The Australian Federal Police (AFP) Ukash Ransom is a computer virus, which will display a bogus notification, that pretends to be from the Australian police and states that your computer has been blocked due to it being involved with the distribution of pornographic material, SPAM and copyrighted content.
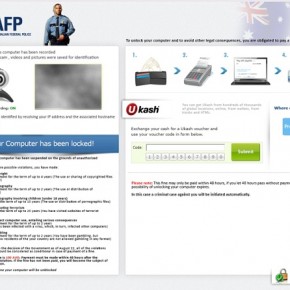
The Australian Federal Police virus will lock you out of your computer and applications, so whenever you’ll try to log on into your Windows operating system or Safe Mode with Networking, it will display instead a lock screen asking you to pay a non-existing fine of 100 $ in the form of a Ukash or PaySafeCard code.
Furthermore, to make this alert seem more authentic, this virus also has the ability to access your installed webcam ,so that the bogus Australian Federal Police notification shows what is happening in the room.
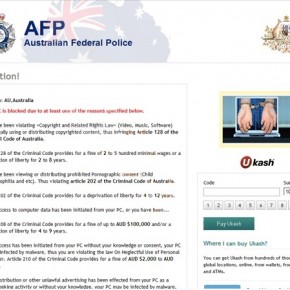
If your computer is infected with Australian Federal Police virus, then you are seeing any of the below notifications:
AFP Australian Federal Police
Attention!
Your PC is blocked due to at least one of the reasons specified below. You have been violating “Copyright and Related Rights Law” (Video, Music, Software) and illegally using or distributing copyrighted content, thus infringing Article 128 of the Criminal Code of Australia. Article 128 of the Criminal Code provides for a fine of 2 to 5 hundred minimal wages or a deprivation of liberty for 2 to 8 years.
You have been viewing or distributing prohibited Pornographic content (Child Porn/Zoophillia anr etc.) Thus violating article 202 of the Criminal Code of Australia.
Article 202 of the Criminal Code provides for a deprivation of liberty for 4 to 12 years. Illegal access to computer has been initiated from your PC, or you have been… Article 208 of the Criminal Code provides for a fine of up to AUD $100,000 and/or a deprivation of liberty for 4 to 9 years.
Illegal access has been initiated from your PC without your knowledge or consent, your PC may be infected by malware, thus you are violating the law On Neglectful Use of Personal Computer. Article 210 of the Criminal Code provides for a fine of AUD $2,000 to AUD $8,00.
The Australian Federal Police Ransom is a scam, and you should ignore any alert that this malicious software might generate and remove this trojan ransomware from your computer.
Under no circumstance should you send any money to these cyber criminals, as this could lead to identity theft,and if you have, you should request a refund stating that the program is a scam and a computer virus.
Australian Federal Police (AFP) – Virus Removal Guide
This page is a comprehensive guide, which will remove the Australian Federal Police infection from your your computer. Please perform all the steps in the correct order. If you have any questions or doubt at any point STOP and ask for our assistance.
The Australian Federal Police will start automatically when you login to your computer and display its screenlocker so that you are unable to access your computer, therefore we will need to remove this infection by using any of the below methods:
OPTION 1: Remove Australian Federal Police lock screen virus with System Restore
OPTION 2: Remove Australian Federal Police virus with with HitmanPro Kickstart
OPTION 3: Remove Australian Federal Police virus with Kaspersky Rescue Disk
OPTION 1: Remove Australian Federal Police lock screen virus with System Restore
System Restore helps you restore your computer’s system files to an earlier point in time. It’s a way to undo system changes to your computer without affecting your personal files, such as e‑mail, documents, or photos.
Because the Australian Federal Police virus will not allow you to start the computer in Windows regular mode, we will need to start System Restore from the Safe Mode with Command Prompt mode.
STEP 1: Restore Windows to a previous state using System Restore
- Reboot your computer into Safe Mode with Command Prompt. To do this, turn your computer off and then back on and immediately when you see anything on the screen, start tapping the F8 key on your keyboard.
If you are using Windows 8, the trick is to hold the Shift button and gently tap the F8 key repeatedly, this will sometimes boot you into the new advanced “recovery mode”, where you can choose to see advanced repair options. On the next screen, you will need to click on the Troubleshoot option, then select Advanced Options and select Windows Startup Settings. Click on the Restart button, and you should now be able to see the Advanced Boot Options screen. - Using the arrow keys on your keyboard, select Safe Mode with Command Prompt and press Enter on your keyboard.
- At the command prompt, type rstrui.exe, and then press ENTER.
Alternatively, if you are using Windows Vista, 7 and 8, you can type: C:\windows\system32\rstrui.exe , and press Enter. And if you are a Windows XP user, type C:\windows\system32\restore\rstrui.exe, then press Enter. - System Restore should start, and you will display also a list of restore points. Try using a restore point created just before the date and time the Australian Federal Police lock screen virus has infected your computer.
- When System Restore has completed its task, start your computer in Windows regular mode, and perform a scan with Malwarebytes Anti-Malware and HitmanPro, as seen in the next step.
STEP 2: Remove Australian Federal Police malicious files with Malwarebytes Anti-Malware Free
Even after using System Restore,
- You can download Malwarebytes Anti-Malware Free from the below link, then double-click on the icon named mbam-setup.exe to install this program.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK(This link will open a download page in a new window from where you can download Malwarebytes Anti-Malware Free) - When the installation begins, keep following the prompts in order to continue with the setup process, then at the last screen click on the Finish button.
- On the Scanner tab, select Perform quick scan, and then click on the Scan button to start searching for the Australian Federal Police malicious files.
- Malwarebytes’ Anti-Malware will now start scanning your computer for Australian Federal Police virus as shown below.
- When the Malwarebytes Anti-Malware scan has finished, click on the Show Results button.
- You will now be presented with a screen showing you the computer infections that Malwarebytes Anti-Malware has detected. Make sure that everything is Checked (ticked), then click on the Remove Selected button.
