxy.dll ( ROBLOX Corporation)
FF Extension: DownloadTerms - C:\Program Files (x86)\Mozilla Firefox\extensions\jmwgabsbmtxairm@wzcttjml.com
FF HKLM-x32\...\Firefox\Extensions: [{4ED1F68A-5463-4931-9384-8FFF5ED91D92}] C:\Program Files (x86)\McAfee\SiteAdvisor
FF Extension: McAfee SiteAdvisor - C:\Program Files (x86)\McAfee\SiteAdvisor
FF HKLM-x32\...\Thunderbird\Extensions: [msktbird@mcafee.com] C:\Program Files\McAfee\MSK
FF Extension: McAfee Anti-Spam Thunderbird Extension - C:\Program Files\McAfee\MSK
Chrome:
=======
CHR DefaultSearchURL: (Ask) - http://websearch.ask.com/redirect?client=cr&src=kw&tb=ORJ&o=&locale=&apn_uid=41C38969-F144-4076-AF1F-68B126EDBA2C&apn_ptnrs=TV&apn_sauid=834568E3-43CA-425C-AEED-70BB0522D6BF&apn_dtid=OSJ000YYUS&q={searchTerms}
CHR DefaultSuggestURL: (Ask) - http://ss.websearch.ask.com/query?qsrc=2922&li=ff&sstype=prefix&q={searchTerms}
CHR Plugin: (Shockwave Flash) - C:\Program Files (x86)\Google\Chrome\Application\29.0.1547.66\PepperFlash\pepflashplayer.dll ()
CHR Plugin: (Chrome Remote Desktop Viewer) - internal-remoting-viewer
CHR Plugin: (Native Client) - C:\Program Files (x86)\Google\Chrome\Application\29.0.1547.66\ppGoogleNaClPluginChrome.dll ()
CHR Plugin: (Chrome PDF Viewer) - C:\Program Files (x86)\Google\Chrome\Application\29.0.1547.66\pdf.dll ()
CHR Plugin: (Adobe Acrobat) - C:\Program Files (x86)\Adobe\Reader 11.0\Reader\Browser\nppdf32.dll (Adobe Systems Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin2.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin3.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin4.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin5.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin6.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin7.dll (Apple Inc.)
CHR Plugin: (Microsoft Office 2010) - C:\PROGRA~2\MICROS~1\Office14\NPAUTHZ.DLL (Microsoft Corporation)
CHR Plugin: (Microsoft Office 2010) - C:\PROGRA~2\MICROS~1\Office14\NPSPWRAP.DLL (Microsoft Corporation)
CHR Plugin: (CANON iMAGE GATEWAY Album Plugin Utility) - C:\Program Files (x86)\Canon\Easy-PhotoPrint EX\NPEZFFPI.DLL (CANON INC.)
CHR Plugin: (Google Update) - C:\Program Files (x86)\Google\Update\1.3.21.135\npGoogleUpdate3.dll No File
CHR Plugin: (Intel\u00AE Identity Protection Technology) - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IPT\npIntelWebAPIIPT.dll (Intel Corporation)
CHR Plugin: (Intel\u00AE Identity Protection Technology) - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IPT\npIntelWebAPIUpdater.dll (Intel Corporation)
CHR Plugin: (Java(TM) Platform SE 7 U9) - C:\Program Files (x86)\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation)
CHR Plugin: (Photo Gallery) - C:\Program Files (x86)\Windows Live\Photo Gallery\NPWLPG.dll (Microsoft Corporation)
CHR Plugin: (iTunes Application Detector) - C:\Program Files (x86)\iTunes\Mozilla Plugins\npitunes.dll ()
CHR Plugin: (Roblox Launcher Plugin) - C:\Users\Lynne\AppData\Local\Roblox\Versions\version-9ae7cc04e47a4b12\\NPRobloxProxy.dll No File
CHR Plugin: (Shockwave Flash) - C:\Windows\SysWOW64\Macromed\Flash\NPSWF32_11_5_502_146.dll ()
CHR Plugin: (Java Deployment Toolkit 7.0.90.5) - C:\Windows\SysWOW64\npDeployJava1.dll (Oracle Corporation)
CHR Plugin: (McAfee SecurityCenter) - c:\PROGRA~2\mcafee\msc\NPMCSN~1.DLL ()
CHR Extension: (Google Docs) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\aohghmighlieiainnegkcijnfilokake\0.5_0
CHR Extension: (Google Drive) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\apdfllckaahabafndbhieahigkjlhalf\6.3_0
CHR Extension: (YouTube) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\blpcfgokakmgnkcojhhkbfbldkacnbeo\4.2.6_0
CHR Extension: (Google Search) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf\0.0.0.20_0
CHR Extension: (SiteAdvisor) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\fheoggkfdfchfphceeifdbepaooicaho\3.6.3.1241_0
CHR Extension: (Chrome In-App Payments service) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\nmmhkkegccagdldgiimedpiccmgmieda\0.0.4.10_0
CHR Extension: (Gmail) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\pjkljhegncpnkpknbcohdijeoejaedia\7_0
CHR HKLM-x32\...\Chrome\Extension: [fheoggkfdfchfphceeifdbepaooicaho] - C:\Program Files (x86)\McAfee\SiteAdvisor\McChPlg.crx
==================== Services (Whitelisted) =================
R2 9734BF6A-2DCD-40f0-BAB0-5AAFEEBE1269; C:\Program Files (x86)\Roxio\BackOnTrack\App\SaibSVC.exe [457360 2012-06-20] ()
R2 ACDaemon; C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACService.exe [113152 2010-03-18] (ArcSoft Inc.)
R2 Application Sendori; C:\Program Files (x86)\Sendori\SendoriSvc.exe [119072 2013-07-01] (Sendori, Inc.)
R2 BOT4Service; C:\Program Files (x86)\Roxio\BackOnTrack\App\BService.exe [22160 2012-07-11] ()
R2 ClassicShellService; C:\Program Files\Classic Shell\ClassicShellService.exe [68608 2012-12-23] (IvoSoft)
R2 HomeNetSvc; C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 jhi_service; C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\DAL\jhi_service.exe [166720 2012-07-19] (Intel Corporation)
R2 McAfee SiteAdvisor Service; C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 McMPFSvc; C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 McNaiAnn; C:\Program Files\Common Files\mcafee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
S3 McODS; C:\Program Files\McAfee\VirusScan\mcods.exe [388680 2013-08-23] (McAfee, Inc.)
R2 mcpltsvc; C:\Program Files\Common Files\mcafee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 McProxy; C:\Program Files\Common Files\mcafee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 mfecore; C:\Program Files\Common Files\McAfee\AMCore\mcshield.exe [1017016 2013-02-28] (McAfee, Inc.)
R2 mfefire; C:\Program Files\Common Files\McAfee\SystemCore\\mfefire.exe [218760 2013-04-03] (McAfee, Inc.)
R2 mfevtp; C:\Windows\system32\mfevtps.exe [182752 2013-04-03] (McAfee, Inc.)
R2 MSK80Service; C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 RichVideo; C:\Program Files (x86)\CyberLink\Shared files\RichVideo.exe [254512 2012-04-24] ()
R2 RoxioBurnLauncher; C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Roxio Burn\RoxioBurnLauncher.exe [535184 2012-07-05] ()
S3 RoxMediaDB14; C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Common\RoxMediaDB14.exe [1096848 2012-11-29] (Corel Corporation)
S2 RoxWatch14; C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Common\RoxWatch14.exe [341136 2012-11-29] (Corel Corporation)
R2 Service Sendori; C:\Program Files (x86)\Sendori\Sendori.Service.exe [22304 2013-07-01] (sendori)
R2 SftService; C:\Program Files (x86)\Dell Backup and Recovery\SftService.exe [1914728 2012-11-26] (SoftThinks SAS)
R2 sndappv2; C:\Program Files (x86)\Sendori\sndappv2.exe [3623200 2013-07-01] (Sendori)
S3 WinDefend; C:\Program Files\Windows Defender\MsMpEng.exe [16048 2013-07-01] (Microsoft Corporation)
R2 ZAtheros Wlan Agent; C:\Program Files (x86)\Dell Wireless\Ath_WlanAgent.exe [77824 2012-06-19] (Atheros)
S2 McShield; "C:\Program Files\Common Files\McAfee\SystemCore\\mcshield.exe" [x]
==================== Drivers (Whitelisted) ====================
R3 cfwids; C:\Windows\System32\drivers\cfwids.sys [70112 2013-04-03] (McAfee, Inc.)
R1 CLVirtualDrive; C:\Windows\system32\DRIVERS\CLVirtualDrive.sys [92536 2012-06-25] (CyberLink)
S3 DellRbtn; C:\Windows\System32\drivers\DellRbtn.sys [10752 2012-08-05] (OSR Open Systems Resources, Inc.)
S3 HipShieldK; C:\Windows\System32\drivers\HipShieldK.sys [197264 2012-05-28] (McAfee, Inc.)
R3 mfeapfk; C:\Windows\System32\drivers\mfeapfk.sys [179664 2013-04-03] (McAfee, Inc.)
R3 mfeavfk; C:\Windows\System32\drivers\mfeavfk.sys [309968 2013-04-03] (McAfee, Inc.)
S0 mfeelamk; C:\Windows\System32\drivers\mfeelamk.sys [69240 2013-04-03] (McAfee, Inc.)
R3 mfefirek; C:\Windows\System32\drivers\mfefirek.sys [516608 2013-04-03] (McAfee, Inc.)
R0 mfehidk; C:\Windows\System32\drivers\mfehidk.sys [772944 2013-04-03] (McAfee, Inc.)
R3 mfencbdc; C:\Windows\system32\DRIVERS\mfencbdc.sys [337120 2013-02-18] (McAfee, Inc.)
S3 mfencrk; C:\Windows\system32\DRIVERS\mfencrk.sys [95856 2013-02-18] (McAfee, Inc.)
S3 mferkdet; C:\Windows\System32\drivers\mferkdet.sys [106552 2013-02-19] (McAfee, Inc.)
R0 mfewfpk; C:\Windows\System32\drivers\mfewfpk.sys [342416 2013-04-03] (McAfee, Inc.)
R0 PxHlpa64; C:\Windows\System32\Drivers\PxHlpa64.sys [56336 2012-06-22] (Corel Corporation)
R0 Sahdad64; C:\Windows\System32\Drivers\Sahdad64.sys [28304 2012-06-20] (Corel Corporation)
R0 Saibad64; C:\Windows\System32\Drivers\Saibad64.sys [20112 2012-06-20] (Corel Corporation)
R1 SaibVdAd64; C:\Windows\System32\Drivers\SaibVdAd64.sys [27792 2012-06-20] (Corel Corporation)
S3 ArcCD; No ImagePath
U1 ArcRec; No ImagePath
S4 ArcUdfs; No ImagePath
==================== NetSvcs (Whitelisted) ===================
==================== One Month Created Files and Folders ========
2013-09-09 06:22 - 2013-09-09 06:22 - 01948948 _____ (Farbar) C:\Users\Lynne\Downloads\FRST64.exe
2013-09-09 06:08 - 2013-09-09 06:16 - 00000000 ____D C:\AdwCleaner
2013-09-08 15:34 - 2013-09-08 15:34 - 00000000 ____D C:\Users\Lynne\Desktop\Computer Issues
2013-09-07 19:45 - 2013-09-09 06:24 - 00001846 _____ C:\Users\Public\Desktop\McAfee Security Center.lnk
2013-09-07 19:44 - 2013-09-08 09:18 - 00000000 ____D C:\Program Files (x86)\McAfee
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files\McAfee.com
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files\McAfee
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files (x86)\McAfee.com
2013-09-07 19:44 - 2012-05-28 10:28 - 00197264 _____ (McAfee, Inc.) C:\Windows\system32\Drivers\HipShieldK.sys
2013-09-07 19:38 - 2013-04-03 13:34 - 00182752 _____ (McAfee, Inc.) C:\Windows\system32\mfevtps.exe
2013-09-07 19:33 - 2013-09-07 19:33 - 05102984 _____ (McAfee, Inc.) C:\Users\Lynne\Downloads\McAfeeSetup.exe
2013-09-07 19:26 - 2013-09-07 19:26 - 46812214 _____ (InstallShield Software Corporation) C:\Users\Mackinaw\Downloads\VSE88P3.exe
2013-09-07 17:37 - 2013-09-07 17:37 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Malwarebytes
2013-09-07 17:37 - 2013-09-07 17:37 - 00000000 ____D C:\ProgramData\Malwarebytes
2013-09-07 15:57 - 2013-09-07 15:57 - 10285040 _____ (Malwarebytes Corporation ) C:\Users\Lynne\Downloads\mbam-setup-1.75.0.1300.exe
2013-09-07 15:41 - 2013-09-08 10:15 - 00000000 ____D C:\Users\Lynne\Desktop\RK_Quarantine
2013-09-07 13:28 - 2013-09-07 14:29 - 00000646 _____ C:\Users\Lynne\Downloads\Stinger_07092013_132803.html
2013-09-07 13:25 - 2013-09-07 13:25 - 00000000 ____D C:\Windows\pss
2013-09-07 11:55 - 2013-09-07 11:55 - 00000000 _____ C:\Users\Lynne\Downloads\Stinger_07092013_115540.html
2013-09-07 10:05 - 2013-09-07 10:05 - 00060014 _____ C:\Users\Lynne\Downloads\Extras.Txt
2013-09-07 10:04 - 2013-09-07 10:04 - 00113400 _____ C:\Users\Lynne\Downloads\OTL.Txt
2013-09-07 09:56 - 2013-09-09 06:21 - 00000000 ____D C:\Users\Lynne\Desktop\0 ACCESSSSS
2013-09-07 09:32 - 2013-09-07 09:33 - 00000274 _____ C:\Users\Lynne\Downloads\RootkitRemover20130907093205.txt
2013-09-07 09:26 - 2013-09-07 09:27 - 00001015 _____ C:\Users\Lynne\Downloads\Stinger_07092013_092623.html
2013-09-07 09:26 - 2013-09-07 09:26 - 00000000 ____D C:\Quarantine
2013-09-07 09:25 - 2013-09-07 17:36 - 00000000 ____D C:\Program Files\stinger
2013-09-07 09:25 - 2013-09-07 09:26 - 00498508 _____ C:\Users\Lynne\Downloads\runtime.dat
2013-09-07 09:25 - 2013-09-07 09:26 - 00000114 ___RH C:\Users\Lynne\Downloads\Stinger.opt
2013-09-07 09:09 - 2013-09-07 09:09 - 03856847 _____ C:\Users\Lynne\Downloads\epo5600eng.zip
2013-09-07 09:01 - 2013-09-07 09:23 - 00007605 _____ C:\Users\Lynne\AppData\Local\resmon.resmoncfg
2013-09-07 07:15 - 2013-09-07 07:17 - 00000274 _____ C:\Users\Lynne\Downloads\RootkitRemover20130907071555.txt
2013-09-07 07:15 - 2013-09-07 07:15 - 00551408 _____ (McAfee, Inc.) C:\Users\Lynne\Downloads\rootkitremover.exe
2013-09-06 20:50 - 2013-09-06 20:50 - 00000000 ____D C:\ProgramData\softthinks
2013-09-06 19:46 - 2013-09-06 20:50 - 00000000 ____D C:\Users\Lynne\Documents\Profile1
2013-09-05 17:09 - 2013-09-05 17:11 - 00001177 _____ C:\Users\Mackinaw\Desktop\ROBLOX Studio 2013.lnk
2013-09-05 17:09 - 2013-09-05 17:09 - 00543088 _____ (ROBLOX Corporation) C:\Users\Mackinaw\Downloads\RobloxPlayerLauncher.exe
2013-09-05 17:09 - 2013-09-05 17:09 - 00000000 ____D C:\Users\Mackinaw\AppData\Local\Roblox
2013-09-05 17:05 - 2013-09-05 17:05 - 00000000 ____D C:\ProgramData\nbaby
2013-08-30 08:51 - 2013-08-30 08:51 - 00000000 ____D C:\Users\Public\Juniper Networks
2013-08-30 08:51 - 2013-05-23 18:29 - 00594024 _____ (Juniper Networks) C:\Windows\system32\dsNcSmartCardProv.dll
2013-08-30 08:51 - 2013-05-23 18:29 - 00423528 _____ (Juniper Networks) C:\Windows\system32\dsNcCredProv.dll
2013-08-30 08:50 - 2013-08-30 08:51 - 00000000 ____D C:\Program Files (x86)\Juniper Networks
2013-08-30 08:49 - 2013-08-30 08:49 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (3).exe
2013-08-30 08:48 - 2013-08-30 09:02 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Juniper Networks
2013-08-30 08:48 - 2013-08-30 08:48 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (2).exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00263592 _____ (Oracle Corporation) C:\Windows\SysWOW64\javaws.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00175016 _____ (Oracle Corporation) C:\Windows\SysWOW64\javaw.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00175016 _____ (Oracle Corporation) C:\Windows\SysWOW64\java.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00096168 _____ (Oracle Corporation) C:\Windows\SysWOW64\WindowsAccessBridge-32.dll
2013-08-30 08:48 - 2013-08-30 08:48 - 00000000 ____D C:\Users\Lynne\AppData\Local\Juniper Networks
2013-08-30 08:46 - 2013-08-30 08:47 - 00903080 _____ (Oracle Corporation) C:\Users\Lynne\Downloads\chromeinstall-7u25.exe
2013-08-30 08:46 - 2013-08-30 08:46 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller.exe
2013-08-30 08:46 - 2013-08-30 08:46 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (1).exe
2013-08-29 15:57 - 2013-08-29 16:41 - 00000000 ____D C:\Users\Mackinaw\AppData\Roaming\.minecraft
2013-08-29 15:57 - 2013-08-29 15:57 - 00675988 _____ C:\Users\Mackinaw\Downloads\Minecraft.exe
2013-08-14 11:37 - 2013-08-14 11:39 - 00000000 ____D C:\Windows\system32\MRT
2013-08-14 09:16 - 2013-07-09 02:07 - 02233168 _____ (Microsoft Corporation) C:\Windows\system32\Drivers\tcpip.sys
2013-08-14 09:16 - 2013-05-23 19:02 - 01314816 _____ (Microsoft Corporation) C:\Windows\system32\rpcrt4.dll
2013-08-14 09:16 - 2013-05-23 18:25 - 00694272 _____ (Microsoft Corporation) C:\Windows\SysWOW64\rpcrt4.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 02241024 _____ (Microsoft Corporation) C:\Windows\system32\wininet.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 01365504 _____ (Microsoft Corporation) C:\Windows\system32\urlmon.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 00915968 _____ (Microsoft Corporation) C:\Windows\system32\uxtheme.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 00053760 _____ (Microsoft Corporation) C:\Windows\system32\UXInit.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 00051712 _____ (Microsoft Corporation) C:\Windows\system32\ie4uinit.exe
2013-08-14 09:15 - 2013-07-26 01:12 - 19239424 _____ (Microsoft Corporation) C:\Windows\system32\mshtml.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 15405056 _____ (Microsoft Corporation) C:\Windows\system32\ieframe.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 03958784 _____ (Microsoft Corporation) C:\Windows\system32\jscript9.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 02647040 _____ (Microsoft Corporation) C:\Windows\system32\iertutil.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00855552 _____ (Microsoft Corporation) C:\Windows\system32\jscript.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00603136 _____ (Microsoft Corporation) C:\Windows\system32\msfeeds.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00136704 _____ (Microsoft Corporation) C:\Windows\system32\iesysprep.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00067072 _____ (Microsoft Corporation) C:\Windows\system32\iesetup.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00053760 _____ (Microsoft Corporation) C:\Windows\system32\jsproxy.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00039936 _____ (Microsoft Corporation) C:\Windows\system32\iernonce.dll
2013-08-14 09:15 - 2013-07-25 23:35 - 02706432 _____ (Microsoft Corporation) C:\Windows\system32\mshtml.tlb
2013-08-14 09:15 - 2013-07-25 23:13 - 01767936 _____ (Microsoft Corporation) C:\Windows\SysWOW64\wininet.dll
2013-08-14 09:15 - 2013-07-25 23:13 - 01141248 _____ (Microsoft Corporation) C:\Windows\SysWOW64\urlmon.dll
2013-08-14 09:15 - 2013-07-25 23:13 - 00044032 _____ (Microsoft Corporation) C:\Windows\SysWOW64\UXInit.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 14329344 _____ (Microsoft Corporation) C:\Windows\SysWOW64\mshtml.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 02877440 _____ (Microsoft Corporation) C:\Windows\SysWOW64\jscript9.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 02048512 _____ (Microsoft Corporation) C:\Windows\SysWOW64\iertutil.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00690688 _____ (Microsoft Corporation) C:\Windows\SysWOW64\jscript.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00493056 _____ (Microsoft Corporation) C:\Windows\SysWOW64\msfeeds.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00109056 _____ (Microsoft Corporation) C:\Windows\SysWOW64\iesysprep.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00061440 _____ (Microsoft Corporation) C:\Windows\SysWOW64\iesetup.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00039936 _____ (Microsoft Corporation) C:\Windows\SysWOW64\jsproxy.dll
2013-08-14 09:15 - 2013-07-25 23:11 - 13761024 _____ (Microsoft Corporation) C:\Windows\SysWOW64\ieframe.dll
2013-08-14 09:15 - 2013-07-25 23:11 - 00033280 _____ (Microsoft Corporation) C:\Windows\SysWOW64\iernonce.dll
2013-08-14 09:15 - 2013-07-25 22:49 - 02706432 _____ (Microsoft Corporation) C:\Windows\SysWOW64\mshtml.tlb
2013-08-14 09:15 - 2013-07-25 20:54 - 00534528 _____ (Microsoft Corporation) C:\Windows\SysWOW64\uxtheme.dll
2013-08-14 09:15 - 2013-07-13 02:18 - 00337408 _____ (Microsoft Corporation) C:\Windows\system32\wintrust.dll
2013-08-14 09:15 - 2013-07-13 02:16 - 01889280 _____ (Microsoft Corporation) C:\Windows\system32\crypt32.dll
2013-08-14 09:15 - 2013-07-13 02:16 - 00068096 _____ (Microsoft Corporation) C:\Windows\system32\cryptsvc.dll
2013-08-14 09:15 - 2013-07-13 02:15 - 00124416 _____ (Microsoft Corporation) C:\Windows\system32\apprepapi.dll
2013-08-14 09:15 - 2013-07-13 02:15 - 00098304 _____ (Microsoft Corporation) C:\Windows\system32\apprepsync.dll
2013-08-14 09:15 - 2013-07-13 00:24 - 00261120 _____ (Microsoft Corporation) C:\Windows\SysWOW64\wintrust.dll
