If your computer is locked, and you are seeing a “Huomio! Tietokonenne on tehty vaarattomaksi vähintään yhdestä alla mainituista syistä” notification from POLIISI Tietoverkkorikos Tutkinnan Yksikkö, then your computer is infected with a piece of malware known as Trojan Reveton.
The POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus is distributed through several means. Malicious websites, or legitimate websites that have been compromised, may drop this trojan onto a compromised computer. This drive-by-download often happens surreptitiously. Another method used to propagate this type of malware is spam email containing infected attachments or links to malicious websites. The threat may also be downloaded manually by tricking the user into thinking they are installing a useful piece of software.
The POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus is also prevalent on peer-to-peer file sharing websites and is often packaged with pirated or illegally acquired software.
Once installed on your computer, the POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus will display a bogus notification that pretends to be from POLIISI Tietoverkkorikos Tutkinnan Yksikkö and ICSPA, and states that your computer has been blocked due to it being involved with the distribution of pornographic material, SPAM and copyrighted content.
The POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus will lock you out of your computer and applications, so whenever you’ll try to log on into your Windows operating system or Safe Mode with Networking, it will display instead a lock screen asking you to pay a non-existing fine of 100 Euro in the form of a Ukash or Paysafecard voucher.
Furthermore, to make this alert seem more authentic, this virus also has the ability to access your installed webcam, so that the bogus POLIISI Tietoverkkorikos Tutkinnan Yksikkö notification shows what is happening in the room.
The POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus locks the computer and depending on the user’s current location, displays a localized webpage that covers the entire desktop of the infected computer and demands payment for the supposed possession of illicit material.
![POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus [Image: POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus]](http://malwaretips.com/blogs/wp-content/uploads/2013/05/POLIISI-Tietoverkkorikos-Tutkinnan-Yksikko-virus.jpg)
Cyber criminals often updated the design of this lock screen, however you should always keep in mind that POLIISI Tietoverkkorikos Tutkinnan Yksikkö will never lock down your computer or monitor your online activities.
The message displayed by the threat can be localized depending on the user’s location, with text written in the appropriate language.
POLIISI
Tietoverkkorikos Tutkinnan Yksikkö
Huomio! Tietokonenne on tehty vaarattomaksi vähintään yhdestä alla mainituista syistä.
Te rikotte Tekijänoikeuslakia (Video, Musiikki, Ohjelmisto) ja käytätte laittomasti tai levitätte sisällystä, jonka suojaa tekijänoikeus sillä lailla rikkoen Suomessa rikoslain lakipykålää 128.
Lakipykålå 128 edellyttää 200-500 minimityöpalkkaa suuruista sakkoa tai vapausrangaistusta 2-8 vuotta.
Te olette katsoneet tai levittäneet kiellettyjä pornosisållyksiå (Lapsiporno/Zoofilia). Sillä lailla te olette rikkoneet Suomessa rikoslain lakipykäläå 202. Lakipykålå 202 edellyttää vapausrangaistusta 4-12 vuotta.
Tietokoneenne avulla yritettiin päästä laittomasti tietokoneen tietoihin tai te …
Suomessa rikoslain lakipykalå 208 edellyttää €100.000 suuruista sakkoa ja/tai vapausrangaistusta 4-9 vuotta.
Laiton pääsy yritettiin suorittaa tietokoneestanne teidän tietämättä ja ilman suostumustanne, tietikoneessanne on haittaohjelma, sillä lailla te rikotte lakia ‘Tietokoneen huolittomasta käytöstä”. Rikoslain lakipykälä 210 edellyttää €2000-€8000 suuruista sakkoa. Jos roskapostin tai muun laittoman mainoksen levittäminen suoritettiin tietokoneenne kautta edun saamiseksi teidän tietämättä haittaohjelmat voivat vaikuttaa tietokoneeseen.
Rikoslain lakipykälä 212 edellyttää €250.000 suuruista sakkoa ja/ tai vapausrangaistusta 6 vuotta. Siinä tapauksessa jos toiminnat suoritettiin teidän tietämättä te joudutte edellä mainitun Suomen rikoslain pykälän alaiseksi. Tällä hetkellä teidän henkilöllisyydenne ja osoitteenne selvitetään, 72 tuntien kuluessa teitä vastaan nostetaan rikosasia koskien yhtä tai muutamaa edellä mainittuja pykälää.
