If your web browser is constantly being redirected to the Ad.adserverplus.com site, then it is possible that you have an adware program installed on your computer.

This ad.adserverplus.com redirect is usually caused by adware installed on your computer. These adware programs are bundled with other free software that you download off of the Internet. Unfortunately, some free downloads do not adequately disclose that other software will also be installed and you may find that you have installed adware without your knowledge.
Once this malicious program is installed, whenever you will browse the Internet, an ad from Ad.adserverplus.com will randomly pop-up.
These ads are aimed to promote the installation of additional questionable content including web browser toolbars, optimization utilities and other products, all so the adware publisher can generate pay-per-click revenue.
When infected with this adware program, other common symptoms include:
- Advertising banners are injected with the web pages that you are visiting.
- Random web page text is turned into hyperlinks.
- Browser popups appear which recommend fake updates or other software.
- Other unwanted adware programs might get installed without the user’s knowledge.
Always opt for the custom installation and deselect anything that is not familiar, especially optional software that you never wanted to download and install in the first place. It goes without saying that you should not install software that you don’t trust.
How to remove Ad.adserverplus.com pop-ups (Virus Removal Guide)
Please perform all the steps in the correct order. If you have any questions or doubt at any point, STOP and ask for our assistance.
- STEP 1: Use Zemana AntiMalware Portable to remove adware
- STEP 2: Scan and clean your computer with Malwarebytes
- STEP 3: Double-check for malicious programs with HitmanPro
- (OPTIONAL) STEP 4: Reset your browser to default settings
STEP 1: Use Zemana AntiMalware Portable to remove adware
Zemana AntiMalware Portable is a free utility that will scan your computer for the Ad.adserverplus.com pop-up ads and other malicious programs.
- You can download Zemana AntiMalware Portable from the below link:
ZEMANA ANTIMALWARE PORTABLE DOWNLOAD LINK (This link will start the download of “Zemana AntiMalware Portable”) - Double-click on the file named “Zemana.AntiMalware.Portable” to perform a system scan with Zemana AntiMalware Free.
You may be presented with a User Account Control dialog asking you if you want to run this program. If this happens, you should click “Yes” to allow Zemana AntiMalware to run.
- When Zemana AntiMalware will start, click on the “Scan” button to perform a system scan.
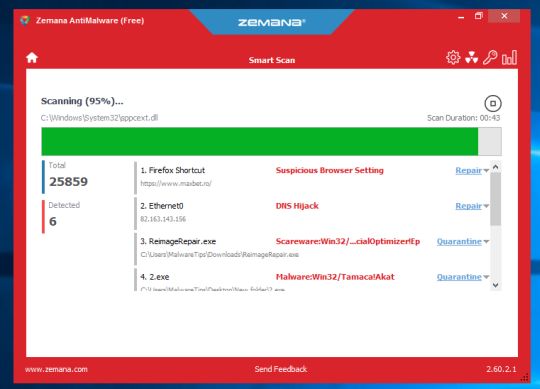
- Zemana AntiMalware will now scan your computer for malicious programs. This process can take up to 10 minutes.
- When Zemana has finished finished scanning it will show a screen that displays any malware that has been detected. To remove all the malicious files, click on the “Next” button.
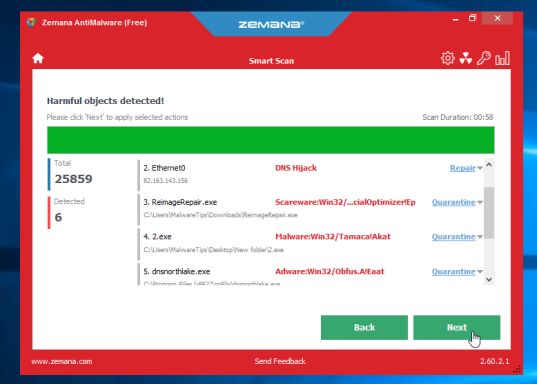
Zemana AntiMalware will now start to remove all the malicious programs from your computer. When the process is complete, you can close Zemana AntiMalware and continue with the rest of the instructions.
STEP 2: Scan and clean your computer with Malwarebytes
Malwarebytes is a powerful on-demand scanner which should remove the Ad.adserverplus.com redirect from your machine. It is important to note that Malwarebytes will run alongside antivirus software without conflicts.