2013-08-14 09:15 - 2013-07-13 00:23 - 01568256 _____ (Microsoft Corporation) C:\Windows\SysWOW64\crypt32.dll
2013-08-14 09:15 - 2013-07-13 00:23 - 00087040 _____ (Microsoft Corporation) C:\Windows\SysWOW64\apprepapi.dll
2013-08-14 09:15 - 2013-07-13 00:23 - 00074240 _____ (Microsoft Corporation) C:\Windows\SysWOW64\apprepsync.dll
2013-08-14 09:15 - 2013-07-01 20:44 - 00036288 _____ (Microsoft Corporation) C:\Windows\system32\Drivers\WdBoot.sys
2013-08-14 09:15 - 2013-07-01 18:08 - 00247216 _____ (Microsoft Corporation) C:\Windows\system32\Drivers\WdFilter.sys
==================== One Month Modified Files and Folders =======
2013-09-09 06:31 - 2012-12-09 15:27 - 01928767 _____ C:\Windows\WindowsUpdate.log
2013-09-09 06:31 - 2012-07-26 03:28 - 00849856 _____ C:\Windows\system32\PerfStringBackup.INI
2013-09-09 06:30 - 2012-07-26 03:21 - 00028342 _____ C:\Windows\setupact.log
2013-09-09 06:28 - 2013-09-09 06:28 - 00000000 ____D C:\FRST
2013-09-09 06:26 - 2012-11-01 12:56 - 00000000 ____D C:\Program Files (x86)\Dell Backup and Recovery
2013-09-09 06:24 - 2013-09-07 19:45 - 00001846 _____ C:\Users\Public\Desktop\McAfee Security Center.lnk
2013-09-09 06:24 - 2012-12-09 15:36 - 00003596 _____ C:\Windows\System32\Tasks\Optimize Start Menu Cache Files-S-1-5-21-1091386282-3387701449-470047853-1001
2013-09-09 06:22 - 2013-09-09 06:22 - 01948948 _____ (Farbar) C:\Users\Lynne\Downloads\FRST64.exe
2013-09-09 06:21 - 2013-09-07 09:56 - 00000000 ____D C:\Users\Lynne\Desktop\0 ACCESSSSS
2013-09-09 06:18 - 2013-03-11 11:43 - 00000916 _____ C:\Windows\Tasks\GoogleUpdateTaskMachineCore.job
2013-09-09 06:18 - 2012-12-26 13:57 - 00000348 _____ C:\Windows\Tasks\GlaryInitialize.job
2013-09-09 06:18 - 2012-07-26 03:22 - 00000006 ____H C:\Windows\Tasks\SA.DAT
2013-09-09 06:16 - 2013-09-09 06:08 - 00000000 ____D C:\AdwCleaner
2013-09-09 06:03 - 2013-03-11 11:43 - 00000920 _____ C:\Windows\Tasks\GoogleUpdateTaskMachineUA.job
2013-09-09 06:00 - 2012-07-26 04:12 - 00000000 ____D C:\Windows\system32\sru
2013-09-08 16:45 - 2013-01-29 20:18 - 00000000 ____D C:\Users\Lynne\AppData\Local\LogMeIn Hamachi
2013-09-08 15:58 - 2012-12-16 16:24 - 00000000 ____D C:\ProgramData\CanonIJPLM
2013-09-08 15:43 - 2012-03-31 11:34 - 00000000 ____D C:\Users\Lynne\Desktop\K E N N E T H
2013-09-08 15:34 - 2013-09-08 15:34 - 00000000 ____D C:\Users\Lynne\Desktop\Computer Issues
2013-09-08 15:26 - 2012-11-01 12:53 - 00000000 ____D C:\ProgramData\McAfee
2013-09-08 10:15 - 2013-09-07 15:41 - 00000000 ____D C:\Users\Lynne\Desktop\RK_Quarantine
2013-09-08 09:18 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files (x86)\McAfee
2013-09-08 09:17 - 2012-12-31 10:57 - 00000000 ____D C:\Windows\Minidump
2013-09-08 09:17 - 2012-11-01 14:39 - 00107636 _____ C:\Windows\PFRO.log
2013-09-08 08:31 - 2012-07-26 01:26 - 00262144 ___SH C:\Windows\system32\config\ELAM
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files\McAfee.com
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files\McAfee
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files (x86)\McAfee.com
2013-09-07 19:44 - 2012-11-01 12:53 - 00000000 ____D C:\Program Files\Common Files\mcafee
2013-09-07 19:44 - 2012-07-26 04:12 - 00000000 ___HD C:\Windows\ELAMBKUP
2013-09-07 19:33 - 2013-09-07 19:33 - 05102984 _____ (McAfee, Inc.) C:\Users\Lynne\Downloads\McAfeeSetup.exe
2013-09-07 19:26 - 2013-09-07 19:26 - 46812214 _____ (InstallShield Software Corporation) C:\Users\Mackinaw\Downloads\VSE88P3.exe
2013-09-07 19:16 - 2013-04-26 08:24 - 00000000 ____D C:\Program Files (x86)\Mozilla Firefox
2013-09-07 18:56 - 2010-08-20 20:28 - 00000000 ____D C:\Users\Lynne\Desktop\L Y N N E
2013-09-07 17:37 - 2013-09-07 17:37 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Malwarebytes
2013-09-07 17:37 - 2013-09-07 17:37 - 00000000 ____D C:\ProgramData\Malwarebytes
2013-09-07 17:36 - 2013-09-07 09:25 - 00000000 ____D C:\Program Files\stinger
2013-09-07 15:57 - 2013-09-07 15:57 - 10285040 _____ (Malwarebytes Corporation ) C:\Users\Lynne\Downloads\mbam-setup-1.75.0.1300.exe
2013-09-07 14:29 - 2013-09-07 13:28 - 00000646 _____ C:\Users\Lynne\Downloads\Stinger_07092013_132803.html
2013-09-07 13:25 - 2013-09-07 13:25 - 00000000 ____D C:\Windows\pss
2013-09-07 11:55 - 2013-09-07 11:55 - 00000000 _____ C:\Users\Lynne\Downloads\Stinger_07092013_115540.html
2013-09-07 10:05 - 2013-09-07 10:05 - 00060014 _____ C:\Users\Lynne\Downloads\Extras.Txt
2013-09-07 10:04 - 2013-09-07 10:04 - 00113400 _____ C:\Users\Lynne\Downloads\OTL.Txt
2013-09-07 09:33 - 2013-09-07 09:32 - 00000274 _____ C:\Users\Lynne\Downloads\RootkitRemover20130907093205.txt
2013-09-07 09:27 - 2013-09-07 09:26 - 00001015 _____ C:\Users\Lynne\Downloads\Stinger_07092013_092623.html
2013-09-07 09:26 - 2013-09-07 09:26 - 00000000 ____D C:\Quarantine
2013-09-07 09:26 - 2013-09-07 09:25 - 00498508 _____ C:\Users\Lynne\Downloads\runtime.dat
2013-09-07 09:26 - 2013-09-07 09:25 - 00000114 ___RH C:\Users\Lynne\Downloads\Stinger.opt
2013-09-07 09:23 - 2013-09-07 09:01 - 00007605 _____ C:\Users\Lynne\AppData\Local\resmon.resmoncfg
2013-09-07 09:09 - 2013-09-07 09:09 - 03856847 _____ C:\Users\Lynne\Downloads\epo5600eng.zip
2013-09-07 07:17 - 2013-09-07 07:15 - 00000274 _____ C:\Users\Lynne\Downloads\RootkitRemover20130907071555.txt
2013-09-07 07:15 - 2013-09-07 07:15 - 00551408 _____ (McAfee, Inc.) C:\Users\Lynne\Downloads\rootkitremover.exe
2013-09-06 20:50 - 2013-09-06 20:50 - 00000000 ____D C:\ProgramData\softthinks
2013-09-06 20:50 - 2013-09-06 19:46 - 00000000 ____D C:\Users\Lynne\Documents\Profile1
2013-09-06 20:50 - 2012-11-01 16:14 - 00000000 __SHD C:\System Recovery
2013-09-06 19:43 - 2012-12-09 16:18 - 00000000 ____D C:\Users\Lynne\AppData\Local\softthinks
2013-09-06 07:10 - 2012-12-09 18:52 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\.minecraft
2013-09-05 21:00 - 2012-07-26 01:26 - 00262144 ___SH C:\Windows\system32\config\BBI
2013-09-05 17:17 - 2012-12-11 21:18 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Roblox
2013-09-05 17:16 - 2013-06-09 17:00 - 00001174 _____ C:\Users\Lynne\Desktop\ROBLOX Studio 2013.lnk
2013-09-05 17:11 - 2013-09-05 17:09 - 00001177 _____ C:\Users\Mackinaw\Desktop\ROBLOX Studio 2013.lnk
2013-09-05 17:09 - 2013-09-05 17:09 - 00543088 _____ (ROBLOX Corporation) C:\Users\Mackinaw\Downloads\RobloxPlayerLauncher.exe
2013-09-05 17:09 - 2013-09-05 17:09 - 00000000 ____D C:\Users\Mackinaw\AppData\Local\Roblox
2013-09-05 17:08 - 2013-04-14 20:13 - 00000000 ____D C:\Users\Mackinaw\AppData\Local\LogMeIn Hamachi
2013-09-05 17:05 - 2013-09-05 17:05 - 00000000 ____D C:\ProgramData\nbaby
2013-09-05 17:03 - 2012-12-22 20:40 - 00000000 ____D C:\ProgramData\Sendori
2013-09-05 07:19 - 2010-10-04 12:59 - 04594688 ___SH C:\Users\Lynne\Desktop\Thumbs.db
2013-09-05 06:34 - 2012-12-09 15:43 - 00000000 ____D C:\Program Files (x86)\Google
2013-08-31 12:21 - 2012-12-17 07:21 - 00000000 ____D C:\Users\Lynne\AppData\Local\Windows Live
2013-08-30 09:02 - 2013-08-30 08:48 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Juniper Networks
2013-08-30 08:51 - 2013-08-30 08:51 - 00000000 ____D C:\Users\Public\Juniper Networks
2013-08-30 08:51 - 2013-08-30 08:50 - 00000000 ____D C:\Program Files (x86)\Juniper Networks
2013-08-30 08:49 - 2013-08-30 08:49 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (3).exe
2013-08-30 08:48 - 2013-08-30 08:48 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (2).exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00263592 _____ (Oracle Corporation) C:\Windows\SysWOW64\javaws.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00175016 _____ (Oracle Corporation) C:\Windows\SysWOW64\javaw.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00175016 _____ (Oracle Corporation) C:\Windows\SysWOW64\java.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00096168 _____ (Oracle Corporation) C:\Windows\SysWOW64\WindowsAccessBridge-32.dll
2013-08-30 08:48 - 2013-08-30 08:48 - 00000000 ____D C:\Users\Lynne\AppData\Local\Juniper Networks
2013-08-30 08:48 - 2012-12-09 18:52 - 00867240 _____ (Oracle Corporation) C:\Windows\SysWOW64\npDeployJava1.dll
2013-08-30 08:48 - 2012-12-09 18:52 - 00789416 _____ (Oracle Corporation) C:\Windows\SysWOW64\deployJava1.dll
2013-08-30 08:47 - 2013-08-30 08:46 - 00903080 _____ (Oracle Corporation) C:\Users\Lynne\Downloads\chromeinstall-7u25.exe
2013-08-30 08:46 - 2013-08-30 08:46 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller.exe
2013-08-30 08:46 - 2013-08-30 08:46 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (1).exe
2013-08-30 04:18 - 2012-07-26 04:12 - 00000000 ____D C:\Windows\AUInstallAgent
2013-08-29 18:11 - 2012-12-21 07:54 - 00000000 ____D C:\ProgramData\Microsoft Help
2013-08-29 16:41 - 2013-08-29 15:57 - 00000000 ____D C:\Users\Mackinaw\AppData\Roaming\.minecraft
2013-08-29 16:01 - 2013-04-18 20:17 - 00000000 ____D C:\Users\Mackinaw\AppData\Local\Clipboarder
2013-08-29 15:57 - 2013-08-29 15:57 - 00675988 _____ C:\Users\Mackinaw\Downloads\Minecraft.exe
2013-08-19 17:46 - 2010-11-21 18:51 - 00000000 ____D C:\Users\Lynne\Desktop\M A C
2013-08-15 10:20 - 2012-07-26 04:12 - 00000000 ____D C:\Windows\rescache
2013-08-15 07:20 - 2012-07-26 04:12 - 00000000 ____D C:\Program Files\Windows Defender
2013-08-15 07:20 - 2012-07-26 04:12 - 00000000 ____D C:\Program Files (x86)\Windows Defender
2013-08-14 11:39 - 2013-08-14 11:37 - 00000000 ____D C:\Windows\system32\MRT
2013-08-14 11:37 - 2012-12-13 04:05 - 78161360 _____ (Microsoft Corporation) C:\Windows\system32\MRT.exe
Files to move or delete:
====================
C:\Users\Lynne\AppData\Local\Temp\ICReinstall_ZipOpenerSetup.exe
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe
==================== Bamital & volsnap Check =================
C:\Windows\System32\winlogon.exe => MD5 is legit
C:\Windows\System32\wininit.exe => MD5 is legit
C:\Windows\explorer.exe => MD5 is legit
C:\Windows\SysWOW64\explorer.exe => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
C:\Windows\SysWOW64\svchost.exe => MD5 is legit
C:\Windows\System32\services.exe => MD5 is legit
C:\Windows\System32\User32.dll => MD5 is legit
C:\Windows\SysWOW64\User32.dll => MD5 is legit
C:\Windows\System32\userinit.exe => MD5 is legit
C:\Windows\SysWOW64\userinit.exe => MD5 is legit
C:\Windows\System32\Drivers\volsnap.sys => MD5 is legit
LastRegBack: 2013-09-09 03:01
==================== End Of Log ============================
Additional scan result of Farbar Recovery Scan Tool (x64) Version: 09-09-2013
Ran by Lynne at 2013-09-09 06:32:56
Running from E:\
Boot Mode: Normal
==========================================================
==================== Installed Programs =======================
8GadgetPack (x32 Version: 4.1.0)
Adobe Flash Player 11 Plugin (x32 Version: 11.5.502.146)
Adobe Photoshop Elements 2.0 (x32 Version: 2.0)
Adobe Reader XI (11.0.01) (x32 Version: 11.0.01)
Adobe Shockwave Player 12.0 (x32 Version: 12.0.3.133)
Amazon Browser App (x32 Version: 1.0.0.0)
Any Video Converter 5.0.5 (x32)
Apple Application Support (x32 Version: 2.3.3)
Apple Mobile Device Support (Version: 6.1.0.13)
Apple Software Update (x32 Version: 2.1.3.127)
Bonjour (Version: 3.0.0.10)
Canon Easy-PhotoPrint EX (x32)
Canon Easy-PhotoPrint Pro - Pro9000 series Extention Data (x32)
Canon Easy-PhotoPrint Pro - Pro9500 series Extention Data (x32)
Canon Easy-PhotoPrint Pro (x32)
Canon MG8100 series MP Drivers
Canon MP Navigator EX 4.0 (x32)
Canon My Printer (x32)
Canon Solution Menu EX (x32)
Classic Shell (Version: 3.6.4)
CyberLink LabelPrint 2.5 (x32 Version: 2.5.5415a)
CyberLink Media Suite 10 (x32 Version: 10.0.1.1913)
CyberLink Media Suite Essentials (x32 Version: 10.0)
CyberLink Power2Go 8 (x32 Version: 8.0.0.1904)
CyberLink PowerDirector 10 (x32 Version: 10.0.1.1904)
CyberLink PowerDVD 10 (x32 Version: 10.0.4318.52)
D3DX10 (x32 Version: 15.4.2368.0902)
Definition Update for Microsoft Office 2010 (KB982726) 32-Bit Edition (x32)
Dell Backup and Recovery - Support Software (x32 Version: 1.0.0.5)
Dell Backup and Recovery (x32 Version: 1.0.0.5)
Dell Digital Delivery (x32 Version: 2.2.4000.0)
Dell Wireless Driver Installation (x32 Version: 10.0)
DirectX 9 Runtime (x32 Version: 1.00.0000)
Easy CD & DVD Burning Content (x32 Version: 14.0.030)
exant SmartAudio HD (Version: 8.50.12.0)
GIMP 2.8.4 (Version: 2.8.4)
Glary Utilities 2.51.0.1666 (x32 Version: 2.51.0.1666)
Google Chrome (x32 Version: 29.0.1547.66)
Google Update Helper (x32 Version: 1.3.21.153)
Intel(R) Control Center (x32 Version: 1.2.1.1008)
Intel(R) Management Engine Components (x32 Version: 8.1.0.1281)
Intel(R) Processor Graphics (x32 Version: 9.17.10.2849)
Intel(R) Rapid Storage Technology (x32 Version: 11.5.0.1207)
Intel® Trusted Connect Service Client (Version: 1.24.738.1)
iTunes (Version: 11.0.2.26)
Java 7 Update 11 (64-bit) (Version: 7.0.110)
Java 7 Update 25 (x32 Version: 7.0.250)
Java Auto Updater (x32 Version: 2.1.9.5)
Juniper Networks Network Connect 7.4.0 (x32 Version: 7.4.0.25351)
Juniper Networks, Inc. Setup Client (HKCU Version: 7.4.3.36355)
Juniper Networks, Inc. Setup Client 64-bit Activex Control (Version: 2.1.1.1)
Juniper Networks, Inc. Setup Client Activex Control (x32 Version: 2.1.1.1)
Junk Mail filter update (x32 Version: 16.4.3505.0912)
LogMeIn Hamachi (x32 Version: 2.1.0.374)
McAfee SecurityCenter (x32 Version: 12.1.353)
Microsoft Application Error Reporting (Version: 12.0.6015.5000)
Microsoft Office (x32 Version: 14.0.6120.5004)
Microsoft Office 2010 Service Pack 1 (SP1) (x32)
Microsoft Office Access MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Access Setup Metadata MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Excel MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Groove MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office InfoPath MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Office 64-bit Components 2010 (Version: 14.0.6029.1000)
Microsoft Office OneNote MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Outlook Connector (x32 Version: 14.0.5118.5000)
Microsoft Office Outlook MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office PowerPoint MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Professional Plus 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Proof (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Proof (French) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Proof (Spanish) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Proofing (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Publisher MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Shared 64-bit MUI (English) 2010 (Version: 14.0.6029.1000)
Microsoft Office Shared 64-bit Setup Metadata MUI (English) 2010 (Version: 14.0.6029.1000)
Microsoft Office Shared MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Shared Setup Metadata MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Word MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Outlook Social Connector Provider for Windows Live Messenger 32-bit (x32 Version: 14.0.5120.5000)
Microsoft SkyDrive (HKCU Version: 16.4.6013.0910)
Microsoft SQL Server 2005 Compact Edition [ENU] (x32 Version: 3.1.0000)
Microsoft Visual C++ 2005 Redistributable (x32 Version: 8.0.56336)
Microsoft Visual C++ 2005 Redistributable (x32 Version: 8.0.59193)
Microsoft Visual C++ 2005 Redistributable (x32 Version: 8.0.61001)
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.17 (x32 Version: 9.0.30729)
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161 (x32 Version: 9.0.30729.6161)
Microsoft Visual C++ 2010 x64 Redistributable - 10.0.40219 (Version: 10.0.40219)
Microsoft Visual C++ 2010 x86 Redistributable - 10.0.40219 (x32 Version: 10.0.40219)
Movie Maker (x32 Version: 16.4.3505.0912)
Mozilla Firefox 20.0.1 (x86 en-US) (x32 Version: 20.0.1)
Mozilla Maintenance Service (x32 Version: 20.0.1)
MSVCRT (x32 Version: 15.4.2862.0708)
MSVCRT Redists (x32 Version: 1.0)
MSVCRT_amd64 (x32 Version: 15.4.2862.0708)
MSVCRT110 (x32 Version: 16.4.1108.0727)
MSVCRT110_amd64 (Version: 16.4.1109.0912)
My Dell (Version: 3.3.6280.92)
MyTomTom 3.2.0.906 (x32 Version: 3.2.0.906)
Photo Gallery (x32 Version: 16.4.3505.0912)
Photo Story 3 for Windows (x32 Version: 3.0.1115.11)
QuickTime (x32 Version: 7.73.80.64)
RBVirtualFolder64Inst (Version: 1.00.0000)
ROBLOX Player for Lynne (HKCU)
ROBLOX Studio 2013 for Lynne (HKCU)
Roxio BackOnTrack (x32 Version: 4.5)
Roxio Burn (x32 Version: 2.0)
Roxio Central (x32 Version: 7.0.0)
Roxio Easy CD and DVD Burning (x32 Version: 1.4.222)
Roxio Easy CD and DVD Burning (x32 Version: 14.0.49.2)
Sendori (x32 Version: 2.0.15)
Shared C Run-time for x64 (Version: 10.0.0)
Sonic CinePlayer Decoder Pack (x32 Version: 4.3.0)
swMSM (x32 Version: 12.0.0.1)
TeamViewer 8 (x32 Version: 8.0.16642)
Update for Microsoft Office 2010 (KB2553065) (x32)
Update for Microsoft Office 2010 (KB2553181) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2553267) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2553310) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2553378) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2566458) (x32)
Update for Microsoft Office 2010 (KB2596964) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2598242) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2687503) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2687509) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2760631) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2767886) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2825640) 32-Bit Edition (x32)
Update for Microsoft OneNote 2010 (KB2553290) 32-Bit Edition (x32)
Update for Microsoft Outlook 2010 (KB2597090) 32-Bit Edition (x32)
Update for Microsoft Outlook 2010 (KB2687623) 32-Bit Edition (x32)
Update for Microsoft Outlook Social Connector 2010 (KB2553406) 32-Bit Edition (x32)
Update for Microsoft PowerPoint 2010 (KB2598240) 32-Bit Edition (x32)
Update for Microsoft SharePoint Workspace 2010 (KB2589371) 32-Bit Edition (x32)
Vegas Pro 11.0 (x32 Version: 11.0.682)
Visual Studio C++ 10.0 Runtime (x32 Version: 10.0.0)
Windows Live Communications Platform (x32 Version: 16.4.3505.0912)
Windows Live Essentials (x32 Version: 16.4.3505.0912)
Windows Live Installer (x32 Version: 16.4.3505.0912)
Windows Live Mail (x32 Version: 16.4.3505.0912)
Windows Live Messenger (x32 Version: 16.4.3505.0912)
Windows Live MIME IFilter (Version: 16.4.3505.0912)
Windows Live Photo Common (x32 Version: 16.4.3505.0912)
Windows Live PIMT Platform (x32 Version: 16.4.3505.0912)
Windows Live SOXE (x32 Version: 16.4.3505.0912)
Windows Live SOXE Definitions (x32 Version: 16.4.3505.0912)
Windows Live UX Platform (x32 Version: 16.4.3505.0912)
Windows Live UX Platform Language Pack (x32 Version: 16.4.3505.0912)
Windows Live Writer (x32 Version: 16.4.3505.0912)
Windows Live Writer Resources (x32 Version: 16.4.3505.0912)
WinRAR 4.20 (64-bit) (Version: 4.20.0)
WinRAR Packages (HKCU)
==================== Restore Points =========================
07-09-2013 23:22:03 Installed McAfee VirusScan Enterprise.