STEP 3: Double-check for the Australian Federal Police virus with HitmanPro
- You can download HitmanPro from the below link:
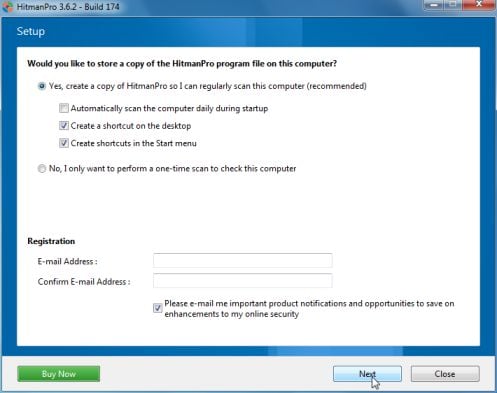
HITMANPRO DOWNLOAD LINK (This link will open a web page from where you can download HitmanPro) - Double-click on the file named HitmanPro.exe (for 32-bit versions of Windows) or HitmanPro_x64.exe (for 64-bit versions of Windows). When the program starts you will be presented with the start screen as shown below.
Click on the Next button, to install HitmanPro on your computer.
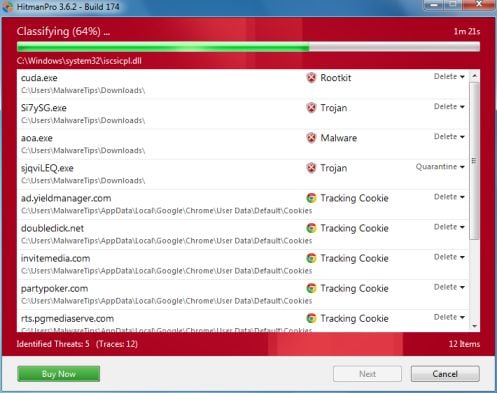
- HitmanPro will now begin to scan your computer for Australian Federal Police malicious files.
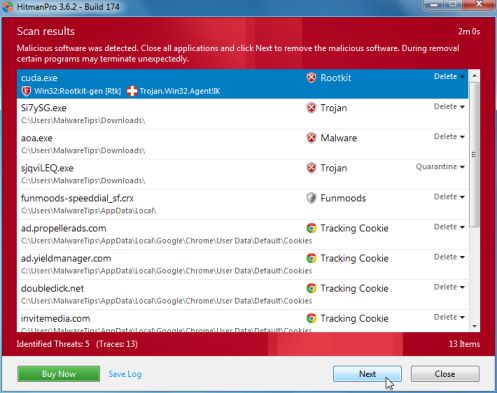
- When it has finished it will display a list of all the malware that the program found as shown in the image below. Click on the Next button, to remove Australian Federal Police virus.
- Click on the Activate free license button to begin the free 30 days trial, and remove all the malicious files from your computer.
OPTION 2: Remove Australian Federal Police virus with with HitmanPro Kickstart
If you cannot start your computer into Safe Mode with Command Prompt mode, we can use the HitmanPro Kickstart program to bypass Australian Federal Police lock screen.
As the Australian Federal Police ransomware infection locks you out of your computer, you will need to create a bootable USB drive that contains the HitmanPro Kickstart program.
We will then boot your computer using this bootable USB drive and use it to clean the infection so that you are able to access Windows normally again.
You will also need a USB drive, which will have all of its data erased and will then be formatted. Therefore, only use a USB drive that does not contain any important data.
- Using a “clean” (non-infected) computer, please download HitmanPro Kickstart from the below link.
HITMANPRO DOWNLOAD LINK (This link will open a download page in a new web page from where you can download HitmanPro Kickstart) - Once HitmanPro has been downloaded, please insert the USB flash drive that you would like to erase and use for the installation of HitmanPro Kickstart. Then double-click on the file named HitmanPro.exe (for 32-bit versions of Windows) or HitmanPro_x64.exe (for 64-bit versions of Windows).
To create a bootable HitmanPro USB drive, please follow the instructions from this video:
- Now, remove the HitmanPro Kickstart USB drive and insert it into the Australian Federal Police infected computer.
- Once you have inserted the HitmanPro Kickstart USB drive, turn off the infected computer and then turn it on. As soon as you power it on, look for text on the screen that tells you how to access the boot menu.
The keys that are commonly associated with enabling the boot menu are F10, F11 or F12. - Once you determine the proper key (usually the F11 key) that you need to press to access the Boot Menu, restart your computer again and start immediately tapping that key. Next, please perform a scan with HitmanPro Kickstart as shown in the video below.
- HitmanPro will now reboot your computer and Windows should start normally. Then please Malwarebytes Anti-Malware and HitmanPro, and scan your computer for any left over infections.
OPTION 3: Remove Australian Federal Police virus with Kaspersky Rescue Disk
If any of the above methods did not clean your infected computer, we can use a Kaspersky Rescue Disk Bootable to clean the Windows registry and to perform a system scan to remove the Australian Federal Police virus.
To create a bootable Kaspersky Rescue Disk, we will need the following items:
- A clean (non-infected) computer with Internet access
- A blank DVD or CD
- A computer with a DVD or CD burner
STEP 1: Download and create a bootable Kaspersky Rescue Disk CD
- You can download Kaspersky Rescue Disk utility from link below:
KASPERSKY RESCUE DISK DOWNLOAD LINK (This link will automatically download Kaspersky Rescue Disk (kav_rescue_10.iso) on your computer.) - To create the bootable rescue disk, we will need to use the ImgBurn program. You can download ImgBurn from the below link, then install this program.
IMGBURN DOWNLOAD LINK (This link will open a new page from where you can download the ImgBurn program) - Insert your blank DVD or CD in your burner, then start ImgBurn and click on the Write image file to disc button.
- Under Source click on the Browse for file button, then navigate to the location where you previously saved the Kaspersky Rescue Disk utility (kav_rescue_10.iso), then click on the Write button.
That’s it, ImgBurn will now begin writing your bootable Kaspersky Rescue Disk.
STEP 2: Start your computer using the Kaspersky Rescue Disk
- Once you’ve got the Kasperky Rescue Disk in hand, insert it into the infected computer, and turn off and then turn it on again.
- As soon as you power it on, you will see a screen that tells you to press any key to enter the menu, so please tap any key to boot your machine from the Kaspersky Rescue Disk.