- You can download download Malwarebytes from the below link.
MALWAREBYTES DOWNLOAD LINK (This link open a new page from where you can download “Malwarebytes”) - When Malwarebytes has finished downloading, double-click on the “mb3-setup-consumer” file to install Malwarebytes on your computer.
You may be presented with an User Account Control pop-up asking if you want to allow Malwarebytes to make changes to your device. If this happens, you should click “Yes” to continue with the installation.
- When the Malwarebytes installation begins, you will see the Malwarebytes Setup Wizard which will guide you through the installation process.
To install Malwarebytes on your machine, keep following the prompts by clicking the “Next” button.
- Once installed, Malwarebytes will automatically start and update the antivirus database. To start a system scan you can click on the “Scan Now” button.
- Malwarebytes will now start scanning your computer for malicious programs.
This process can take a few minutes, so we suggest you do something else and periodically check on the status of the scan to see when it is finished.
- When the scan has completed, you will be presented with a screen showing the malware infections that Malwarebytes has detected.
To remove the malicious programs that Malwarebytes has found, click on the “Quarantine Selected” button.
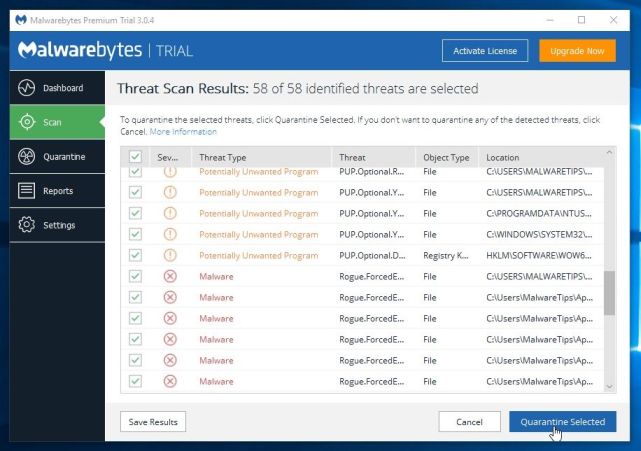
- Malwarebytes will now quarantine all the malicious files and registry keys that it has found.
To complete the malware removal process, Malwarebytes may ask you to restart your computer.
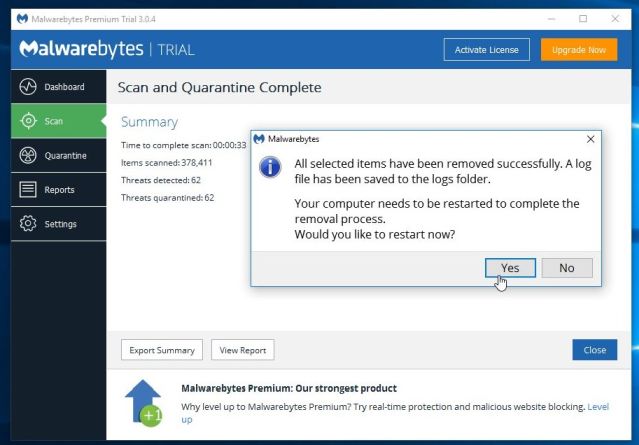
When the malware removal process is complete, you can close Malwarebytes and continue with the rest of the instructions.
STEP 3: Double-check for malicious programs with HitmanPro
HitmanPro can find and remove malware, adware, bots, and other threats that even the best antivirus suite can oftentimes miss. HitmanPro is designed to run alongside your antivirus suite, firewall, and other security tools.
- You can download HitmanPro from the below link:
HITMANPRO DOWNLOAD LINK (This link will open a new web page from where you can download “HitmanPro”) - When HitmanPro has finished downloading, double-click on the “hitmanpro” file to install this program on your computer.

You may be presented with an User Account Control pop-up asking if you want to allow HitmanPro to make changes to your device. If this happens, you should click “Yes” to continue with the installation.
- When the program starts you will be presented with the start screen as shown below. Now click on the Next button to continue with the scan process.
- HitmanPro will now begin to scan your computer for malware.