==================== Hosts content: ==========================
2012-07-26 01:26 - 2013-08-30 10:10 - 00000824 ____A C:\Windows\system32\Drivers\etc\hosts
==================== Scheduled Tasks (whitelisted) =============
Task: {04775B23-53A9-417C-A988-49D3DD31FB23} - System32\Tasks\Microsoft\Windows\WindowsUpdate\AUSessionConnect
Task: {10D85952-E3F6-47A1-96CF-5E1C2D874EA6} - System32\Tasks\Microsoft\Windows\SystemRestore\SR => C:\Windows\system32\srtasks.exe [2012-07-25] (Microsoft Corporation)
Task: {13A2AC02-B682-48CC-9155-2E2673580117} - System32\Tasks\Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319 64 Critical
Task: {17644F17-DC4C-4AC8-9444-7AAA52EB5CDC} - System32\Tasks\Microsoft\Windows\NetCfg\BindingWorkItemQueueHandler
Task: {1AAFF332-5C62-4558-9991-DAA649C4C9C5} - System32\Tasks\Microsoft\Windows\Sysmain\WsSwapAssessmentTask => C:\Windows\System32\sysmain.dll [2013-05-04] (Microsoft Corporation)
Task: {1DB7C2F1-876C-4F24-AD17-8428211113F9} - System32\Tasks\Microsoft\Windows\MemoryDiagnostic\ProcessMemoryDiagnosticEvents
Task: {214B24F4-FEB4-4C59-AF1F-70136065199C} - System32\Tasks\Microsoft\Windows\Shell\IndexerAutomaticMaintenance
Task: {23700E5C-0E77-499D-908A-415D5C6252F4} - System32\Tasks\Microsoft\Windows\Plug and Play\Device Install Group Policy
Task: {23A5D8BE-9196-40EB-BD89-794398B2B073} - System32\Tasks\Microsoft\Windows\WS\WSRefreshBannedAppsListTask => C:\Windows\System32\WSClient.dll [2012-09-20] (Microsoft Corporation)
Task: {2A65F893-A5C5-4DAB-A650-FD99BD475D3F} - System32\Tasks\Microsoft\Windows Live\SOXE\Extractor Definitions Update Task
Task: {2AC0D6D8-21E7-4491-8141-8BA8FAC7163A} - System32\Tasks\Microsoft\Windows\WindowsUpdate\AUFirmwareInstall
Task: {2C6B9EA8-7F5A-4ABA-BF96-8D352D02A743} - System32\Tasks\Microsoft\Windows\Device Setup\Metadata Refresh
Task: {2E030FA7-3D7C-4E1D-8CFE-56ADB26FD402} - System32\Tasks\Microsoft\Windows\PI\Sqm-Tasks
Task: {3054485A-F517-4E95-9977-4DD827B1E9B3} - System32\Tasks\Microsoft\Windows\WS\Badge Update
Task: {378401BA-A703-444A-A79C-3C47AD2DC5B6} - System32\Tasks\Microsoft\Windows\TaskScheduler\Maintenance Configurator
Task: {3AE164E7-30CD-40BC-9422-3EC7A5618965} - System32\Tasks\Microsoft\Windows\WS\WSTask
Task: {3C490ABD-D849-41AF-9AC4-87DD759B0996} - System32\Tasks\Microsoft\Windows\Power Efficiency Diagnostics\AnalyzeSystem
Task: {4073C1B3-6E16-4AA8-B7F3-C6A6D35D5071} - System32\Tasks\Microsoft\Windows\TPM\Tpm-Maintenance
Task: {44B3F1B8-5943-4072-8D8C-A9484676AC44} - System32\Tasks\Microsoft\Windows\Live\Roaming\SynchronizeWithStorage
Task: {483A8F5C-5D26-44B5-B49E-AF6741D1BBEB} - System32\Tasks\Microsoft\Windows\Mobile Broadband Accounts\MNO Metadata Parser => C:\Windows\System32\MbaeParserTask.exe [2013-06-01] (Microsoft Corporation)
Task: {4B952129-9AE9-41A3-BE2B-8AD2E06F66B6} - System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTaskLogon
Task: {4F7D2764-C269-47B6-8086-988B898844EA} - System32\Tasks\Microsoft\Windows\WindowsUpdate\AUScheduledInstall
Task: {50ABA94D-E849-485E-BA91-174F2C685EAD} - System32\Tasks\GoogleUpdateTaskMachineCore => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe [2013-03-11] (Google Inc.)
Task: {5755E746-D7ED-4C20-A472-66C11834CDE4} - System32\Tasks\Microsoft\Windows\TaskScheduler\Manual Maintenance
Task: {5C4EFB77-EFA6-45DF-A373-D795C0725BFF} - System32\Tasks\Microsoft\Windows\Plug and Play\Device Install Reboot Required
Task: {627441F3-8526-4B62-BF9A-1A3EA414E71A} - System32\Tasks\Microsoft\Windows\SpacePort\SpaceAgentTask => C:\Windows\system32\SpaceAgent.exe [2012-07-25] (Microsoft Corporation)
Task: {66FE2F79-6950-4974-B108-1DCFAF95098F} - System32\Tasks\GoogleUpdateTaskMachineUA => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe [2013-03-11] (Google Inc.)
Task: {6E9DE125-5583-4031-B572-FEE48F25CFFF} - System32\Tasks\Microsoft\Windows\Shell\FamilySafetyMonitor => C:\Windows\System32\wpcmon.exe [2012-09-20] (Microsoft Corporation)
Task: {6FDDEA7C-6310-428D-AEB2-54FFC72811EF} - System32\Tasks\Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319
Task: {74096F94-B654-4DB0-96F5-3C3408B92FE3} - System32\Tasks\Microsoft\Windows\PI\Secure-Boot-Update
Task: {76413BDF-12A3-40F8-BDD8-A78B10C837C2} - System32\Tasks\PCDoctorBackgroundMonitorTask => C:\Program Files\My Dell\uaclauncher.exe [2013-05-07] (PC-Doctor, Inc.)
Task: {7D9A9A1C-499C-40A6-8F8A-5BCC4CC9A87C} - System32\Tasks\Microsoft\Windows\TaskScheduler\Regular Maintenance
Task: {845CB020-68B5-4C6B-9876-7BEC7B3E27AC} - System32\Tasks\Microsoft\Windows\TaskScheduler\Idle Maintenance
Task: {87354DAA-66DF-4B41-9346-15958D96E1D2} - System32\Tasks\Microsoft\Windows\FileHistory\File History (maintenance mode)
Task: {900E75C3-A5F3-4FD1-91F5-C330F3882810} - System32\Tasks\Optimize Start Menu Cache Files-S-1-5-21-1091386282-3387701449-470047853-1001
Task: {901E0C63-1A9B-4675-8F15-FA8B43273EC0} - System32\Tasks\WPD\SqmUpload_S-1-5-21-1091386282-3387701449-470047853-1004 => C:\Windows\System32\portabledeviceapi.dll [2012-07-25] (Microsoft Corporation)
Task: {921A1D4E-32FB-46D7-B6C0-6F467884074D} - System32\Tasks\Microsoft\Windows\WS\Sync Licenses
Task: {9479EF8E-11D4-41B3-9783-CC65070D592D} - System32\Tasks\Microsoft\Windows\Time Synchronization\ForceSynchronizeTime
Task: {94DCF254-64FB-4C4E-8E12-5F4055C10C2A} - System32\Tasks\Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319 64
Task: {9605EB24-BED2-40BA-BA91-960249578E1E} - System32\Tasks\Microsoft\Windows\WindowsUpdate\Scheduled Start => Sc.exe start wuauserv
Task: {989A7C6D-BE82-4C3C-AF96-6116039E336B} - System32\Tasks\Microsoft\Windows\MemoryDiagnostic\RunFullMemoryDiagnostic
Task: {A72208BF-7A49-4FB8-B684-252375F3443A} - System32\Tasks\Microsoft\Windows\WS\License Validation => C:\Windows\System32\WSClient.dll [2012-09-20] (Microsoft Corporation)
Task: {A7AA1B0E-2FFF-49FD-8509-E5EB90F5A8A2} - System32\Tasks\SystemToolsDailyTest => C:\Windows\System32\uaclauncher.exe
Task: {A800277E-E202-4492-AD38-3312641CBC04} - System32\Tasks\Microsoft\Windows\Live\Roaming\MaintenanceTask
Task: {AB62FA47-2C99-44B1-A5D0-D4161423BE43} - System32\Tasks\Microsoft\Windows\Shell\FamilySafetyRefresh
Task: {AC6259DE-AC59-459E-849E-6ADFFD1ADE63} - System32\Tasks\Microsoft\Windows\Shell\CreateObjectTask
Task: {AEB0B5BD-B9E5-458A-898A-E559BD9EB51B} - System32\Tasks\Microsoft\Windows\SettingSync\BackgroundUploadTask
Task: {AF549BD8-337C-4BF7-8681-36A182E30507} - System32\Tasks\Microsoft\Windows\Chkdsk\ProactiveScan
Task: {BC76AEF7-2CF0-4EB6-B65B-A8803E0B5E12} - System32\Tasks\Microsoft\Windows\AppID\SmartScreenSpecific
Task: {BD5B181F-2A05-4F6F-B973-D46ECF18C53F} - System32\Tasks\GlaryInitialize => C:\Program Files (x86)\Glary Utilities\initialize.exe [2012-12-07] (Glarysoft Ltd)
Task: {BD60E878-672E-4B3D-A3BE-0058AADB6F68} - System32\Tasks\Microsoft\Windows\Servicing\StartComponentCleanup
Task: {C1ACCD1E-4385-4FB2-B5E4-7F2A57A626A2} - System32\Tasks\Microsoft\Windows\Data Integrity Scan\Data Integrity Scan
Task: {C463FD1E-31C7-4C20-AB65-08E514CA152D} - System32\Tasks\Microsoft\Windows\IME\SQM data sender
Task: {C6A88F2D-53D2-4805-9D69-443738A1847C} - System32\Tasks\Microsoft\Windows\ApplicationData\CleanupTemporaryState => C:\Windows\System32\Windows.Storage.ApplicationData.dll [2012-07-25] (Microsoft Corporation)
Task: {CD1054FF-8005-4904-8B9C-436EAB1E2021} - System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTaskNetwork
Task: {DBCF6E1B-CE0A-441E-B7A5-219C8BE50C65} - System32\Tasks\Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319 Critical
Task: {DECE5921-598D-454B-9A04-B2DE95EFC1B3} - System32\Tasks\Microsoft\Windows\Data Integrity Scan\Data Integrity Scan for Crash Recovery
Task: {E18BC818-DF31-4BD5-8178-197393ED16CB} - System32\Tasks\PCDEventLauncherTask => C:\Program Files\My Dell\sessionchecker.exe [2013-07-17] (PC-Doctor, Inc.)
Task: {E4DFE66F-E089-4CC3-A70F-957223D565F4} - System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTask
Task: {E8DAA09B-DF2A-4951-9134-6FA9587793F9} - System32\Tasks\Microsoft\Windows\Plug and Play\Sysprep Generalize Drivers => C:\Windows\System32\drvinst.exe [2012-09-20] (Microsoft Corporation)
Task: {EAD237E7-D276-4257-9F16-51DF41548733} - System32\Tasks\Microsoft\Windows\Time Synchronization\SynchronizeTime => Sc.exe start w32time task_started
Task: {EBF06DEC-4228-4813-AC0C-62821AE4E330} - System32\Tasks\Microsoft\Windows\Application Experience\StartupAppTask => C:\Windows\System32\Startupscan.dll [2012-07-25] (Microsoft Corporation)
Task: {ED0C1F69-C3A2-41EA-B8C3-3F0D83A1F6C0} - System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\BthSQM
Task: {F5AB8BF7-6B84-494D-9200-CEC052A6D37C} - System32\Tasks\OfficeSoftwareProtectionPlatform\SvcRestartTask => Sc.exe start osppsvc
Task: C:\Windows\Tasks\GlaryInitialize.job => C:\Program Files (x86)\Glary Utilities\initialize.exe
Task: C:\Windows\Tasks\GoogleUpdateTaskMachineCore.job => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe
Task: C:\Windows\Tasks\GoogleUpdateTaskMachineUA.job => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe
==================== Loaded Modules (whitelisted) =============
2012-12-23 16:28 - 2012-12-23 16:28 - 01989632 _____ (IvoSoft) C:\Program Files\Classic Shell\ClassicStartMenuDLL.dll
2012-07-26 03:55 - 2012-07-26 03:53 - 00170864 _____ () C:\Program Files\WindowsApps\microsoft.windowscommunicationsapps_16.4.4206.722_x64__8wekyb3d8bbwe\ModernShared\ErrorReporting\ErrorReporting.dll
2013-02-03 18:54 - 2013-02-03 18:54 - 00244696 _____ (Microsoft Corporation) C:\Users\Lynne\AppData\Local\Microsoft\SkyDrive\16.4.6013.0910\amd64\SkyDriveShell64.dll
2013-02-03 18:54 - 2013-02-03 18:54 - 00661448 _____ (Microsoft Corporation) C:\Users\Lynne\AppData\Local\Microsoft\SkyDrive\16.4.6013.0910\amd64\MSVCP110.dll
2013-02-03 18:54 - 2013-02-03 18:54 - 00828872 _____ (Microsoft Corporation) C:\Users\Lynne\AppData\Local\Microsoft\SkyDrive\16.4.6013.0910\amd64\MSVCR110.dll
2011-03-17 01:07 - 2011-03-17 01:07 - 04297568 _____ () C:\Program Files\Common Files\microsoft shared\OFFICE14\Cultures\OFFICE.ODF
2010-10-20 16:23 - 2010-10-20 16:23 - 08801632 _____ () C:\Program Files\Microsoft Office\Office14\1033\GrooveIntlResource.dll
2012-12-23 16:28 - 2012-12-23 16:28 - 00741888 _____ (IvoSoft) C:\Program Files\Classic Shell\ClassicExplorer64.dll
2012-10-06 01:12 - 2012-10-06 01:12 - 00286208 _____ (Intel Corporation) C:\Windows\system32\
Ran by Lynne (administrator) on LYNNEHENDEE on 09-09-2013 06:32:11
Running from E:\
Windows 8 (X64) OS Language: English(US)
Internet Explorer Version 10
Boot Mode: Normal
==================== Processes (Whitelisted) =================
(IvoSoft) C:\Program Files\Classic Shell\ClassicShellService.exe
() C:\Program Files (x86)\Roxio\BackOnTrack\App\SaibSVC.exe
(ArcSoft Inc.) C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACService.exe
(Apple Inc.) C:\Program Files (x86)\Common Files\Apple\Mobile Device Support\AppleMobileDeviceService.exe
(Apple Inc.) C:\Program Files\Bonjour\mDNSResponder.exe
() C:\Program Files (x86)\Roxio\BackOnTrack\App\BService.exe
(Microsoft Corporation) C:\Windows\system32\dashost.exe
(Juniper Networks) C:\Program Files (x86)\Juniper Networks\Common Files\dsNcService.exe
(LogMeIn Inc.) C:\Program Files (x86)\LogMeIn Hamachi\hamachi-2.exe
(Intel(R) Corporation) c:\Program Files\Intel\iCLS Client\HeciServer.exe
(Intel Corporation) C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\DAL\jhi_service.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe
(McAfee, Inc.) C:\Windows\system32\mfevtps.exe
() C:\Program Files (x86)\CyberLink\Shared files\RichVideo.exe
(IvoSoft) C:\Program Files\Classic Shell\ClassicStartMenu.exe
(Sendori) C:\Program Files (x86)\Sendori\sndappv2.exe
(TeamViewer GmbH) C:\Program Files (x86)\TeamViewer\Version8\TeamViewer_Service.exe
(Atheros) C:\Program Files (x86)\Dell Wireless\Ath_WlanAgent.exe
(Sendori, Inc.) C:\Program Files (x86)\Sendori\SendoriSvc.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\AMCore\mcshield.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\SystemCore\mfefire.exe
(sendori) C:\Program Files (x86)\Sendori\Sendori.Service.exe
(Sendori, Inc.) C:\Program Files (x86)\Sendori\SendoriUp.exe
(McAfee, Inc.) C:\PROGRA~1\McAfee\MSC\McAPExe.exe
(Microsoft Corporation) C:\Program Files\WindowsApps\microsoft.windowscommunicationsapps_16.4.4206.722_x64__8wekyb3d8bbwe\LiveComm.exe
(Intel Corporation) C:\Program Files (x86)\Intel\Intel(R) Rapid Storage Technology\IAStorDataMgrSvc.exe
(Intel Corporation) C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\LMS\LMS.exe
() C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Roxio Burn\RoxioBurnLauncher.exe
(SoftThinks SAS) C:\Program Files (x86)\Dell Backup and Recovery\SftService.exe
(Intel Corporation) C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\UNS\UNS.exe
(Microsoft Corporation) C:\Windows\system32\prevhost.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(Google Inc.) C:\Program Files (x86)\Google\Chrome\Application\chrome.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\Platform\mcuicnt.exe
(Microsoft Corporation) C:\Program Files\Common Files\Microsoft Shared\OfficeSoftwareProtectionPlatform\OSPPSVC.EXE
(McAfee, Inc.) c:\PROGRA~2\mcafee\SITEAD~1\saui.exe
(SoftThinks - Dell) C:\Program Files (x86)\Dell Backup and Recovery\TOASTER.EXE
(SoftThinks - Dell) C:\Program Files (x86)\Dell Backup and Recovery\Components\DBRUpdate\DBRUpd.exe
(McAfee, Inc.) c:\PROGRA~1\mcafee\VIRUSS~1\mcvsshld.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\Platform\Core\mchost.exe
(McAfee, Inc.) C:\Program Files\Common Files\McAfee\Platform\Core\mchost.exe
(Microsoft Corporation) C:\Windows\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_6.2.9200.16613_none_6273bd8950d6cae2\TiWorker.exe
==================== Registry (Whitelisted) ==================
HKLM\...\Run: [HotKeysCmds] - C:\Windows\system32\hkcmd.exe [ ] ()
HKLM\...\Run: [CanonMyPrinter] - C:\Program Files\Canon\MyPrinter\BJMyPrt.exe [2726728 2010-03-24] (CANON INC.)
