(1)
aswMBR version 0.9.9.1707 Copyright(c) 2011 AVAST Software
Run date: 2013-01-10 15:44:45
-----------------------------
15:44:45.265 OS Version: Windows 5.1.2600 Service Pack 3
15:44:45.265 Number of processors: 1 586 0x205
15:44:45.265 ComputerName: YADDLE UserName: David
15:44:45.921 Initialize success
15:55:00.718 AVAST engine defs: 13011000
15:56:46.906 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\Scsi\symmpi1Port1Path0Target0Lun0
15:56:46.906 Disk 0 Vendor: SEAGATE_ DX10 Size: 70007MB BusType: 1
15:56:46.906 Disk 0 MBR read successfully
15:56:46.906 Disk 0 MBR scan
15:56:46.937 Disk 0 Windows XP default MBR code
15:56:46.937 Disk 0 Partition 1 00 DE Dell Utility Dell 4.1 39 MB offset 63
15:56:46.968 Disk 0 Partition 2 80 (A) 07 HPFS/NTFS NTFS 69962 MB offset 80325
15:56:46.984 Disk 0 scanning sectors +143364060
15:56:47.031 Disk 0 scanning C:\WINDOWS\system32\drivers
15:57:19.390 Service scanning
15:58:10.921 Modules scanning
15:58:19.078 Disk 0 trace - called modules:
15:58:19.093 ntoskrnl.exe CLASSPNP.SYS disk.sys SCSIPORT.SYS hal.dll symmpi.sys
15:58:19.093 1 nt!IofCallDriver -> \Device\Harddisk0\DR0[0x8ad19ab8]
15:58:19.093 3 CLASSPNP.SYS[f7657fd7] -> nt!IofCallDriver -> \Device\Scsi\symmpi1Port1Path0Target0Lun0[0x8acdc030]
15:58:19.500 AVAST engine scan C:\WINDOWS
15:58:44.328 AVAST engine scan C:\WINDOWS\system32
16:04:21.578 AVAST engine scan C:\WINDOWS\system32\drivers
16:05:00.531 AVAST engine scan C:\Documents and Settings\David
16:12:07.125 AVAST engine scan C:\Documents and Settings\All Users
16:12:50.625 Scan finished successfully
16:24:27.937 Disk 0 MBR has been saved successfully to "C:\Documents and Settings\David\Desktop\MBR.dat"
16:24:27.953 The log file has been saved successfully to "C:\Documents and Settings\David\Desktop\aswMBR.txt"
Below is the OTL log I created with your original instructions by scanning all users clicking on LOP check and Purity Check, etc.
(2)
OTL logfile created on: 1/11/2013 12:01:57 AM - Run 3
OTL by OldTimer - Version 3.2.69.0 Folder = C:\Documents and Settings\David\Desktop
Windows XP Professional Edition Service Pack 3 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
2.00 Gb Total Physical Memory | 1.40 Gb Available Physical Memory | 70.11% Memory free
3.85 Gb Paging File | 3.44 Gb Available in Paging File | 89.30% Paging File free
Paging file location(s): C:\pagefile.sys 0 0 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 68.32 Gb Total Space | 44.54 Gb Free Space | 65.20% Space Free | Partition Type: NTFS
Computer Name: YADDLE | User Name: David | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: All users | Quick Scan
Company Name Whitelist: On | Skip Microsoft Files: On | No Company Name Whitelist: On | File Age = 30 Days
========== Processes (SafeList) ==========
PRC - [2013/01/10 23:57:35 | 000,917,552 | ---- | M] (Mozilla Corporation) -- C:\Program Files\Mozilla Firefox\firefox.exe
PRC - [2013/01/07 19:38:05 | 000,602,112 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\David\Desktop\OTL.exe
PRC - [2012/12/14 16:49:28 | 000,398,184 | ---- | M] (Malwarebytes Corporation) -- C:\Program Files\Malwarebytes' Anti-Malware\mbamscheduler.exe
PRC - [2012/11/28 17:04:52 | 001,695,816 | ---- | M] (InternetSafety.com, Inc.) -- C:\Program Files\Internet Content Filter\UpdateService.exe
PRC - [2012/11/28 17:03:46 | 003,267,072 | ---- | M] (InternetSafety.com, Inc.) -- C:\Program Files\Internet Content Filter\SafeEyes.exe
PRC - [2012/09/12 17:25:22 | 000,020,472 | ---- | M] (Microsoft Corporation) -- c:\Program Files\Microsoft Security Client\MsMpEng.exe
PRC - [2012/09/12 17:19:44 | 000,947,176 | ---- | M] (Microsoft Corporation) -- C:\Program Files\Microsoft Security Client\msseces.exe
PRC - [2010/10/28 19:02:02 | 000,056,952 | ---- | M] (Ipswitch) -- C:\Program Files\Ipswitch\WS_FTP 12\WsftpCOMHelper.exe
PRC - [2009/11/11 10:21:38 | 000,583,640 | ---- | M] (PC Tools) -- C:\Program Files\Common Files\PC Tools\sMonitor\StartManSvc.exe
PRC - [2008/04/13 19:12:19 | 001,033,728 | ---- | M] (Microsoft Corporation) -- C:\WINDOWS\explorer.exe
PRC - [2004/03/11 23:00:30 | 000,135,168 | ---- | M] (Dell Inc.) -- c:\Program Files\Dell Printers\Additional Color Laser Software\Status Monitor\dlsdbnt.exe
PRC - [2004/03/11 23:00:30 | 000,090,112 | ---- | M] (Dell Inc.) -- c:\Program Files\Dell Printers\Additional Color Laser Software\Status Monitor\dlpwdnt.exe
PRC - [2003/12/11 11:30:00 | 000,049,152 | ---- | M] (ATI Technologies, Inc.) -- C:\Program Files\ATI Technologies\Fire GL Control Panel\atiisrgl.exe
PRC - [2002/08/07 06:34:26 | 000,221,184 | ---- | M] (Intel Corporation) -- C:\Program Files\intel\ASF Agent\ASFAgent.exe
========== Modules (No Company Name) ==========
MOD - [2013/01/10 23:56:01 | 003,021,872 | ---- | M] () -- C:\Program Files\Mozilla Firefox\mozjs.dll
MOD - [2012/02/17 19:55:35 | 000,166,912 | ---- | M] () -- C:\Program Files\WinRAR\RarExt.dll
MOD - [2010/10/28 18:55:42 | 006,551,672 | ---- | M] () -- C:\Program Files\Ipswitch\WS_FTP 12\res0409.dll
MOD - [2010/10/28 18:52:36 | 000,948,496 | ---- | M] () -- C:\Program Files\Ipswitch\WS_FTP 12\libeay32.dll
MOD - [2010/10/28 18:52:36 | 000,153,360 | ---- | M] () -- C:\Program Files\Ipswitch\WS_FTP 12\ssleay32.dll
MOD - [2008/04/13 19:11:59 | 000,014,336 | ---- | M] () -- C:\WINDOWS\SYSTEM32\msdmo.dll
========== Services (SafeList) ==========
SRV - File not found [Disabled | Stopped] -- %SystemRoot%\System32\hidserv.dll -- (HidServ)
SRV - [2013/01/10 23:57:34 | 000,115,760 | ---- | M] (Mozilla Foundation) [On_Demand | Stopped] -- C:\Program Files\Mozilla Maintenance Service\maintenanceservice.exe -- (MozillaMaintenance)
SRV - [2013/01/09 12:50:52 | 000,251,400 | ---- | M] (Adobe Systems Incorporated) [On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\Macromed\Flash\FlashPlayerUpdateService.exe -- (AdobeFlashPlayerUpdateSvc)
SRV - [2012/12/14 16:49:28 | 000,682,344 | ---- | M] (Malwarebytes Corporation) [Auto | Stopped] -- C:\Program Files\Malwarebytes' Anti-Malware\mbamservice.exe -- (MBAMService)
SRV - [2012/12/14 16:49:28 | 000,398,184 | ---- | M] (Malwarebytes Corporation) [Auto | Running] -- C:\Program Files\Malwarebytes' Anti-Malware\mbamscheduler.exe -- (MBAMScheduler)
SRV - [2012/11/28 17:04:52 | 001,695,816 | ---- | M] (InternetSafety.com, Inc.) [Auto | Running] -- C:\Program Files\Internet Content Filter\UpdateService.exe -- (seUpdateSvc)
SRV - [2012/11/28 17:04:52 | 001,695,816 | ---- | M] (InternetSafety.com, Inc.) [Auto | Running] -- C:\Program Files\Internet Content Filter\UpdateService.exe -- (mfeicfupdate)
SRV - [2012/09/12 17:25:22 | 000,020,472 | ---- | M] (Microsoft Corporation) [Auto | Running] -- c:\Program Files\Microsoft Security Client\MsMpEng.exe -- (MsMpSvc)
SRV - [2009/11/11 10:21:38 | 000,583,640 | ---- | M] (PC Tools) [Auto | Running] -- C:\Program Files\Common Files\PC Tools\sMonitor\StartManSvc.exe -- (PCToolsSSDMonitorSvc)
SRV - [2004/10/15 09:12:38 | 000,131,072 | ---- | M] (SonicWALL, Inc.) [On_Demand | Stopped] -- C:\Program Files\SonicWALL\SonicWALL Global VPN Client\RampartSvc.exe -- (RampartSvc)
SRV - [2004/03/11 23:00:30 | 000,135,168 | ---- | M] (Dell Inc.) [Auto | Running] -- c:\Program Files\Dell Printers\Additional Color Laser Software\Status Monitor\dlsdbnt.exe -- (DLSDB)
SRV - [2004/03/11 23:00:30 | 000,090,112 | ---- | M] (Dell Inc.) [Auto | Running] -- c:\Program Files\Dell Printers\Additional Color Laser Software\Status Monitor\dlpwdnt.exe -- (DLPWD)
SRV - [2003/12/11 11:30:00 | 000,049,152 | ---- | M] (ATI Technologies, Inc.) [Auto | Running] -- C:\Program Files\ATI Technologies\Fire GL Control Panel\atiisrgl.exe -- (FGLRYUtil)
SRV - [2002/08/07 06:34:26 | 000,221,184 | ---- | M] (Intel Corporation) [Auto | Running] -- C:\Program Files\intel\ASF Agent\ASFAgent.exe -- (ASFAgent)
SRV - [2002/07/30 17:15:24 | 001,118,208 | ---- | M] (Intel Corporation) [On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\NMSSvc.Exe -- (NMSSvc)
========== Driver Services (SafeList) ==========
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (WDICA)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\RkPavproc3.sys -- (RkPavproc3)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\RkPavproc2.sys -- (RkPavproc2)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\RkPavproc1.sys -- (RkPavproc1)
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (PDRFRAME)
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (PDRELI)
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (PDFRAME)
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (PDCOMP)
DRV - File not found [Kernel | System | Stopped] -- -- (PCIDump)
DRV - File not found [Kernel | System | Stopped] -- -- (lbrtfdc)
DRV - File not found [Kernel | On_Demand | Stopped] -- System32\DRIVERS\wATV03nt.sys -- (iAimTV2)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\DOCUME~1\David\LOCALS~1\Temp\cpuz134\cpuz134_x32.sys -- (cpuz134)
DRV - File not found [Kernel | System | Stopped] -- -- (Changer)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\DOCUME~1\David\LOCALS~1\Temp\catchme.sys -- (catchme)
DRV - File not found [Kernel | On_Demand | Stopped] -- System32\Drivers\BW2NDIS5.sys -- (BW2NDIS5)
DRV - File not found [Kernel | On_Demand | Unknown] -- C:\DOCUME~1\David\LOCALS~1\Temp\aswMBR.sys -- (aswMBR)
DRV - [2013/01/10 16:27:41 | 000,029,904 | ---- | M] (Microsoft Corporation) [Kernel | System | Running] -- c:\Documents and Settings\All Users\Application Data\Microsoft\Microsoft Antimalware\Definition Updates\{03E6FF9C-C04C-418D-B466-32F75BC457F4}\MpKsl571993da.sys -- (MpKsl571993da)
DRV - [2013/01/07 00:17:16 | 000,017,904 | ---- | M] (Emsi Software GmbH) [Kernel | System | Running] -- C:\Documents and Settings\David\Desktop\fffu\EmsisoftEmergencyKit\Run\a2ddax86.sys -- (A2DDA)
DRV - [2012/12/14 16:49:28 | 000,021,104 | ---- | M] (Malwarebytes Corporation) [File_System | On_Demand | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\mbam.sys -- (MBAMProtector)
DRV - [2010/11/09 13:56:12 | 000,098,392 | ---- | M] (Sunbelt Software) [Kernel | System | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\SBREDrv.sys -- (SBRE)
DRV - [2008/04/13 13:40:51 | 000,008,320 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\dlttape.sys -- (dlttape)
DRV - [2008/01/26 06:50:20 | 000,194,320 | ---- | M] (Kaspersky Lab) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\klif.sys -- (KLIF)
DRV - [2004/10/15 09:46:12 | 000,091,136 | ---- | M] (SonicWALL, Inc.) [Kernel | System | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\RCFOX.SYS -- (RCFOX)
DRV - [2004/08/04 00:29:49 | 000,019,455 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wvchntxx.sys -- (iAimFP4)
DRV - [2004/08/04 00:29:47 | 000,012,063 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wsiintxx.sys -- (iAimFP3)
DRV - [2004/08/04 00:29:45 | 000,023,615 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wch7xxnt.sys -- (iAimTV4)
DRV - [2004/08/04 00:29:43 | 000,033,599 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\watv04nt.sys -- (iAimTV3)
DRV - [2004/08/04 00:29:42 | 000,019,551 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\watv02nt.sys -- (iAimTV1)
DRV - [2004/08/04 00:29:41 | 000,029,311 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\watv01nt.sys -- (iAimTV0)
DRV - [2004/08/04 00:29:37 | 000,012,415 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wadv01nt.sys -- (iAimFP0)
DRV - [2004/08/04 00:29:37 | 000,012,127 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wadv02nt.sys -- (iAimFP1)
DRV - [2004/08/04 00:29:37 | 000,011,775 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wadv05nt.sys -- (iAimFP2)
DRV - [2004/08/04 00:29:36 | 000,161,020 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\i81xnt5.sys -- (i81x)
DRV - [2004/05/14 16:15:22 | 000,147,236 | ---- | M] (Deterministic Networks, Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\dne2000.sys -- (DNE)
DRV - [2004/01/22 01:54:23 | 000,206,464 | ---- | M] (Roxio) [File_System | System | Running] -- C:\WINDOWS\System32\drivers\udfreadr_xp.sys -- (UdfReadr_xp)
DRV - [2004/01/22 01:54:23 | 000,143,834 | ---- | M] (Roxio) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\pwd_2K.sys -- (pwd_2k)
DRV - [2004/01/22 01:54:23 | 000,030,630 | ---- | M] (Roxio) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\System32\drivers\Mmc_2k.sys -- (mmc_2K)
DRV - [2004/01/22 01:54:23 | 000,025,898 | ---- | M] (Roxio) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\System32\drivers\Dvd_2k.sys -- (dvd_2K)
DRV - [2003/12/11 08:56:40 | 000,630,272 | ---- | M] (ATI Technologies Inc.) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ati2mtag.sys -- (ati2mtag)
DRV - [2003/11/20 12:03:06 | 000,009,728 | ---- | M] (Quantum Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\QntmDLT.sys -- (QntmDLT)
DRV - [2003/08/20 13:01:22 | 000,023,180 | ---- | M] (SonicWALL, Inc.) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\rcvpn.sys -- (rcvpn)
DRV - [2003/03/27 11:58:56 | 000,287,920 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctdvda2k.sys -- (ctdvda2k)
DRV - [2003/03/26 16:33:58 | 000,498,688 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctaud2k.sys -- (ctaud2k)