- In the next screen, you will need to chose a language, then you click on Kaspersky Rescue Disk. Graphic Mode and press ENTER, to start the Kaspersky Rescue Disk.
STEP 3: Scan your system with Kaspersky Rescue Disk
- Within a few short seconds you should see the full working environment, with the Kaspersky Rescue Disk screen front and center as shown below.
- Switch tabs over to the My Update Center, and then click the Start update button to load the latest anti-virus definitions. Please be patience while this process its completed.
- Switch back over to the Objects Scan tab, select the drives you want to scan, and then click the Start Objects Scan button.
- When Kaspersky Antivirus will detect the Australian Federal Police virus, you’ll be prompted to select an action. When this happens, please select Quarantine or Delete to remove this infection from your computer.
- When the antivirus scan has completed, you can restart back into Windows regular mode, by clicking on the Kaspersky Start button
(lower left corner), and selecting Restart.
Once your computer will start in Windows regular more, download Malwarebytes Anti-Malware and HitmanPro, and scan your computer for any left over infections.
Your computer should now be free of the Australian Federal Police infection. If your current anti-virus solution let this infection through, you may want to consider purchasing the PRO version of Malwarebytes Anti-Malware to protect against these types of threats in the future, and perform regular computer scans with HitmanPro.
If you are still experiencing problems while trying to remove Australian Federal Police Ukash virus from your machine, please start a new thread in our Malware Removal Assistance forum.

![Remove Australian Federal Police virus (Removal Guide) 1 [Image: AFP virus]](https://malwaretips.com/blogs/wp-content/uploads/2012/11/australian-federal-police-virus-290x290.jpg)
![Windows F8 key [Image: F8 key]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/F8-key.jpg.png)
![Advanced Boot Options screen [Image: Starting computer in Safe Mode with Command Prompt]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Safe-Mode-with-Command-Prompt.jpg)
![rstrui.exe command in Safe Mode with Command Prompt [Image: Start System Restore to remove lock screen virus]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/system-restore-command.jpg)
![Restore your computer's system files to an earlier point in time [Image: Restore settings to remove ransomware]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/system-restore.jpg)
![Malwarebytes Anti-Malware installation screen [Image: Malwarebytes Anti-Malware final installation screen]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)
![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
![Malwarebytes Anti-Malwar removing Australian Federal Police virus [Image: Malwarebytes Anti-Malwar removing Australian Federal Police virus]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)
![HitmanPro free 30 days trial [Image: HitmanPro 30 days activation button]](http://malwaretips.com/blogs/wp-content/uploads/2012/11/hitmanpro-activation.jpg)
![Windows Boot Menu screens [Image: Windows Boot Menu screens]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/windows-boot-manager.jpg)
![Creating Kaspersky Rescue Disk bootable CD [Image: Bootable Kaspersky Rescue CD]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/creating-bootable-kaspersky-rescue-disk.jpg)
![Starting infected computer from Kaspersky Rescue Disk [Image: Starting infected computer from Kaspersky Rescue Disk]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Kaspersky-Rescue-Disk-boot.png)
![Kaspersky Rescue Disk Graphic Mode screen [Image: Kaspersky Rescue Disk Graphic Mode screen]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Kaspersky-Rescue-Disk-graphic-mode.png)
![Kaspersky Rescue Disk scanner [Image: Kaspersky Rescue Disk scanner]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Kaspersky-Rescue-Disk.jpg)
![Updating Kaspersky Rescue Disk antivirus definitions [Image: Updating Kaspersky Rescue Disk antivirus definitions]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Kaspersky-Rescue-Disk-update.jpg)
![Kaspersky Rescue Disk scan [Image: Kaspersky Rescue Disk scan]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Kaspersky-Rescue-Disk-scan.jpg)
![Kaspersky Rescue Disk when detecting malware [Image: Kaspersky Rescue Disk prompt]](http://malwaretips.com/blogs/wp-content/uploads/2013/06/Kaspersky-Rescue-Disk-alarm.png)










Hello,
You are safe, the police is not looking for you :). This pop-up is a scam. Please reefer to this post for more details: https://malwaretips.com/blogs/remove-fbi-virus-from-iphone-and-ipad/
Please note that in some cases, the router may be infected, in this case, you will just need to reset the router on its default settings (to do this, keep pressed for 30 seconds the RESET button on the back of your router).
You can also ask for FREE malware removal support in the Malware Removal Assistance forum – https://malwaretips.com/forums/malware-removal-assistance.10/ . In this support forum, a trained staff member will help you clean-up your machine by using advanced tools. Never used a forum? Learn how- https://malwaretips.com/help/welcome-guide/
My Iphone 6 was hit yesterday with this heart stopping virus. What an accusation!! I was using a video download app when it happened. Also the mobile reception here in the country is very bad.
Quickly, I closed app turn off phone before it took me further down a dark alley. Then Powered up to check safari and deleted app.
Safari works… Phone works…
Could i have got out before it could have infected my device?
Would the afp actually send warning and accusations at all? You think they would get the evidence and come arrest you??
Hello Layaknsk,
Please take a look at this thread.. – https://malwaretips.com/threads/mandiant-virus-on-lg-google-smart-tv.52900/ – it depends on the TV brand, usually you will need to reset it to its default settings. Also make sure to disconnect it from the Internet while trying to perform a cleanup…..
Hello Kate,
Please follow this guide: https://malwaretips.com/blogs/android-police-virus-removal/
I have recently contracted the AFP virus (two days ago) cryptolocker virus.
please advise me if you have a solution to attack this new version.
if you can solve this for me I will definitely donate money to your site to assist you fighting these criminal lowlifes praying on innocent people.
with all their knowledge they should be able to earn a honest living
Hi can you tell me how to remove the afp virus from my ipad air thanks del
Thank you so much
Hello,
If the Malwarebytes and HitmanPro scans said that your PC is clean, then you’ve got nothing to worry about. :)
So when i got this virus i just did a malwarebytes scan, no more lock screen. Two additional scans found nothing. Should i consider myself in the clear?