HKLM\...\Policies\Explorer: [NoActiveDesktop] 1
HKLM\...\Policies\Explorer: [NoControlPanel] 0
HKCU\...\Run: [MyTomTomSA.exe] - C:\Program Files (x86)\MyTomTom 3\MyTomTomSA.exe [451656 2013-01-07] (TomTom)
HKCU\...\Run: [GoogleChromeAutoLaunch_6A12F0BBFE608579AB07135F9DFD76FE] - C:\Program Files (x86)\Google\Chrome\Application\chrome.exe [829392 2013-09-02] (Google Inc.)
MountPoints2: {67ec6cba-6534-11e2-be78-7845c4380f68} - "H:\MI.exe"
HKLM-x32\...\Run: [IMSS] - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IMSS\PIconStartup.exe [133440 2012-07-19] (Intel Corporation)
HKLM-x32\...\Run: [IAStorIcon] - C:\Program Files (x86)\Intel\Intel(R) Rapid Storage Technology\IAStorIcon.exe [277504 2012-07-09] (Intel Corporation)
HKLM-x32\...\Run: [CLMLServer_For_P2G8] - C:\Program Files (x86)\CyberLink\Power2Go8\CLMLSvc_P2G8.exe [111120 2012-06-07] (CyberLink)
HKLM-x32\...\Run: [CLVirtualDrive] - C:\Program Files (x86)\CyberLink\Power2Go8\VirtualDrive.exe [491120 2012-07-04] (CyberLink Corp.)
HKLM-x32\...\Run: [RemoteControl10] - C:\Program Files (x86)\CyberLink\PowerDVD10\PDVD10Serv.exe [143888 2012-06-01] (CyberLink Corp.)
HKLM-x32\...\Run: [BCSSync] - C:\Program Files (x86)\Microsoft Office\Office14\BCSSync.exe [91520 2010-03-13] (Microsoft Corporation)
HKLM-x32\...\Run: [Sendori Tray] - C:\Program Files (x86)\Sendori\SendoriTray.exe [83232 2013-07-01] (Sendori, Inc.)
HKLM-x32\...\Run: [APSDaemon] - C:\Program Files (x86)\Common Files\Apple\Apple Application Support\APSDaemon.exe [59720 2013-01-28] (Apple Inc.)
HKLM-x32\...\Run: [Adobe ARM] - C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe [946352 2012-12-18] (Adobe Systems Incorporated)
HKLM-x32\...\Run: [ArcSoft Connection Service] - C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACDaemon.exe [207424 2010-10-27] (ArcSoft Inc.)
HKLM-x32\...\Run: [QuickTime Task] - C:\Program Files (x86)\QuickTime\QTTask.exe [421888 2012-10-25] (Apple Inc.)
HKLM-x32\...\Run: [iTunesHelper] - C:\Program Files (x86)\iTunes\iTunesHelper.exe [152392 2013-02-20] (Apple Inc.)
HKLM-x32\...\Run: [ISUSPM] - C:\ProgramData\FLEXnet\Connect\11\\isuspm.exe [324976 2010-05-21] (Flexera Software, Inc.)
HKLM-x32\...\Run: [RoxWatchTray] - C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Common\RoxWatchTray14.exe [294032 2012-11-29] (Corel Corporation)
HKLM-x32\...\Run: [CanonSolutionMenuEx] - C:\Program Files (x86)\Canon\Solution Menu EX\CNSEMAIN.EXE [1185112 2010-04-02] (CANON INC.)
HKLM-x32\...\Run: [LogMeIn Hamachi Ui] - C:\Program Files (x86)\LogMeIn Hamachi\hamachi-2-ui.exe [2255184 2013-05-15] (LogMeIn Inc.)
HKLM-x32\...\Run: [SunJavaUpdateSched] - C:\Program Files (x86)\Common Files\Java\Java Update\jusched.exe [253816 2013-03-12] (Oracle Corporation)
HKLM-x32\...\Run: [mcpltui_exe] - C:\Program Files\McAfee.com\Agent\mcagent.exe [454600 2013-02-28] (McAfee, Inc.)
HKU\Mackinaw\...\Run: [MyTomTomSA.exe] - C:\Program Files (x86)\MyTomTom 3\MyTomTomSA.exe [451656 2013-01-07] (TomTom)
IMEO\sidebar.exe: [Debugger] C:\Program Files (x86)\Windows Sidebar\8GadgetPack.exe -run
Startup: C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\Adobe Gamma Loader.lnk
ShortcutTarget: Adobe Gamma Loader.lnk -> C:\Program Files (x86)\Common Files\Adobe\Calibration\Adobe Gamma Loader.exe (Adobe Systems, Inc.)
==================== Internet (Whitelisted) ====================
HKCU\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://dell13.msn.com
HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://dell13.msn.com/
HKCU\Software\Microsoft\Internet Explorer\Main,Start Page Redirect Cache = http://www.msn.com/?ocid=iehp
SearchScopes: HKLM - DefaultScope {0633EE93-D776-472f-A0FF-E1416B8B2E3A} URL = http://search.live.com/results.aspx?q={searchTerms}&src={referrer:source?}
SearchScopes: HKLM - {0633EE93-D776-472f-A0FF-E1416B8B2E3A} URL = http://search.live.com/results.aspx?q={searchTerms}&src={referrer:source?}
SearchScopes: HKLM - {7E492935-6215-4766-95F8-83CA18516A2B} URL = http://www.bing.com/search?q={searchTerms}&form=IE10TR&src=IE10TR&pc=MDDCJS
SearchScopes: HKLM-x32 - {7E492935-6215-4766-95F8-83CA18516A2B} URL = http://www.bing.com/search?q={searchTerms}&form=IE10TR&src=IE10TR&pc=MDDCJS
SearchScopes: HKCU - {7E492935-6215-4766-95F8-83CA18516A2B} URL =
SearchScopes: HKCU - {FA533155-F2FE-4486-842E-089EA28D3653} URL = http://search.yahoo.com/search?fr=mcafee&p={SearchTerms}
BHO: ExplorerBHO Class - {449D0D6E-2412-4E61-B68F-1CB625CD9E52} - C:\Program Files\Classic Shell\ClassicExplorer64.dll (IvoSoft)
BHO: Groove GFS Browser Helper - {72853161-30C5-4D22-B7F9-0BBC1D38A37E} - C:\Program Files\Microsoft Office\Office14\GROOVEEX.DLL (Microsoft Corporation)
BHO: Java(tm) Plug-In SSV Helper - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files\Java\jre7\bin\ssv.dll (Oracle Corporation)
BHO: McAfee SiteAdvisor BHO - {B164E929-A1B6-4A06-B104-2CD0E90A88FF} - C:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.)
BHO: Office Document Cache Handler - {B4F3A835-0E21-4959-BA22-42B3008E02FF} - C:\Program Files\Microsoft Office\Office14\URLREDIR.DLL (Microsoft Corporation)
BHO: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files\Java\jre7\bin\jp2ssv.dll (Oracle Corporation)
BHO: ClassicIE9BHO Class - {EA801577-E6AD-4BD5-8F71-4BE0154331A4} - C:\Program Files\Classic Shell\ClassicIE9DLL_64.dll (IvoSoft)
BHO-x32: Adobe PDF Link Helper - {18DF081C-E8AD-4283-A596-FA578C2EBDC3} - C:\Program Files (x86)\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelperShim.dll (Adobe Systems Incorporated)
BHO-x32: ExplorerBHO Class - {449D0D6E-2412-4E61-B68F-1CB625CD9E52} - C:\Program Files\Classic Shell\ClassicExplorer32.dll (IvoSoft)
BHO-x32: Groove GFS Browser Helper - {72853161-30C5-4D22-B7F9-0BBC1D38A37E} - C:\Program Files (x86)\Microsoft Office\Office14\GROOVEEX.DLL (Microsoft Corporation)
BHO-x32: Java(tm) Plug-In SSV Helper - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files (x86)\Java\jre7\bin\ssv.dll (Oracle Corporation)
BHO-x32: McAfee SiteAdvisor BHO - {B164E929-A1B6-4A06-B104-2CD0E90A88FF} - C:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.)
BHO-x32: Office Document Cache Handler - {B4F3A835-0E21-4959-BA22-42B3008E02FF} - C:\Program Files (x86)\Microsoft Office\Office14\URLREDIR.DLL (Microsoft Corporation)
BHO-x32: Java(tm) Plug-In 2 SSV Helper - {DBC80044-A445-435b-BC74-9C25C1C588A9} - C:\Program Files (x86)\Java\jre7\bin\jp2ssv.dll (Oracle Corporation)
BHO-x32: ClassicIE9BHO Class - {EA801577-E6AD-4BD5-8F71-4BE0154331A4} - C:\Program Files\Classic Shell\ClassicIE9DLL_32.dll (IvoSoft)
Toolbar: HKLM - Classic Explorer Bar - {553891B7-A0D5-4526-BE18-D3CE461D6310} - C:\Program Files\Classic Shell\ClassicExplorer64.dll (IvoSoft)
Toolbar: HKLM - McAfee SiteAdvisor Toolbar - {0EBBBE48-BAD4-4B4C-8E5A-516ABECAE064} - C:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.)
Toolbar: HKLM-x32 - Classic Explorer Bar - {553891B7-A0D5-4526-BE18-D3CE461D6310} - C:\Program Files\Classic Shell\ClassicExplorer32.dll (IvoSoft)
Toolbar: HKLM-x32 - McAfee SiteAdvisor Toolbar - {0EBBBE48-BAD4-4B4C-8E5A-516ABECAE064} - C:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.)
DPF: HKLM {AA570693-00E2-4907-B6F1-60A1199B030C} https://juniper.net/dana-cached/sc/JuniperSetupClient64.cab
DPF: HKLM-x32 {F27237D7-93C8-44C2-AC6E-D6057B9A918F} https://juniper.net/dana-cached/sc/JuniperSetupClient.cab
Handler: dssrequest - {5513F07E-936B-4E52-9B00-067394E91CC5} - C:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.)
Handler: sacore - {5513F07E-936B-4E52-9B00-067394E91CC5} - C:\Program Files (x86)\McAfee\SiteAdvisor\x64\McIEPlg.dll (McAfee, Inc.)
Handler-x32: dssrequest - {5513F07E-936B-4E52-9B00-067394E91CC5} - C:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.)
Handler-x32: sacore - {5513F07E-936B-4E52-9B00-067394E91CC5} - C:\Program Files (x86)\McAfee\SiteAdvisor\McIEPlg.dll (McAfee, Inc.)
Filter: application/x-mfe-ipt - {3EF5086B-5478-4598-A054-786C45D75692} - C:\Program Files\McAfee\MSC\McSnIePl64.dll (McAfee, Inc.)
Filter-x32: application/x-mfe-ipt - {3EF5086B-5478-4598-A054-786C45D75692} - C:\Program Files (x86)\McAfee\MSC\McSnIePl.dll (McAfee, Inc.)
FireFox:
========
FF ProfilePath: C:\Users\Lynne\AppData\Roaming\Mozilla\Firefox\Profiles\r4q34n7i.default
FF Plugin: @adobe.com/FlashPlayer - C:\Windows\system32\Macromed\Flash\NPSWF64_11_5_502_146.dll ()
FF Plugin: @java.com/DTPlugin,version=10.11.2 - C:\Windows\system32\npDeployJava1.dll (Oracle Corporation)
FF Plugin: @java.com/JavaPlugin,version=10.11.2 - C:\Program Files\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation)
FF Plugin: @mcafee.com/MSC,version=10 - c:\PROGRA~1\mcafee\msc\NPMCSN~1.DLL ()
FF Plugin: @microsoft.com/OfficeAuthz,version=14.0 - C:\PROGRA~1\MICROS~1\Office14\NPAUTHZ.DLL (Microsoft Corporation)
FF Plugin-x32: @adobe.com/FlashPlayer - C:\Windows\SysWOW64\Macromed\Flash\NPSWF32_11_5_502_146.dll ()
FF Plugin-x32: @adobe.com/ShockwavePlayer - C:\Windows\SysWOW64\Adobe\Director\np32dsw_1203133.dll (Adobe Systems, Inc.)
FF Plugin-x32: @Apple.com/iTunes,version=1.0 - C:\Program Files (x86)\iTunes\Mozilla Plugins\npitunes.dll ()
FF Plugin-x32: @canon.com/EPPEX - C:\Program Files (x86)\Canon\Easy-PhotoPrint EX\NPEZFFPI.DLL (CANON INC.)
FF Plugin-x32: @intel-webapi.intel.com/Intel WebAPI ipt;version=2.1.42 - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IPT\npIntelWebAPIIPT.dll (Intel Corporation)
FF Plugin-x32: @intel-webapi.intel.com/Intel WebAPI updater - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IPT\npIntelWebAPIUpdater.dll (Intel Corporation)
FF Plugin-x32: @java.com/DTPlugin,version=10.25.2 - C:\Windows\SysWOW64\npDeployJava1.dll (Oracle Corporation)
FF Plugin-x32: @java.com/JavaPlugin,version=10.25.2 - C:\Program Files (x86)\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation)
FF Plugin-x32: @mcafee.com/MSC,version=10 - c:\PROGRA~2\mcafee\msc\NPMCSN~1.DLL ()
FF Plugin-x32: @mcafee.com/SAFFPlugin - C:\Program Files (x86)\McAfee\SiteAdvisor\npmcffplg32.dll (McAfee, Inc.)
FF Plugin-x32: @microsoft.com/OfficeAuthz,version=14.0 - C:\PROGRA~2\MICROS~1\Office14\NPAUTHZ.DLL (Microsoft Corporation)
FF Plugin-x32: @microsoft.com/SharePoint,version=14.0 - C:\PROGRA~2\MICROS~1\Office14\NPSPWRAP.DLL (Microsoft Corporation)
FF Plugin-x32: @microsoft.com/WLPG,version=16.4.3505.0912 - C:\Program Files (x86)\Windows Live\Photo Gallery\NPWLPG.dll (Microsoft Corporation)
FF Plugin-x32: @tools.google.com/Google Update;version=3 - C:\Program Files (x86)\Google\Update\1.3.21.153\npGoogleUpdate3.dll (Google Inc.)
FF Plugin-x32: @tools.google.com/Google Update;version=9 - C:\Program Files (x86)\Google\Update\1.3.21.153\npGoogleUpdate3.dll (Google Inc.)
FF Plugin-x32: Adobe Reader - C:\Program Files (x86)\Adobe\Reader 11.0\Reader\AIR\nppdf32.dll (Adobe Systems Inc.)
FF Plugin HKCU: @nsroblox.roblox.com/launcher - C:\Users\Lynne\AppData\Local\Roblox\Versions\version-759151294bb84441\\NPRobloxProxy.dll ( ROBLOX Corporation)
FF Extension: DownloadTerms - C:\Program Files (x86)\Mozilla Firefox\extensions\jmwgabsbmtxairm@wzcttjml.com
FF HKLM-x32\...\Firefox\Extensions: [{4ED1F68A-5463-4931-9384-8FFF5ED91D92}] C:\Program Files (x86)\McAfee\SiteAdvisor
FF Extension: McAfee SiteAdvisor - C:\Program Files (x86)\McAfee\SiteAdvisor
FF HKLM-x32\...\Thunderbird\Extensions: [msktbird@mcafee.com] C:\Program Files\McAfee\MSK
FF Extension: McAfee Anti-Spam Thunderbird Extension - C:\Program Files\McAfee\MSK
Chrome:
=======
CHR DefaultSearchURL: (Ask) - http://websearch.ask.com/redirect?client=cr&src=kw&tb=ORJ&o=&locale=&apn_uid=41C38969-F144-4076-AF1F-68B126EDBA2C&apn_ptnrs=TV&apn_sauid=834568E3-43CA-425C-AEED-70BB0522D6BF&apn_dtid=OSJ000YYUS&q={searchTerms}
CHR DefaultSuggestURL: (Ask) - http://ss.websearch.ask.com/query?qsrc=2922&li=ff&sstype=prefix&q={searchTerms}
CHR Plugin: (Shockwave Flash) - C:\Program Files (x86)\Google\Chrome\Application\29.0.1547.66\PepperFlash\pepflashplayer.dll ()
CHR Plugin: (Chrome Remote Desktop Viewer) - internal-remoting-viewer
CHR Plugin: (Native Client) - C:\Program Files (x86)\Google\Chrome\Application\29.0.1547.66\ppGoogleNaClPluginChrome.dll ()
CHR Plugin: (Chrome PDF Viewer) - C:\Program Files (x86)\Google\Chrome\Application\29.0.1547.66\pdf.dll ()
CHR Plugin: (Adobe Acrobat) - C:\Program Files (x86)\Adobe\Reader 11.0\Reader\Browser\nppdf32.dll (Adobe Systems Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin2.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin3.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin4.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin5.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin6.dll (Apple Inc.)
CHR Plugin: (QuickTime Plug-in 7.7.3) - C:\Program Files (x86)\QuickTime\plugins\npqtplugin7.dll (Apple Inc.)
CHR Plugin: (Microsoft Office 2010) - C:\PROGRA~2\MICROS~1\Office14\NPAUTHZ.DLL (Microsoft Corporation)
CHR Plugin: (Microsoft Office 2010) - C:\PROGRA~2\MICROS~1\Office14\NPSPWRAP.DLL (Microsoft Corporation)
CHR Plugin: (CANON iMAGE GATEWAY Album Plugin Utility) - C:\Program Files (x86)\Canon\Easy-PhotoPrint EX\NPEZFFPI.DLL (CANON INC.)