DRV - [2003/03/26 16:32:32 | 000,189,504 | ---- | M] (Creative Technology Ltd.) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctoss2k.sys -- (ossrv)
DRV - [2003/03/26 16:32:02 | 000,141,536 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\hap16v2k.sys -- (hap16v2k)
DRV - [2003/03/26 16:31:40 | 000,823,616 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ha10kx2k.sys -- (ha10kx2k)
DRV - [2003/03/06 10:10:34 | 000,015,840 | ---- | M] (Creative Technology Ltd.) [Kernel | Auto | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\pfmodnt.sys -- (PfModNT)
DRV - [2003/02/20 17:24:46 | 000,116,000 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\emupia2k.sys -- (emupia)
DRV - [2003/02/20 17:24:34 | 000,135,248 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctsfm2k.sys -- (ctsfm2k)
DRV - [2003/02/20 17:24:18 | 000,006,144 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctprxy2k.sys -- (ctprxy2k)
DRV - [2003/02/20 17:22:38 | 000,135,040 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctac32k.sys -- (ctac32k)
DRV - [2002/12/17 13:32:58 | 000,061,424 | ---- | M] (Roxio) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\cdr4_xp.sys -- (Cdr4_xp)
DRV - [2002/12/17 13:32:46 | 000,023,436 | ---- | M] (Roxio) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\cdralw2k.sys -- (Cdralw2k)
DRV - [2002/12/17 13:27:32 | 000,241,152 | ---- | M] (Roxio) [File_System | System | Running] -- C:\WINDOWS\System32\drivers\cdudf_xp.sys -- (cdudf_xp)
DRV - [2002/11/08 14:45:06 | 000,017,217 | ---- | M] (Dell Computer Corporation) [Kernel | System | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\omci.sys -- (omci)
DRV - [2002/08/29 14:29:12 | 000,036,096 | ---- | M] (LSI Logic) [Kernel | Boot | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\SYMMPI.SYS -- (symmpi)
DRV - [2002/07/30 17:15:40 | 000,009,868 | ---- | M] (Intel Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\NMSCFG.SYS -- (NMSCFG)
DRV - [2002/05/07 17:06:36 | 000,023,744 | ---- | M] (Intel Corporation) [Kernel | Auto | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\platalrt.sys -- (PlatAlrt)
DRV - [2002/05/07 17:05:56 | 000,039,680 | ---- | M] (Intel Corporation) [Kernel | Auto | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\Netalrt.sys -- (NetAlrt)
DRV - [2001/08/17 13:11:06 | 000,066,591 | ---- | M] (3Com Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\EL90XBC5.SYS -- (EL90XBC)
========== Standard Registry (SafeList) ==========
========== Internet Explorer ==========
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Search,Default_Search_URL = http://www.google.com/ie
IE - HKLM\..\SearchScopes,DefaultScope =
IE - HKLM\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" = http://search.live.com/results.aspx?q={searchTerms}&src={referrer:source?}
IE - HKU\.DEFAULT\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.dell.com
IE - HKU\.DEFAULT\SOFTWARE\Microsoft\Internet Explorer\Main,First Home Page = http://www.dell.com
IE - HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-18\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.dell.com
IE - HKU\S-1-5-18\SOFTWARE\Microsoft\Internet Explorer\Main,First Home Page = http://www.dell.com
IE - HKU\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-19\..\SearchScopes,DefaultScope =
IE - HKU\S-1-5-19\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-20\..\SearchScopes,DefaultScope =
IE - HKU\S-1-5-20\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Search_URL = http://www.earthlink.net/partner/more/msie/button/search.html
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.google.com/
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Internet Explorer\Search,SearchAssistant = http://www.google.com/ie
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\SearchScopes,DefaultScope = {C1046C13-D6E3-4AA1-ADF6-319BB623E49D}
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" = http://www.bing.com/search?q={searchTerms}&src=IE-SearchBox&FORM=IE8SRC
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\SearchScopes\{C1046C13-D6E3-4AA1-ADF6-319BB623E49D}: "URL" = http://www.google.com/search?q={searchTerms}&sourceid=ie7&rls=com.microsoft:en-US&ie=utf8&oe=utf8
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-500\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.dell.com
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-500\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.dell.com
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-500\..\SearchScopes,DefaultScope = {0633EE93-D776-472f-A0FF-E1416B8B2E3A}
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
========== FireFox ==========
FF - prefs.js..browser.search.defaultenginename: ""
FF - prefs.js..browser.search.order.1: ""
FF - prefs.js..browser.search.selectedEngine: "Google"
FF - prefs.js..browser.startup.homepage: "http://www.christcenteredmall.com/stores/art/"
FF - prefs.js..extensions.enabledAddons: %7B972ce4c6-7e08-4474-a285-3208198ce6fd%7D:18.0
FF - prefs.js..network.proxy.type: 0
FF - user.js - File not found
FF - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\WINDOWS\system32\Macromed\Flash\NPSWF32_11_5_502_146.dll ()
FF - HKLM\Software\MozillaPlugins\@Microsoft.com/NpCtrl,version=1.0: c:\Program Files\Microsoft Silverlight\4.1.10329.0\npctrl.dll ( Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/WPF,version=3.5: c:\WINDOWS\Microsoft.NET\Framework\v3.5\Windows Presentation Foundation\NPWPF.dll (Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@real.com/nppl3260;version=15.0.6.14: C:\Program Files\Real\RealPlayer\Netscape6\nppl3260.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprjplug;version=15.0.6.14: C:\Program Files\Real\RealPlayer\Netscape6\nprjplug.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprpchromebrowserrecordext;version=15.0.6.14: C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprpchromebrowserrecordext.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprphtml5videoshim;version=15.0.6.14: C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprphtml5videoshim.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprpplugin;version=15.0.6.14: C:\Program Files\Real\RealPlayer\Netscape6\nprpplugin.dll (RealPlayer)
FF - HKLM\Software\MozillaPlugins\@tools.google.com/Google Update;version=3: C:\Program Files\Google\Update\1.3.21.124\npGoogleUpdate3.dll (Google Inc.)
FF - HKLM\Software\MozillaPlugins\@tools.google.com/Google Update;version=9: C:\Program Files\Google\Update\1.3.21.124\npGoogleUpdate3.dll (Google Inc.)
FF - HKLM\Software\MozillaPlugins\@videolan.org/vlc,version=2.0.3: C:\Program Files\VideoLAN\VLC\npvlc.dll (VideoLAN)
FF - HKLM\Software\MozillaPlugins\Adobe Reader: C:\Program Files\Adobe\Reader 10.0\Reader\AIR\nppdf32.dll (Adobe Systems Inc.)
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\{0153E448-190B-4987-BDE1-F256CADA672F}: C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\Firefox\Ext [2012/09/14 22:42:51 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 18.0\extensions\\Components: C:\Program Files\Mozilla Firefox\components [2013/01/10 23:57:36 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 18.0\extensions\\Plugins: C:\Program Files\Mozilla Firefox\plugins
[2011/03/22 16:31:40 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\David\Application Data\Mozilla\Extensions
[2012/12/15 15:34:25 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\David\Application Data\Mozilla\Firefox\Profiles\ch1ntccj.default\extensions
[2012/12/15 15:34:25 | 000,804,627 | ---- | M] () (No name found) -- C:\Documents and Settings\David\Application Data\Mozilla\Firefox\Profiles\ch1ntccj.default\extensions\{d10d0bf8-f5b5-c8b4-a8b2-2b9879e08c5d}.xpi
[2013/01/10 23:55:35 | 000,000,000 | ---D | M] (No name found) -- C:\Program Files\Mozilla Firefox\extensions
[2013/01/10 23:57:36 | 000,262,704 | ---- | M] (Mozilla Foundation) -- C:\Program Files\mozilla firefox\components\browsercomps.dll
[2012/08/30 14:25:05 | 000,002,465 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\bing.xml
[2012/10/21 09:26:34 | 000,002,058 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\twitter.xml
========== Chrome ==========
CHR - homepage: http://www.google.com/
CHR - default_search_provider: Google (Enabled)
CHR - default_search_provider: search_url = {google:baseURL}search?q={searchTerms}&{google:RLZ}{google:acceptedSuggestion}{google riginalQueryForSuggestion}{google:assistedQueryStats}{google:searchFieldtrialParameter}sourceid=chrome&ie={inputEncoding}
riginalQueryForSuggestion}{google:assistedQueryStats}{google:searchFieldtrialParameter}sourceid=chrome&ie={inputEncoding}
CHR - default_search_provider: suggest_url = {google:baseSuggestURL}search?{google:searchFieldtrialParameter}client=chrome&hl={language}&q={searchTerms}&sugkey={google:suggestAPIKeyParameter}
CHR - homepage: http://www.google.com/
CHR - plugin: Shockwave Flash (Enabled) = C:\Program Files\Google\Chrome\Application\23.0.1271.97\PepperFlash\pepflashplayer.dll
CHR - plugin: Shockwave Flash (Enabled) = C:\WINDOWS\system32\Macromed\Flash\NPSWF32_11_4_402_287.dll
CHR - plugin: Chrome Remote Desktop Viewer (Enabled) = internal-remoting-viewer
CHR - plugin: Native Client (Enabled) = C:\Program Files\Google\Chrome\Application\23.0.1271.97\ppGoogleNaClPluginChrome.dll
CHR - plugin: Chrome PDF Viewer (Enabled) = C:\Program Files\Google\Chrome\Application\23.0.1271.97\pdf.dll
CHR - plugin: Adobe Acrobat (Enabled) = C:\Program Files\Adobe\Reader 10.0\Reader\Browser\nppdf32.dll
CHR - plugin: Microsoft\u00AE DRM (Enabled) = C:\Program Files\Windows Media Player\npdrmv2.dll
CHR - plugin: Microsoft\u00AE DRM (Enabled) = C:\Program Files\Windows Media Player\npwmsdrm.dll
CHR - plugin: Windows Media Player Plug-in Dynamic Link Library (Enabled) = C:\Program Files\Windows Media Player\npdsplay.dll
CHR - plugin: RealNetworks(tm) Chrome Background Extension Plug-In (32-bit) (Enabled) = C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprpchromebrowserrecordext.dll
CHR - plugin: RealPlayer(tm) HTML5VideoShim Plug-In (32-bit) (Enabled) = C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprphtml5videoshim.dll
CHR - plugin: RealPlayer(tm) G2 LiveConnect-Enabled Plug-In (32-bit) (Enabled) = C:\Program Files\Real\RealPlayer\Netscape6\nppl3260.dll
CHR - plugin: RealPlayer Download Plugin (Enabled) = C:\Program Files\Real\RealPlayer\Netscape6\nprpplugin.dll
CHR - plugin: Google Update (Enabled) = C:\Program Files\Google\Update\1.3.21.124\npGoogleUpdate3.dll
CHR - plugin: RealJukebox NS Plugin (Enabled) = C:\Program Files\Real\RealPlayer\Netscape6\nprjplug.dll
CHR - plugin: VLC Web Plugin (Enabled) = C:\Program Files\VideoLAN\VLC\npvlc.dll
CHR - plugin: Silverlight Plug-In (Enabled) = c:\Program Files\Microsoft Silverlight\4.1.10329.0\npctrl.dll
CHR - plugin: Windows Presentation Foundation (Enabled) = c:\WINDOWS\Microsoft.NET\Framework\v3.5\Windows Presentation Foundation\NPWPF.dll
CHR - Extension: YouTube = C:\Documents and Settings\David\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\blpcfgokakmgnkcojhhkbfbldkacnbeo\4.2.5_1\
CHR - Extension: Google Search = C:\Documents and Settings\David\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf\0.0.0.19_1\
CHR - Extension: RealPlayer HTML5Video Downloader Extension = C:\Documents and Settings\David\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\jfmjfhklogoienhpfnppmbcbjfjnkonk\1.5_0\
CHR - Extension: Gmail = C:\Documents and Settings\David\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\pjkljhegncpnkpknbcohdijeoejaedia\7_1\
O1 HOSTS File: ([2013/01/09 22:43:06 | 000,000,855 | ---- | M]) - C:\WINDOWS\SYSTEM32\DRIVERS\ETC\Hosts
O1 - Hosts: 127.0.0.1 localhost
O2 - BHO: (RealPlayer Download and Record Plugin for Internet Explorer) - {3049C3E9-B461-4BC5-8870-4C09146192CA} - C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\IE\rpbrowserrecordplugin.dll (RealPlayer)
O2 - BHO: (Spybot-S&D IE Protection) - {53707962-6F74-2D53-2644-206D7942484F} - C:\Program Files\Spybot - Search & Destroy\SDHelper.dll (Safer Networking Limited)
O2 - BHO: (SSVHelper Class) - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files\Java\jre1.6.0_05\bin\ssv.dll (Sun Microsystems, Inc.)
O3 - HKU\.DEFAULT\..\Toolbar\WebBrowser: (no name) - {2318C2B1-4965-11D4-9B18-009027A5CD4F} - No CLSID value found.
O3 - HKU\S-1-5-18\..\Toolbar\WebBrowser: (no name) - {2318C2B1-4965-11D4-9B18-009027A5CD4F} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\ShellBrowser: (no name) - {2318C2B1-4965-11D4-9B18-009027A5CD4F} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\ShellBrowser: (no name) - {47833539-D0C5-4125-9FA8-0819E2EAAC93} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {430DDB4F-38CC-4E91-AF33-4157334EC937} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {472734EA-242A-422B-ADF8-83D1E48CC825} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {47833539-D0C5-4125-9FA8-0819E2EAAC93} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {C7768536-96F8-4001-B1A2-90EE21279187} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {D7F30B62-8269-41AF-9539-B2697FA7D77E} - No CLSID value found.
O4 - HKLM..\Run: [ICF] C:\Program Files\Internet Content Filter\SafeEyes.exe (InternetSafety.com, Inc.)
