- Dec 30, 2012
- 4,809
IDG News Service — A new Trojan program that can spy on victims, steal login credentials and interfere with browsing sessions is being sold on the underground market and might soon see wider distribution.
The new threat is called Pandemiya and its features are similar to that of the infamous Zeus Trojan program that many cybercriminal gangs used for years to steal financial information from businesses and consumers.
Zeus source code was leaked on underground forums in 2011, allowing other malware developers to create Trojan programs based on it, including threats like Citadel, Ice IX and Gameover Zeus, whose activity was recently disrupted by an international law enforcement effort.
"Pandemiya's coding quality is quite interesting, and contrary to recent trends in malware development, it is not based on Zeus source code at all, unlike Citadel/Ice IX, etc.," researchers from RSA, the security division of EMC, said Tuesday in a blog post. "Through our research, we found out that the author of Pandemiya spent close to a year of coding the application, and that it consists of more than 25,000 lines of original code in C."
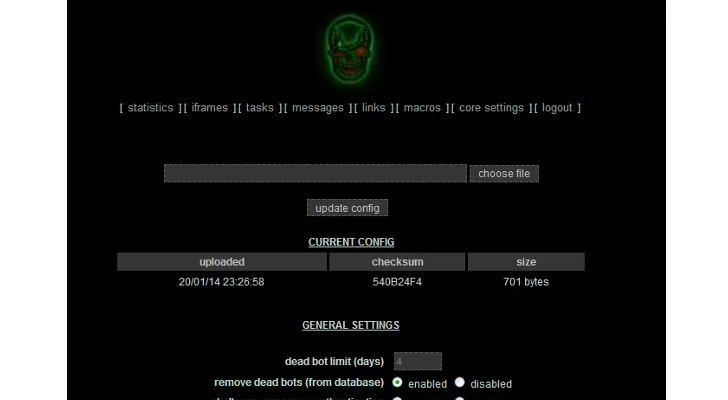
The new Trojan program can inject rogue code into websites opened in a local browser, a technique known as Web injection; grab information entered into Web forms; steal files; and take screenshots. Because it has a modular architecture, its functionality can also be extended through individual DLL (dynamic link library) files that act as plug-ins.
Some of Pandemiya's existing plug-ins allow cybercriminals to open reverse proxies on infected computers, to steal FTP credentials and to infect executable files. Its creators are also working on others to enable reverse Remote Desktop Protocol connections and to allow the malware to spread through hijacked Facebook accounts, the RSA researchers said.
"Like many of the other Trojans we've seen of late, Pandemiya includes protective measures to encrypt the communication with the control panel, and prevent detection by automated network analyzers," the researchers said.
The new threat is being advertised on underground forums for US$1,500 for the core application and $2,000 with additional plug-ins, a relatively high entry price for cybercriminals. This aspect and the fact that it's new have kept Pandemiya from gaining popularity so far, but because it can easily be expanded with DLL plug-ins "could make it more pervasive in the near future," the RSA researchers said.
Source
The new threat is called Pandemiya and its features are similar to that of the infamous Zeus Trojan program that many cybercriminal gangs used for years to steal financial information from businesses and consumers.
Zeus source code was leaked on underground forums in 2011, allowing other malware developers to create Trojan programs based on it, including threats like Citadel, Ice IX and Gameover Zeus, whose activity was recently disrupted by an international law enforcement effort.
"Pandemiya's coding quality is quite interesting, and contrary to recent trends in malware development, it is not based on Zeus source code at all, unlike Citadel/Ice IX, etc.," researchers from RSA, the security division of EMC, said Tuesday in a blog post. "Through our research, we found out that the author of Pandemiya spent close to a year of coding the application, and that it consists of more than 25,000 lines of original code in C."
The new Trojan program can inject rogue code into websites opened in a local browser, a technique known as Web injection; grab information entered into Web forms; steal files; and take screenshots. Because it has a modular architecture, its functionality can also be extended through individual DLL (dynamic link library) files that act as plug-ins.
Some of Pandemiya's existing plug-ins allow cybercriminals to open reverse proxies on infected computers, to steal FTP credentials and to infect executable files. Its creators are also working on others to enable reverse Remote Desktop Protocol connections and to allow the malware to spread through hijacked Facebook accounts, the RSA researchers said.
"Like many of the other Trojans we've seen of late, Pandemiya includes protective measures to encrypt the communication with the control panel, and prevent detection by automated network analyzers," the researchers said.
The new threat is being advertised on underground forums for US$1,500 for the core application and $2,000 with additional plug-ins, a relatively high entry price for cybercriminals. This aspect and the fact that it's new have kept Pandemiya from gaining popularity so far, but because it can easily be expanded with DLL plug-ins "could make it more pervasive in the near future," the RSA researchers said.
Source