Thank you man! You’re the best!!
Hello,
I would also perform the HitmanPro scan just to be on the safe side, however you should be safe! :)
Hey I got this virus and restarted my computer in safe mode with networking. When I did a did a scan using malwarebytes nothing came up? Does that mean I am in the clear?
Hello,
If Malwarebytes and HitmanPro did not find any threats, then you should be fine.
If you really want to make a third check you can use these tools:
STEP 1: Run a scan with Emsisoft Emergency Kit.
1. Please download the latest official version of Emsisoft Emergency Kit: http://www.emsisoft.com/en/software/eek/
2. After the download process will finish , you’ll need to unpack EmsisoftEmergencyKit.zip and then double click onEmergencyKitScanner.bat
3. A pop-up will prompt you to update Emsisoft Emergency Kit , please click the “Yes” button.After the Update process has completed , put the mouse cursor over the “Menu” tab on the left and click-on “Scan PC”.
4. Select “Smart scan” and click-on the below “SCAN” button.When the scan will be completed , you will be presented with a screen showing you the malware infections that Emsisoft Emergency Kit has detected.Make sure that everything is Checked (ticked) and click on the ‘Quarantine selected objects’ button.
STEP 2: Run a scan with Eset Online Scanner.
1.Download ESET Online Scanner utility.
ESET Online Scanner Download Link (This link will automatically download ESET Online Scanner on your computer.)
2. Double click on the Eset installer program (esetsmartinstaller_enu.exe).
3.Check Yes, I accept the Terms of Use, then click the Start button.
4.Check Scan archives and push the Start button.
5. ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.
When the scan completes, push Finish
STEP 3: Run a scan with Kaspersky Virus Removal Tool:
1. You can download from Kaspersky Virus Removal Tool from here : http://www.kaspersky.com/antivirus-removal-tool?form=1
2. Double click the setup file to run it, then follow the onscreen prompts until it is installed
Click the Options button (the ‘Gear’ icon), then make sure only the following are ticked:
System Memory
Hidden startup objects
Disk boot sectors
Local Disk (C:)
Also any other drives (Removable that you may have)
3. Then click on Actions on the left hand side
4. Click Select Action, then make sure both Disinfect and Delete if disinfection fails are ticked
5. Click on Automatic Scan, then click the Start Scanning button, to run the scan
Stay safe!
Hi, I believe my computer has been affected by this virus. I tried Option 1 – and managed to restart my computer to a previous state. However, when I tried to do steps 2 and 3 (scanning and attempting to remove the virus with both Malwarebytes and HitmanPro), the scans both came up and said that there were no threats found. How can I be sure that there is no virus still on my computer?
Hello Dereck,
You could boot into Safe Mode with Command Prompt, type “explorer.exe” and then use a USB stick to bring Malwarebytes and HitmanPro on the infected computer.
Also, take a look at Option 2, it’s pretty easy to follow …
Stay safe!
Is a system restore vital or can it just be cleaned in safe mode with both of your program’s?
Hello,
Can you pleas try to create a bootable HitmanPro USB. Let me know if it worked!
Hi there, option one didn’t working. There was a system restore error. Now I have a basic desktop. Please help!
Hello,
Yes, but unlike the Windows infection, it just affects your web browser, follow this guide to clean your MAC OS X: http://malwaretips.com/blogs/your-browser-has-been-locked-fbi-mac-os-x/
can it infect a mac?
Thank you. Option 1 worked a treat. Very much appreciated.
theyshiuldshut ukash down because of this scam
Hello,
Did you manage to create a bootable HitmanPro USB stick or Kaspersky Rescue Disk?
Hell Paul,
Have you tried to create a HitmanPro bootable USB stick?
When I try to run my computer in safe mode, it just shuts itself down just before windows starts and reboots. What should I do?
Hi I have this virus and I can’t get the computer to even start in any safe mode. It keeps rebooting my computer. What should I do?
thanks mate,you have restored my faith in man.your system worked a treat.
Hello,
An time consuming method, but it works! :)
Stay safe Raj!
Thanks for replying Stelian. I decided to reformat my windows to be on the safe side.
Thanks for your time buddy.
Hello,
There are plenty of website with adult content, so I would avoid that particular site.
Now, even if you do not have the AFP lockscreen, you might have some malicious files on your computer. Just to be on the safe side, I would perform a scan with Malwarebytes Anti-Malware and HitmanPro.
Also, please update Java (If installed) to its latest version!
Stay safe!
Hi Stelian,
I received the AFP message while watching online porn and I couldn’t leave the page so I used the Power button to shut down my computer. However, after that I was able to log in to my computer and everything seems fine. Does that mean I shouldn’t watch porn from that particular website? I will be reformatting my window, that should do the trick right? Please reply. Thanks
Hello David,
If you can login into your Windows normally, then download Malwarebytes Anti-Malware and HitmanPro, and run a full system scan with both utilities.
Stay safe!
Hello Rob,
You should really scan your computer with Mawlarebytes Anti-Malware and HitmanPro, to check for any malicious file that might be on your computer.
Stay safe!
Hi, I received the same message and it wouldn’t let me leave the page initially, however I used the ‘start task manager’.. ‘end task’, and it clicked off. I have then restarted my computer a couple of times (as I normally would), and I am not receiving any more messages. As far as I can tell my PC seems to be working fine. Have I just got lucky? Do I still need to follow the steps? or is it all fine? everything seems fine. Any advice would be appreciated. Thank you!
Hello Stelian, please help!? I came across this scam but I receive a totally different notification on my computer to what you have shown. Could this be another version of the ukash scam? And another thing is that my computer is still functional and it starts up normally, does that mean I don’t have the virus? Do I still need to follow your steps? Please help as I am not very good with these type of things… Thank you!
Hello Leanne,
If this infection has not compromised your Administrator account, then you can login and perform the Malwarebytes Anti-Malware and HitmanPro scans from there.
As an alternative, while your computer in Safe Mode with Command Prompt, type msconfig in the Command prompt box.
This should start the Windows System Configuration tool.
Go to the Start-up tab, and search for any suspicious or unknown entries (random numbers or letter, ctfmon.exe and other suspicious entries) and uncheck them from start-up.