O4 - HKLM..\Run: [MSC] c:\Program Files\Microsoft Security Client\msseces.exe (Microsoft Corporation)
O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Restrictions present
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: HonorAutoRunSetting = 1
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O7 - HKU\.DEFAULT\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: CDRAutoRun = 0
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\S-1-5-18\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: CDRAutoRun = 0
O7 - HKU\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\S-1-5-19\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-19\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O7 - HKU\S-1-5-20\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-20\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-500\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-500\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O9 - Extra 'Tools' menuitem : Sun Java Console - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.6.0_05\bin\npjpi160_05.dll (Sun Microsystems, Inc.)
O9 - Extra 'Tools' menuitem : Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\Program Files\Spybot - Search & Destroy\SDHelper.dll (Safer Networking Limited)
O10 - Protocol_Catalog9\Catalog_Entries\000000000001 - %SystemRoot%\System32\mswsock.dll File not found
O10 - Protocol_Catalog9\Catalog_Entries\000000000002 - %SystemRoot%\System32\mswsock.dll File not found
O10 - Protocol_Catalog9\Catalog_Entries\000000000044 - %SystemRoot%\System32\mswsock.dll File not found
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: ([]msn in My Computer)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: cj.com ([members] https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: cj.com ([signup] https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: cj.com ([www] https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: linkshare.com ([]https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: overture.com ([secure] https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: shareasale.com ([]https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Ranges: Range32 ([https] in Trusted sites)
O16 - DPF: {04E214E5-63AF-4236-83C6-A7ADCBF9BD02} http://housecall60.trendmicro.com/housecall/xscan60.cab (HouseCall Control)
O16 - DPF: {166B1BCA-3F9C-11CF-8075-444553540000} http://download.macromedia.com/pub/shockwave/cabs/director/sw.cab (Shockwave ActiveX Control)
O16 - DPF: {17492023-C23A-453E-A040-C7C580BBF700} http://go.microsoft.com/fwlink/?linkid=39204 (Windows Genuine Advantage Validation Tool)
O16 - DPF: {2BC66F54-93A8-11D3-BEB6-00105AA9B6AE} http://security.symantec.com/sscv6/SharedContent/vc/bin/AvSniff.cab (Symantec AntiVirus scanner)
O16 - DPF: {3E68E405-C6DE-49FF-83AE-41EE9F4C36CE} http://office.microsoft.com/officeupdate/content/opuc3.cab (Office Update Installation Engine)
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} http://www.update.microsoft.com/windowsupdate/v6/V5Controls/en/x86/client/wuweb_site.cab?1345029211828 (WUWebControl Class)
O16 - DPF: {644E432F-49D3-41A1-8DD5-E099162EEEC5} http://security.symantec.com/sscv6/SharedContent/common/bin/cabsa.cab (Symantec RuFSI Utility Class)
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} http://www.update.microsoft.com/microsoftupdate/v6/V5Controls/en/x86/client/muweb_site.cab?1348617615734 (MUWebControl Class)
O16 - DPF: {7530BFB8-7293-4D34-9923-61A11451AFC5} http://download.eset.com/special/eos/OnlineScanner.cab (Reg Error: Key error.)
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} http://java.sun.com/update/1.6.0/jinstall-1_6_0_05-windows-i586.cab (Java Plug-in 1.6.0_05)
O16 - DPF: {A8658086-E6AC-4957-BC8E-7D54A7E8A78E} http://www.microsoft.com/security/controls/SassCln.CAB (SassCln Object)
O16 - DPF: {CAFEEFAC-0014-0002-0000-ABCDEFFEDCBA} http://java.sun.com/products/plugin/autodl/jinstall-142-windows-i586.cab (Java Plug-in 1.4.2)
O16 - DPF: {CAFEEFAC-0015-0000-0002-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_02-windows-i586.cab (Java Plug-in 1.5.0_02)
O16 - DPF: {CAFEEFAC-0015-0000-0004-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_04-windows-i586.cab (Java Plug-in 1.5.0_04)
O16 - DPF: {CAFEEFAC-0015-0000-0005-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_05-windows-i586.cab (Java Plug-in 1.5.0_05)
O16 - DPF: {CAFEEFAC-0015-0000-0006-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_06-windows-i586.cab (Java Plug-in 1.5.0_06)
O16 - DPF: {CAFEEFAC-0015-0000-0009-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_09-windows-i586.cab (Java Plug-in 1.5.0_09)
O16 - DPF: {CAFEEFAC-0015-0000-0010-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_10-windows-i586.cab (Java Plug-in 1.5.0_10)
O16 - DPF: {CAFEEFAC-0015-0000-0011-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_11-windows-i586.cab (Java Plug-in 1.5.0_11)
O16 - DPF: {CAFEEFAC-0016-0000-0001-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_01-windows-i586.cab (Java Plug-in 1.6.0_01)
O16 - DPF: {CAFEEFAC-0016-0000-0002-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_02-windows-i586.cab (Java Plug-in 1.6.0_02)
O16 - DPF: {CAFEEFAC-0016-0000-0003-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_03-windows-i586.cab (Java Plug-in 1.6.0_03)
O16 - DPF: {CAFEEFAC-0016-0000-0005-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_05-windows-i586.cab (Java Plug-in 1.6.0_05)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_05-windows-i586.cab (Java Plug-in 1.6.0_05)
O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} http://fpdownload.adobe.com/pub/shockwave/cabs/flash/swflash.cab (Shockwave Flash Object)
O16 - DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7} http://platformdl.adobe.com/NOS/getPlusPlus/1.6/gp.cab (Reg Error: Key error.)
O16 - DPF: Microsoft XML Parser for Java file://C:\WINDOWS\Java\classes\xmldso.cab (Reg Error: Key error.)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 209.18.47.61 209.18.47.62
O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{C20CC9F1-1414-49A9-9A3A-122B89C617F6}: DhcpNameServer = 209.18.47.61 209.18.47.62
O20 - HKLM Winlogon: Shell - (Explorer.exe) - C:\WINDOWS\explorer.exe (Microsoft Corporation)
O20 - HKLM Winlogon: UserInit - (C:\WINDOWS\system32\userinit.exe) - C:\WINDOWS\SYSTEM32\userinit.exe (Microsoft Corporation)
O28 - HKLM ShellExecuteHooks: {56F9679E-7826-4C84-81F3-532071A8BCC5} - C:\Program Files\Windows Desktop Search\MsnlNamespaceMgr.dll (Microsoft Corporation)
O32 - HKLM CDRom: AutoRun - 1
O32 - AutoRun File - [2002/09/03 14:36:02 | 000,000,000 | ---- | M] () - C:\AUTOEXEC.BAT -- [ NTFS ]
O34 - HKLM BootExecute: (autocheck autochk *)
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = ComFile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
O38 - SubSystems\\Windows: (ServerDll=winsrv:UserServerDllInitialization,3)
O38 - SubSystems\\Windows: (ServerDll=winsrv:ConServerDllInitialization,2)
========== Files/Folders - Created Within 30 Days ==========
[2013/01/10 23:58:36 | 000,000,000 | RH-D | C] -- C:\Documents and Settings\David\Recent
[2013/01/10 23:55:34 | 000,000,000 | ---D | C] -- C:\Program Files\Mozilla Firefox
[2013/01/10 15:41:57 | 004,732,416 | ---- | C] (AVAST Software) -- C:\Documents and Settings\David\Desktop\aswMBR.exe
[2013/01/10 04:39:05 | 000,000,000 | -HSD | C] -- C:\RECYCLER
[2013/01/10 04:37:12 | 000,000,000 | ---D | C] -- C:\WINDOWS\temp
[2013/01/10 04:28:06 | 000,518,144 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWREG.exe
[2013/01/10 04:28:06 | 000,406,528 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWSC.exe
[2013/01/10 04:28:06 | 000,212,480 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWXCACLS.exe
[2013/01/10 04:28:06 | 000,060,416 | ---- | C] (NirSoft) -- C:\WINDOWS\NIRCMD.exe
[2013/01/10 04:25:09 | 000,000,000 | ---D | C] -- C:\Qoobox
[2013/01/10 04:20:32 | 005,019,950 | R--- | C] (Swearware) -- C:\Documents and Settings\David\Desktop\ComboFix.exe
[2013/01/09 21:06:20 | 000,181,064 | ---- | C] (Sysinternals) -- C:\WINDOWS\PSEXESVC.EXE
[2013/01/09 21:05:03 | 000,000,000 | ---D | C] -- C:\RegBackup
[2013/01/09 21:01:27 | 000,000,000 | ---D | C] -- C:\Tweaking.com_Windows_Repair_Logs
[2013/01/09 21:00:46 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\tweaking.com_windows_repair_aio
[2013/01/09 16:46:05 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\RK_Quarantine
[2013/01/08 20:08:29 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\mbar-1.01.0.1011
[2013/01/08 02:21:10 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\adzz
[2013/01/08 02:00:04 | 000,000,000 | ---D | C] -- C:\_OTL
[2013/01/07 19:37:44 | 000,602,112 | ---- | C] (OldTimer Tools) -- C:\Documents and Settings\David\Desktop\OTL.exe
[2013/01/07 03:33:25 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Application Data\ElevatedDiagnostics
[2013/01/07 03:32:42 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\Windows PowerShell 1.0
[2013/01/07 03:32:29 | 000,000,000 | ---D | C] -- C:\WINDOWS\System32\windowspowershell
[2013/01/07 02:38:33 | 000,000,000 | ---D | C] -- C:\ReimageUndo
[2013/01/06 23:58:42 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\Reimage Repair
[2013/01/06 23:58:39 | 000,000,000 | ---D | C] -- C:\rei
[2013/01/06 23:58:16 | 000,000,000 | ---D | C] -- C:\Program Files\Reimage
[2013/01/06 23:09:30 | 000,000,000 | ---D | C] -- C:\Program Files\Microsoft Security Client
[2013/01/06 21:38:28 | 000,012,872 | ---- | C] (SurfRight B.V.) -- C:\WINDOWS\System32\bootdelete.exe
[2013/01/06 21:33:42 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\HitmanPro
[2013/01/06 21:33:41 | 000,000,000 | ---D | C] -- C:\Program Files\HitmanPro
[2013/01/06 21:33:11 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\HitmanPro
[2013/01/06 21:32:42 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\roigguer
[2013/01/06 20:29:15 | 000,000,000 | RHSD | C] -- C:\cmdcons
[2013/01/06 20:27:30 | 000,000,000 | R--D | C] -- C:\Documents and Settings\All Users\Documents\My Videos
[2013/01/06 20:27:30 | 000,000,000 | R--D | C] -- C:\Documents and Settings\All Users\Documents\My Pictures
[2013/01/06 20:26:54 | 000,000,000 | ---D | C] -- C:\WINDOWS\erdnt
[2013/01/06 20:25:03 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\fffu
[2013/01/06 17:57:34 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\01014CE1ACC253E7000001014BE457DE
[2012/12/13 05:26:59 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\web page patches
========== Files - Modified Within 30 Days ==========
[2013/01/10 23:50:00 | 000,000,830 | ---- | M] () -- C:\WINDOWS\tasks\Adobe Flash Player Updater.job
[2013/01/10 23:24:00 | 000,000,884 | ---- | M] () -- C:\WINDOWS\tasks\GoogleUpdateTaskMachineUA.job
[2013/01/10 21:08:25 | 001,872,454 | ---- | M] () -- C:\Documents and Settings\David\Desktop\mockup.bmp
[2013/01/10 16:24:27 | 000,000,512 | ---- | M] () -- C:\Documents and Settings\David\Desktop\MBR.dat
[2013/01/10 15:42:56 | 004,732,416 | ---- | M] (AVAST Software) -- C:\Documents and Settings\David\Desktop\aswMBR.exe
[2013/01/10 14:33:56 | 000,002,515 | ---- | M] () -- C:\Documents and Settings\David\Application Data\Microsoft\Internet Explorer\Quick Launch\Word.lnk
[2013/01/10 10:41:30 | 000,000,384 | -H-- | M] () -- C:\WINDOWS\tasks\Microsoft Antimalware Scheduled Scan.job
[2013/01/10 10:31:54 | 000,000,286 | ---- | M] () -- C:\WINDOWS\tasks\RealUpgradeScheduledTaskS-1-5-21-989678199-2234712002-1868543911-1006.job
[2013/01/10 10:31:54 | 000,000,278 | ---- | M] () -- C:\WINDOWS\tasks\RealUpgradeLogonTaskS-1-5-21-989678199-2234712002-1868543911-1006.job
[2013/01/10 10:31:44 | 000,001,170 | ---- | M] () -- C:\WINDOWS\System32\WPA.DBL
[2013/01/10 10:31:30 | 000,000,880 | ---- | M] () -- C:\WINDOWS\tasks\GoogleUpdateTaskMachineCore.job
[2013/01/10 10:31:17 | 000,002,048 | --S- | M] () -- C:\WINDOWS\BOOTSTAT.DAT
[2013/01/10 10:31:16 | 2146,508,800 | -HS- | M] () -- C:\hiberfil.sys
[2013/01/10 04:20:52 | 005,019,950 | R--- | M] (Swearware) -- C:\Documents and Settings\David\Desktop\ComboFix.exe
[2013/01/09 22:43:28 | 000,181,064 | ---- | M] (Sysinternals) -- C:\WINDOWS\PSEXESVC.EXE
[2013/01/09 22:43:06 | 000,000,855 | ---- | M] () -- C:\WINDOWS\System32\drivers\ETC\Hosts
[2013/01/09 20:45:23 | 000,000,664 | ---- | M] () -- C:\WINDOWS\System32\d3d9caps.dat
[2013/01/09 18:05:53 | 003,293,002 | ---- | M] () -- C:\Documents and Settings\David\Desktop\tweaking.com_windows_repair_aio.zip
[2013/01/09 13:02:28 | 000,000,792 | ---- | M] () -- C:\Documents and Settings\David\Application Data\Microsoft\Internet Explorer\Quick Launch\Launch Microsoft Office Outlook.lnk
[2013/01/08 21:48:18 | 000,397,390 | ---- | M] () -- C:\WINDOWS\System32\perfh009.dat
[2013/01/08 21:48:18 | 000,059,736 | ---- | M] () -- C:\WINDOWS\System32\perfc009.dat
[2013/01/08 20:07:38 | 013,485,902 | ---- | M] () -- C:\Documents and Settings\David\Desktop\mbar-1.01.0.1011.zip