CHR Plugin: (Google Update) - C:\Program Files (x86)\Google\Update\1.3.21.135\npGoogleUpdate3.dll No File
CHR Plugin: (Intel\u00AE Identity Protection Technology) - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IPT\npIntelWebAPIIPT.dll (Intel Corporation)
CHR Plugin: (Intel\u00AE Identity Protection Technology) - C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\IPT\npIntelWebAPIUpdater.dll (Intel Corporation)
CHR Plugin: (Java(TM) Platform SE 7 U9) - C:\Program Files (x86)\Java\jre7\bin\plugin2\npjp2.dll (Oracle Corporation)
CHR Plugin: (Photo Gallery) - C:\Program Files (x86)\Windows Live\Photo Gallery\NPWLPG.dll (Microsoft Corporation)
CHR Plugin: (iTunes Application Detector) - C:\Program Files (x86)\iTunes\Mozilla Plugins\npitunes.dll ()
CHR Plugin: (Roblox Launcher Plugin) - C:\Users\Lynne\AppData\Local\Roblox\Versions\version-9ae7cc04e47a4b12\\NPRobloxProxy.dll No File
CHR Plugin: (Shockwave Flash) - C:\Windows\SysWOW64\Macromed\Flash\NPSWF32_11_5_502_146.dll ()
CHR Plugin: (Java Deployment Toolkit 7.0.90.5) - C:\Windows\SysWOW64\npDeployJava1.dll (Oracle Corporation)
CHR Plugin: (McAfee SecurityCenter) - c:\PROGRA~2\mcafee\msc\NPMCSN~1.DLL ()
CHR Extension: (Google Docs) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\aohghmighlieiainnegkcijnfilokake\0.5_0
CHR Extension: (Google Drive) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\apdfllckaahabafndbhieahigkjlhalf\6.3_0
CHR Extension: (YouTube) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\blpcfgokakmgnkcojhhkbfbldkacnbeo\4.2.6_0
CHR Extension: (Google Search) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf\0.0.0.20_0
CHR Extension: (SiteAdvisor) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\fheoggkfdfchfphceeifdbepaooicaho\3.6.3.1241_0
CHR Extension: (Chrome In-App Payments service) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\nmmhkkegccagdldgiimedpiccmgmieda\0.0.4.10_0
CHR Extension: (Gmail) - C:\Users\Lynne\AppData\Local\Google\Chrome\User Data\Default\Extensions\pjkljhegncpnkpknbcohdijeoejaedia\7_0
CHR HKLM-x32\...\Chrome\Extension: [fheoggkfdfchfphceeifdbepaooicaho] - C:\Program Files (x86)\McAfee\SiteAdvisor\McChPlg.crx
==================== Services (Whitelisted) =================
R2 9734BF6A-2DCD-40f0-BAB0-5AAFEEBE1269; C:\Program Files (x86)\Roxio\BackOnTrack\App\SaibSVC.exe [457360 2012-06-20] ()
R2 ACDaemon; C:\Program Files (x86)\Common Files\ArcSoft\Connection Service\Bin\ACService.exe [113152 2010-03-18] (ArcSoft Inc.)
R2 Application Sendori; C:\Program Files (x86)\Sendori\SendoriSvc.exe [119072 2013-07-01] (Sendori, Inc.)
R2 BOT4Service; C:\Program Files (x86)\Roxio\BackOnTrack\App\BService.exe [22160 2012-07-11] ()
R2 ClassicShellService; C:\Program Files\Classic Shell\ClassicShellService.exe [68608 2012-12-23] (IvoSoft)
R2 HomeNetSvc; C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 jhi_service; C:\Program Files (x86)\Intel\Intel(R) Management Engine Components\DAL\jhi_service.exe [166720 2012-07-19] (Intel Corporation)
R2 McAfee SiteAdvisor Service; C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 McMPFSvc; C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 McNaiAnn; C:\Program Files\Common Files\mcafee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
S3 McODS; C:\Program Files\McAfee\VirusScan\mcods.exe [388680 2013-08-23] (McAfee, Inc.)
R2 mcpltsvc; C:\Program Files\Common Files\mcafee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 McProxy; C:\Program Files\Common Files\mcafee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 mfecore; C:\Program Files\Common Files\McAfee\AMCore\mcshield.exe [1017016 2013-02-28] (McAfee, Inc.)
R2 mfefire; C:\Program Files\Common Files\McAfee\SystemCore\\mfefire.exe [218760 2013-04-03] (McAfee, Inc.)
R2 mfevtp; C:\Windows\system32\mfevtps.exe [182752 2013-04-03] (McAfee, Inc.)
R2 MSK80Service; C:\Program Files\Common Files\McAfee\Platform\McSvcHost\McSvHost.exe [221296 2013-03-05] (McAfee, Inc.)
R2 RichVideo; C:\Program Files (x86)\CyberLink\Shared files\RichVideo.exe [254512 2012-04-24] ()
R2 RoxioBurnLauncher; C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Roxio Burn\RoxioBurnLauncher.exe [535184 2012-07-05] ()
S3 RoxMediaDB14; C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Common\RoxMediaDB14.exe [1096848 2012-11-29] (Corel Corporation)
S2 RoxWatch14; C:\Program Files (x86)\Roxio Easy CD & DVD Burning\Common\RoxWatch14.exe [341136 2012-11-29] (Corel Corporation)
R2 Service Sendori; C:\Program Files (x86)\Sendori\Sendori.Service.exe [22304 2013-07-01] (sendori)
R2 SftService; C:\Program Files (x86)\Dell Backup and Recovery\SftService.exe [1914728 2012-11-26] (SoftThinks SAS)
R2 sndappv2; C:\Program Files (x86)\Sendori\sndappv2.exe [3623200 2013-07-01] (Sendori)
S3 WinDefend; C:\Program Files\Windows Defender\MsMpEng.exe [16048 2013-07-01] (Microsoft Corporation)
R2 ZAtheros Wlan Agent; C:\Program Files (x86)\Dell Wireless\Ath_WlanAgent.exe [77824 2012-06-19] (Atheros)
S2 McShield; "C:\Program Files\Common Files\McAfee\SystemCore\\mcshield.exe" [x]
==================== Drivers (Whitelisted) ====================
R3 cfwids; C:\Windows\System32\drivers\cfwids.sys [70112 2013-04-03] (McAfee, Inc.)
R1 CLVirtualDrive; C:\Windows\system32\DRIVERS\CLVirtualDrive.sys [92536 2012-06-25] (CyberLink)
S3 DellRbtn; C:\Windows\System32\drivers\DellRbtn.sys [10752 2012-08-05] (OSR Open Systems Resources, Inc.)
S3 HipShieldK; C:\Windows\System32\drivers\HipShieldK.sys [197264 2012-05-28] (McAfee, Inc.)
R3 mfeapfk; C:\Windows\System32\drivers\mfeapfk.sys [179664 2013-04-03] (McAfee, Inc.)
R3 mfeavfk; C:\Windows\System32\drivers\mfeavfk.sys [309968 2013-04-03] (McAfee, Inc.)
S0 mfeelamk; C:\Windows\System32\drivers\mfeelamk.sys [69240 2013-04-03] (McAfee, Inc.)
R3 mfefirek; C:\Windows\System32\drivers\mfefirek.sys [516608 2013-04-03] (McAfee, Inc.)
R0 mfehidk; C:\Windows\System32\drivers\mfehidk.sys [772944 2013-04-03] (McAfee, Inc.)
R3 mfencbdc; C:\Windows\system32\DRIVERS\mfencbdc.sys [337120 2013-02-18] (McAfee, Inc.)
S3 mfencrk; C:\Windows\system32\DRIVERS\mfencrk.sys [95856 2013-02-18] (McAfee, Inc.)
S3 mferkdet; C:\Windows\System32\drivers\mferkdet.sys [106552 2013-02-19] (McAfee, Inc.)
R0 mfewfpk; C:\Windows\System32\drivers\mfewfpk.sys [342416 2013-04-03] (McAfee, Inc.)
R0 PxHlpa64; C:\Windows\System32\Drivers\PxHlpa64.sys [56336 2012-06-22] (Corel Corporation)
R0 Sahdad64; C:\Windows\System32\Drivers\Sahdad64.sys [28304 2012-06-20] (Corel Corporation)
R0 Saibad64; C:\Windows\System32\Drivers\Saibad64.sys [20112 2012-06-20] (Corel Corporation)
R1 SaibVdAd64; C:\Windows\System32\Drivers\SaibVdAd64.sys [27792 2012-06-20] (Corel Corporation)
S3 ArcCD; No ImagePath
U1 ArcRec; No ImagePath
S4 ArcUdfs; No ImagePath
==================== NetSvcs (Whitelisted) ===================
==================== One Month Created Files and Folders ========
2013-09-09 06:22 - 2013-09-09 06:22 - 01948948 _____ (Farbar) C:\Users\Lynne\Downloads\FRST64.exe
2013-09-09 06:08 - 2013-09-09 06:16 - 00000000 ____D C:\AdwCleaner
2013-09-08 15:34 - 2013-09-08 15:34 - 00000000 ____D C:\Users\Lynne\Desktop\Computer Issues
2013-09-07 19:45 - 2013-09-09 06:24 - 00001846 _____ C:\Users\Public\Desktop\McAfee Security Center.lnk
2013-09-07 19:44 - 2013-09-08 09:18 - 00000000 ____D C:\Program Files (x86)\McAfee
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files\McAfee.com
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files\McAfee
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files (x86)\McAfee.com
2013-09-07 19:44 - 2012-05-28 10:28 - 00197264 _____ (McAfee, Inc.) C:\Windows\system32\Drivers\HipShieldK.sys
2013-09-07 19:38 - 2013-04-03 13:34 - 00182752 _____ (McAfee, Inc.) C:\Windows\system32\mfevtps.exe
2013-09-07 19:33 - 2013-09-07 19:33 - 05102984 _____ (McAfee, Inc.) C:\Users\Lynne\Downloads\McAfeeSetup.exe
2013-09-07 19:26 - 2013-09-07 19:26 - 46812214 _____ (InstallShield Software Corporation) C:\Users\Mackinaw\Downloads\VSE88P3.exe
2013-09-07 17:37 - 2013-09-07 17:37 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Malwarebytes
2013-09-07 17:37 - 2013-09-07 17:37 - 00000000 ____D C:\ProgramData\Malwarebytes
2013-09-07 15:57 - 2013-09-07 15:57 - 10285040 _____ (Malwarebytes Corporation ) C:\Users\Lynne\Downloads\mbam-setup-1.75.0.1300.exe
2013-09-07 15:41 - 2013-09-08 10:15 - 00000000 ____D C:\Users\Lynne\Desktop\RK_Quarantine
2013-09-07 13:28 - 2013-09-07 14:29 - 00000646 _____ C:\Users\Lynne\Downloads\Stinger_07092013_132803.html
2013-09-07 13:25 - 2013-09-07 13:25 - 00000000 ____D C:\Windows\pss
2013-09-07 11:55 - 2013-09-07 11:55 - 00000000 _____ C:\Users\Lynne\Downloads\Stinger_07092013_115540.html
2013-09-07 10:05 - 2013-09-07 10:05 - 00060014 _____ C:\Users\Lynne\Downloads\Extras.Txt
2013-09-07 10:04 - 2013-09-07 10:04 - 00113400 _____ C:\Users\Lynne\Downloads\OTL.Txt
2013-09-07 09:56 - 2013-09-09 06:21 - 00000000 ____D C:\Users\Lynne\Desktop\0 ACCESSSSS
2013-09-07 09:32 - 2013-09-07 09:33 - 00000274 _____ C:\Users\Lynne\Downloads\RootkitRemover20130907093205.txt
2013-09-07 09:26 - 2013-09-07 09:27 - 00001015 _____ C:\Users\Lynne\Downloads\Stinger_07092013_092623.html
2013-09-07 09:26 - 2013-09-07 09:26 - 00000000 ____D C:\Quarantine
2013-09-07 09:25 - 2013-09-07 17:36 - 00000000 ____D C:\Program Files\stinger
2013-09-07 09:25 - 2013-09-07 09:26 - 00498508 _____ C:\Users\Lynne\Downloads\runtime.dat
2013-09-07 09:25 - 2013-09-07 09:26 - 00000114 ___RH C:\Users\Lynne\Downloads\Stinger.opt
2013-09-07 09:09 - 2013-09-07 09:09 - 03856847 _____ C:\Users\Lynne\Downloads\epo5600eng.zip
2013-09-07 09:01 - 2013-09-07 09:23 - 00007605 _____ C:\Users\Lynne\AppData\Local\resmon.resmoncfg
2013-09-07 07:15 - 2013-09-07 07:17 - 00000274 _____ C:\Users\Lynne\Downloads\RootkitRemover20130907071555.txt
2013-09-07 07:15 - 2013-09-07 07:15 - 00551408 _____ (McAfee, Inc.) C:\Users\Lynne\Downloads\rootkitremover.exe
2013-09-06 20:50 - 2013-09-06 20:50 - 00000000 ____D C:\ProgramData\softthinks
2013-09-06 19:46 - 2013-09-06 20:50 - 00000000 ____D C:\Users\Lynne\Documents\Profile1
2013-09-05 17:09 - 2013-09-05 17:11 - 00001177 _____ C:\Users\Mackinaw\Desktop\ROBLOX Studio 2013.lnk
2013-09-05 17:09 - 2013-09-05 17:09 - 00543088 _____ (ROBLOX Corporation) C:\Users\Mackinaw\Downloads\RobloxPlayerLauncher.exe
2013-09-05 17:09 - 2013-09-05 17:09 - 00000000 ____D C:\Users\Mackinaw\AppData\Local\Roblox
2013-09-05 17:05 - 2013-09-05 17:05 - 00000000 ____D C:\ProgramData\nbaby
2013-08-30 08:51 - 2013-08-30 08:51 - 00000000 ____D C:\Users\Public\Juniper Networks
2013-08-30 08:51 - 2013-05-23 18:29 - 00594024 _____ (Juniper Networks) C:\Windows\system32\dsNcSmartCardProv.dll
2013-08-30 08:51 - 2013-05-23 18:29 - 00423528 _____ (Juniper Networks) C:\Windows\system32\dsNcCredProv.dll
2013-08-30 08:50 - 2013-08-30 08:51 - 00000000 ____D C:\Program Files (x86)\Juniper Networks
2013-08-30 08:49 - 2013-08-30 08:49 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (3).exe
2013-08-30 08:48 - 2013-08-30 09:02 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Juniper Networks
2013-08-30 08:48 - 2013-08-30 08:48 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (2).exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00263592 _____ (Oracle Corporation) C:\Windows\SysWOW64\javaws.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00175016 _____ (Oracle Corporation) C:\Windows\SysWOW64\javaw.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00175016 _____ (Oracle Corporation) C:\Windows\SysWOW64\java.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00096168 _____ (Oracle Corporation) C:\Windows\SysWOW64\WindowsAccessBridge-32.dll
2013-08-30 08:48 - 2013-08-30 08:48 - 00000000 ____D C:\Users\Lynne\AppData\Local\Juniper Networks
2013-08-30 08:46 - 2013-08-30 08:47 - 00903080 _____ (Oracle Corporation) C:\Users\Lynne\Downloads\chromeinstall-7u25.exe
2013-08-30 08:46 - 2013-08-30 08:46 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller.exe
2013-08-30 08:46 - 2013-08-30 08:46 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (1).exe
2013-08-29 15:57 - 2013-08-29 16:41 - 00000000 ____D C:\Users\Mackinaw\AppData\Roaming\.minecraft
2013-08-29 15:57 - 2013-08-29 15:57 - 00675988 _____ C:\Users\Mackinaw\Downloads\Minecraft.exe
2013-08-14 11:37 - 2013-08-14 11:39 - 00000000 ____D C:\Windows\system32\MRT
2013-08-14 09:16 - 2013-07-09 02:07 - 02233168 _____ (Microsoft Corporation) C:\Windows\system32\Drivers\tcpip.sys
2013-08-14 09:16 - 2013-05-23 19:02 - 01314816 _____ (Microsoft Corporation) C:\Windows\system32\rpcrt4.dll
2013-08-14 09:16 - 2013-05-23 18:25 - 00694272 _____ (Microsoft Corporation) C:\Windows\SysWOW64\rpcrt4.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 02241024 _____ (Microsoft Corporation) C:\Windows\system32\wininet.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 01365504 _____ (Microsoft Corporation) C:\Windows\system32\urlmon.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 00915968 _____ (Microsoft Corporation) C:\Windows\system32\uxtheme.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 00053760 _____ (Microsoft Corporation) C:\Windows\system32\UXInit.dll
2013-08-14 09:15 - 2013-07-26 01:13 - 00051712 _____ (Microsoft Corporation) C:\Windows\system32\ie4uinit.exe
2013-08-14 09:15 - 2013-07-26 01:12 - 19239424 _____ (Microsoft Corporation) C:\Windows\system32\mshtml.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 15405056 _____ (Microsoft Corporation) C:\Windows\system32\ieframe.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 03958784 _____ (Microsoft Corporation) C:\Windows\system32\jscript9.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 02647040 _____ (Microsoft Corporation) C:\Windows\system32\iertutil.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00855552 _____ (Microsoft Corporation) C:\Windows\system32\jscript.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00603136 _____ (Microsoft Corporation) C:\Windows\system32\msfeeds.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00136704 _____ (Microsoft Corporation) C:\Windows\system32\iesysprep.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00067072 _____ (Microsoft Corporation) C:\Windows\system32\iesetup.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00053760 _____ (Microsoft Corporation) C:\Windows\system32\jsproxy.dll
2013-08-14 09:15 - 2013-07-26 01:12 - 00039936 _____ (Microsoft Corporation) C:\Windows\system32\iernonce.dll
2013-08-14 09:15 - 2013-07-25 23:35 - 02706432 _____ (Microsoft Corporation) C:\Windows\system32\mshtml.tlb
2013-08-14 09:15 - 2013-07-25 23:13 - 01767936 _____ (Microsoft Corporation) C:\Windows\SysWOW64\wininet.dll
2013-08-14 09:15 - 2013-07-25 23:13 - 01141248 _____ (Microsoft Corporation) C:\Windows\SysWOW64\urlmon.dll
2013-08-14 09:15 - 2013-07-25 23:13 - 00044032 _____ (Microsoft Corporation) C:\Windows\SysWOW64\UXInit.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 14329344 _____ (Microsoft Corporation) C:\Windows\SysWOW64\mshtml.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 02877440 _____ (Microsoft Corporation) C:\Windows\SysWOW64\jscript9.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 02048512 _____ (Microsoft Corporation) C:\Windows\SysWOW64\iertutil.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00690688 _____ (Microsoft Corporation) C:\Windows\SysWOW64\jscript.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00493056 _____ (Microsoft Corporation) C:\Windows\SysWOW64\msfeeds.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00109056 _____ (Microsoft Corporation) C:\Windows\SysWOW64\iesysprep.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00061440 _____ (Microsoft Corporation) C:\Windows\SysWOW64\iesetup.dll
2013-08-14 09:15 - 2013-07-25 23:12 - 00039936 _____ (Microsoft Corporation) C:\Windows\SysWOW64\jsproxy.dll
2013-08-14 09:15 - 2013-07-25 23:11 - 13761024 _____ (Microsoft Corporation) C:\Windows\SysWOW64\ieframe.dll
2013-08-14 09:15 - 2013-07-25 23:11 - 00033280 _____ (Microsoft Corporation) C:\Windows\SysWOW64\iernonce.dll
2013-08-14 09:15 - 2013-07-25 22:49 - 02706432 _____ (Microsoft Corporation) C:\Windows\SysWOW64\mshtml.tlb
2013-08-14 09:15 - 2013-07-25 20:54 - 00534528 _____ (Microsoft Corporation) C:\Windows\SysWOW64\uxtheme.dll
2013-08-14 09:15 - 2013-07-13 02:18 - 00337408 _____ (Microsoft Corporation) C:\Windows\system32\wintrust.dll
2013-08-14 09:15 - 2013-07-13 02:16 - 01889280 _____ (Microsoft Corporation) C:\Windows\system32\crypt32.dll
2013-08-14 09:15 - 2013-07-13 02:16 - 00068096 _____ (Microsoft Corporation) C:\Windows\system32\cryptsvc.dll
2013-08-14 09:15 - 2013-07-13 02:15 - 00124416 _____ (Microsoft Corporation) C:\Windows\system32\apprepapi.dll
2013-08-14 09:15 - 2013-07-13 02:15 - 00098304 _____ (Microsoft Corporation) C:\Windows\system32\apprepsync.dll
2013-08-14 09:15 - 2013-07-13 00:24 - 00261120 _____ (Microsoft Corporation) C:\Windows\SysWOW64\wintrust.dll
2013-08-14 09:15 - 2013-07-13 00:23 - 01568256 _____ (Microsoft Corporation) C:\Windows\SysWOW64\crypt32.dll
2013-08-14 09:15 - 2013-07-13 00:23 - 00087040 _____ (Microsoft Corporation) C:\Windows\SysWOW64\apprepapi.dll
2013-08-14 09:15 - 2013-07-13 00:23 - 00074240 _____ (Microsoft Corporation) C:\Windows\SysWOW64\apprepsync.dll
2013-08-14 09:15 - 2013-07-01 20:44 - 00036288 _____ (Microsoft Corporation) C:\Windows\system32\Drivers\WdBoot.sys
2013-08-14 09:15 - 2013-07-01 18:08 - 00247216 _____ (Microsoft Corporation) C:\Windows\system32\Drivers\WdFilter.sys
==================== One Month Modified Files and Folders =======
2013-09-09 06:31 - 2012-12-09 15:27 - 01928767 _____ C:\Windows\WindowsUpdate.log
2013-09-09 06:31 - 2012-07-26 03:28 - 00849856 _____ C:\Windows\system32\PerfStringBackup.INI
2013-09-09 06:30 - 2012-07-26 03:21 - 00028342 _____ C:\Windows\setupact.log
2013-09-09 06:28 - 2013-09-09 06:28 - 00000000 ____D C:\FRST
2013-09-09 06:26 - 2012-11-01 12:56 - 00000000 ____D C:\Program Files (x86)\Dell Backup and Recovery