Suomen rikoslain korjauksen 28. elokuuta 2012 mukaan tämän lain rikkominen (ensi kerralla eikä toistaiseksi) voi edellyttää ehdollista rangaistusta siinä tapauksessa jos te maksatte sakon valtiolle. Sakot on mandollista maksaa vain 72 tuntien kuluessa rikoksen jälkeen. 72 tuntien kuluttua sakon maksun mandollisuus päättyy ja rikosasia aloitetaan automaattisesti seuraavien 72 tunnissa!
Sakon määrä on €100. Te voitte maksaa laskun Ukash/PaySafeCard.
Kun sakko on maksettu, tietokonenne tulee vapaasti käyttöön 1-72 tunnissa sen jälkeen, kun maksu pääse viralliselle tilille.
The POLIISI Tietoverkkorikos Tutkinnan Yksikkö lock screen is a scam, and you should ignore any alerts that this malicious software might generate.
Under no circumstance should you send any Ukash or Paysafecard code to these cyber criminals, and if you have, you can should request a refund, stating that you are the victim of a computer virus and scam.
POLIISI Tietoverkkorikos Tutkinnan Yksikkö lock screen – Virus Removal Guide
STEP 1: Remove POLIISI Tietoverkkorikos Tutkinnan Yksikkö lock screen from your computer
POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus has modified your Windows registry and added its malicious files to run at start-up, so whenever you’re trying to boot your computer it will launch instead its bogus notification.To remove these malicious changes, we can use any of the below methods :
Method 1: Start your computer in Safe Mode with Networking and scan for malware
Some variants of POLIISI Tietoverkkorikos Tutkinnan Yksikkö Ukash virus will allow the users to start the infected computer in Safe Mode with Networking without displaying the bogus lock screen. In this first method, we will try to start the computer in Safe Mode with Networking and then scan for malware to remove the malicious files.
- Remove all floppy disks, CDs, and DVDs from your computer, and then restart your computer.
- Press and hold the F8 key as your computer restarts.Please keep in mind that you need to press the F8 key before the Windows start-up logo appears.
Note: With some computers, if you press and hold a key as the computer is booting you will get a stuck key message. If this occurs, instead of pressing and holding the “F8 key”, tap the “F8 key” continuously until you get the Advanced Boot Options screen. - On the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.
![Remove POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus (Removal Guide) 2 [Image: Safe Mode with Networking]](//malwaretips.com/blogs/wp-content/uploads/2013/01/safemode.jpg)
- If your computer has started in Safe Mode with Networking, you’ll need to perform a system scan (as seen on STEP 2) with Malwarebytes Anti-Malware and HitmanPro to remove the malicious files from your machine.
IF the POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus didn’t allow you to start the computer in Safe Mode with Networking,you’ll need to follow Method 2 to get rid of its lock screen.
Method 2: Restore Windows to a previous state using System Restore
System Restore can return your computer system files and programs to a time when everything was working fine, so we will try to use this Windows feature to get rid of POLIISI Tietoverkkorikos Tutkinnan Yksikkö lock screen.
- Restart your computer, and then press and hold F8 during the initial startup to start your computer in safe mode with a Command prompt.
Note: With some computers, if you press and hold a key as the computer is booting you will get a stuck key message. If this occurs, instead of pressing and holding the “F8 key”, tap the “F8 key” continuously until you get the Advanced Boot Options screen. - Use the arrow keys to select the Safe mode with a Command prompt option.
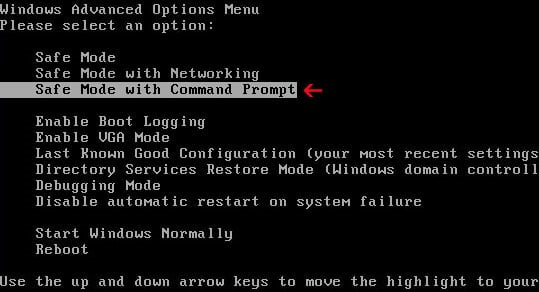
- At the command prompt, type cd restore, and then press ENTER.
Next,we will type rstrui.exe , and then press ENTER.Alternatively, if you are using Windows Vista, 7 and 8, you can just type : C:\windows\system32\rstrui.exe , and press ENTER.
If you are using Windows XP, you will need to type C:\windows\system32\restore\rstrui.exe, and then press ENTER.
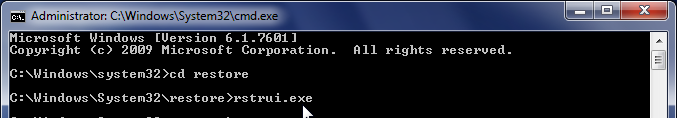
- The System Restore utility will start, and you’ll need to select a restore point previous to this infection.