[2013/01/07 19:38:05 | 000,602,112 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\David\Desktop\OTL.exe
[2013/01/07 03:22:26 | 000,546,744 | ---- | M] () -- C:\WINDOWS\System32\FNTCACHE.DAT
[2013/01/07 03:08:38 | 000,000,550 | ---- | M] () -- C:\WINDOWS\System32\reimage.rep
[2013/01/07 03:08:33 | 000,000,734 | ---- | M] () -- C:\WINDOWS\System32\drivers\ETC\hosts.bak
[2013/01/07 03:00:42 | 000,000,179 | ---- | M] () -- C:\WINDOWS\reimage.ini
[2013/01/07 02:38:34 | 000,009,216 | ---- | M] () -- C:\WINDOWS\System32\Native.exe
[2013/01/06 23:58:48 | 000,001,749 | ---- | M] () -- C:\Documents and Settings\All Users\Desktop\PC Scan & Repair by Reimage.lnk
[2013/01/06 23:09:49 | 000,001,945 | ---- | M] () -- C:\WINDOWS\epplauncher.mif
[2013/01/06 21:48:20 | 000,012,872 | ---- | M] (SurfRight B.V.) -- C:\WINDOWS\System32\bootdelete.exe
[2013/01/06 21:33:42 | 000,001,610 | ---- | M] () -- C:\Documents and Settings\All Users\Desktop\HitmanPro.lnk
[2013/01/06 20:29:19 | 000,000,327 | RHS- | M] () -- C:\BOOT.INI
[2013/01/03 01:58:22 | 000,000,784 | ---- | M] () -- C:\Documents and Settings\All Users\Desktop\Malwarebytes.lnk
[2012/12/21 02:04:30 | 000,000,211 | ---- | M] () -- C:\Boot.bak
[2012/12/16 15:06:03 | 000,444,870 | R--- | M] () -- C:\WINDOWS\System32\drivers\ETC\hosts.old
[2012/12/14 16:49:28 | 000,021,104 | ---- | M] (Malwarebytes Corporation) -- C:\WINDOWS\System32\drivers\mbam.sys
[2012/12/13 12:59:44 | 000,027,584 | ---- | M] () -- C:\Documents and Settings\David\Desktop\kissing-the-face-of-god-pewter-frame.jpg
[2012/12/13 05:28:40 | 000,002,359 | ---- | M] () -- C:\Documents and Settings\David\Desktop\Notepad.lnk
========== Files Created - No Company Name ==========
[2013/01/10 21:08:24 | 001,872,454 | ---- | C] () -- C:\Documents and Settings\David\Desktop\mockup.bmp
[2013/01/10 16:24:27 | 000,000,512 | ---- | C] () -- C:\Documents and Settings\David\Desktop\MBR.dat
[2013/01/10 04:28:06 | 000,256,000 | ---- | C] () -- C:\WINDOWS\PEV.exe
[2013/01/10 04:28:06 | 000,208,896 | ---- | C] () -- C:\WINDOWS\MBR.exe
[2013/01/10 04:28:06 | 000,098,816 | ---- | C] () -- C:\WINDOWS\sed.exe
[2013/01/10 04:28:06 | 000,080,412 | ---- | C] () -- C:\WINDOWS\grep.exe
[2013/01/10 04:28:06 | 000,068,096 | ---- | C] () -- C:\WINDOWS\zip.exe
[2013/01/09 20:59:34 | 2146,508,800 | -HS- | C] () -- C:\hiberfil.sys
[2013/01/09 18:05:10 | 003,293,002 | ---- | C] () -- C:\Documents and Settings\David\Desktop\tweaking.com_windows_repair_aio.zip
[2013/01/09 16:42:53 | 000,000,664 | ---- | C] () -- C:\WINDOWS\System32\d3d9caps.dat
[2013/01/08 20:04:37 | 013,485,902 | ---- | C] () -- C:\Documents and Settings\David\Desktop\mbar-1.01.0.1011.zip
[2013/01/07 03:08:33 | 000,000,550 | ---- | C] () -- C:\WINDOWS\System32\reimage.rep
[2013/01/07 03:03:18 | 000,001,992 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\MSN.lnk
[2013/01/07 03:03:18 | 000,001,605 | ---- | C] () -- C:\Documents and Settings\David\Start Menu\Programs\Remote Assistance.lnk
[2013/01/07 03:03:18 | 000,000,792 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\Windows Movie Maker.lnk
[2013/01/07 03:03:18 | 000,000,744 | ---- | C] () -- C:\Documents and Settings\David\Start Menu\Programs\Outlook Express.lnk
[2013/01/07 02:38:34 | 000,009,216 | ---- | C] () -- C:\WINDOWS\System32\Native.exe
[2013/01/06 23:58:49 | 000,000,179 | ---- | C] () -- C:\WINDOWS\reimage.ini
[2013/01/06 23:58:48 | 000,001,749 | ---- | C] () -- C:\Documents and Settings\All Users\Desktop\PC Scan & Repair by Reimage.lnk
[2013/01/06 23:19:42 | 000,000,384 | -H-- | C] () -- C:\WINDOWS\tasks\Microsoft Antimalware Scheduled Scan.job
[2013/01/06 23:09:43 | 000,001,698 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\Microsoft Security Essentials.lnk
[2013/01/06 21:33:42 | 000,001,610 | ---- | C] () -- C:\Documents and Settings\All Users\Desktop\HitmanPro.lnk
[2013/01/06 20:29:19 | 000,000,211 | ---- | C] () -- C:\Boot.bak
[2013/01/06 20:29:16 | 000,260,272 | RHS- | C] () -- C:\cmldr
[2012/12/13 12:59:44 | 000,027,584 | ---- | C] () -- C:\Documents and Settings\David\Desktop\kissing-the-face-of-god-pewter-frame.jpg
[2012/04/26 16:50:30 | 000,178,257 | ---- | C] () -- C:\Documents and Settings\David\Local Settings\Application Data\census.cache
[2012/04/26 16:50:28 | 000,199,016 | ---- | C] () -- C:\Documents and Settings\David\Local Settings\Application Data\ars.cache
[2012/04/26 16:31:27 | 000,000,036 | ---- | C] () -- C:\Documents and Settings\David\Local Settings\Application Data\housecall.guid.cache
[2012/02/16 11:52:51 | 000,003,072 | ---- | C] () -- C:\WINDOWS\System32\iacenc.dll
[2012/02/07 11:59:20 | 000,000,000 | ---- | C] () -- C:\WINDOWS\RussSqr.INI
[2012/01/18 12:24:32 | 000,107,280 | ---- | C] () -- C:\WINDOWS\System32\zlib1.dll
[2012/01/02 02:49:08 | 000,175,616 | ---- | C] () -- C:\WINDOWS\System32\unrar.dll
[2011/03/22 16:31:14 | 000,000,000 | ---- | C] () -- C:\WINDOWS\nsreg.dat
[2010/01/28 01:02:42 | 000,003,072 | ---- | C] () -- C:\Documents and Settings\David\Cache.db
[2009/10/03 11:04:19 | 000,008,627 | ---- | C] () -- C:\Documents and Settings\David\PAV_FOG.OPC
[2005/09/06 15:49:09 | 000,000,000 | ---- | C] () -- C:\Documents and Settings\David\WebProxy.ini
[2004/02/03 11:27:42 | 000,017,920 | ---- | C] () -- C:\Documents and Settings\David\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
========== ZeroAccess Check ==========
[2009/05/31 18:59:08 | 000,000,227 | RHS- | M] () -- C:\WINDOWS\assembly\Desktop.ini
[HKEY_CURRENT_USER\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32]
[HKEY_CURRENT_USER\Software\Classes\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}\InProcServer32]
[HKEY_LOCAL_MACHINE\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32]
"" = %SystemRoot%\system32\shdocvw.dll -- [2008/04/13 19:12:05 | 001,499,136 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Apartment
[HKEY_LOCAL_MACHINE\Software\Classes\clsid\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InProcServer32]
"" = %systemroot%\system32\wbem\fastprox.dll -- [2009/02/09 07:10:48 | 000,473,600 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Free
[HKEY_LOCAL_MACHINE\Software\Classes\clsid\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InProcServer32]
"" = %systemroot%\system32\wbem\wbemess.dll -- [2008/04/13 19:12:08 | 000,273,920 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Both
========== LOP Check ==========
[2013/01/06 17:57:34 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\01014CE1ACC253E7000001014BE457DE
[2008/01/28 11:52:18 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Backup
[2013/01/06 21:38:43 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\HitmanPro
[2012/12/06 17:13:31 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Internet Content Filter
[2008/01/28 11:54:58 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\sentinel
[2012/09/26 18:55:11 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\TuneUp Software
[2012/09/26 18:53:58 | 000,000,000 | -HSD | M] -- C:\Documents and Settings\All Users\Application Data\{32364CEA-7855-4A3C-B674-53D8E9B97936}
[2011/11/24 03:00:21 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\Desktop Maestro
[2013/01/07 03:33:25 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\ElevatedDiagnostics
[2011/04/14 08:03:57 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\Neuratron
[2006/07/07 18:35:01 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\OurPictures
[2004/03/23 21:52:52 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\The Labyrinth Plus! Edition
[2012/09/26 18:54:27 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\TuneUp Software
[2012/09/25 19:25:42 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\Windows Desktop Search
[2012/09/28 07:51:45 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\Windows Search
========== Purity Check ==========
< End of report >
(3)
Below is the result of the run fix scan with the inserted code:
All processes killed
========== OTL ==========
Unable to delete ADS C:\Documents and Settings\All Users\Application Data\TEMP:0D786AE3 .
========== FILES ==========
< ipconfig /flushdns /c >
Windows IP Configuration
Successfully flushed the DNS Resolver Cache.
C:\Documents and Settings\David\Desktop\cmd.bat deleted successfully.
C:\Documents and Settings\David\Desktop\cmd.txt deleted successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: Administrator
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: All Users
User: David
->Temp folder emptied: 78174255 bytes
->Temporary Internet Files folder emptied: 6488577 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 9075230 bytes
->Google Chrome cache emptied: 0 bytes
->Flash cache emptied: 506 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: LocalService
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 32902 bytes
User: NetworkService
->Temp folder emptied: 6434 bytes
->Temporary Internet Files folder emptied: 33170 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32\dllcache .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 5519 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temp folder emptied: 0 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temporary Internet Files folder emptied: 0 bytes
RecycleBin emptied: 204926 bytes
Total Files Cleaned = 90.00 mb
C:\WINDOWS\System32\drivers\etc\Hosts moved successfully.
HOSTS file reset successfully
OTL by OldTimer - Version 3.2.69.0 log created on 01112013_000738
Files\Folders moved on Reboot...
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
(4)
I was able to run HitManPro without any ill effects. When I had run the scan a couple of days ago, it came up with BOM in the HOSTS FILE. I tried a couple of times to delete it, but the scan crashed at 98% in regular and in safe mode with networking. When I ran the scan again in Safe Mode w/networking, I went ahead and clicked the button which reset the hosts file link and the BOM no longer showed up but the scan would still crash at 98%. Today, after doing the few changes you requested, the scan works perfectly with no bad effects!
aswMBR version 0.9.9.1707 Copyright(c) 2011 AVAST Software
Run date: 2013-01-10 15:44:45
-----------------------------
15:44:45.265 OS Version: Windows 5.1.2600 Service Pack 3
15:44:45.265 Number of processors: 1 586 0x205
15:44:45.265 ComputerName: YADDLE UserName: David
15:44:45.921 Initialize success
15:55:00.718 AVAST engine defs: 13011000
15:56:46.906 Disk 0 (boot) \Device\Harddisk0\DR0 -> \Device\Scsi\symmpi1Port1Path0Target0Lun0
15:56:46.906 Disk 0 Vendor: SEAGATE_ DX10 Size: 70007MB BusType: 1
15:56:46.906 Disk 0 MBR read successfully
15:56:46.906 Disk 0 MBR scan
15:56:46.937 Disk 0 Windows XP default MBR code
15:56:46.937 Disk 0 Partition 1 00 DE Dell Utility Dell 4.1 39 MB offset 63
15:56:46.968 Disk 0 Partition 2 80 (A) 07 HPFS/NTFS NTFS 69962 MB offset 80325
15:56:46.984 Disk 0 scanning sectors +143364060
15:56:47.031 Disk 0 scanning C:\WINDOWS\system32\drivers
15:57:19.390 Service scanning
15:58:10.921 Modules scanning
15:58:19.078 Disk 0 trace - called modules:
15:58:19.093 ntoskrnl.exe CLASSPNP.SYS disk.sys SCSIPORT.SYS hal.dll symmpi.sys
15:58:19.093 1 nt!IofCallDriver -> \Device\Harddisk0\DR0[0x8ad19ab8]
15:58:19.093 3 CLASSPNP.SYS[f7657fd7] -> nt!IofCallDriver -> \Device\Scsi\symmpi1Port1Path0Target0Lun0[0x8acdc030]
15:58:19.500 AVAST engine scan C:\WINDOWS
15:58:44.328 AVAST engine scan C:\WINDOWS\system32
16:04:21.578 AVAST engine scan C:\WINDOWS\system32\drivers
16:05:00.531 AVAST engine scan C:\Documents and Settings\David
16:12:07.125 AVAST engine scan C:\Documents and Settings\All Users
16:12:50.625 Scan finished successfully
16:24:27.937 Disk 0 MBR has been saved successfully to "C:\Documents and Settings\David\Desktop\MBR.dat"
16:24:27.953 The log file has been saved successfully to "C:\Documents and Settings\David\Desktop\aswMBR.txt"
Below is the OTL log I created with your original instructions by scanning all users clicking on LOP check and Purity Check, etc.
(2)
OTL logfile created on: 1/11/2013 12:01:57 AM - Run 3
OTL by OldTimer - Version 3.2.69.0 Folder = C:\Documents and Settings\David\Desktop
Windows XP Professional Edition Service Pack 3 (Version = 5.1.2600) - Type = NTWorkstation
Internet Explorer (Version = 8.0.6001.18702)
Locale: 00000409 | Country: United States | Language: ENU | Date Format: M/d/yyyy
2.00 Gb Total Physical Memory | 1.40 Gb Available Physical Memory | 70.11% Memory free
3.85 Gb Paging File | 3.44 Gb Available in Paging File | 89.30% Paging File free
Paging file location(s): C:\pagefile.sys 0 0 [binary data]
%SystemDrive% = C: | %SystemRoot% = C:\WINDOWS | %ProgramFiles% = C:\Program Files
Drive C: | 68.32 Gb Total Space | 44.54 Gb Free Space | 65.20% Space Free | Partition Type: NTFS
Computer Name: YADDLE | User Name: David | Logged in as Administrator.