2013-09-09 06:24 - 2013-09-07 19:45 - 00001846 _____ C:\Users\Public\Desktop\McAfee Security Center.lnk
2013-09-09 06:24 - 2012-12-09 15:36 - 00003596 _____ C:\Windows\System32\Tasks\Optimize Start Menu Cache Files-S-1-5-21-1091386282-3387701449-470047853-1001
2013-09-09 06:22 - 2013-09-09 06:22 - 01948948 _____ (Farbar) C:\Users\Lynne\Downloads\FRST64.exe
2013-09-09 06:21 - 2013-09-07 09:56 - 00000000 ____D C:\Users\Lynne\Desktop\0 ACCESSSSS
2013-09-09 06:18 - 2013-03-11 11:43 - 00000916 _____ C:\Windows\Tasks\GoogleUpdateTaskMachineCore.job
2013-09-09 06:18 - 2012-12-26 13:57 - 00000348 _____ C:\Windows\Tasks\GlaryInitialize.job
2013-09-09 06:18 - 2012-07-26 03:22 - 00000006 ____H C:\Windows\Tasks\SA.DAT
2013-09-09 06:16 - 2013-09-09 06:08 - 00000000 ____D C:\AdwCleaner
2013-09-09 06:03 - 2013-03-11 11:43 - 00000920 _____ C:\Windows\Tasks\GoogleUpdateTaskMachineUA.job
2013-09-09 06:00 - 2012-07-26 04:12 - 00000000 ____D C:\Windows\system32\sru
2013-09-08 16:45 - 2013-01-29 20:18 - 00000000 ____D C:\Users\Lynne\AppData\Local\LogMeIn Hamachi
2013-09-08 15:58 - 2012-12-16 16:24 - 00000000 ____D C:\ProgramData\CanonIJPLM
2013-09-08 15:43 - 2012-03-31 11:34 - 00000000 ____D C:\Users\Lynne\Desktop\K E N N E T H
2013-09-08 15:34 - 2013-09-08 15:34 - 00000000 ____D C:\Users\Lynne\Desktop\Computer Issues
2013-09-08 15:26 - 2012-11-01 12:53 - 00000000 ____D C:\ProgramData\McAfee
2013-09-08 10:15 - 2013-09-07 15:41 - 00000000 ____D C:\Users\Lynne\Desktop\RK_Quarantine
2013-09-08 09:18 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files (x86)\McAfee
2013-09-08 09:17 - 2012-12-31 10:57 - 00000000 ____D C:\Windows\Minidump
2013-09-08 09:17 - 2012-11-01 14:39 - 00107636 _____ C:\Windows\PFRO.log
2013-09-08 08:31 - 2012-07-26 01:26 - 00262144 ___SH C:\Windows\system32\config\ELAM
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files\McAfee.com
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files\McAfee
2013-09-07 19:44 - 2013-09-07 19:44 - 00000000 ____D C:\Program Files (x86)\McAfee.com
2013-09-07 19:44 - 2012-11-01 12:53 - 00000000 ____D C:\Program Files\Common Files\mcafee
2013-09-07 19:44 - 2012-07-26 04:12 - 00000000 ___HD C:\Windows\ELAMBKUP
2013-09-07 19:33 - 2013-09-07 19:33 - 05102984 _____ (McAfee, Inc.) C:\Users\Lynne\Downloads\McAfeeSetup.exe
2013-09-07 19:26 - 2013-09-07 19:26 - 46812214 _____ (InstallShield Software Corporation) C:\Users\Mackinaw\Downloads\VSE88P3.exe
2013-09-07 19:16 - 2013-04-26 08:24 - 00000000 ____D C:\Program Files (x86)\Mozilla Firefox
2013-09-07 18:56 - 2010-08-20 20:28 - 00000000 ____D C:\Users\Lynne\Desktop\L Y N N E
2013-09-07 17:37 - 2013-09-07 17:37 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Malwarebytes
2013-09-07 17:37 - 2013-09-07 17:37 - 00000000 ____D C:\ProgramData\Malwarebytes
2013-09-07 17:36 - 2013-09-07 09:25 - 00000000 ____D C:\Program Files\stinger
2013-09-07 15:57 - 2013-09-07 15:57 - 10285040 _____ (Malwarebytes Corporation ) C:\Users\Lynne\Downloads\mbam-setup-1.75.0.1300.exe
2013-09-07 14:29 - 2013-09-07 13:28 - 00000646 _____ C:\Users\Lynne\Downloads\Stinger_07092013_132803.html
2013-09-07 13:25 - 2013-09-07 13:25 - 00000000 ____D C:\Windows\pss
2013-09-07 11:55 - 2013-09-07 11:55 - 00000000 _____ C:\Users\Lynne\Downloads\Stinger_07092013_115540.html
2013-09-07 10:05 - 2013-09-07 10:05 - 00060014 _____ C:\Users\Lynne\Downloads\Extras.Txt
2013-09-07 10:04 - 2013-09-07 10:04 - 00113400 _____ C:\Users\Lynne\Downloads\OTL.Txt
2013-09-07 09:33 - 2013-09-07 09:32 - 00000274 _____ C:\Users\Lynne\Downloads\RootkitRemover20130907093205.txt
2013-09-07 09:27 - 2013-09-07 09:26 - 00001015 _____ C:\Users\Lynne\Downloads\Stinger_07092013_092623.html
2013-09-07 09:26 - 2013-09-07 09:26 - 00000000 ____D C:\Quarantine
2013-09-07 09:26 - 2013-09-07 09:25 - 00498508 _____ C:\Users\Lynne\Downloads\runtime.dat
2013-09-07 09:26 - 2013-09-07 09:25 - 00000114 ___RH C:\Users\Lynne\Downloads\Stinger.opt
2013-09-07 09:23 - 2013-09-07 09:01 - 00007605 _____ C:\Users\Lynne\AppData\Local\resmon.resmoncfg
2013-09-07 09:09 - 2013-09-07 09:09 - 03856847 _____ C:\Users\Lynne\Downloads\epo5600eng.zip
2013-09-07 07:17 - 2013-09-07 07:15 - 00000274 _____ C:\Users\Lynne\Downloads\RootkitRemover20130907071555.txt
2013-09-07 07:15 - 2013-09-07 07:15 - 00551408 _____ (McAfee, Inc.) C:\Users\Lynne\Downloads\rootkitremover.exe
2013-09-06 20:50 - 2013-09-06 20:50 - 00000000 ____D C:\ProgramData\softthinks
2013-09-06 20:50 - 2013-09-06 19:46 - 00000000 ____D C:\Users\Lynne\Documents\Profile1
2013-09-06 20:50 - 2012-11-01 16:14 - 00000000 __SHD C:\System Recovery
2013-09-06 19:43 - 2012-12-09 16:18 - 00000000 ____D C:\Users\Lynne\AppData\Local\softthinks
2013-09-06 07:10 - 2012-12-09 18:52 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\.minecraft
2013-09-05 21:00 - 2012-07-26 01:26 - 00262144 ___SH C:\Windows\system32\config\BBI
2013-09-05 17:17 - 2012-12-11 21:18 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Roblox
2013-09-05 17:16 - 2013-06-09 17:00 - 00001174 _____ C:\Users\Lynne\Desktop\ROBLOX Studio 2013.lnk
2013-09-05 17:11 - 2013-09-05 17:09 - 00001177 _____ C:\Users\Mackinaw\Desktop\ROBLOX Studio 2013.lnk
2013-09-05 17:09 - 2013-09-05 17:09 - 00543088 _____ (ROBLOX Corporation) C:\Users\Mackinaw\Downloads\RobloxPlayerLauncher.exe
2013-09-05 17:09 - 2013-09-05 17:09 - 00000000 ____D C:\Users\Mackinaw\AppData\Local\Roblox
2013-09-05 17:08 - 2013-04-14 20:13 - 00000000 ____D C:\Users\Mackinaw\AppData\Local\LogMeIn Hamachi
2013-09-05 17:05 - 2013-09-05 17:05 - 00000000 ____D C:\ProgramData\nbaby
2013-09-05 17:03 - 2012-12-22 20:40 - 00000000 ____D C:\ProgramData\Sendori
2013-09-05 07:19 - 2010-10-04 12:59 - 04594688 ___SH C:\Users\Lynne\Desktop\Thumbs.db
2013-09-05 06:34 - 2012-12-09 15:43 - 00000000 ____D C:\Program Files (x86)\Google
2013-08-31 12:21 - 2012-12-17 07:21 - 00000000 ____D C:\Users\Lynne\AppData\Local\Windows Live
2013-08-30 09:02 - 2013-08-30 08:48 - 00000000 ____D C:\Users\Lynne\AppData\Roaming\Juniper Networks
2013-08-30 08:51 - 2013-08-30 08:51 - 00000000 ____D C:\Users\Public\Juniper Networks
2013-08-30 08:51 - 2013-08-30 08:50 - 00000000 ____D C:\Program Files (x86)\Juniper Networks
2013-08-30 08:49 - 2013-08-30 08:49 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (3).exe
2013-08-30 08:48 - 2013-08-30 08:48 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (2).exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00263592 _____ (Oracle Corporation) C:\Windows\SysWOW64\javaws.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00175016 _____ (Oracle Corporation) C:\Windows\SysWOW64\javaw.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00175016 _____ (Oracle Corporation) C:\Windows\SysWOW64\java.exe
2013-08-30 08:48 - 2013-08-30 08:48 - 00096168 _____ (Oracle Corporation) C:\Windows\SysWOW64\WindowsAccessBridge-32.dll
2013-08-30 08:48 - 2013-08-30 08:48 - 00000000 ____D C:\Users\Lynne\AppData\Local\Juniper Networks
2013-08-30 08:48 - 2012-12-09 18:52 - 00867240 _____ (Oracle Corporation) C:\Windows\SysWOW64\npDeployJava1.dll
2013-08-30 08:48 - 2012-12-09 18:52 - 00789416 _____ (Oracle Corporation) C:\Windows\SysWOW64\deployJava1.dll
2013-08-30 08:47 - 2013-08-30 08:46 - 00903080 _____ (Oracle Corporation) C:\Users\Lynne\Downloads\chromeinstall-7u25.exe
2013-08-30 08:46 - 2013-08-30 08:46 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller.exe
2013-08-30 08:46 - 2013-08-30 08:46 - 01791496 _____ (Juniper Networks, Inc.) C:\Users\Lynne\Downloads\JuniperSetupClientInstaller (1).exe
2013-08-30 04:18 - 2012-07-26 04:12 - 00000000 ____D C:\Windows\AUInstallAgent
2013-08-29 18:11 - 2012-12-21 07:54 - 00000000 ____D C:\ProgramData\Microsoft Help
2013-08-29 16:41 - 2013-08-29 15:57 - 00000000 ____D C:\Users\Mackinaw\AppData\Roaming\.minecraft
2013-08-29 16:01 - 2013-04-18 20:17 - 00000000 ____D C:\Users\Mackinaw\AppData\Local\Clipboarder
2013-08-29 15:57 - 2013-08-29 15:57 - 00675988 _____ C:\Users\Mackinaw\Downloads\Minecraft.exe
2013-08-19 17:46 - 2010-11-21 18:51 - 00000000 ____D C:\Users\Lynne\Desktop\M A C
2013-08-15 10:20 - 2012-07-26 04:12 - 00000000 ____D C:\Windows\rescache
2013-08-15 07:20 - 2012-07-26 04:12 - 00000000 ____D C:\Program Files\Windows Defender
2013-08-15 07:20 - 2012-07-26 04:12 - 00000000 ____D C:\Program Files (x86)\Windows Defender
2013-08-14 11:39 - 2013-08-14 11:37 - 00000000 ____D C:\Windows\system32\MRT
2013-08-14 11:37 - 2012-12-13 04:05 - 78161360 _____ (Microsoft Corporation) C:\Windows\system32\MRT.exe
Files to move or delete:
====================
C:\Users\Lynne\AppData\Local\Temp\ICReinstall_ZipOpenerSetup.exe
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe
==================== Bamital & volsnap Check =================
C:\Windows\System32\winlogon.exe => MD5 is legit
C:\Windows\System32\wininit.exe => MD5 is legit
C:\Windows\explorer.exe => MD5 is legit
C:\Windows\SysWOW64\explorer.exe => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
C:\Windows\SysWOW64\svchost.exe => MD5 is legit
C:\Windows\System32\services.exe => MD5 is legit
C:\Windows\System32\User32.dll => MD5 is legit
C:\Windows\SysWOW64\User32.dll => MD5 is legit
C:\Windows\System32\userinit.exe => MD5 is legit
C:\Windows\SysWOW64\userinit.exe => MD5 is legit
C:\Windows\System32\Drivers\volsnap.sys => MD5 is legit
LastRegBack: 2013-09-09 03:01
==================== End Of Log ============================
Additional scan result of Farbar Recovery Scan Tool (x64) Version: 09-09-2013
Ran by Lynne at 2013-09-09 06:32:56
Running from E:\
Boot Mode: Normal
==========================================================
==================== Installed Programs =======================
8GadgetPack (x32 Version: 4.1.0)
Adobe Flash Player 11 Plugin (x32 Version: 11.5.502.146)
Adobe Photoshop Elements 2.0 (x32 Version: 2.0)
Adobe Reader XI (11.0.01) (x32 Version: 11.0.01)
Adobe Shockwave Player 12.0 (x32 Version: 12.0.3.133)
Amazon Browser App (x32 Version: 1.0.0.0)
Any Video Converter 5.0.5 (x32)
Apple Application Support (x32 Version: 2.3.3)
Apple Mobile Device Support (Version: 6.1.0.13)
Apple Software Update (x32 Version: 2.1.3.127)
Bonjour (Version: 3.0.0.10)
Canon Easy-PhotoPrint EX (x32)
Canon Easy-PhotoPrint Pro - Pro9000 series Extention Data (x32)
Canon Easy-PhotoPrint Pro - Pro9500 series Extention Data (x32)
Canon Easy-PhotoPrint Pro (x32)
Canon MG8100 series MP Drivers
Canon MP Navigator EX 4.0 (x32)
Canon My Printer (x32)
Canon Solution Menu EX (x32)
Classic Shell (Version: 3.6.4)
CyberLink LabelPrint 2.5 (x32 Version: 2.5.5415a)
CyberLink Media Suite 10 (x32 Version: 10.0.1.1913)
CyberLink Media Suite Essentials (x32 Version: 10.0)
CyberLink Power2Go 8 (x32 Version: 8.0.0.1904)
CyberLink PowerDirector 10 (x32 Version: 10.0.1.1904)
CyberLink PowerDVD 10 (x32 Version: 10.0.4318.52)
D3DX10 (x32 Version: 15.4.2368.0902)
Definition Update for Microsoft Office 2010 (KB982726) 32-Bit Edition (x32)
Dell Backup and Recovery - Support Software (x32 Version: 1.0.0.5)
Dell Backup and Recovery (x32 Version: 1.0.0.5)
Dell Digital Delivery (x32 Version: 2.2.4000.0)
Dell Wireless Driver Installation (x32 Version: 10.0)
DirectX 9 Runtime (x32 Version: 1.00.0000)
Easy CD & DVD Burning Content (x32 Version: 14.0.030)
exant SmartAudio HD (Version: 8.50.12.0)
GIMP 2.8.4 (Version: 2.8.4)
Glary Utilities 2.51.0.1666 (x32 Version: 2.51.0.1666)
Google Chrome (x32 Version: 29.0.1547.66)
Google Update Helper (x32 Version: 1.3.21.153)
Intel(R) Control Center (x32 Version: 1.2.1.1008)
Intel(R) Management Engine Components (x32 Version: 8.1.0.1281)
Intel(R) Processor Graphics (x32 Version: 9.17.10.2849)
Intel(R) Rapid Storage Technology (x32 Version: 11.5.0.1207)
Intel® Trusted Connect Service Client (Version: 1.24.738.1)
iTunes (Version: 11.0.2.26)
Java 7 Update 11 (64-bit) (Version: 7.0.110)
Java 7 Update 25 (x32 Version: 7.0.250)
Java Auto Updater (x32 Version: 2.1.9.5)
Juniper Networks Network Connect 7.4.0 (x32 Version: 7.4.0.25351)
Juniper Networks, Inc. Setup Client (HKCU Version: 7.4.3.36355)
Juniper Networks, Inc. Setup Client 64-bit Activex Control (Version: 2.1.1.1)
Juniper Networks, Inc. Setup Client Activex Control (x32 Version: 2.1.1.1)
Junk Mail filter update (x32 Version: 16.4.3505.0912)
LogMeIn Hamachi (x32 Version: 2.1.0.374)
McAfee SecurityCenter (x32 Version: 12.1.353)
Microsoft Application Error Reporting (Version: 12.0.6015.5000)
Microsoft Office (x32 Version: 14.0.6120.5004)
Microsoft Office 2010 Service Pack 1 (SP1) (x32)
Microsoft Office Access MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Access Setup Metadata MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Excel MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Groove MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office InfoPath MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Office 64-bit Components 2010 (Version: 14.0.6029.1000)
Microsoft Office OneNote MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Outlook Connector (x32 Version: 14.0.5118.5000)
Microsoft Office Outlook MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office PowerPoint MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Professional Plus 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Proof (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Proof (French) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Proof (Spanish) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Proofing (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Publisher MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Shared 64-bit MUI (English) 2010 (Version: 14.0.6029.1000)
Microsoft Office Shared 64-bit Setup Metadata MUI (English) 2010 (Version: 14.0.6029.1000)
Microsoft Office Shared MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Shared Setup Metadata MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Office Word MUI (English) 2010 (x32 Version: 14.0.6029.1000)
Microsoft Outlook Social Connector Provider for Windows Live Messenger 32-bit (x32 Version: 14.0.5120.5000)
Microsoft SkyDrive (HKCU Version: 16.4.6013.0910)
Microsoft SQL Server 2005 Compact Edition [ENU] (x32 Version: 3.1.0000)
Microsoft Visual C++ 2005 Redistributable (x32 Version: 8.0.56336)
Microsoft Visual C++ 2005 Redistributable (x32 Version: 8.0.59193)
Microsoft Visual C++ 2005 Redistributable (x32 Version: 8.0.61001)
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.17 (x32 Version: 9.0.30729)
Microsoft Visual C++ 2008 Redistributable - x86 9.0.30729.6161 (x32 Version: 9.0.30729.6161)
Microsoft Visual C++ 2010 x64 Redistributable - 10.0.40219 (Version: 10.0.40219)
Microsoft Visual C++ 2010 x86 Redistributable - 10.0.40219 (x32 Version: 10.0.40219)
Movie Maker (x32 Version: 16.4.3505.0912)
Mozilla Firefox 20.0.1 (x86 en-US) (x32 Version: 20.0.1)
Mozilla Maintenance Service (x32 Version: 20.0.1)
MSVCRT (x32 Version: 15.4.2862.0708)
MSVCRT Redists (x32 Version: 1.0)
MSVCRT_amd64 (x32 Version: 15.4.2862.0708)
MSVCRT110 (x32 Version: 16.4.1108.0727)
MSVCRT110_amd64 (Version: 16.4.1109.0912)
My Dell (Version: 3.3.6280.92)
MyTomTom 3.2.0.906 (x32 Version: 3.2.0.906)
Photo Gallery (x32 Version: 16.4.3505.0912)
Photo Story 3 for Windows (x32 Version: 3.0.1115.11)
QuickTime (x32 Version: 7.73.80.64)
RBVirtualFolder64Inst (Version: 1.00.0000)
ROBLOX Player for Lynne (HKCU)
ROBLOX Studio 2013 for Lynne (HKCU)
Roxio BackOnTrack (x32 Version: 4.5)
Roxio Burn (x32 Version: 2.0)
Roxio Central (x32 Version: 7.0.0)
Roxio Easy CD and DVD Burning (x32 Version: 1.4.222)
Roxio Easy CD and DVD Burning (x32 Version: 14.0.49.2)
Sendori (x32 Version: 2.0.15)
Shared C Run-time for x64 (Version: 10.0.0)
Sonic CinePlayer Decoder Pack (x32 Version: 4.3.0)
swMSM (x32 Version: 12.0.0.1)
TeamViewer 8 (x32 Version: 8.0.16642)
Update for Microsoft Office 2010 (KB2553065) (x32)
Update for Microsoft Office 2010 (KB2553181) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2553267) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2553310) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2553378) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2566458) (x32)
Update for Microsoft Office 2010 (KB2596964) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2598242) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2687503) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2687509) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2760631) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2767886) 32-Bit Edition (x32)
Update for Microsoft Office 2010 (KB2825640) 32-Bit Edition (x32)
Update for Microsoft OneNote 2010 (KB2553290) 32-Bit Edition (x32)
Update for Microsoft Outlook 2010 (KB2597090) 32-Bit Edition (x32)
Update for Microsoft Outlook 2010 (KB2687623) 32-Bit Edition (x32)
Update for Microsoft Outlook Social Connector 2010 (KB2553406) 32-Bit Edition (x32)
Update for Microsoft PowerPoint 2010 (KB2598240) 32-Bit Edition (x32)
Update for Microsoft SharePoint Workspace 2010 (KB2589371) 32-Bit Edition (x32)
Vegas Pro 11.0 (x32 Version: 11.0.682)
Visual Studio C++ 10.0 Runtime (x32 Version: 10.0.0)
Windows Live Communications Platform (x32 Version: 16.4.3505.0912)
Windows Live Essentials (x32 Version: 16.4.3505.0912)
Windows Live Installer (x32 Version: 16.4.3505.0912)
Windows Live Mail (x32 Version: 16.4.3505.0912)
Windows Live Messenger (x32 Version: 16.4.3505.0912)
Windows Live MIME IFilter (Version: 16.4.3505.0912)
Windows Live Photo Common (x32 Version: 16.4.3505.0912)
Windows Live PIMT Platform (x32 Version: 16.4.3505.0912)
Windows Live SOXE (x32 Version: 16.4.3505.0912)
Windows Live SOXE Definitions (x32 Version: 16.4.3505.0912)
Windows Live UX Platform (x32 Version: 16.4.3505.0912)
Windows Live UX Platform Language Pack (x32 Version: 16.4.3505.0912)
Windows Live Writer (x32 Version: 16.4.3505.0912)
Windows Live Writer Resources (x32 Version: 16.4.3505.0912)
WinRAR 4.20 (64-bit) (Version: 4.20.0)
WinRAR Packages (HKCU)
==================== Restore Points =========================
07-09-2013 23:22:03 Installed McAfee VirusScan Enterprise.