Next, start your computer in normal mode and perform a scan HitmanPro and Malwarebytes Anti-Malware as seen in this guide.
Good luck! Waiting for your reply to see how everything is working!
Thanks for your support!
Hello,
This type of infection is mostly spread via a Java or Adobe exploit, and is mostly found on website with adult content.
Basically you did not update this programs, and visited an infected website, which exploited a a vulnerability on a program installed on your machine.
You will not need to follow the steps from this guide to remove this infection.
Stay safe!
Thank you so much!
Hello,
I would advise you to also run the HitmanPro scan just to be on the safe side. However, if you do not get the AFP lock screen when starting your computer, then this ransomware should be gone.
hi , i have performed the malware bytes scan and a;so did the a scan with Avast that i already had on my laptop. Is this sufficient? and is the virus definitley gone? Thanks.
Hello,
If are able to boot into Windows regular mode, and if you have performed a scan with Malwarebytes and HitmanPro, then your computer should be clean.
Nevertheless, for you peace of mind, you can run a scan with ESET Online Scanner
1.Download ESET Online Scanner utility.
ESET Online Scanner Download Link : http://download.eset.com/special/eos/esetsmartinstaller_enu.exe
2. Double click on the Eset installer program (esetsmartinstaller_enu.exe).
3.Check Yes, I accept the Terms of Use, then click the Start button.
4.Check Scan archives and push the Start button.
5. ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.
6. When the scan completes, click on the Finish button.
Thank-you so much this had helped me heaps I was so close to pay 100$!Thank-you so much:)I have used option one and two! great!
Hello Paul,
Avast Free Antivirus and COMODO Internet Security Free are both great free options, which will provide a high level of security for your computer.
I do recommend that you read this guide >> http://malwaretips.com/blogs/how-to-easily-avoid-pc-infections/ < < so that you'll learn how to avoid future infections!
Anyway ,you should really start a thread in our Security Configuration forum as you need to build a layered security config: http://malwaretips.com/Forum-Security-Configuration-Wizard
Dude u’re a light save. Honestly. Im not computer savvy but ure tutorial step by step worked easily. Unfortuately i did pay the $100 but hey i didnt know there was another safe way 2 exchange $ safely across the waves without revealing bank details but i strongly believe in karma so all i can say is i wouldnt want 2 b them in the near future…anyways bless ure kind spirit & thumbs up 4 ure good advice. i wish u now 10 fold 4 what u have done 4 ure fellow brothers & sisters. ure bookmarked 4 brillant service now by many im sure especially by me.
ps. i did step 2 & used trial hitman pro 3.7 anti-malware. pss. Thanks again. Peace.
Thank you so so much for this posting. You saved my day!!!
Sorry one more thing. If you cant run the above software based on the steps above (Like in my case), you need to save the software to a flash drive per steps above and then execute (Run the .exe files) via DOS prompt as I couldn’t run the software any other way. But you gotta know which drive the flash will come under on your infected PC. It was trial and error for me displaying directories via DOS, but it should be either E or F for flash drives, it was E for me. Hope this helps.
PS: I cant believe the AFP have done nothing to remove this virus from the internet, maybe they cant..
God bless Google!!!!!
Thank you so much, bless you for this. In my case, I am part of a network so the virus software above only partly worked. It showed what the “Ransomware” file was called which is “altshell.dat”. The above software showed me where on my PC this file resided and I simply went and deleted it via DOS prompt. I don’t even know DOS much I just Googled to find out how to display the directory and delete the file. The other methods did not work in isolation, instead I went through each and in the end used method 4 with the hitman pro virus software and found and deleted the file above and all is good. My only question is that there was also a “altshell.ini” file as well not sure if this was linked but I deleted that too. Oh yes if you can’t find the folder on your PC (as identified by the hitman software that contains the virus file) this will probably be due to Windows in their wisdom hiding it so you need to unhide hidden folders. In my case the virus was under C:\Users\Username\AppData\Roaming\altshell.dat and altshell.ini. So, moral of the story is, if the above methods don’t work in isolation, do what I did and use bits of them, like with the hitman software to find where the damn evil file is and then delete it. If I had taken this to my offshore IT help desk, they would have just told me to fully reimage my PC, taking days to do, losing work time and huge stress!!! You saved me, god bless you.
thanks for your help I obviously need to update malware/antivirus software, any suggestions at all please , thanks again
Thank you for your help I ended up using the hitman pro USB method but I finally got rid of the Trojan and now my computer is running just fine.
Thanks Man
Your a superhero. So many people say there going to help but there is always an ulterior motive.
You got me and my business up and running in no time.
Thank-you for the given advice.
I ended up having to use method 4. I was able to get on the guest user on my PC at the time, no screen lock was in place on guest..Which was interesting. Downloaded the given Malwarebytes download. Went through all the processes and the other user became accessible with virus deleted..
I was fortunate and at ease that i could access the other user account on the computer at.. This made it possible to come by this site straight away after the event..
Thanks, again. =]
A thousand times thankyou. We are in our 60’s and not very technological savvy but we were able to remove that hideous Australia “Federal Police” virus. We downloaded the two programmes to usb and it was so simple for us after that. Don’t know what these creeps get out of sending viruses but I do believe in karma.
Once again thank you.
Thank you so much Stelian!!! Really appreciate you taking the time to help out people with pc problems. We will be looking to your blog in the future if we have any further problems
Thanks again
Hello Sander,
If the Malwarebytes and HitmanPro scan results are clean, you should be fine!
Thank you!
Hello Zuhair,
Please follow this guide: http://malwaretips.com/blogs/remove-22find-com-hijack/
Hi,
thanks for the help.
I have used Method 2, and it worked perfectly!
But still I have a virus called(22FIND)in my laptop, I tried many Methods to remove ,still in my laptop, using Win 7.
Any help pls
Hi Stelian
So happy – managed to remove a trojan.ransom (skype.dat) on my computer by using option 2 (restore Windows).
The Hitman Pro found 2 traces: F\HKLM\software/classes and S\HKLM/software/classes
I only had a white screen – no ransom message.