Boot Mode: Normal | Scan Mode: All users | Quick Scan
Company Name Whitelist: On | Skip Microsoft Files: On | No Company Name Whitelist: On | File Age = 30 Days
========== Processes (SafeList) ==========
PRC - [2013/01/10 23:57:35 | 000,917,552 | ---- | M] (Mozilla Corporation) -- C:\Program Files\Mozilla Firefox\firefox.exe
PRC - [2013/01/07 19:38:05 | 000,602,112 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\David\Desktop\OTL.exe
PRC - [2012/12/14 16:49:28 | 000,398,184 | ---- | M] (Malwarebytes Corporation) -- C:\Program Files\Malwarebytes' Anti-Malware\mbamscheduler.exe
PRC - [2012/11/28 17:04:52 | 001,695,816 | ---- | M] (InternetSafety.com, Inc.) -- C:\Program Files\Internet Content Filter\UpdateService.exe
PRC - [2012/11/28 17:03:46 | 003,267,072 | ---- | M] (InternetSafety.com, Inc.) -- C:\Program Files\Internet Content Filter\SafeEyes.exe
PRC - [2012/09/12 17:25:22 | 000,020,472 | ---- | M] (Microsoft Corporation) -- c:\Program Files\Microsoft Security Client\MsMpEng.exe
PRC - [2012/09/12 17:19:44 | 000,947,176 | ---- | M] (Microsoft Corporation) -- C:\Program Files\Microsoft Security Client\msseces.exe
PRC - [2010/10/28 19:02:02 | 000,056,952 | ---- | M] (Ipswitch) -- C:\Program Files\Ipswitch\WS_FTP 12\WsftpCOMHelper.exe
PRC - [2009/11/11 10:21:38 | 000,583,640 | ---- | M] (PC Tools) -- C:\Program Files\Common Files\PC Tools\sMonitor\StartManSvc.exe
PRC - [2008/04/13 19:12:19 | 001,033,728 | ---- | M] (Microsoft Corporation) -- C:\WINDOWS\explorer.exe
PRC - [2004/03/11 23:00:30 | 000,135,168 | ---- | M] (Dell Inc.) -- c:\Program Files\Dell Printers\Additional Color Laser Software\Status Monitor\dlsdbnt.exe
PRC - [2004/03/11 23:00:30 | 000,090,112 | ---- | M] (Dell Inc.) -- c:\Program Files\Dell Printers\Additional Color Laser Software\Status Monitor\dlpwdnt.exe
PRC - [2003/12/11 11:30:00 | 000,049,152 | ---- | M] (ATI Technologies, Inc.) -- C:\Program Files\ATI Technologies\Fire GL Control Panel\atiisrgl.exe
PRC - [2002/08/07 06:34:26 | 000,221,184 | ---- | M] (Intel Corporation) -- C:\Program Files\intel\ASF Agent\ASFAgent.exe
========== Modules (No Company Name) ==========
MOD - [2013/01/10 23:56:01 | 003,021,872 | ---- | M] () -- C:\Program Files\Mozilla Firefox\mozjs.dll
MOD - [2012/02/17 19:55:35 | 000,166,912 | ---- | M] () -- C:\Program Files\WinRAR\RarExt.dll
MOD - [2010/10/28 18:55:42 | 006,551,672 | ---- | M] () -- C:\Program Files\Ipswitch\WS_FTP 12\res0409.dll
MOD - [2010/10/28 18:52:36 | 000,948,496 | ---- | M] () -- C:\Program Files\Ipswitch\WS_FTP 12\libeay32.dll
MOD - [2010/10/28 18:52:36 | 000,153,360 | ---- | M] () -- C:\Program Files\Ipswitch\WS_FTP 12\ssleay32.dll
MOD - [2008/04/13 19:11:59 | 000,014,336 | ---- | M] () -- C:\WINDOWS\SYSTEM32\msdmo.dll
========== Services (SafeList) ==========
SRV - File not found [Disabled | Stopped] -- %SystemRoot%\System32\hidserv.dll -- (HidServ)
SRV - [2013/01/10 23:57:34 | 000,115,760 | ---- | M] (Mozilla Foundation) [On_Demand | Stopped] -- C:\Program Files\Mozilla Maintenance Service\maintenanceservice.exe -- (MozillaMaintenance)
SRV - [2013/01/09 12:50:52 | 000,251,400 | ---- | M] (Adobe Systems Incorporated) [On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\Macromed\Flash\FlashPlayerUpdateService.exe -- (AdobeFlashPlayerUpdateSvc)
SRV - [2012/12/14 16:49:28 | 000,682,344 | ---- | M] (Malwarebytes Corporation) [Auto | Stopped] -- C:\Program Files\Malwarebytes' Anti-Malware\mbamservice.exe -- (MBAMService)
SRV - [2012/12/14 16:49:28 | 000,398,184 | ---- | M] (Malwarebytes Corporation) [Auto | Running] -- C:\Program Files\Malwarebytes' Anti-Malware\mbamscheduler.exe -- (MBAMScheduler)
SRV - [2012/11/28 17:04:52 | 001,695,816 | ---- | M] (InternetSafety.com, Inc.) [Auto | Running] -- C:\Program Files\Internet Content Filter\UpdateService.exe -- (seUpdateSvc)
SRV - [2012/11/28 17:04:52 | 001,695,816 | ---- | M] (InternetSafety.com, Inc.) [Auto | Running] -- C:\Program Files\Internet Content Filter\UpdateService.exe -- (mfeicfupdate)
SRV - [2012/09/12 17:25:22 | 000,020,472 | ---- | M] (Microsoft Corporation) [Auto | Running] -- c:\Program Files\Microsoft Security Client\MsMpEng.exe -- (MsMpSvc)
SRV - [2009/11/11 10:21:38 | 000,583,640 | ---- | M] (PC Tools) [Auto | Running] -- C:\Program Files\Common Files\PC Tools\sMonitor\StartManSvc.exe -- (PCToolsSSDMonitorSvc)
SRV - [2004/10/15 09:12:38 | 000,131,072 | ---- | M] (SonicWALL, Inc.) [On_Demand | Stopped] -- C:\Program Files\SonicWALL\SonicWALL Global VPN Client\RampartSvc.exe -- (RampartSvc)
SRV - [2004/03/11 23:00:30 | 000,135,168 | ---- | M] (Dell Inc.) [Auto | Running] -- c:\Program Files\Dell Printers\Additional Color Laser Software\Status Monitor\dlsdbnt.exe -- (DLSDB)
SRV - [2004/03/11 23:00:30 | 000,090,112 | ---- | M] (Dell Inc.) [Auto | Running] -- c:\Program Files\Dell Printers\Additional Color Laser Software\Status Monitor\dlpwdnt.exe -- (DLPWD)
SRV - [2003/12/11 11:30:00 | 000,049,152 | ---- | M] (ATI Technologies, Inc.) [Auto | Running] -- C:\Program Files\ATI Technologies\Fire GL Control Panel\atiisrgl.exe -- (FGLRYUtil)
SRV - [2002/08/07 06:34:26 | 000,221,184 | ---- | M] (Intel Corporation) [Auto | Running] -- C:\Program Files\intel\ASF Agent\ASFAgent.exe -- (ASFAgent)
SRV - [2002/07/30 17:15:24 | 001,118,208 | ---- | M] (Intel Corporation) [On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\NMSSvc.Exe -- (NMSSvc)
========== Driver Services (SafeList) ==========
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (WDICA)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\RkPavproc3.sys -- (RkPavproc3)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\RkPavproc2.sys -- (RkPavproc2)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\WINDOWS\system32\drivers\RkPavproc1.sys -- (RkPavproc1)
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (PDRFRAME)
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (PDRELI)
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (PDFRAME)
DRV - File not found [Kernel | On_Demand | Stopped] -- -- (PDCOMP)
DRV - File not found [Kernel | System | Stopped] -- -- (PCIDump)
DRV - File not found [Kernel | System | Stopped] -- -- (lbrtfdc)
DRV - File not found [Kernel | On_Demand | Stopped] -- System32\DRIVERS\wATV03nt.sys -- (iAimTV2)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\DOCUME~1\David\LOCALS~1\Temp\cpuz134\cpuz134_x32.sys -- (cpuz134)
DRV - File not found [Kernel | System | Stopped] -- -- (Changer)
DRV - File not found [Kernel | On_Demand | Stopped] -- C:\DOCUME~1\David\LOCALS~1\Temp\catchme.sys -- (catchme)
DRV - File not found [Kernel | On_Demand | Stopped] -- System32\Drivers\BW2NDIS5.sys -- (BW2NDIS5)
DRV - File not found [Kernel | On_Demand | Unknown] -- C:\DOCUME~1\David\LOCALS~1\Temp\aswMBR.sys -- (aswMBR)
DRV - [2013/01/10 16:27:41 | 000,029,904 | ---- | M] (Microsoft Corporation) [Kernel | System | Running] -- c:\Documents and Settings\All Users\Application Data\Microsoft\Microsoft Antimalware\Definition Updates\{03E6FF9C-C04C-418D-B466-32F75BC457F4}\MpKsl571993da.sys -- (MpKsl571993da)
DRV - [2013/01/07 00:17:16 | 000,017,904 | ---- | M] (Emsi Software GmbH) [Kernel | System | Running] -- C:\Documents and Settings\David\Desktop\fffu\EmsisoftEmergencyKit\Run\a2ddax86.sys -- (A2DDA)
DRV - [2012/12/14 16:49:28 | 000,021,104 | ---- | M] (Malwarebytes Corporation) [File_System | On_Demand | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\mbam.sys -- (MBAMProtector)
DRV - [2010/11/09 13:56:12 | 000,098,392 | ---- | M] (Sunbelt Software) [Kernel | System | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\SBREDrv.sys -- (SBRE)
DRV - [2008/04/13 13:40:51 | 000,008,320 | ---- | M] (Microsoft Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\dlttape.sys -- (dlttape)
DRV - [2008/01/26 06:50:20 | 000,194,320 | ---- | M] (Kaspersky Lab) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\klif.sys -- (KLIF)
DRV - [2004/10/15 09:46:12 | 000,091,136 | ---- | M] (SonicWALL, Inc.) [Kernel | System | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\RCFOX.SYS -- (RCFOX)
DRV - [2004/08/04 00:29:49 | 000,019,455 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wvchntxx.sys -- (iAimFP4)
DRV - [2004/08/04 00:29:47 | 000,012,063 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wsiintxx.sys -- (iAimFP3)
DRV - [2004/08/04 00:29:45 | 000,023,615 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wch7xxnt.sys -- (iAimTV4)
DRV - [2004/08/04 00:29:43 | 000,033,599 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\watv04nt.sys -- (iAimTV3)
DRV - [2004/08/04 00:29:42 | 000,019,551 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\watv02nt.sys -- (iAimTV1)
DRV - [2004/08/04 00:29:41 | 000,029,311 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\watv01nt.sys -- (iAimTV0)
DRV - [2004/08/04 00:29:37 | 000,012,415 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wadv01nt.sys -- (iAimFP0)
DRV - [2004/08/04 00:29:37 | 000,012,127 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wadv02nt.sys -- (iAimFP1)
DRV - [2004/08/04 00:29:37 | 000,011,775 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\wadv05nt.sys -- (iAimFP2)
DRV - [2004/08/04 00:29:36 | 000,161,020 | ---- | M] (Intel(R) Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\i81xnt5.sys -- (i81x)
DRV - [2004/05/14 16:15:22 | 000,147,236 | ---- | M] (Deterministic Networks, Inc.) [Kernel | On_Demand | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\dne2000.sys -- (DNE)
DRV - [2004/01/22 01:54:23 | 000,206,464 | ---- | M] (Roxio) [File_System | System | Running] -- C:\WINDOWS\System32\drivers\udfreadr_xp.sys -- (UdfReadr_xp)
DRV - [2004/01/22 01:54:23 | 000,143,834 | ---- | M] (Roxio) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\pwd_2K.sys -- (pwd_2k)
DRV - [2004/01/22 01:54:23 | 000,030,630 | ---- | M] (Roxio) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\System32\drivers\Mmc_2k.sys -- (mmc_2K)
DRV - [2004/01/22 01:54:23 | 000,025,898 | ---- | M] (Roxio) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\System32\drivers\Dvd_2k.sys -- (dvd_2K)
DRV - [2003/12/11 08:56:40 | 000,630,272 | ---- | M] (ATI Technologies Inc.) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ati2mtag.sys -- (ati2mtag)
DRV - [2003/11/20 12:03:06 | 000,009,728 | ---- | M] (Quantum Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\QntmDLT.sys -- (QntmDLT)
DRV - [2003/08/20 13:01:22 | 000,023,180 | ---- | M] (SonicWALL, Inc.) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\rcvpn.sys -- (rcvpn)
DRV - [2003/03/27 11:58:56 | 000,287,920 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctdvda2k.sys -- (ctdvda2k)
DRV - [2003/03/26 16:33:58 | 000,498,688 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctaud2k.sys -- (ctaud2k)
DRV - [2003/03/26 16:32:32 | 000,189,504 | ---- | M] (Creative Technology Ltd.) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctoss2k.sys -- (ossrv)
DRV - [2003/03/26 16:32:02 | 000,141,536 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\hap16v2k.sys -- (hap16v2k)
DRV - [2003/03/26 16:31:40 | 000,823,616 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ha10kx2k.sys -- (ha10kx2k)
DRV - [2003/03/06 10:10:34 | 000,015,840 | ---- | M] (Creative Technology Ltd.) [Kernel | Auto | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\pfmodnt.sys -- (PfModNT)
DRV - [2003/02/20 17:24:46 | 000,116,000 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\emupia2k.sys -- (emupia)
DRV - [2003/02/20 17:24:34 | 000,135,248 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctsfm2k.sys -- (ctsfm2k)
DRV - [2003/02/20 17:24:18 | 000,006,144 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctprxy2k.sys -- (ctprxy2k)
DRV - [2003/02/20 17:22:38 | 000,135,040 | ---- | M] (Creative Technology Ltd) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\ctac32k.sys -- (ctac32k)
DRV - [2002/12/17 13:32:58 | 000,061,424 | ---- | M] (Roxio) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\cdr4_xp.sys -- (Cdr4_xp)
DRV - [2002/12/17 13:32:46 | 000,023,436 | ---- | M] (Roxio) [Kernel | System | Running] -- C:\WINDOWS\System32\drivers\cdralw2k.sys -- (Cdralw2k)
DRV - [2002/12/17 13:27:32 | 000,241,152 | ---- | M] (Roxio) [File_System | System | Running] -- C:\WINDOWS\System32\drivers\cdudf_xp.sys -- (cdudf_xp)
DRV - [2002/11/08 14:45:06 | 000,017,217 | ---- | M] (Dell Computer Corporation) [Kernel | System | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\omci.sys -- (omci)
DRV - [2002/08/29 14:29:12 | 000,036,096 | ---- | M] (LSI Logic) [Kernel | Boot | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\SYMMPI.SYS -- (symmpi)
DRV - [2002/07/30 17:15:40 | 000,009,868 | ---- | M] (Intel Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\NMSCFG.SYS -- (NMSCFG)
DRV - [2002/05/07 17:06:36 | 000,023,744 | ---- | M] (Intel Corporation) [Kernel | Auto | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\platalrt.sys -- (PlatAlrt)
DRV - [2002/05/07 17:05:56 | 000,039,680 | ---- | M] (Intel Corporation) [Kernel | Auto | Running] -- C:\WINDOWS\SYSTEM32\DRIVERS\Netalrt.sys -- (NetAlrt)
DRV - [2001/08/17 13:11:06 | 000,066,591 | ---- | M] (3Com Corporation) [Kernel | On_Demand | Stopped] -- C:\WINDOWS\SYSTEM32\DRIVERS\EL90XBC5.SYS -- (EL90XBC)
========== Standard Registry (SafeList) ==========
========== Internet Explorer ==========
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Search,Default_Search_URL = http://www.google.com/ie
IE - HKLM\..\SearchScopes,DefaultScope =
IE - HKLM\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" = http://search.live.com/results.aspx?q={searchTerms}&src={referrer:source?}
IE - HKU\.DEFAULT\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.dell.com
IE - HKU\.DEFAULT\SOFTWARE\Microsoft\Internet Explorer\Main,First Home Page = http://www.dell.com
IE - HKU\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-18\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.dell.com
IE - HKU\S-1-5-18\SOFTWARE\Microsoft\Internet Explorer\Main,First Home Page = http://www.dell.com
IE - HKU\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-19\..\SearchScopes,DefaultScope =
IE - HKU\S-1-5-19\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-20\..\SearchScopes,DefaultScope =
IE - HKU\S-1-5-20\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Search_URL = http://www.earthlink.net/partner/more/msie/button/search.html
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.google.com/
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Internet Explorer\Search,SearchAssistant = http://www.google.com/ie
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\SearchScopes,DefaultScope = {C1046C13-D6E3-4AA1-ADF6-319BB623E49D}
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" = http://www.bing.com/search?q={searchTerms}&src=IE-SearchBox&FORM=IE8SRC
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\SearchScopes\{C1046C13-D6E3-4AA1-ADF6-319BB623E49D}: "URL" = http://www.google.com/search?q={searchTerms}&sourceid=ie7&rls=com.microsoft:en-US&ie=utf8&oe=utf8
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-500\SOFTWARE\Microsoft\Internet Explorer\Main,Default_Page_URL = http://www.dell.com
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-500\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.dell.com
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-500\..\SearchScopes,DefaultScope = {0633EE93-D776-472f-A0FF-E1416B8B2E3A}
IE - HKU\S-1-5-21-989678199-2234712002-1868543911-500\Software\Microsoft\Windows\CurrentVersion\Internet Settings: "ProxyEnable" = 0
========== FireFox ==========
FF - prefs.js..browser.search.defaultenginename: ""
FF - prefs.js..browser.search.order.1: ""
FF - prefs.js..browser.search.selectedEngine: "Google"
FF - prefs.js..browser.startup.homepage: "http://www.christcenteredmall.com/stores/art/"
FF - prefs.js..extensions.enabledAddons: %7B972ce4c6-7e08-4474-a285-3208198ce6fd%7D:18.0
FF - prefs.js..network.proxy.type: 0
FF - user.js - File not found
FF - HKLM\Software\MozillaPlugins\@adobe.com/FlashPlayer: C:\WINDOWS\system32\Macromed\Flash\NPSWF32_11_5_502_146.dll ()
FF - HKLM\Software\MozillaPlugins\@Microsoft.com/NpCtrl,version=1.0: c:\Program Files\Microsoft Silverlight\4.1.10329.0\npctrl.dll ( Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@microsoft.com/WPF,version=3.5: c:\WINDOWS\Microsoft.NET\Framework\v3.5\Windows Presentation Foundation\NPWPF.dll (Microsoft Corporation)
FF - HKLM\Software\MozillaPlugins\@real.com/nppl3260;version=15.0.6.14: C:\Program Files\Real\RealPlayer\Netscape6\nppl3260.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprjplug;version=15.0.6.14: C:\Program Files\Real\RealPlayer\Netscape6\nprjplug.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprpchromebrowserrecordext;version=15.0.6.14: C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprpchromebrowserrecordext.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprphtml5videoshim;version=15.0.6.14: C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprphtml5videoshim.dll (RealNetworks, Inc.)