==================== Hosts content: ==========================
2012-07-26 01:26 - 2013-08-30 10:10 - 00000824 ____A C:\Windows\system32\Drivers\etc\hosts
==================== Scheduled Tasks (whitelisted) =============
Task: {04775B23-53A9-417C-A988-49D3DD31FB23} - System32\Tasks\Microsoft\Windows\WindowsUpdate\AUSessionConnect
Task: {10D85952-E3F6-47A1-96CF-5E1C2D874EA6} - System32\Tasks\Microsoft\Windows\SystemRestore\SR => C:\Windows\system32\srtasks.exe [2012-07-25] (Microsoft Corporation)
Task: {13A2AC02-B682-48CC-9155-2E2673580117} - System32\Tasks\Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319 64 Critical
Task: {17644F17-DC4C-4AC8-9444-7AAA52EB5CDC} - System32\Tasks\Microsoft\Windows\NetCfg\BindingWorkItemQueueHandler
Task: {1AAFF332-5C62-4558-9991-DAA649C4C9C5} - System32\Tasks\Microsoft\Windows\Sysmain\WsSwapAssessmentTask => C:\Windows\System32\sysmain.dll [2013-05-04] (Microsoft Corporation)
Task: {1DB7C2F1-876C-4F24-AD17-8428211113F9} - System32\Tasks\Microsoft\Windows\MemoryDiagnostic\ProcessMemoryDiagnosticEvents
Task: {214B24F4-FEB4-4C59-AF1F-70136065199C} - System32\Tasks\Microsoft\Windows\Shell\IndexerAutomaticMaintenance
Task: {23700E5C-0E77-499D-908A-415D5C6252F4} - System32\Tasks\Microsoft\Windows\Plug and Play\Device Install Group Policy
Task: {23A5D8BE-9196-40EB-BD89-794398B2B073} - System32\Tasks\Microsoft\Windows\WS\WSRefreshBannedAppsListTask => C:\Windows\System32\WSClient.dll [2012-09-20] (Microsoft Corporation)
Task: {2A65F893-A5C5-4DAB-A650-FD99BD475D3F} - System32\Tasks\Microsoft\Windows Live\SOXE\Extractor Definitions Update Task
Task: {2AC0D6D8-21E7-4491-8141-8BA8FAC7163A} - System32\Tasks\Microsoft\Windows\WindowsUpdate\AUFirmwareInstall
Task: {2C6B9EA8-7F5A-4ABA-BF96-8D352D02A743} - System32\Tasks\Microsoft\Windows\Device Setup\Metadata Refresh
Task: {2E030FA7-3D7C-4E1D-8CFE-56ADB26FD402} - System32\Tasks\Microsoft\Windows\PI\Sqm-Tasks
Task: {3054485A-F517-4E95-9977-4DD827B1E9B3} - System32\Tasks\Microsoft\Windows\WS\Badge Update
Task: {378401BA-A703-444A-A79C-3C47AD2DC5B6} - System32\Tasks\Microsoft\Windows\TaskScheduler\Maintenance Configurator
Task: {3AE164E7-30CD-40BC-9422-3EC7A5618965} - System32\Tasks\Microsoft\Windows\WS\WSTask
Task: {3C490ABD-D849-41AF-9AC4-87DD759B0996} - System32\Tasks\Microsoft\Windows\Power Efficiency Diagnostics\AnalyzeSystem
Task: {4073C1B3-6E16-4AA8-B7F3-C6A6D35D5071} - System32\Tasks\Microsoft\Windows\TPM\Tpm-Maintenance
Task: {44B3F1B8-5943-4072-8D8C-A9484676AC44} - System32\Tasks\Microsoft\Windows\Live\Roaming\SynchronizeWithStorage
Task: {483A8F5C-5D26-44B5-B49E-AF6741D1BBEB} - System32\Tasks\Microsoft\Windows\Mobile Broadband Accounts\MNO Metadata Parser => C:\Windows\System32\MbaeParserTask.exe [2013-06-01] (Microsoft Corporation)
Task: {4B952129-9AE9-41A3-BE2B-8AD2E06F66B6} - System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTaskLogon
Task: {4F7D2764-C269-47B6-8086-988B898844EA} - System32\Tasks\Microsoft\Windows\WindowsUpdate\AUScheduledInstall
Task: {50ABA94D-E849-485E-BA91-174F2C685EAD} - System32\Tasks\GoogleUpdateTaskMachineCore => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe [2013-03-11] (Google Inc.)
Task: {5755E746-D7ED-4C20-A472-66C11834CDE4} - System32\Tasks\Microsoft\Windows\TaskScheduler\Manual Maintenance
Task: {5C4EFB77-EFA6-45DF-A373-D795C0725BFF} - System32\Tasks\Microsoft\Windows\Plug and Play\Device Install Reboot Required
Task: {627441F3-8526-4B62-BF9A-1A3EA414E71A} - System32\Tasks\Microsoft\Windows\SpacePort\SpaceAgentTask => C:\Windows\system32\SpaceAgent.exe [2012-07-25] (Microsoft Corporation)
Task: {66FE2F79-6950-4974-B108-1DCFAF95098F} - System32\Tasks\GoogleUpdateTaskMachineUA => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe [2013-03-11] (Google Inc.)
Task: {6E9DE125-5583-4031-B572-FEE48F25CFFF} - System32\Tasks\Microsoft\Windows\Shell\FamilySafetyMonitor => C:\Windows\System32\wpcmon.exe [2012-09-20] (Microsoft Corporation)
Task: {6FDDEA7C-6310-428D-AEB2-54FFC72811EF} - System32\Tasks\Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319
Task: {74096F94-B654-4DB0-96F5-3C3408B92FE3} - System32\Tasks\Microsoft\Windows\PI\Secure-Boot-Update
Task: {76413BDF-12A3-40F8-BDD8-A78B10C837C2} - System32\Tasks\PCDoctorBackgroundMonitorTask => C:\Program Files\My Dell\uaclauncher.exe [2013-05-07] (PC-Doctor, Inc.)
Task: {7D9A9A1C-499C-40A6-8F8A-5BCC4CC9A87C} - System32\Tasks\Microsoft\Windows\TaskScheduler\Regular Maintenance
Task: {845CB020-68B5-4C6B-9876-7BEC7B3E27AC} - System32\Tasks\Microsoft\Windows\TaskScheduler\Idle Maintenance
Task: {87354DAA-66DF-4B41-9346-15958D96E1D2} - System32\Tasks\Microsoft\Windows\FileHistory\File History (maintenance mode)
Task: {900E75C3-A5F3-4FD1-91F5-C330F3882810} - System32\Tasks\Optimize Start Menu Cache Files-S-1-5-21-1091386282-3387701449-470047853-1001
Task: {901E0C63-1A9B-4675-8F15-FA8B43273EC0} - System32\Tasks\WPD\SqmUpload_S-1-5-21-1091386282-3387701449-470047853-1004 => C:\Windows\System32\portabledeviceapi.dll [2012-07-25] (Microsoft Corporation)
Task: {921A1D4E-32FB-46D7-B6C0-6F467884074D} - System32\Tasks\Microsoft\Windows\WS\Sync Licenses
Task: {9479EF8E-11D4-41B3-9783-CC65070D592D} - System32\Tasks\Microsoft\Windows\Time Synchronization\ForceSynchronizeTime
Task: {94DCF254-64FB-4C4E-8E12-5F4055C10C2A} - System32\Tasks\Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319 64
Task: {9605EB24-BED2-40BA-BA91-960249578E1E} - System32\Tasks\Microsoft\Windows\WindowsUpdate\Scheduled Start => Sc.exe start wuauserv
Task: {989A7C6D-BE82-4C3C-AF96-6116039E336B} - System32\Tasks\Microsoft\Windows\MemoryDiagnostic\RunFullMemoryDiagnostic
Task: {A72208BF-7A49-4FB8-B684-252375F3443A} - System32\Tasks\Microsoft\Windows\WS\License Validation => C:\Windows\System32\WSClient.dll [2012-09-20] (Microsoft Corporation)
Task: {A7AA1B0E-2FFF-49FD-8509-E5EB90F5A8A2} - System32\Tasks\SystemToolsDailyTest => C:\Windows\System32\uaclauncher.exe
Task: {A800277E-E202-4492-AD38-3312641CBC04} - System32\Tasks\Microsoft\Windows\Live\Roaming\MaintenanceTask
Task: {AB62FA47-2C99-44B1-A5D0-D4161423BE43} - System32\Tasks\Microsoft\Windows\Shell\FamilySafetyRefresh
Task: {AC6259DE-AC59-459E-849E-6ADFFD1ADE63} - System32\Tasks\Microsoft\Windows\Shell\CreateObjectTask
Task: {AEB0B5BD-B9E5-458A-898A-E559BD9EB51B} - System32\Tasks\Microsoft\Windows\SettingSync\BackgroundUploadTask
Task: {AF549BD8-337C-4BF7-8681-36A182E30507} - System32\Tasks\Microsoft\Windows\Chkdsk\ProactiveScan
Task: {BC76AEF7-2CF0-4EB6-B65B-A8803E0B5E12} - System32\Tasks\Microsoft\Windows\AppID\SmartScreenSpecific
Task: {BD5B181F-2A05-4F6F-B973-D46ECF18C53F} - System32\Tasks\GlaryInitialize => C:\Program Files (x86)\Glary Utilities\initialize.exe [2012-12-07] (Glarysoft Ltd)
Task: {BD60E878-672E-4B3D-A3BE-0058AADB6F68} - System32\Tasks\Microsoft\Windows\Servicing\StartComponentCleanup
Task: {C1ACCD1E-4385-4FB2-B5E4-7F2A57A626A2} - System32\Tasks\Microsoft\Windows\Data Integrity Scan\Data Integrity Scan
Task: {C463FD1E-31C7-4C20-AB65-08E514CA152D} - System32\Tasks\Microsoft\Windows\IME\SQM data sender
Task: {C6A88F2D-53D2-4805-9D69-443738A1847C} - System32\Tasks\Microsoft\Windows\ApplicationData\CleanupTemporaryState => C:\Windows\System32\Windows.Storage.ApplicationData.dll [2012-07-25] (Microsoft Corporation)
Task: {CD1054FF-8005-4904-8B9C-436EAB1E2021} - System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTaskNetwork
Task: {DBCF6E1B-CE0A-441E-B7A5-219C8BE50C65} - System32\Tasks\Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319 Critical
Task: {DECE5921-598D-454B-9A04-B2DE95EFC1B3} - System32\Tasks\Microsoft\Windows\Data Integrity Scan\Data Integrity Scan for Crash Recovery
Task: {E18BC818-DF31-4BD5-8178-197393ED16CB} - System32\Tasks\PCDEventLauncherTask => C:\Program Files\My Dell\sessionchecker.exe [2013-07-17] (PC-Doctor, Inc.)
Task: {E4DFE66F-E089-4CC3-A70F-957223D565F4} - System32\Tasks\Microsoft\Windows\SoftwareProtectionPlatform\SvcRestartTask
Task: {E8DAA09B-DF2A-4951-9134-6FA9587793F9} - System32\Tasks\Microsoft\Windows\Plug and Play\Sysprep Generalize Drivers => C:\Windows\System32\drvinst.exe [2012-09-20] (Microsoft Corporation)
Task: {EAD237E7-D276-4257-9F16-51DF41548733} - System32\Tasks\Microsoft\Windows\Time Synchronization\SynchronizeTime => Sc.exe start w32time task_started
Task: {EBF06DEC-4228-4813-AC0C-62821AE4E330} - System32\Tasks\Microsoft\Windows\Application Experience\StartupAppTask => C:\Windows\System32\Startupscan.dll [2012-07-25] (Microsoft Corporation)
Task: {ED0C1F69-C3A2-41EA-B8C3-3F0D83A1F6C0} - System32\Tasks\Microsoft\Windows\Customer Experience Improvement Program\BthSQM
Task: {F5AB8BF7-6B84-494D-9200-CEC052A6D37C} - System32\Tasks\OfficeSoftwareProtectionPlatform\SvcRestartTask => Sc.exe start osppsvc
Task: C:\Windows\Tasks\GlaryInitialize.job => C:\Program Files (x86)\Glary Utilities\initialize.exe
Task: C:\Windows\Tasks\GoogleUpdateTaskMachineCore.job => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe
Task: C:\Windows\Tasks\GoogleUpdateTaskMachineUA.job => C:\Program Files (x86)\Google\Update\GoogleUpdate.exe
==================== Loaded Modules (whitelisted) =============
2012-12-23 16:28 - 2012-12-23 16:28 - 01989632 _____ (IvoSoft) C:\Program Files\Classic Shell\ClassicStartMenuDLL.dll
2012-07-26 03:55 - 2012-07-26 03:53 - 00170864 _____ () C:\Program Files\WindowsApps\microsoft.windowscommunicationsapps_16.4.4206.722_x64__8wekyb3d8bbwe\ModernShared\ErrorReporting\ErrorReporting.dll
2013-02-03 18:54 - 2013-02-03 18:54 - 00244696 _____ (Microsoft Corporation) C:\Users\Lynne\AppData\Local\Microsoft\SkyDrive\16.4.6013.0910\amd64\SkyDriveShell64.dll
2013-02-03 18:54 - 2013-02-03 18:54 - 00661448 _____ (Microsoft Corporation) C:\Users\Lynne\AppData\Local\Microsoft\SkyDrive\16.4.6013.0910\amd64\MSVCP110.dll
2013-02-03 18:54 - 2013-02-03 18:54 - 00828872 _____ (Microsoft Corporation) C:\Users\Lynne\AppData\Local\Microsoft\SkyDrive\16.4.6013.0910\amd64\MSVCR110.dll
2011-03-17 01:07 - 2011-03-17 01:07 - 04297568 _____ () C:\Program Files\Common Files\microsoft shared\OFFICE14\Cultures\OFFICE.ODF
2010-10-20 16:23 - 2010-10-20 16:23 - 08801632 _____ () C:\Program Files\Microsoft Office\Office14\1033\GrooveIntlResource.dll
2012-12-23 16:28 - 2012-12-23 16:28 - 00741888 _____ (IvoSoft) C:\Program Files\Classic Shell\ClassicExplorer64.dll
2012-10-06 01:12 - 2012-10-06 01:12 - 00286208 _____ (Intel Corporation) C:\Windows\system32\
Hi,
After these 2 steps below, please give me an update on your PC's performance and any other symptoms that you may still be experiencing.
Open OTL. Under custom scan/fixes, copy and paste the following:
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Please download Malwarebytes' Anti-Malware from here to your desktop.
After these 2 steps below, please give me an update on your PC's performance and any other symptoms that you may still be experiencing.
Open OTL. Under custom scan/fixes, copy and paste the following:
:OTL
O2 - BHO: (Giant Savings Extension) - {11111111-1111-1111-1111-110211181110} - C:\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.dll (215 Apps)
O2 - BHO: (DownloadTerms) - {2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3} - C:\Users\Lynne\AppData\Local\DownloadTerms\temp.dat File not found
:Files
C:\Program Files (x86)\Giant Savings Extension
C:\Users\Lynne\AppData\Local\DownloadTerms
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe
:Commands
[EMPTYTEMP]
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Please download Malwarebytes' Anti-Malware from here to your desktop.
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to
- Update Malwarebytes' Anti-Malware
- and Launch Malwarebytes' Anti-Malware
- then click Finish.
- If an update is found, it will download and install the latest version.
- When it prompts you to try their 30-day trail, click decline
- Once the program has loaded, select Perform quick scan, then click Scan.
- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is Checked (ticked) except items in the C:\System Volume Information folder and click on Remove Selected.
- When completed, a log will open in Notepad. please copy and paste the log into your next reply
- If you accidently close it, the log file is saved here and will be named like this:
- C:\Documents and Settings\Username\Application Data\Malwarebytes\Malwarebytes' Anti-Malware\Logs\mbam-log-date (time).txt
Hi Fiery,
Below is the OTL log. The mwb scan resulted in "no malicious items detected". I will check back in and after some PC usage this weekend, will give you an update on performance and any symptoms. Thank you, thank you! Crossing my fingers that we've succeeded! ~ Lynne
All processes killed
========== OTL ==========
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{11111111-1111-1111-1111-110211181110}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{11111111-1111-1111-1111-110211181110}\ not found.
File C:\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.dll not found.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}\ not found.
========== FILES ==========
File\Folder C:\Program Files (x86)\Giant Savings Extension not found.
File\Folder C:\Users\Lynne\AppData\Local\DownloadTerms not found.
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe moved successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Lynne
->Temp folder emptied: 49651314 bytes
->Temporary Internet Files folder emptied: 124863533 bytes
->Java cache emptied: 247434 bytes
->FireFox cache emptied: 6595480 bytes
->Google Chrome cache emptied: 10611519 bytes
->Flash cache emptied: 826 bytes
User: Mackinaw
->Temp folder emptied: 144513103 bytes
->Temporary Internet Files folder emptied: 770613 bytes
->Java cache emptied: 0 bytes
->Google Chrome cache emptied: 76746461 bytes
->Flash cache emptied: 610 bytes
User: Public
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 3390083 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 138925434 bytes
RecycleBin emptied: 23698220 bytes
Total Files Cleaned = 553.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 09132013_125913
Files\Folders moved on Reboot...
C:\Users\Lynne\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
C:\Windows\temp\FXSAPIDebugLogFile.txt moved successfully.
C:\Windows\temp\FXSTIFFDebugLogFile.txt moved successfully.
File move failed. C:\Windows\temp\sndappv2.log scheduled to be moved on reboot.
C:\Windows\temp\~DF0BE1CAF848083A4D.TMP moved successfully.
File\Folder C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\pr%253Dd57c058c96efe41009dc0c0990b40d16%2526width%253D160%2526height%253D600%2526informer%253D8193319%2526uri%253Dhttp%253A%252F%252Fwww.lijit[10].js not found!