- After System Restore has completed its task, you should be able to boot in Windows normal mode, and perform a system scan (as seen on STEP 2) with Malwarebytes Anti-Malware and HitmanPro to remove the malicious files from your machine.
IF the POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus didn’t allow you to restore your computer to a previous point, you’ll need to follow Method 3 to get rid of its screen lock.
Method 3: Remove POLIISI Tietoverkkorikos Tutkinnan Yksikkö lock screen with msconfig utility
When your computer was infected with the POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus, this trojan has set a its malicious files to start whenever your computer is booting. IF you didn’t have a system restore point, we can use msconfig to remove the malicious startup entries.
- While your computer is in Safe Mode with Command Prompt, type msconfig to start the Windows System Configuration utility.
![Type msconfig in the Command prompt [Image: Type msconfig in the Command prompt]](//malwaretips.com/blogs/wp-content/uploads/2013/02/command-prompt-start-msconfig.jpg)
- Click on the Startup tab, then search for any suspicious or unknonw entries (random numbers or letters, ctfmon.exe, and other suspicious or unknown entries), and unckech them from startup, then click on OK.
This will stop the POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus from starting with Windows, however it won’t remove the malicious files from your computer.
![Uncheck any suspicious entries from start-up [Image: Uncheck any suspicious entries from start-up]](//malwaretips.com/blogs/wp-content/uploads/2013/02/msconfig-remove-startup-item.jpg)
- Type shutdown /r in the command prompt to restart your computer, then perform a scan with Malwarebytes Anti-Malware and HitmanPro as seen on STEP 2.
IF the POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus didn’t allow you to start the computer in Safe Mode with Command Prompt you’ll need to follow Method 4 to get rid of its screen lock.
Method 4: Remove POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus with HitmanPro Kickstart
IF you couldn’t boot into Safe Mode with Command Prompt or didn’t have a System Restore point on your machine, we can use HitmanPro Kickstart to bypass this infection, and access your computer to scan it for malware.
- We will need to create a HitmanPro Kickstart USB flash drive,so while you are using a “clean” (non-infected) computer, download HitmanPro from the below link.
HITMANPRO DOWNLOAD LINK (This link will open a download page in a new window from where you can download HitmanPro) - Insert your USB flash drive into your computer and follow the instructions from the below video:
- After you have create the HitmanPro Kickstart USB flash drive, you can insert this USB drive into the infected machine and start your computer.
- Once the computer starts, repeatedly tap the F11 key (on some machines its F10 or F2),which should bring up the Boot Menu, from there you can select to boot from your USB.
Next,you’ll need to perform a system scan with HitmanPro as see in the below video:
- After HitmanPro Kickstart has completed its task,you should be able to boot in Windows normal mode,from there you’ll need to perform a system scan (as seen on STEP 2) with Malwarebytes Anti-Malware and HitmanPro to remove the malicious files from your machine.
STEP 2: Remove POLIISI Tietoverkkorikos Tutkinnan Yksikkö malicious files from your computer
Run a computer scan with Malwarebytes Anti-Malware Free
- You can download Malwarebytes Anti-Malware Free from the below link,then double click on it to install this program.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK(This link will open a download page in a new window from where you can download Malwarebytes Anti-Malware Free) - When the installation begins, keep following the prompts in order to continue with the setup process.
DO NOT make any changes to default settings and when the program has finished installing, make sure you leave both the Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware checked,then click on the Finish button.
![Malwarebytes Anti-Malware final installation screen [Image: Malwarebytes Anti-Malware final installation screen]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
- On the Scanner tab,select Perform quick scan and then click on the Scan button to start scanning your computer.
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)
- Malwarebytes’ Anti-Malware will now start scanning your computer for POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus as shown below.
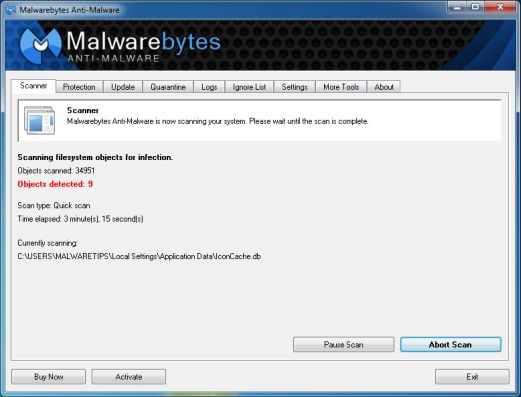
- When the Malwarebytes scan will be completed,click on Show Result.