FF - HKLM\Software\MozillaPlugins\@real.com/nprpplugin;version=15.0.6.14: C:\Program Files\Real\RealPlayer\Netscape6\nprpplugin.dll (RealPlayer)
FF - HKLM\Software\MozillaPlugins\@tools.google.com/Google Update;version=3: C:\Program Files\Google\Update\1.3.21.124\npGoogleUpdate3.dll (Google Inc.)
FF - HKLM\Software\MozillaPlugins\@tools.google.com/Google Update;version=9: C:\Program Files\Google\Update\1.3.21.124\npGoogleUpdate3.dll (Google Inc.)
FF - HKLM\Software\MozillaPlugins\@videolan.org/vlc,version=2.0.3: C:\Program Files\VideoLAN\VLC\npvlc.dll (VideoLAN)
FF - HKLM\Software\MozillaPlugins\Adobe Reader: C:\Program Files\Adobe\Reader 10.0\Reader\AIR\nppdf32.dll (Adobe Systems Inc.)
FF - HKEY_LOCAL_MACHINE\software\mozilla\Firefox\Extensions\\{0153E448-190B-4987-BDE1-F256CADA672F}: C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\Firefox\Ext [2012/09/14 22:42:51 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 18.0\extensions\\Components: C:\Program Files\Mozilla Firefox\components [2013/01/10 23:57:36 | 000,000,000 | ---D | M]
FF - HKEY_LOCAL_MACHINE\software\mozilla\Mozilla Firefox 18.0\extensions\\Plugins: C:\Program Files\Mozilla Firefox\plugins
[2011/03/22 16:31:40 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\David\Application Data\Mozilla\Extensions
[2012/12/15 15:34:25 | 000,000,000 | ---D | M] (No name found) -- C:\Documents and Settings\David\Application Data\Mozilla\Firefox\Profiles\ch1ntccj.default\extensions
[2012/12/15 15:34:25 | 000,804,627 | ---- | M] () (No name found) -- C:\Documents and Settings\David\Application Data\Mozilla\Firefox\Profiles\ch1ntccj.default\extensions\{d10d0bf8-f5b5-c8b4-a8b2-2b9879e08c5d}.xpi
[2013/01/10 23:55:35 | 000,000,000 | ---D | M] (No name found) -- C:\Program Files\Mozilla Firefox\extensions
[2013/01/10 23:57:36 | 000,262,704 | ---- | M] (Mozilla Foundation) -- C:\Program Files\mozilla firefox\components\browsercomps.dll
[2012/08/30 14:25:05 | 000,002,465 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\bing.xml
[2012/10/21 09:26:34 | 000,002,058 | ---- | M] () -- C:\Program Files\mozilla firefox\searchplugins\twitter.xml
========== Chrome ==========
CHR - homepage: http://www.google.com/
CHR - default_search_provider: Google (Enabled)
CHR - default_search_provider: search_url = {google:baseURL}search?q={searchTerms}&{google:RLZ}{google:acceptedSuggestion}{google
CHR - default_search_provider: suggest_url = {google:baseSuggestURL}search?{google:searchFieldtrialParameter}client=chrome&hl={language}&q={searchTerms}&sugkey={google:suggestAPIKeyParameter}
CHR - homepage: http://www.google.com/
CHR - plugin: Shockwave Flash (Enabled) = C:\Program Files\Google\Chrome\Application\23.0.1271.97\PepperFlash\pepflashplayer.dll
CHR - plugin: Shockwave Flash (Enabled) = C:\WINDOWS\system32\Macromed\Flash\NPSWF32_11_4_402_287.dll
CHR - plugin: Chrome Remote Desktop Viewer (Enabled) = internal-remoting-viewer
CHR - plugin: Native Client (Enabled) = C:\Program Files\Google\Chrome\Application\23.0.1271.97\ppGoogleNaClPluginChrome.dll
CHR - plugin: Chrome PDF Viewer (Enabled) = C:\Program Files\Google\Chrome\Application\23.0.1271.97\pdf.dll
CHR - plugin: Adobe Acrobat (Enabled) = C:\Program Files\Adobe\Reader 10.0\Reader\Browser\nppdf32.dll
CHR - plugin: Microsoft\u00AE DRM (Enabled) = C:\Program Files\Windows Media Player\npdrmv2.dll
CHR - plugin: Microsoft\u00AE DRM (Enabled) = C:\Program Files\Windows Media Player\npwmsdrm.dll
CHR - plugin: Windows Media Player Plug-in Dynamic Link Library (Enabled) = C:\Program Files\Windows Media Player\npdsplay.dll
CHR - plugin: RealNetworks(tm) Chrome Background Extension Plug-In (32-bit) (Enabled) = C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprpchromebrowserrecordext.dll
CHR - plugin: RealPlayer(tm) HTML5VideoShim Plug-In (32-bit) (Enabled) = C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\MozillaPlugins\nprphtml5videoshim.dll
CHR - plugin: RealPlayer(tm) G2 LiveConnect-Enabled Plug-In (32-bit) (Enabled) = C:\Program Files\Real\RealPlayer\Netscape6\nppl3260.dll
CHR - plugin: RealPlayer Download Plugin (Enabled) = C:\Program Files\Real\RealPlayer\Netscape6\nprpplugin.dll
CHR - plugin: Google Update (Enabled) = C:\Program Files\Google\Update\1.3.21.124\npGoogleUpdate3.dll
CHR - plugin: RealJukebox NS Plugin (Enabled) = C:\Program Files\Real\RealPlayer\Netscape6\nprjplug.dll
CHR - plugin: VLC Web Plugin (Enabled) = C:\Program Files\VideoLAN\VLC\npvlc.dll
CHR - plugin: Silverlight Plug-In (Enabled) = c:\Program Files\Microsoft Silverlight\4.1.10329.0\npctrl.dll
CHR - plugin: Windows Presentation Foundation (Enabled) = c:\WINDOWS\Microsoft.NET\Framework\v3.5\Windows Presentation Foundation\NPWPF.dll
CHR - Extension: YouTube = C:\Documents and Settings\David\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\blpcfgokakmgnkcojhhkbfbldkacnbeo\4.2.5_1\
CHR - Extension: Google Search = C:\Documents and Settings\David\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\coobgpohoikkiipiblmjeljniedjpjpf\0.0.0.19_1\
CHR - Extension: RealPlayer HTML5Video Downloader Extension = C:\Documents and Settings\David\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\jfmjfhklogoienhpfnppmbcbjfjnkonk\1.5_0\
CHR - Extension: Gmail = C:\Documents and Settings\David\Local Settings\Application Data\Google\Chrome\User Data\Default\Extensions\pjkljhegncpnkpknbcohdijeoejaedia\7_1\
O1 HOSTS File: ([2013/01/09 22:43:06 | 000,000,855 | ---- | M]) - C:\WINDOWS\SYSTEM32\DRIVERS\ETC\Hosts
O1 - Hosts: 127.0.0.1 localhost
O2 - BHO: (RealPlayer Download and Record Plugin for Internet Explorer) - {3049C3E9-B461-4BC5-8870-4C09146192CA} - C:\Documents and Settings\All Users\Application Data\Real\RealPlayer\BrowserRecordPlugin\IE\rpbrowserrecordplugin.dll (RealPlayer)
O2 - BHO: (Spybot-S&D IE Protection) - {53707962-6F74-2D53-2644-206D7942484F} - C:\Program Files\Spybot - Search & Destroy\SDHelper.dll (Safer Networking Limited)
O2 - BHO: (SSVHelper Class) - {761497BB-D6F0-462C-B6EB-D4DAF1D92D43} - C:\Program Files\Java\jre1.6.0_05\bin\ssv.dll (Sun Microsystems, Inc.)
O3 - HKU\.DEFAULT\..\Toolbar\WebBrowser: (no name) - {2318C2B1-4965-11D4-9B18-009027A5CD4F} - No CLSID value found.
O3 - HKU\S-1-5-18\..\Toolbar\WebBrowser: (no name) - {2318C2B1-4965-11D4-9B18-009027A5CD4F} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\ShellBrowser: (no name) - {2318C2B1-4965-11D4-9B18-009027A5CD4F} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\ShellBrowser: (no name) - {47833539-D0C5-4125-9FA8-0819E2EAAC93} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {430DDB4F-38CC-4E91-AF33-4157334EC937} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {472734EA-242A-422B-ADF8-83D1E48CC825} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {47833539-D0C5-4125-9FA8-0819E2EAAC93} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {C7768536-96F8-4001-B1A2-90EE21279187} - No CLSID value found.
O3 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..\Toolbar\WebBrowser: (no name) - {D7F30B62-8269-41AF-9539-B2697FA7D77E} - No CLSID value found.
O4 - HKLM..\Run: [ICF] C:\Program Files\Internet Content Filter\SafeEyes.exe (InternetSafety.com, Inc.)
O4 - HKLM..\Run: [MSC] c:\Program Files\Microsoft Security Client\msseces.exe (Microsoft Corporation)
O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O6 - HKLM\Software\Policies\Microsoft\Internet Explorer\Restrictions present
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: HonorAutoRunSetting = 1
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O7 - HKU\.DEFAULT\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: CDRAutoRun = 0
O7 - HKU\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\S-1-5-18\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: CDRAutoRun = 0
O7 - HKU\S-1-5-18\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\S-1-5-19\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-19\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O7 - HKU\S-1-5-20\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-20\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 323
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveAutoRun = 67108863
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDrives = 0
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-500\Software\Policies\Microsoft\Internet Explorer\Control Panel present
O7 - HKU\S-1-5-21-989678199-2234712002-1868543911-500\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoDriveTypeAutoRun = 145
O9 - Extra 'Tools' menuitem : Sun Java Console - {08B0E5C0-4FCB-11CF-AAA5-00401C608501} - C:\Program Files\Java\jre1.6.0_05\bin\npjpi160_05.dll (Sun Microsystems, Inc.)