File\Folder C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\pr%253Dd57c058c96efe41009dc0c0990b40d16%2526width%253D160%2526height%253D600%2526informer%253D8193319%2526uri%253Dhttp%253A%252F%252Fwww.lijit[11].js not found!
C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
MWB log:
Hi,
After these 2 steps below, please give me an update on your PC's performance and any other symptoms that you may still be experiencing.
Open OTL. Under custom scan/fixes, copy and paste the following:
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Please download Malwarebytes' Anti-Malware from here to your desktop.
Below is the OTL log. The mwb scan resulted in "no malicious items detected". I will check back in and after some PC usage this weekend, will give you an update on performance and any symptoms. Thank you, thank you! Crossing my fingers that we've succeeded! ~ Lynne
All processes killed
========== OTL ==========
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{11111111-1111-1111-1111-110211181110}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{11111111-1111-1111-1111-110211181110}\ not found.
File C:\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.dll not found.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}\ not found.
========== FILES ==========
File\Folder C:\Program Files (x86)\Giant Savings Extension not found.
File\Folder C:\Users\Lynne\AppData\Local\DownloadTerms not found.
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe moved successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Lynne
->Temp folder emptied: 49651314 bytes
->Temporary Internet Files folder emptied: 124863533 bytes
->Java cache emptied: 247434 bytes
->FireFox cache emptied: 6595480 bytes
->Google Chrome cache emptied: 10611519 bytes
->Flash cache emptied: 826 bytes
User: Mackinaw
->Temp folder emptied: 144513103 bytes
->Temporary Internet Files folder emptied: 770613 bytes
->Java cache emptied: 0 bytes
->Google Chrome cache emptied: 76746461 bytes
->Flash cache emptied: 610 bytes
User: Public
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 3390083 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 138925434 bytes
RecycleBin emptied: 23698220 bytes
Total Files Cleaned = 553.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 09132013_125913
Files\Folders moved on Reboot...
C:\Users\Lynne\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
C:\Windows\temp\FXSAPIDebugLogFile.txt moved successfully.
C:\Windows\temp\FXSTIFFDebugLogFile.txt moved successfully.
File move failed. C:\Windows\temp\sndappv2.log scheduled to be moved on reboot.
C:\Windows\temp\~DF0BE1CAF848083A4D.TMP moved successfully.
File\Folder C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\pr%253Dd57c058c96efe41009dc0c0990b40d16%2526width%253D160%2526height%253D600%2526informer%253D8193319%2526uri%253Dhttp%253A%252F%252Fwww.lijit[10].js not found!
File\Folder C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\pr%253Dd57c058c96efe41009dc0c0990b40d16%2526width%253D160%2526height%253D600%2526informer%253D8193319%2526uri%253Dhttp%253A%252F%252Fwww.lijit[11].js not found!
C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
MWB log:
Hi,
After these 2 steps below, please give me an update on your PC's performance and any other symptoms that you may still be experiencing.
Open OTL. Under custom scan/fixes, copy and paste the following:
:OTL
O2 - BHO: (Giant Savings Extension) - {11111111-1111-1111-1111-110211181110} - C:\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.dll (215 Apps)
O2 - BHO: (DownloadTerms) - {2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3} - C:\Users\Lynne\AppData\Local\DownloadTerms\temp.dat File not found
:Files
C:\Program Files (x86)\Giant Savings Extension
C:\Users\Lynne\AppData\Local\DownloadTerms
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe
:Commands
[EMPTYTEMP]
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Please download Malwarebytes' Anti-Malware from here to your desktop.
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to
- Update Malwarebytes' Anti-Malware
- and Launch Malwarebytes' Anti-Malware
- then click Finish.
- If an update is found, it will download and install the latest version.
- When it prompts you to try their 30-day trail, click decline
- Once the program has loaded, select Perform quick scan, then click Scan.
- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is Checked (ticked) except items in the C:\System Volume Information folder and click on Remove Selected.
- When completed, a log will open in Notepad. please copy and paste the log into your next reply
- If you accidently close it, the log file is saved here and will be named like this:
- C:\Documents and Settings\Username\Application Data\Malwarebytes\Malwarebytes' Anti-Malware\Logs\mbam-log-date (time).txt
Forgot to paste mwb log, which is below the OTL log. ~Lynne
Hi Fiery,
Below is the OTL log. The mwb scan resulted in "no malicious items detected". I will check back in and after some PC usage this weekend, will give you an update on performance and any symptoms. Thank you, thank you! Crossing my fingers that we've succeeded! ~ Lynne
All processes killed
========== OTL ==========
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{11111111-1111-1111-1111-110211181110}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{11111111-1111-1111-1111-110211181110}\ not found.
File C:\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.dll not found.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}\ not found.
========== FILES ==========
File\Folder C:\Program Files (x86)\Giant Savings Extension not found.
File\Folder C:\Users\Lynne\AppData\Local\DownloadTerms not found.
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe moved successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Lynne
->Temp folder emptied: 49651314 bytes
->Temporary Internet Files folder emptied: 124863533 bytes
->Java cache emptied: 247434 bytes
->FireFox cache emptied: 6595480 bytes
->Google Chrome cache emptied: 10611519 bytes
->Flash cache emptied: 826 bytes
User: Mackinaw
->Temp folder emptied: 144513103 bytes
->Temporary Internet Files folder emptied: 770613 bytes
->Java cache emptied: 0 bytes
->Google Chrome cache emptied: 76746461 bytes
->Flash cache emptied: 610 bytes
User: Public
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 3390083 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 138925434 bytes
RecycleBin emptied: 23698220 bytes
Total Files Cleaned = 553.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 09132013_125913
Files\Folders moved on Reboot...
C:\Users\Lynne\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
C:\Windows\temp\FXSAPIDebugLogFile.txt moved successfully.
C:\Windows\temp\FXSTIFFDebugLogFile.txt moved successfully.
File move failed. C:\Windows\temp\sndappv2.log scheduled to be moved on reboot.
C:\Windows\temp\~DF0BE1CAF848083A4D.TMP moved successfully.
File\Folder C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\pr%253Dd57c058c96efe41009dc0c0990b40d16%2526width%253D160%2526height%253D600%2526informer%253D8193319%2526uri%253Dhttp%253A%252F%252Fwww.lijit[10].js not found!
File\Folder C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\pr%253Dd57c058c96efe41009dc0c0990b40d16%2526width%253D160%2526height%253D600%2526informer%253D8193319%2526uri%253Dhttp%253A%252F%252Fwww.lijit[11].js not found!
C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
MWB log:
Hi,
After these 2 steps below, please give me an update on your PC's performance and any other symptoms that you may still be experiencing.
Open OTL. Under custom scan/fixes, copy and paste the following:
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Please download Malwarebytes' Anti-Malware from here to your desktop.
[/quote]
Malwarebytes Anti-Malware 1.75.0.1300
www.malwarebytes.org
Database version: v2013.09.13.08
Windows 8 x64 NTFS
Internet Explorer 10.0.9200.16688
Lynne :: LYNNEHENDEE [administrator]
9/13/2013 1:26:11 PM
mbam-log-2013-09-13 (13-26-11).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM | P2P
Scan options disabled:
Objects scanned: 249903
Time elapsed: 4 minute(s), 54 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
Hi Fiery,
Below is the OTL log. The mwb scan resulted in "no malicious items detected". I will check back in and after some PC usage this weekend, will give you an update on performance and any symptoms. Thank you, thank you! Crossing my fingers that we've succeeded! ~ Lynne
All processes killed
========== OTL ==========
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{11111111-1111-1111-1111-110211181110}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{11111111-1111-1111-1111-110211181110}\ not found.
File C:\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.dll not found.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3}\ not found.
========== FILES ==========
File\Folder C:\Program Files (x86)\Giant Savings Extension not found.
File\Folder C:\Users\Lynne\AppData\Local\DownloadTerms not found.
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe moved successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Lynne
->Temp folder emptied: 49651314 bytes
->Temporary Internet Files folder emptied: 124863533 bytes
->Java cache emptied: 247434 bytes
->FireFox cache emptied: 6595480 bytes
->Google Chrome cache emptied: 10611519 bytes
->Flash cache emptied: 826 bytes
User: Mackinaw
->Temp folder emptied: 144513103 bytes
->Temporary Internet Files folder emptied: 770613 bytes
->Java cache emptied: 0 bytes
->Google Chrome cache emptied: 76746461 bytes
->Flash cache emptied: 610 bytes
User: Public
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 3390083 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 138925434 bytes
RecycleBin emptied: 23698220 bytes
Total Files Cleaned = 553.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 09132013_125913
Files\Folders moved on Reboot...
C:\Users\Lynne\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
C:\Windows\temp\FXSAPIDebugLogFile.txt moved successfully.
C:\Windows\temp\FXSTIFFDebugLogFile.txt moved successfully.
File move failed. C:\Windows\temp\sndappv2.log scheduled to be moved on reboot.
C:\Windows\temp\~DF0BE1CAF848083A4D.TMP moved successfully.
File\Folder C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\pr%253Dd57c058c96efe41009dc0c0990b40d16%2526width%253D160%2526height%253D600%2526informer%253D8193319%2526uri%253Dhttp%253A%252F%252Fwww.lijit[10].js not found!
File\Folder C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\pr%253Dd57c058c96efe41009dc0c0990b40d16%2526width%253D160%2526height%253D600%2526informer%253D8193319%2526uri%253Dhttp%253A%252F%252Fwww.lijit[11].js not found!
C:\Windows\SysNative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
MWB log:
Hi,
After these 2 steps below, please give me an update on your PC's performance and any other symptoms that you may still be experiencing.
Open OTL. Under custom scan/fixes, copy and paste the following:
:OTL
O2 - BHO: (Giant Savings Extension) - {11111111-1111-1111-1111-110211181110} - C:\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.dll (215 Apps)
O2 - BHO: (DownloadTerms) - {2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3} - C:\Users\Lynne\AppData\Local\DownloadTerms\temp.dat File not found
:Files
C:\Program Files (x86)\Giant Savings Extension
C:\Users\Lynne\AppData\Local\DownloadTerms
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe
:Commands
[EMPTYTEMP]
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Please download Malwarebytes' Anti-Malware from here to your desktop.
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to
- Update Malwarebytes' Anti-Malware
- and Launch Malwarebytes' Anti-Malware
- then click Finish.
- If an update is found, it will download and install the latest version.
- When it prompts you to try their 30-day trail, click decline
- Once the program has loaded, select Perform quick scan, then click Scan.
- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is Checked (ticked) except items in the C:\System Volume Information folder and click on Remove Selected.
- When completed, a log will open in Notepad. please copy and paste the log into your next reply
- If you accidently close it, the log file is saved here and will be named like this:
- C:\Documents and Settings\Username\Application Data\Malwarebytes\Malwarebytes' Anti-Malware\Logs\mbam-log-date (time).txt
[/quote]
Malwarebytes Anti-Malware 1.75.0.1300
www.malwarebytes.org
Database version: v2013.09.13.08
Windows 8 x64 NTFS
Internet Explorer 10.0.9200.16688
Lynne :: LYNNEHENDEE [administrator]
9/13/2013 1:26:11 PM
mbam-log-2013-09-13 (13-26-11).txt
Scan type: Quick scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM | P2P
Scan options disabled:
Objects scanned: 249903
Time elapsed: 4 minute(s), 54 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
Ok, let me know how things go. One more scan and then we will clean up.
Run Eset NOD32 Online AntiVirus here
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
Run Eset NOD32 Online AntiVirus here
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
- Tick the box next to YES, I accept the Terms of Use.
- Click Start
- When asked, allow the activex control to install
- Disable your current antivirus software. You can usually do this with its Notfication Tray icon near the clock.
- Make sure that the option "Remove found threats" is Un-checked, and the following Advance Settings are Checked
- Scan unwanted applications
- Scan for potentially unsafe applications
- Enable Anti-Stealth Technology
- Click Scan
- Wait for the scan to finish
- When the scan is done, if it shows a screen that says "Threats found!", then click "List of found threats", and then click "Export to text file..."
- Save that text file on your desktop. Copy and paste the contents of that log in your next reply to this topic.
- The log can also be found in logfile located at C:\Program Files\ESET\Eset Online Scanner\log.txt
Good morning Fiery - this will sound pretty pathetic but I can't find Internet Explorer. (What???) I have spent an hour looking for it, googling how to find it, and trying to reinstall it. When I tried to install IE10 a message said I have a newer version. I have Windows 8 (ugh) and believe IE-11 came with it but I vaguely recall that I deleted it since I don't ever use it. Anyway - I can't find any sign of IE anywhere and very frustrated.
Good morning Fiery ~ I found IE in location you gave (Thx!). Eset log is pasted below. Did not delete any of the threats. Keeping the Eset results window up in case you instruct me to check "Uninstall application upon close". Thank you for all your time and expertise. (o: ~Lynne
C:\$Recycle.Bin\S-1-5-21-1091386282-3387701449-470047853-1001\$R4XH90E.exe a variant of Win32/OutBrowse.D application
C:\$Recycle.Bin\S-1-5-21-1091386282-3387701449-470047853-1001\$RFXIRZZ.exe a variant of Win32/OutBrowse.D application
C:\AdwCleaner\Quarantine\C\Program Files (x86)\Giant Savings Extension\ButtonUtil.dll.vir a variant of Win32/Toolbar.CrossRider.G application
C:\AdwCleaner\Quarantine\C\Program Files (x86)\Giant Savings Extension\Giant Savings Extension-bg.exe.vir a variant of Win32/Toolbar.CrossRider.E application
C:\AdwCleaner\Quarantine\C\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.exe.vir a variant of Win32/Toolbar.CrossRider.E application
C:\AdwCleaner\Quarantine\C\Program Files (x86)\Giant Savings Extension\Giant Savings ExtensionGui.exe.vir a variant of Win32/Toolbar.CrossRider.F application
C:\Program Files (x86)\Dell Backup and Recovery\Components\DBRUpdate\hstart.exe a variant of Win32/HiddenStart.A application
C:\Users\Lynne\AppData\Local\Temp\DownloadManager2.exe a variant of Win32/OutBrowse.D application
C:\Users\Lynne\Downloads\avc-free.exe Win32/OpenCandy application
C:\Users\Lynne\Downloads\cbsidlm-tr1_13-Free_CUDA_Video_Converter-SEO-75728291 (1).exe Win32/DownloadAdmin.G application
C:\Users\Lynne\Downloads\cbsidlm-tr1_13-Free_CUDA_Video_Converter-SEO-75728291.exe Win32/DownloadAdmin.G application
C:\Users\Lynne\Downloads\IE_Setup.exe a variant of Win32/Adware.iBryte.G application
C:\Users\Lynne\Downloads\SoftonicDownloader_for_sony-vegas-video.exe Win32/SoftonicDownloader.E application
C:\$Recycle.Bin\S-1-5-21-1091386282-3387701449-470047853-1001\$R4XH90E.exe a variant of Win32/OutBrowse.D application
C:\$Recycle.Bin\S-1-5-21-1091386282-3387701449-470047853-1001\$RFXIRZZ.exe a variant of Win32/OutBrowse.D application
C:\AdwCleaner\Quarantine\C\Program Files (x86)\Giant Savings Extension\ButtonUtil.dll.vir a variant of Win32/Toolbar.CrossRider.G application
C:\AdwCleaner\Quarantine\C\Program Files (x86)\Giant Savings Extension\Giant Savings Extension-bg.exe.vir a variant of Win32/Toolbar.CrossRider.E application
C:\AdwCleaner\Quarantine\C\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.exe.vir a variant of Win32/Toolbar.CrossRider.E application
C:\AdwCleaner\Quarantine\C\Program Files (x86)\Giant Savings Extension\Giant Savings ExtensionGui.exe.vir a variant of Win32/Toolbar.CrossRider.F application
C:\Program Files (x86)\Dell Backup and Recovery\Components\DBRUpdate\hstart.exe a variant of Win32/HiddenStart.A application
C:\Users\Lynne\AppData\Local\Temp\DownloadManager2.exe a variant of Win32/OutBrowse.D application
C:\Users\Lynne\Downloads\avc-free.exe Win32/OpenCandy application
C:\Users\Lynne\Downloads\cbsidlm-tr1_13-Free_CUDA_Video_Converter-SEO-75728291 (1).exe Win32/DownloadAdmin.G application
C:\Users\Lynne\Downloads\cbsidlm-tr1_13-Free_CUDA_Video_Converter-SEO-75728291.exe Win32/DownloadAdmin.G application
C:\Users\Lynne\Downloads\IE_Setup.exe a variant of Win32/Adware.iBryte.G application
C:\Users\Lynne\Downloads\SoftonicDownloader_for_sony-vegas-video.exe Win32/SoftonicDownloader.E application
Fiery said:Ok, let me know how things go. One more scan and then we will clean up.
Run Eset NOD32 Online AntiVirus here
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
- Tick the box next to YES, I accept the Terms of Use.
- Click Start
- When asked, allow the activex control to install
- Disable your current antivirus software. You can usually do this with its Notfication Tray icon near the clock.
- Make sure that the option "Remove found threats" is Un-checked, and the following Advance Settings are Checked
- Scan unwanted applications
- Scan for potentially unsafe applications
- Enable Anti-Stealth Technology
- Click Scan
- Wait for the scan to finish
- When the scan is done, if it shows a screen that says "Threats found!", then click "List of found threats", and then click "Export to text file..."
- Save that text file on your desktop. Copy and paste the contents of that log in your next reply to this topic.
- The log can also be found in logfile located at C:\Program Files\ESET\Eset Online Scanner\log.txt
Hi again Fiery - the computer is acting up again. Not as bad (doesn't turn off the McAffee) but definitely not right. It freezes for long periods of time (usually after it sits idle for hours), CTRL-ALT-DEL won't work when it is frozen, I opened Gmail yesterday and it took forever to load ... when it did the desktop gadgets (clock, weather, etc.) were showing through the Gmail page (even though it was maximized to fit the entire monitor screen). Little things like that. I also get an Intel warning occasionally, something that I never saw before. The computer is 10 months old. My 12 year old son plays a lot of Roblox and Minecraft. My usage is email, facebook, banking and bill paying, research, and creating picture slideshows on DVD. Have a happy Hump Day! ~Lynne
Fiery said:Hi,
After these 2 steps below, please give me an update on your PC's performance and any other symptoms that you may still be experiencing.
Open OTL. Under custom scan/fixes, copy and paste the following:
:OTL
O2 - BHO: (Giant Savings Extension) - {11111111-1111-1111-1111-110211181110} - C:\Program Files (x86)\Giant Savings Extension\Giant Savings Extension.dll (215 Apps)
O2 - BHO: (DownloadTerms) - {2C4BA31C-0C15-11E2-90C7-9BFCBEB168B3} - C:\Users\Lynne\AppData\Local\DownloadTerms\temp.dat File not found
:Files
C:\Program Files (x86)\Giant Savings Extension
C:\Users\Lynne\AppData\Local\DownloadTerms
C:\Users\Lynne\AppData\Local\Temp\Quarantine.exe
:Commands
[EMPTYTEMP]
Then click Run Fix. Let your PC reboot to normal mode. A new log will be created automatically, post the content in the next reply.
Please download Malwarebytes' Anti-Malware from here to your desktop.
- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to
- Update Malwarebytes' Anti-Malware
- and Launch Malwarebytes' Anti-Malware
- then click Finish.
- If an update is found, it will download and install the latest version.
- When it prompts you to try their 30-day trail, click decline
- Once the program has loaded, select Perform quick scan, then click Scan.
- When the scan is complete, click OK, then Show Results to view the results.
- Be sure that everything is Checked (ticked) except items in the C:\System Volume Information folder and click on Remove Selected.
- When completed, a log will open in Notepad. please copy and paste the log into your next reply
- If you accidently close it, the log file is saved here and will be named like this:
- C:\Documents and Settings\Username\Application Data\Malwarebytes\Malwarebytes' Anti-Malware\Logs\mbam-log-date (time).txt
Ok, let's get a fresh OTL log.
- Double click on OTL.exe to run it.
- Click the Scan All Users checkbox.
- Check the boxes beside LOP Check and Purity Check
- Click on Run Scan at the top left hand corner.
- When done, one Notepad file will open.
You may also like...
-
-
My computer is being hacked and remotely access and no one can detect it
- Started by Rov123
- Replies: 3
-
On Sale! McAfee Total Protection 10-Device 2025 | 15-Months
- Started by Brownie2019
- Replies: 2
-
AVLab.pl Analysis of system protection against active online malware – July 2025
- Started by Adrian Ścibor
- Replies: 165