Thanks for sharing your expertise. Greatly appreciated.
Hi, just wanted to say thank you for helping me out. Thank you! God bless!
Saying thank you would be a Huuuuuuge UNDERSTATEMENT for ALL your great help to myself and hundreds of others, so all I can say is that you should be absolutely proud of yourself for helping me and hundreds, maybe even thousands of people globally. The Ukash scam led me to panic, but you helped me when I needed it. So I thank you Stelian! and God Bless You Brother
Hello Stephen,
No it’s not an problem, if you have performed a scam with Malwarebytes and HitmanPro, and the scan results were 0 threas, you’re computer is clean!
Stay safe!
Thanks Stelian…I thought my hard drive had died but we are back up and running. Method 2 worked a treat although Hitman Pro didn’t find any AFP malicious files. Is this a problem?
I am not sure if you are ever going to read this Stelian but thank you very very much! Method 1 worked a charm (please ignore my previous comment, not sure what I was doing wrong). You are a genius, being an IT pro myself, I couldn’t get rid of this malware on my friends laptop. Let me know if I could be of any use to you! If you ever decide to travel to Brisbane, Australia someday, I would love to show u around :-)
thank you alot!! worked straight away took me about 20 minutes but worked perfectly fine and good luck to anyone who gets this virus or trojan thingy gave me a heart attack !!!!
THANK YOU SO MUCH! :D
Method 2 worked for me. I followed the steps diligently and my laptop appears fixed. Thank you for sharing your expertise and knowledge. It is appreciated.
Hello Hayley,
I’m glad to read that you have managed to clean up your computer, I would advise you to backup on an USB or external HDD all your personal documents, to avoid losing them in the future. The new malware threats that are launched are very agreesive, so it’s a good idea to have an back-up!
Hello Ehsan,
Just stay safe, and have an awesome life!! :D
Hey Man,
Thanks Heaps, Method 1, worked a treat
Can’t believe the AFP know about this and it’s been going on for more than 6 months……….
I have used method 2 and it worked perfectly. I was going crazy until I found your website on my spare laptop. Thank you so much.
Thanks very much for your help the steps were so easy to follow people like you are what make the world a better place
Thank you so much!! The steps worked perfectly!!
Since it appears that ukash is ac tively processing payments for the scammers can’t they be prosecuted. They bear a lot of responsibility for facilitating this scam. Victims should organize and sue!
Hello Eric,
This AFP notification is a scam, and the most likely point of infection is an compromised email attachment that you have opened!
I do recommend that you read this guide >> http://malwaretips.com/blogs/how-to-easily-avoid-pc-infections/ << so that you'll learn how to avoid future infections!
Hello Rita,
Press the Windows button+ R key to bring up the Run box, then please type iexplore to start your web browser.Then download the tools from this guide, and run a scan with them.
Alternatively, you can boot your computer in Safe Mode with Command Prompt, and type msconfig in the Command prompt OR if you are using Safe Mode with Networking, in the text box or Run box (windows key+R key), type msconfig.
This should start the Windows System Configuration tool. Go to the Start-up tab, and search for any suspicious or unknown entries (random numbers or letter, ctfmon.exe and other suspicious entries) and uncheck them from start-up.
Hi Again, Thank God I was able to fix it. Thanks HEAPS for the instructions. I was in panic mode.
Hi, I have the same Ukash virus. I have been able to open up in safe mode, however, my icons are now gone so I can’t open internet to download step 2. Sorry I am not so computer savy.
Thanks
thanks for the help.
I have used Method 2, and it worked perfectly!
thank you very very much!! any idea why this is happening?
Guys thanks for the tips. Quite helpful. I was able to get rid of this malicious “Australian police”scam.
Thank you so much for your help……
Blessings and thanks so much for your generous, clear and step specific instructions – we are so grateful – looks like the old laptop will hang in a bit longer! Does make me wonder why I bother with Norton!
Thanks Man, I got done today but all looks fine now, Method 2 is the way to go!!!
thank you thank you thank you !!! you are a LIFESAVER. The virus showed up on my computer an hour ago and is now already gone. can not thank you enough!
Cheers for the clear and simple instructions. I used method 2.
WOW…… Thanks mate, I don’t know hw to say thank you, method 1 worked on my lap top.
Just let me know what can I do for you?
Thanks so much!! When I got the screen locked by the scam ad, I pressed ctfl+alt+del to go to tasks adm and then switched users. After that I followed method 2 and went smoothly. Thanks so much again!! Your’re ace!
Hey I would just like to say thank you so much for your help I am in year twelve and have important files, photos and videos in my laptop and I literally thought they were gone forever thank you so much for your advice and step to step help I really appreciate it :) xx
Thank you so much for your time and effort. I have followed method 2 and up to the stage of scanning using Malware bytes, when finished it said I had no virus on my pc. I know I have the virus but the scan is coming up empty? Why is this? I am now doing a full scan.
Hi there, I’ve used Method 2, however after the scan i received a system restore message: System restore did not complete successfully. Your computer’s system files and settings were not changed. It tells me i can Run System restore again? The was another Restore point i could have chosen, that was at the time of receiving the scam. What do you suggest?
Thankyou very much in advance…
I have been this Virus today. and i found your artical whick is really helpful. but the metho 2 will lose the files that i have. So i try another way. This is only work for computer which has a guest account. this virus will block you loggin ur administrator account but it allow me login in as a guest. I can scan Virus in guest account. delete the virus and the problem sovles. This works for me. hopefull will help u guys.
Method 2 work for me…Thanks.
Thanks man! I hate being held to ransom and your advice did the trick. I owe you a free music lesson
– jimmythelips.com
Thank you mate!!!! This saved my (laptop’s) life!!!
How good is it that there are still people out there that will help you without asking for anything in return
Thanks for posting how to fix this virus I used method 2 and now I have my laptop back
Great work and thank you very much
Ur a lifesaver stelian. When this thing came on my screen i knew it was a scam coz of the media but i thought i lost everything on there including 8 months worth of my babies fotos since yhe day she was born. I’m doing the full scan now. Method 2 worked for me. U have made 1 mummy very happy thank u so much. :)
Used Method 2; worked well!