O9 - Extra 'Tools' menuitem : Spybot - Search & Destroy Configuration - {DFB852A3-47F8-48C4-A200-58CAB36FD2A2} - C:\Program Files\Spybot - Search & Destroy\SDHelper.dll (Safer Networking Limited)
O10 - Protocol_Catalog9\Catalog_Entries\000000000001 - %SystemRoot%\System32\mswsock.dll File not found
O10 - Protocol_Catalog9\Catalog_Entries\000000000002 - %SystemRoot%\System32\mswsock.dll File not found
O10 - Protocol_Catalog9\Catalog_Entries\000000000044 - %SystemRoot%\System32\mswsock.dll File not found
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: ([]msn in My Computer)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: cj.com ([members] https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: cj.com ([signup] https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: cj.com ([www] https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: linkshare.com ([]https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: overture.com ([secure] https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Domains: shareasale.com ([]https in Trusted sites)
O15 - HKU\S-1-5-21-989678199-2234712002-1868543911-1006\..Trusted Ranges: Range32 ([https] in Trusted sites)
O16 - DPF: {04E214E5-63AF-4236-83C6-A7ADCBF9BD02} http://housecall60.trendmicro.com/housecall/xscan60.cab (HouseCall Control)
O16 - DPF: {166B1BCA-3F9C-11CF-8075-444553540000} http://download.macromedia.com/pub/shockwave/cabs/director/sw.cab (Shockwave ActiveX Control)
O16 - DPF: {17492023-C23A-453E-A040-C7C580BBF700} http://go.microsoft.com/fwlink/?linkid=39204 (Windows Genuine Advantage Validation Tool)
O16 - DPF: {2BC66F54-93A8-11D3-BEB6-00105AA9B6AE} http://security.symantec.com/sscv6/SharedContent/vc/bin/AvSniff.cab (Symantec AntiVirus scanner)
O16 - DPF: {3E68E405-C6DE-49FF-83AE-41EE9F4C36CE} http://office.microsoft.com/officeupdate/content/opuc3.cab (Office Update Installation Engine)
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} http://www.update.microsoft.com/windowsupdate/v6/V5Controls/en/x86/client/wuweb_site.cab?1345029211828 (WUWebControl Class)
O16 - DPF: {644E432F-49D3-41A1-8DD5-E099162EEEC5} http://security.symantec.com/sscv6/SharedContent/common/bin/cabsa.cab (Symantec RuFSI Utility Class)
O16 - DPF: {6E32070A-766D-4EE6-879C-DC1FA91D2FC3} http://www.update.microsoft.com/microsoftupdate/v6/V5Controls/en/x86/client/muweb_site.cab?1348617615734 (MUWebControl Class)
O16 - DPF: {7530BFB8-7293-4D34-9923-61A11451AFC5} http://download.eset.com/special/eos/OnlineScanner.cab (Reg Error: Key error.)
O16 - DPF: {8AD9C840-044E-11D1-B3E9-00805F499D93} http://java.sun.com/update/1.6.0/jinstall-1_6_0_05-windows-i586.cab (Java Plug-in 1.6.0_05)
O16 - DPF: {A8658086-E6AC-4957-BC8E-7D54A7E8A78E} http://www.microsoft.com/security/controls/SassCln.CAB (SassCln Object)
O16 - DPF: {CAFEEFAC-0014-0002-0000-ABCDEFFEDCBA} http://java.sun.com/products/plugin/autodl/jinstall-142-windows-i586.cab (Java Plug-in 1.4.2)
O16 - DPF: {CAFEEFAC-0015-0000-0002-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_02-windows-i586.cab (Java Plug-in 1.5.0_02)
O16 - DPF: {CAFEEFAC-0015-0000-0004-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_04-windows-i586.cab (Java Plug-in 1.5.0_04)
O16 - DPF: {CAFEEFAC-0015-0000-0005-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_05-windows-i586.cab (Java Plug-in 1.5.0_05)
O16 - DPF: {CAFEEFAC-0015-0000-0006-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_06-windows-i586.cab (Java Plug-in 1.5.0_06)
O16 - DPF: {CAFEEFAC-0015-0000-0009-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_09-windows-i586.cab (Java Plug-in 1.5.0_09)
O16 - DPF: {CAFEEFAC-0015-0000-0010-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_10-windows-i586.cab (Java Plug-in 1.5.0_10)
O16 - DPF: {CAFEEFAC-0015-0000-0011-ABCDEFFEDCBA} http://java.sun.com/update/1.5.0/jinstall-1_5_0_11-windows-i586.cab (Java Plug-in 1.5.0_11)
O16 - DPF: {CAFEEFAC-0016-0000-0001-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_01-windows-i586.cab (Java Plug-in 1.6.0_01)
O16 - DPF: {CAFEEFAC-0016-0000-0002-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_02-windows-i586.cab (Java Plug-in 1.6.0_02)
O16 - DPF: {CAFEEFAC-0016-0000-0003-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_03-windows-i586.cab (Java Plug-in 1.6.0_03)
O16 - DPF: {CAFEEFAC-0016-0000-0005-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_05-windows-i586.cab (Java Plug-in 1.6.0_05)
O16 - DPF: {CAFEEFAC-FFFF-FFFF-FFFF-ABCDEFFEDCBA} http://java.sun.com/update/1.6.0/jinstall-1_6_0_05-windows-i586.cab (Java Plug-in 1.6.0_05)
O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} http://fpdownload.adobe.com/pub/shockwave/cabs/flash/swflash.cab (Shockwave Flash Object)
O16 - DPF: {E2883E8F-472F-4FB0-9522-AC9BF37916A7} http://platformdl.adobe.com/NOS/getPlusPlus/1.6/gp.cab (Reg Error: Key error.)
O16 - DPF: Microsoft XML Parser for Java file://C:\WINDOWS\Java\classes\xmldso.cab (Reg Error: Key error.)
O17 - HKLM\System\CCS\Services\Tcpip\Parameters: DhcpNameServer = 209.18.47.61 209.18.47.62
O17 - HKLM\System\CCS\Services\Tcpip\Parameters\Interfaces\{C20CC9F1-1414-49A9-9A3A-122B89C617F6}: DhcpNameServer = 209.18.47.61 209.18.47.62
O20 - HKLM Winlogon: Shell - (Explorer.exe) - C:\WINDOWS\explorer.exe (Microsoft Corporation)
O20 - HKLM Winlogon: UserInit - (C:\WINDOWS\system32\userinit.exe) - C:\WINDOWS\SYSTEM32\userinit.exe (Microsoft Corporation)
O28 - HKLM ShellExecuteHooks: {56F9679E-7826-4C84-81F3-532071A8BCC5} - C:\Program Files\Windows Desktop Search\MsnlNamespaceMgr.dll (Microsoft Corporation)
O32 - HKLM CDRom: AutoRun - 1
O32 - AutoRun File - [2002/09/03 14:36:02 | 000,000,000 | ---- | M] () - C:\AUTOEXEC.BAT -- [ NTFS ]
O34 - HKLM BootExecute: (autocheck autochk *)
O35 - HKLM\..comfile [open] -- "%1" %*
O35 - HKLM\..exefile [open] -- "%1" %*
O37 - HKLM\...com [@ = ComFile] -- "%1" %*
O37 - HKLM\...exe [@ = exefile] -- "%1" %*
O38 - SubSystems\\Windows: (ServerDll=winsrv:UserServerDllInitialization,3)
O38 - SubSystems\\Windows: (ServerDll=winsrv:ConServerDllInitialization,2)
========== Files/Folders - Created Within 30 Days ==========
[2013/01/10 23:58:36 | 000,000,000 | RH-D | C] -- C:\Documents and Settings\David\Recent
[2013/01/10 23:55:34 | 000,000,000 | ---D | C] -- C:\Program Files\Mozilla Firefox
[2013/01/10 15:41:57 | 004,732,416 | ---- | C] (AVAST Software) -- C:\Documents and Settings\David\Desktop\aswMBR.exe
[2013/01/10 04:39:05 | 000,000,000 | -HSD | C] -- C:\RECYCLER
[2013/01/10 04:37:12 | 000,000,000 | ---D | C] -- C:\WINDOWS\temp
[2013/01/10 04:28:06 | 000,518,144 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWREG.exe
[2013/01/10 04:28:06 | 000,406,528 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWSC.exe
[2013/01/10 04:28:06 | 000,212,480 | ---- | C] (SteelWerX) -- C:\WINDOWS\SWXCACLS.exe
[2013/01/10 04:28:06 | 000,060,416 | ---- | C] (NirSoft) -- C:\WINDOWS\NIRCMD.exe
[2013/01/10 04:25:09 | 000,000,000 | ---D | C] -- C:\Qoobox
[2013/01/10 04:20:32 | 005,019,950 | R--- | C] (Swearware) -- C:\Documents and Settings\David\Desktop\ComboFix.exe
[2013/01/09 21:06:20 | 000,181,064 | ---- | C] (Sysinternals) -- C:\WINDOWS\PSEXESVC.EXE
[2013/01/09 21:05:03 | 000,000,000 | ---D | C] -- C:\RegBackup
[2013/01/09 21:01:27 | 000,000,000 | ---D | C] -- C:\Tweaking.com_Windows_Repair_Logs
[2013/01/09 21:00:46 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\tweaking.com_windows_repair_aio
[2013/01/09 16:46:05 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\RK_Quarantine
[2013/01/08 20:08:29 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\mbar-1.01.0.1011
[2013/01/08 02:21:10 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\adzz
[2013/01/08 02:00:04 | 000,000,000 | ---D | C] -- C:\_OTL
[2013/01/07 19:37:44 | 000,602,112 | ---- | C] (OldTimer Tools) -- C:\Documents and Settings\David\Desktop\OTL.exe
[2013/01/07 03:33:25 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Application Data\ElevatedDiagnostics
[2013/01/07 03:32:42 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\Windows PowerShell 1.0
[2013/01/07 03:32:29 | 000,000,000 | ---D | C] -- C:\WINDOWS\System32\windowspowershell
[2013/01/07 02:38:33 | 000,000,000 | ---D | C] -- C:\ReimageUndo
[2013/01/06 23:58:42 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\Reimage Repair
[2013/01/06 23:58:39 | 000,000,000 | ---D | C] -- C:\rei
[2013/01/06 23:58:16 | 000,000,000 | ---D | C] -- C:\Program Files\Reimage
[2013/01/06 23:09:30 | 000,000,000 | ---D | C] -- C:\Program Files\Microsoft Security Client
[2013/01/06 21:38:28 | 000,012,872 | ---- | C] (SurfRight B.V.) -- C:\WINDOWS\System32\bootdelete.exe
[2013/01/06 21:33:42 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Start Menu\Programs\HitmanPro
[2013/01/06 21:33:41 | 000,000,000 | ---D | C] -- C:\Program Files\HitmanPro
[2013/01/06 21:33:11 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\HitmanPro
[2013/01/06 21:32:42 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\roigguer
[2013/01/06 20:29:15 | 000,000,000 | RHSD | C] -- C:\cmdcons
[2013/01/06 20:27:30 | 000,000,000 | R--D | C] -- C:\Documents and Settings\All Users\Documents\My Videos
[2013/01/06 20:27:30 | 000,000,000 | R--D | C] -- C:\Documents and Settings\All Users\Documents\My Pictures
[2013/01/06 20:26:54 | 000,000,000 | ---D | C] -- C:\WINDOWS\erdnt
[2013/01/06 20:25:03 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\fffu
[2013/01/06 17:57:34 | 000,000,000 | ---D | C] -- C:\Documents and Settings\All Users\Application Data\01014CE1ACC253E7000001014BE457DE
[2012/12/13 05:26:59 | 000,000,000 | ---D | C] -- C:\Documents and Settings\David\Desktop\web page patches
========== Files - Modified Within 30 Days ==========
[2013/01/10 23:50:00 | 000,000,830 | ---- | M] () -- C:\WINDOWS\tasks\Adobe Flash Player Updater.job
[2013/01/10 23:24:00 | 000,000,884 | ---- | M] () -- C:\WINDOWS\tasks\GoogleUpdateTaskMachineUA.job
[2013/01/10 21:08:25 | 001,872,454 | ---- | M] () -- C:\Documents and Settings\David\Desktop\mockup.bmp
[2013/01/10 16:24:27 | 000,000,512 | ---- | M] () -- C:\Documents and Settings\David\Desktop\MBR.dat
[2013/01/10 15:42:56 | 004,732,416 | ---- | M] (AVAST Software) -- C:\Documents and Settings\David\Desktop\aswMBR.exe
[2013/01/10 14:33:56 | 000,002,515 | ---- | M] () -- C:\Documents and Settings\David\Application Data\Microsoft\Internet Explorer\Quick Launch\Word.lnk
[2013/01/10 10:41:30 | 000,000,384 | -H-- | M] () -- C:\WINDOWS\tasks\Microsoft Antimalware Scheduled Scan.job
[2013/01/10 10:31:54 | 000,000,286 | ---- | M] () -- C:\WINDOWS\tasks\RealUpgradeScheduledTaskS-1-5-21-989678199-2234712002-1868543911-1006.job
[2013/01/10 10:31:54 | 000,000,278 | ---- | M] () -- C:\WINDOWS\tasks\RealUpgradeLogonTaskS-1-5-21-989678199-2234712002-1868543911-1006.job
[2013/01/10 10:31:44 | 000,001,170 | ---- | M] () -- C:\WINDOWS\System32\WPA.DBL
[2013/01/10 10:31:30 | 000,000,880 | ---- | M] () -- C:\WINDOWS\tasks\GoogleUpdateTaskMachineCore.job
[2013/01/10 10:31:17 | 000,002,048 | --S- | M] () -- C:\WINDOWS\BOOTSTAT.DAT
[2013/01/10 10:31:16 | 2146,508,800 | -HS- | M] () -- C:\hiberfil.sys
[2013/01/10 04:20:52 | 005,019,950 | R--- | M] (Swearware) -- C:\Documents and Settings\David\Desktop\ComboFix.exe
[2013/01/09 22:43:28 | 000,181,064 | ---- | M] (Sysinternals) -- C:\WINDOWS\PSEXESVC.EXE
[2013/01/09 22:43:06 | 000,000,855 | ---- | M] () -- C:\WINDOWS\System32\drivers\ETC\Hosts
[2013/01/09 20:45:23 | 000,000,664 | ---- | M] () -- C:\WINDOWS\System32\d3d9caps.dat
[2013/01/09 18:05:53 | 003,293,002 | ---- | M] () -- C:\Documents and Settings\David\Desktop\tweaking.com_windows_repair_aio.zip