![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
- You will now be presented with a screen showing you the malware infections that Malwarebytes’ Anti-Malware has detected.Please note that the infections found may be different than what is shown in the image.Make sure that everything is Checked (ticked) and click on the Remove Selected button.
![Click on Remove Selected to get rid of [Image:Malwarebytes removing virus]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)
- After your computer will restart in Normal mode, open Malwarebytes Anti-Malware and perform a Full System scan to verify that there are no remaining threats
Run a computer scan with HitmanPro
- Download HitmanPro from the below link,then double click on it to start this program.
HITMANPRO DOWNLOAD LINK (This link will open a new web page from where you can download HitmanPro)
IF you are experiencing problems while trying to start HitmanPro, you can use the Force Breach mode.To start HitmanPro in Force Breach mode, hold down the left CTRL-key when you start HitmanPro and all non-essential processes are terminated, including the malware process. (How to start HitmanPro in Force Breach mode – Video) - HitmanPro will start and you’ll need to follow the prompts (by clicking on the Next button) to start a system scan with this program.
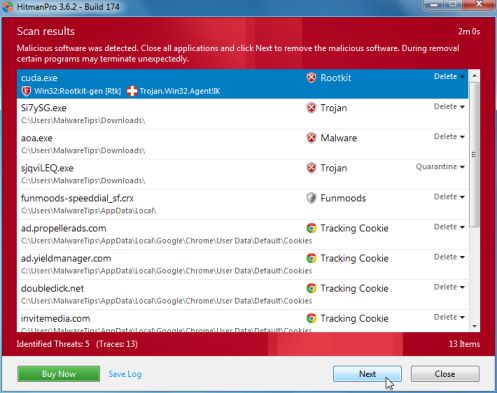
- HitmanPro will start scanning your computer for POLIISI Tietoverkkorikos Tutkinnan Yksikkö malicious files as seen in the image below.
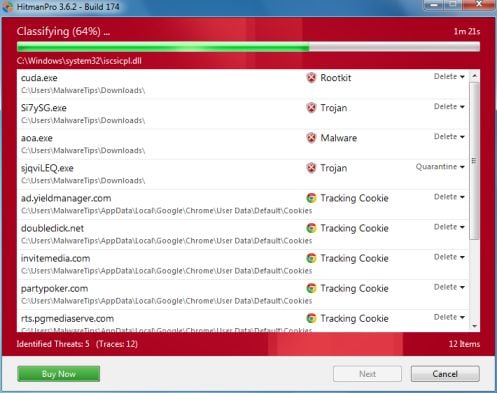
- Once the scan is complete,you’ll see a screen which will display all the infected files that this utility has detected, and you’ll need to click on Next to remove these malicious files.
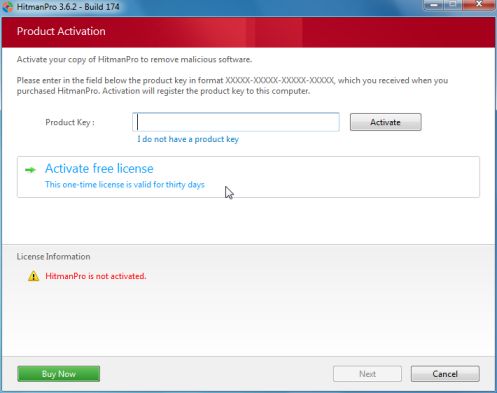
- Click Activate free license to start the free 30 days trial and remove all the malicious files from your computer.

![Remove POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus (Removal Guide) 1 [Image: POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus]](https://malwaretips.com/blogs/wp-content/uploads/2013/05/POLIISI-Tietoverkkorikos-Tutkinnan-Yksikko-virus.jpg)
![Remove POLIISI Tietoverkkorikos Tutkinnan Yksikkö virus (Removal Guide) 2 [Image: Safe Mode with Networking]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/safemode.jpg)



![Type msconfig in the Command prompt [Image: Type msconfig in the Command prompt]](http://malwaretips.com/blogs/wp-content/uploads/2013/02/command-prompt-start-msconfig.jpg)
![Uncheck any suspicious entries from start-up [Image: Uncheck any suspicious entries from start-up]](http://malwaretips.com/blogs/wp-content/uploads/2013/02/msconfig-remove-startup-item.jpg)
![Malwarebytes Anti-Malware final installation screen [Image: Malwarebytes Anti-Malware final installation screen]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)

![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
![Click on Remove Selected to get rid of [Image:Malwarebytes removing virus]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)