I presume that the AFP know about this malware; have they any leads as to the perpetrator(s)?
Thank you, COL! :D
Stay safe, and have an awesome life! If you ever need any help with your computer issues, we are always here!!
Stelian, you are bloody awesome. Thought the laptop was shagged, i am a computor no hoper, but i followed your method 2 – method 1 didnt work – and presto, i have my lappy back.
I fix cars for a living, if ever i can help you in return, i will do my best.
From the Snowy Mountains, NSW
Genious solutions. step-by-step…Method 2 worked for me….Fantastic work Thank you….
Thanks! great instructions! Massive relief to get rid of that horrible virus
Thank you so very much! This method is fantastic and you have made it very easy to follow. My computer would not allow me to even access the Advanced Options Menu so that I could choose Safe Mode. Alternatively, I used one of the other user accounts on the computer (suprisingly, these weren’t affected at all), and I followed Step 2 from that point forward.
I really appreciate this help. Thank you Stelian!
Thank you for the clear instructions, so easy to follow, I had to start with the comand prompt as the PC just rebooted when I tried in either of the Safe or Safe with networking modes, worked great using the compand prompt and restore……….and now my PC is back again……..
Worked great. Saved my computer.THANK YOU!
Hello Emma,
There are different versions of this virus, and sometimes it’s missed by some security developers.What antivirus are you using?
thanks so much for this info. You saved us!!!!! Do i need to delete the entry point app to keep the computer safe and how come my anti virus stuff did not stop this?????? From Sydney Australia
THANK YOU…..appreciate the help…..
u did a great job, thanks a lot. I really really appreciated about this.!
Thanks for your efforts it has taken me days to kill this vile virus off. I have Win 8 which is a nightmare to get to safe mode. F8 does not work. Hold shift and keep banging F8 can work but you can spend a long time trying. There are better ways. 1st create a visitor account (before you get this thing) if you only have one account, often the other account is not affected so you can log into it to use the malware suggested. If it’s to late here is what worked for me:
Load to your ‘password screen’. Hold down ‘shift’ click on the OFF bottom (usually bottom right) and click RESTART while holding the SHIFT key. The PC will restart on Recovery page. Choose ADVANCED REPAIR OPTIONS. Then TROUBLE SHOOT. Then ADVANCED OPTIONS. Then WINDOWS STARTUP SETTINGS finally hit RESTART. You will now have the choice of the many options including SAFE MODE. Safe Mode didn’t work for me so I went number 6 COMMAND PROMPT, then I followed the instructions above, restored to a safe time and bingo I could boot normally and let Malwarebytes and then Hitman Pro do their things. Virus DEAD! Thank you for you post it was a great help once I got to the ‘prompt screen’ and it inspired me to find a way there. Hope this helps the Win 8 users.
You are the man. The methods are really clear and easy to follow. The steps are completely fantastic! You made me phew and saved my laptop. Thank you so much.
Thank you thank you I can breath again it worked
Am scanning my computer now hope it works
Thank you ! This showed up n my computer today and now it’s gone after all your help
Thank you so much for your step by step guide on how to remove this threat. I’m doing a restart now so hopefully I’m virus free!
Hello Joseph,
Boot your computer in Safe Mode with Command Prompt, and type msconfig in the Command prompt. This should start the Windows System Configuration tool. Go to the Start-up tab, and search for any suspicious or unknonw entries (random numbers or letter, ctfmon.exe and other suspicious entrie) and uncheck them from start-up. Next boot your computer in regular mode and perform a scan with HitmanPro and Malwarebytes as seen on the guide.
If it still doesn’t work,you’ll need to create a Kaspersky Rescue CD as seen HERE: http://malwaretips.com/blogs/remove-police-trojan/ , on Method 3.
If everything fails, then you’ll need to create an account on our forums and a member of the staff will help you (with more advanced tools) to remove this nasty virus: http://malwaretips.com/Forum-Malware-Removal-Assistance
Good Luck!
I Have used All of the Methods But none of them have worked for me .The Safe mode with command prompt boot dosent open the virus but as there are no back ups on the infected computer i cannot use it .Is there any other ways to remove the virus using the’ safe mode with command prompt ‘ method and if not i need HELP !! as the USB HitMan Pro method dosent work either as it just freezes on the windows boot screen , Please Help !!!!
Addition to method 1: If you know the process that Ukash is using to hostage, you can ctrl-alt-del and Kill Process Tree the item in question. (Mine was skype – a program I don’t even have!)
Once that was done, I was able to stay in Safe Mode With Networking. It made following your guide for cleanup MUCH quicker.
This was the first virus I’ve ever had on my computer. I honestly freaked out. But the ukash thing looked suspicious so I googled it on my phone and came up with this page. I used the first method and my computer works fine now!
Ive never been good with technology but even I could understand this! THANKYOU!!!!!
Thanks for getting back to me Stelian. I’ll give the rescue disk a shot and let you know how I go.
Thank you for this information. It’s 3 in the bloody morning, and I’m beyond annoyed, but at least it’s gone.
Interesting thing I found was that the first time I tapped the power button to restart, the screenlock disappeared and let me save my work. Weird, but useful!
Might be worth adding, this virus will implement its own restore point at the point of infection..
I dont run system restore as I format regularly and try to play with these viruses to find new ways to remove them, and noticed that this guy had in fact created a restore point on the infected machine, even timestamped with the exact time of failure, 16/01 @ 4:00am..
I know neither window or myself created this point, so restorer’s beware on which restore point you choose, Pick one from a few weeks prior to the current date, If you don’t have one that far back, attempt removal via one of the other methods, else you risk re-infection
Worked brilliantly! You are a lifesaver. Many thanks!
Awesome thanks for the help – got rid of this disgusting malware. Thanks again!
Looks good so far thanks, it was on my daughters computer and she had let her anti virus run out.
Thanks again mate.
Thank you, thank you, thank you, thank you, thank you!
Hello Jason,
You’ll need to create a Kaspersky Rescue CD as seen http://malwaretips.com/blogs/remove-ukash-virus/, on Method 3.