[2013/01/09 13:02:28 | 000,000,792 | ---- | M] () -- C:\Documents and Settings\David\Application Data\Microsoft\Internet Explorer\Quick Launch\Launch Microsoft Office Outlook.lnk
[2013/01/08 21:48:18 | 000,397,390 | ---- | M] () -- C:\WINDOWS\System32\perfh009.dat
[2013/01/08 21:48:18 | 000,059,736 | ---- | M] () -- C:\WINDOWS\System32\perfc009.dat
[2013/01/08 20:07:38 | 013,485,902 | ---- | M] () -- C:\Documents and Settings\David\Desktop\mbar-1.01.0.1011.zip
[2013/01/07 19:38:05 | 000,602,112 | ---- | M] (OldTimer Tools) -- C:\Documents and Settings\David\Desktop\OTL.exe
[2013/01/07 03:22:26 | 000,546,744 | ---- | M] () -- C:\WINDOWS\System32\FNTCACHE.DAT
[2013/01/07 03:08:38 | 000,000,550 | ---- | M] () -- C:\WINDOWS\System32\reimage.rep
[2013/01/07 03:08:33 | 000,000,734 | ---- | M] () -- C:\WINDOWS\System32\drivers\ETC\hosts.bak
[2013/01/07 03:00:42 | 000,000,179 | ---- | M] () -- C:\WINDOWS\reimage.ini
[2013/01/07 02:38:34 | 000,009,216 | ---- | M] () -- C:\WINDOWS\System32\Native.exe
[2013/01/06 23:58:48 | 000,001,749 | ---- | M] () -- C:\Documents and Settings\All Users\Desktop\PC Scan & Repair by Reimage.lnk
[2013/01/06 23:09:49 | 000,001,945 | ---- | M] () -- C:\WINDOWS\epplauncher.mif
[2013/01/06 21:48:20 | 000,012,872 | ---- | M] (SurfRight B.V.) -- C:\WINDOWS\System32\bootdelete.exe
[2013/01/06 21:33:42 | 000,001,610 | ---- | M] () -- C:\Documents and Settings\All Users\Desktop\HitmanPro.lnk
[2013/01/06 20:29:19 | 000,000,327 | RHS- | M] () -- C:\BOOT.INI
[2013/01/03 01:58:22 | 000,000,784 | ---- | M] () -- C:\Documents and Settings\All Users\Desktop\Malwarebytes.lnk
[2012/12/21 02:04:30 | 000,000,211 | ---- | M] () -- C:\Boot.bak
[2012/12/16 15:06:03 | 000,444,870 | R--- | M] () -- C:\WINDOWS\System32\drivers\ETC\hosts.old
[2012/12/14 16:49:28 | 000,021,104 | ---- | M] (Malwarebytes Corporation) -- C:\WINDOWS\System32\drivers\mbam.sys
[2012/12/13 12:59:44 | 000,027,584 | ---- | M] () -- C:\Documents and Settings\David\Desktop\kissing-the-face-of-god-pewter-frame.jpg
[2012/12/13 05:28:40 | 000,002,359 | ---- | M] () -- C:\Documents and Settings\David\Desktop\Notepad.lnk
========== Files Created - No Company Name ==========
[2013/01/10 21:08:24 | 001,872,454 | ---- | C] () -- C:\Documents and Settings\David\Desktop\mockup.bmp
[2013/01/10 16:24:27 | 000,000,512 | ---- | C] () -- C:\Documents and Settings\David\Desktop\MBR.dat
[2013/01/10 04:28:06 | 000,256,000 | ---- | C] () -- C:\WINDOWS\PEV.exe
[2013/01/10 04:28:06 | 000,208,896 | ---- | C] () -- C:\WINDOWS\MBR.exe
[2013/01/10 04:28:06 | 000,098,816 | ---- | C] () -- C:\WINDOWS\sed.exe
[2013/01/10 04:28:06 | 000,080,412 | ---- | C] () -- C:\WINDOWS\grep.exe
[2013/01/10 04:28:06 | 000,068,096 | ---- | C] () -- C:\WINDOWS\zip.exe
[2013/01/09 20:59:34 | 2146,508,800 | -HS- | C] () -- C:\hiberfil.sys
[2013/01/09 18:05:10 | 003,293,002 | ---- | C] () -- C:\Documents and Settings\David\Desktop\tweaking.com_windows_repair_aio.zip
[2013/01/09 16:42:53 | 000,000,664 | ---- | C] () -- C:\WINDOWS\System32\d3d9caps.dat
[2013/01/08 20:04:37 | 013,485,902 | ---- | C] () -- C:\Documents and Settings\David\Desktop\mbar-1.01.0.1011.zip
[2013/01/07 03:08:33 | 000,000,550 | ---- | C] () -- C:\WINDOWS\System32\reimage.rep
[2013/01/07 03:03:18 | 000,001,992 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\MSN.lnk
[2013/01/07 03:03:18 | 000,001,605 | ---- | C] () -- C:\Documents and Settings\David\Start Menu\Programs\Remote Assistance.lnk
[2013/01/07 03:03:18 | 000,000,792 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\Windows Movie Maker.lnk
[2013/01/07 03:03:18 | 000,000,744 | ---- | C] () -- C:\Documents and Settings\David\Start Menu\Programs\Outlook Express.lnk
[2013/01/07 02:38:34 | 000,009,216 | ---- | C] () -- C:\WINDOWS\System32\Native.exe
[2013/01/06 23:58:49 | 000,000,179 | ---- | C] () -- C:\WINDOWS\reimage.ini
[2013/01/06 23:58:48 | 000,001,749 | ---- | C] () -- C:\Documents and Settings\All Users\Desktop\PC Scan & Repair by Reimage.lnk
[2013/01/06 23:19:42 | 000,000,384 | -H-- | C] () -- C:\WINDOWS\tasks\Microsoft Antimalware Scheduled Scan.job
[2013/01/06 23:09:43 | 000,001,698 | ---- | C] () -- C:\Documents and Settings\All Users\Start Menu\Programs\Microsoft Security Essentials.lnk
[2013/01/06 21:33:42 | 000,001,610 | ---- | C] () -- C:\Documents and Settings\All Users\Desktop\HitmanPro.lnk
[2013/01/06 20:29:19 | 000,000,211 | ---- | C] () -- C:\Boot.bak
[2013/01/06 20:29:16 | 000,260,272 | RHS- | C] () -- C:\cmldr
[2012/12/13 12:59:44 | 000,027,584 | ---- | C] () -- C:\Documents and Settings\David\Desktop\kissing-the-face-of-god-pewter-frame.jpg
[2012/04/26 16:50:30 | 000,178,257 | ---- | C] () -- C:\Documents and Settings\David\Local Settings\Application Data\census.cache
[2012/04/26 16:50:28 | 000,199,016 | ---- | C] () -- C:\Documents and Settings\David\Local Settings\Application Data\ars.cache
[2012/04/26 16:31:27 | 000,000,036 | ---- | C] () -- C:\Documents and Settings\David\Local Settings\Application Data\housecall.guid.cache
[2012/02/16 11:52:51 | 000,003,072 | ---- | C] () -- C:\WINDOWS\System32\iacenc.dll
[2012/02/07 11:59:20 | 000,000,000 | ---- | C] () -- C:\WINDOWS\RussSqr.INI
[2012/01/18 12:24:32 | 000,107,280 | ---- | C] () -- C:\WINDOWS\System32\zlib1.dll
[2012/01/02 02:49:08 | 000,175,616 | ---- | C] () -- C:\WINDOWS\System32\unrar.dll
[2011/03/22 16:31:14 | 000,000,000 | ---- | C] () -- C:\WINDOWS\nsreg.dat
[2010/01/28 01:02:42 | 000,003,072 | ---- | C] () -- C:\Documents and Settings\David\Cache.db
[2009/10/03 11:04:19 | 000,008,627 | ---- | C] () -- C:\Documents and Settings\David\PAV_FOG.OPC
[2005/09/06 15:49:09 | 000,000,000 | ---- | C] () -- C:\Documents and Settings\David\WebProxy.ini
[2004/02/03 11:27:42 | 000,017,920 | ---- | C] () -- C:\Documents and Settings\David\Local Settings\Application Data\DCBC2A71-70D8-4DAN-EHR8-E0D61DEA3FDF.ini
========== ZeroAccess Check ==========
[2009/05/31 18:59:08 | 000,000,227 | RHS- | M] () -- C:\WINDOWS\assembly\Desktop.ini
[HKEY_CURRENT_USER\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32]
[HKEY_CURRENT_USER\Software\Classes\clsid\{fbeb8a05-beee-4442-804e-409d6c4515e9}\InProcServer32]
[HKEY_LOCAL_MACHINE\Software\Classes\clsid\{42aedc87-2188-41fd-b9a3-0c966feabec1}\InProcServer32]
"" = %SystemRoot%\system32\shdocvw.dll -- [2008/04/13 19:12:05 | 001,499,136 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Apartment
[HKEY_LOCAL_MACHINE\Software\Classes\clsid\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\InProcServer32]
"" = %systemroot%\system32\wbem\fastprox.dll -- [2009/02/09 07:10:48 | 000,473,600 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Free
[HKEY_LOCAL_MACHINE\Software\Classes\clsid\{F3130CDB-AA52-4C3A-AB32-85FFC23AF9C1}\InProcServer32]
"" = %systemroot%\system32\wbem\wbemess.dll -- [2008/04/13 19:12:08 | 000,273,920 | ---- | M] (Microsoft Corporation)
"ThreadingModel" = Both
========== LOP Check ==========
[2013/01/06 17:57:34 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\01014CE1ACC253E7000001014BE457DE
[2008/01/28 11:52:18 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Backup
[2013/01/06 21:38:43 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\HitmanPro
[2012/12/06 17:13:31 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\Internet Content Filter
[2008/01/28 11:54:58 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\sentinel
[2012/09/26 18:55:11 | 000,000,000 | ---D | M] -- C:\Documents and Settings\All Users\Application Data\TuneUp Software
[2012/09/26 18:53:58 | 000,000,000 | -HSD | M] -- C:\Documents and Settings\All Users\Application Data\{32364CEA-7855-4A3C-B674-53D8E9B97936}
[2011/11/24 03:00:21 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\Desktop Maestro
[2013/01/07 03:33:25 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\ElevatedDiagnostics
[2011/04/14 08:03:57 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\Neuratron
[2006/07/07 18:35:01 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\OurPictures
[2004/03/23 21:52:52 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\The Labyrinth Plus! Edition
[2012/09/26 18:54:27 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\TuneUp Software
[2012/09/25 19:25:42 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\Windows Desktop Search
[2012/09/28 07:51:45 | 000,000,000 | ---D | M] -- C:\Documents and Settings\David\Application Data\Windows Search
========== Purity Check ==========
< End of report >
(3)
Below is the result of the run fix scan with the inserted code:
All processes killed
========== OTL ==========
Unable to delete ADS C:\Documents and Settings\All Users\Application Data\TEMP:0D786AE3 .
========== FILES ==========
< ipconfig /flushdns /c >
Windows IP Configuration
Successfully flushed the DNS Resolver Cache.
C:\Documents and Settings\David\Desktop\cmd.bat deleted successfully.
C:\Documents and Settings\David\Desktop\cmd.txt deleted successfully.
========== COMMANDS ==========
[EMPTYTEMP]
User: Administrator
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: All Users
User: David
->Temp folder emptied: 78174255 bytes
->Temporary Internet Files folder emptied: 6488577 bytes
->Java cache emptied: 0 bytes
->FireFox cache emptied: 9075230 bytes
->Google Chrome cache emptied: 0 bytes
->Flash cache emptied: 506 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
->Flash cache emptied: 0 bytes
User: LocalService
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 32902 bytes
User: NetworkService
->Temp folder emptied: 6434 bytes
->Temporary Internet Files folder emptied: 33170 bytes
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32\dllcache .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 5519 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temp folder emptied: 0 bytes
%systemroot%\system32\config\systemprofile\Local Settings\Temporary Internet Files folder emptied: 0 bytes
RecycleBin emptied: 204926 bytes
Total Files Cleaned = 90.00 mb
C:\WINDOWS\System32\drivers\etc\Hosts moved successfully.
HOSTS file reset successfully
OTL by OldTimer - Version 3.2.69.0 log created on 01112013_000738
Files\Folders moved on Reboot...
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
(4)
I was able to run HitManPro without any ill effects. When I had run the scan a couple of days ago, it came up with BOM in the HOSTS FILE. I tried a couple of times to delete it, but the scan crashed at 98% in regular and in safe mode with networking. When I ran the scan again in Safe Mode w/networking, I went ahead and clicked the button which reset the hosts file link and the BOM no longer showed up but the scan would still crash at 98%. Today, after doing the few changes you requested, the scan works perfectly with no bad effects!
Fiery said:Nothing is showing up in your combofix log. The BOM detection could be a false positive since hitmanpro uses multiple engines.
<hr>
- Download aswmbr.exe from the below link:
aswMBR DOWNLOAD LINK <em>(This link will automatically download aswMBR on your computer)</em>- Double click the aswMBR.exe to run it.
- Click the [Scan] button to start scan
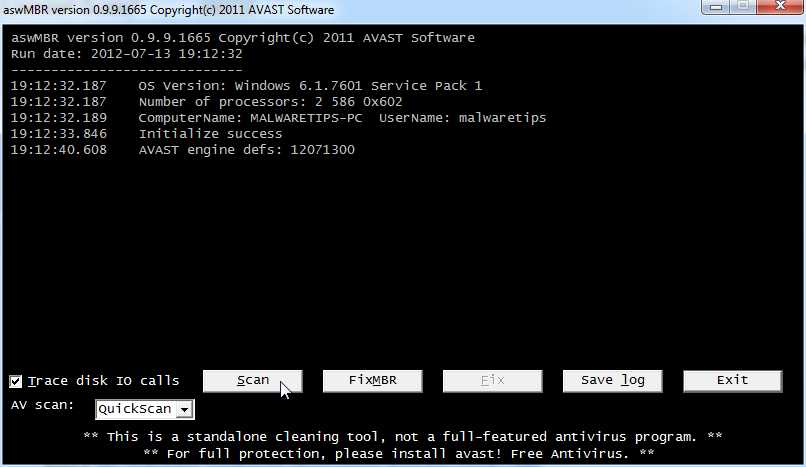
- On completion of the scan click [Save log], save it to your desktop and post in your next reply.
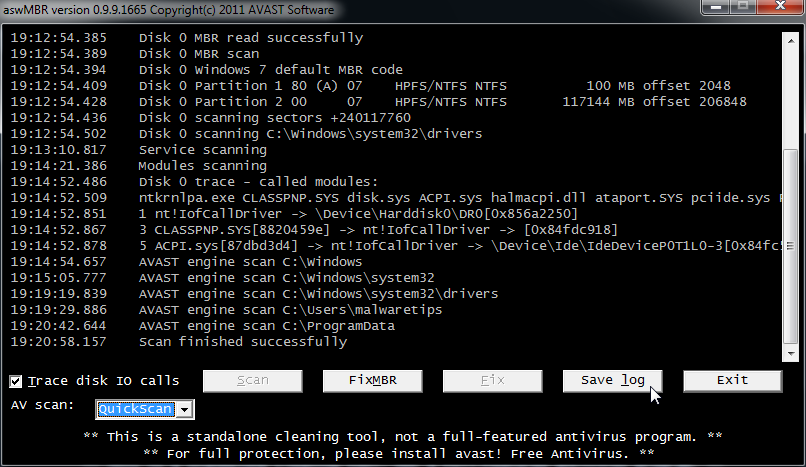
Can you try the OTL script again? I don't think you copied and pasted the script correctly.
Now do a hitmanPro scan and see if it crashes. Write down the directory of the BOM detection and post it in your next reply