If everything fails, then you’ll need to create an account on our forums and a member of the staff will help you (with more advanced tools) to remove this nasty virus: http://malwaretips.com/Forum-Malware-Removal-Assistance
Oh yeah,luis Suarez is epl’s finest!
I commend you sir for taking the time to explain in full detail how to fix this virus.Not only have provided a solution to the problem but you have done it with no affixed cost.Give the man a medal!Look me up if your ever in oz….Would happily shout you a beer or two! Much obliged.
I have a serious problem that I need help with. I have the AFP Ukash virus on my laptop (Compaq V3703 running Windows XP). I cannot start in any of the Safe modes – Ukash actives a couple of seconds or so after restarting and the computer gets locked up once again – so most of the recommendations do not work for me. I then tried using HitmanPro Kickstart to circumvent this, but this also didn’t work. This provided me with the Kickstart boot menu, although this would then go into the Windows Advanced Options Menu (the screen you get after pressing F8). The computer then freezes whether I select start Windows normally or start in Safe Mode.
Oh yeah, I have tried reinstalling Windows XP on the C: drive partition, but this computer has a SATA hard drive which the installer does not recognise. I have tried going into the BIOS to change the SATA driver to IDE as suggested elsewhere, but the BIOS on this machine is very basic and will not allow me to make any changes.
What are my options? I desperately need access to this computer so I can save off a number of files that I have saved on D: drive (Windows is on C:), after which I am happy to reformat. I am not overly tech savvy so would appreciate a simple / lain language fix if one exists. Cheers.
you are a diamond bro… thanks a lot…………
Thanks buddy worked well :)
I used the Hitman kickstart software and followed the two videos. Ihave XP and by following the videos everything worked and the virus was gone, Just to be sure I System restored my pc to an earlier date all seems as it was so a million thanks for the help , : )
Used Method 2. Absolutely brilliant. Thanks.
Messi = Football, Pilici = Computers
Mucho Gracios Mi Amigo!
Thanks for the advice. This insidious webpage locked my daughter laptop – using these steps cleared and unlocked the computer. Can’t imagine how much these mongrels fleece from unsuspecting users who get this. Thanks for your help
Thankyou seems ot have worked appreciate your assistance. ty
Hello Lisa,
This hole page is about how to remove AFP virus…Just read the article! :)
how do i get rid of the scam and can someone please explain the steps to me.
Hello Pat,
You’ll need to created a Kaspersky Rescue CD as seen in this article, on Method 3.
If everything fails, then you’ll need to create an account on our forums and a member of the staff will help you (with more advanced tools) to remove this nasty virus: http://malwaretips.com/Forum-Malware-Removal-Assistance
Sorry must have a later version of the AFP virus it keeps overriding the USB device boot and booting XP from the hard drive even when I set the bios to USB or CD drive and remove the HDD from the boot order, only thing I cand get into is CMD Prompt Window, nothing else works and it won’t see my CD drive or USB stick to launch from there, looks like a reinstall windows tommorrow if AVG support can’t help :/
Mine is strange, got the locked out screen, seemed fishy, so I turned my computer off, turned it on. And everything seems fine – my computer booted up then loaded all the websites etc I had before it got locked.
The scan has picked up some trojans though so hopefully that’s it. Thanks heaps!
Thank you Malware worked for me, I worry about the older people out there who may have limited computer knowledge and fall for this scam.
Method 2 worked for me. I followed the steps diligently and my laptop appears fixed. Thank you for sharing your expertise and knowledge. It is appreciated.
OK GOOD news I updated my MW Bytes and did another full scan and it found 4 RANSOM Trojans and 1 other mall-ware i guess is associated with this terrible virus. So now i have rebooted 2 times and its all back to normal. Thank you so much for your post I really appreciate your time and effort. I also hope my information is helpful to you all. BTW when i said above fake virus i meant fake message. I will say i did sh*t myself and thought WT* but as soon as it said send money i smelled a rat and knew i would be able to find out how to beat them. If i did do anything wrong the police or government wouldn’t tell me about it via my computer LOL they would be knocking on my door. Thanks Again.
Hi, first of all thank you. I Had to use Method 2 cmd with command promt, however it would not let me go to C:\windows\system32 so i did a search and found out i have to do the following command I typed ( cd (space) windows\system32 ENTER) then I typed from there cd restore, waited a few seconds then typed rstrui.exe waited a few seconds and then it worked I was able to perform a system restore.
I then got a ERROR LOADING C:\documents…..\wgsdgsdgsgsd.dll clicked OK then just the windows wall paper screen appeared. I then restarted and went into SAFE MODE again start normally and am now doing a Virus scan to get rid of the stupid fake virus.
Its been over 5 hours of scanning now and I can now get into my Normal windows which is XP but still get that wgsdgsgdgsd.dll error, however i was not able to update the Malwarebytes which i am doing now. If all is good I will do another MW search and if that is good I will not post again. Thanks
i love you, thx heaps!!!
Ignore my previous post – I realised the boot USB it a dual architecture bootable USB HOWEVER, I just did all this as instructed in the videos but after the scanning of the HDD got to about file 10’000 or so, the ransomware white screen took over and nothing else happened. Scan starts, it takes over but is then re-taken over by the ransomware again before it completes… I tried 3 times and same result and at the exact same file scan each time….. Any sugestions ?
Hi,
I have a little problem – all the computers I own and use are 64 Bit but my customers AFP Ransomware infected computer is 32 Bit. As a result, getting a bootable 32 Bit version of the reccommended program HITMAN PRO is pretty hard as you cant run the 32 bit on the 64 bit machine (unless I missed something) ?
I was forced to use an old HDD I had in a box with a 32 Bit image of Vista to boot using the customers computer to then go and download and create the 32 Bit version of the bootable USB drive and then swap the HDD’s, reboot from the 32 bit usb drive and go from there – is there an easier way ?
Thank you Stelian! I’ve used Method no. 1 and worked perfectly! Malwarebytes removed all the viruses from my computer!
Thank you and a Happy New Year from Sydney, Australia!
I have used Method 2, and it worked perfectly!
Thanks Stelian!
thankyou soo much throught i was screwed for a second there