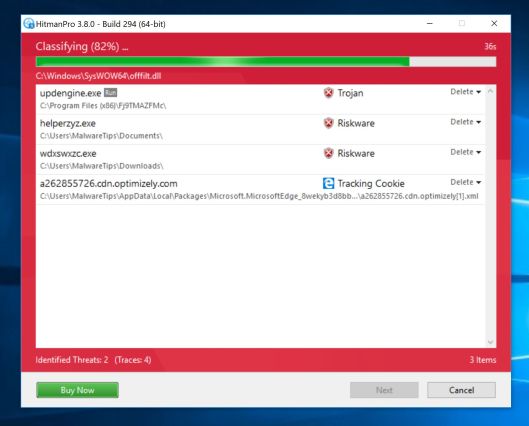
- When it has finished it will display a list of all the malware that the program found as shown in the image below. Click on the “Next” button, to remove malware.

- Click on the “Activate free license” button to begin the free 30 days trial, and remove all the malicious files from your computer.
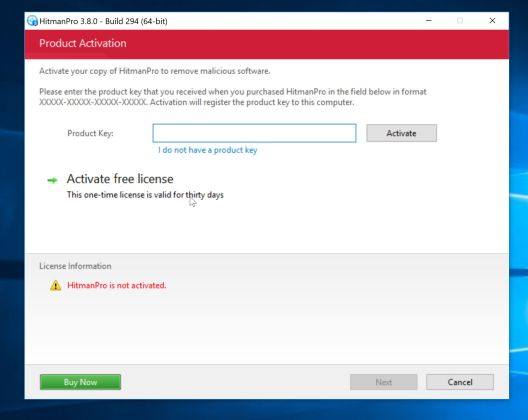
When the process is complete, you can close HitmanPro and continue with the rest of the instructions.
(OPTIONAL) STEP 4: Reset your browser to default settings
This step should be performed only if your issues have not been solved by the previous steps.
Google Chrome
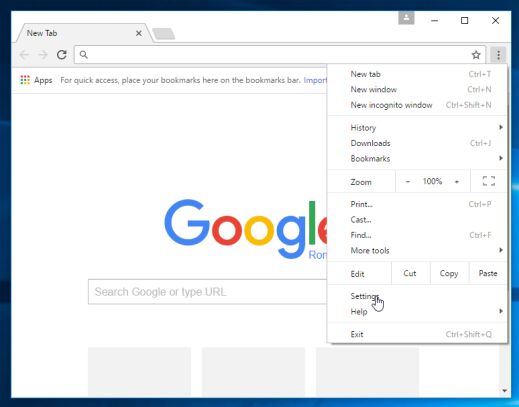
- Click on Chrome’s main menu button, represented by three horizontal lines. When the drop-down menu appears, select the option labeled Settings.
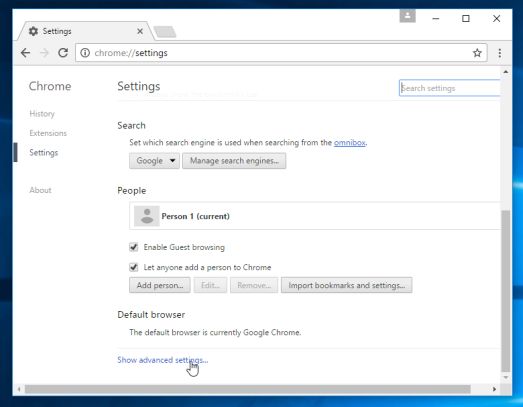
- Chrome’s Settings should now be displayed in a new tab or window, depending on your configuration. Next, scroll to the bottom of the page and click on the Show advanced settings link (as seen in the below example).
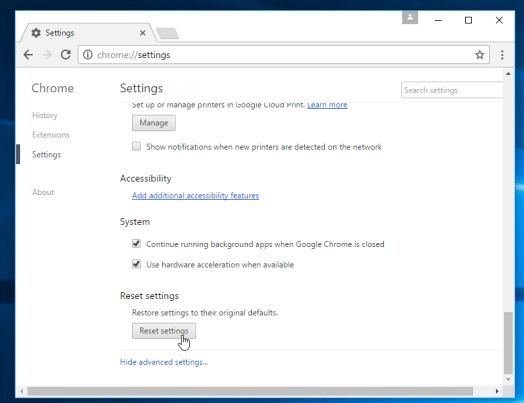
- Chrome’s advanced Settings should now be displayed. Scroll down until the Reset browser settings section is visible, as shown in the example below. Next, click on the Reset browser settings button.
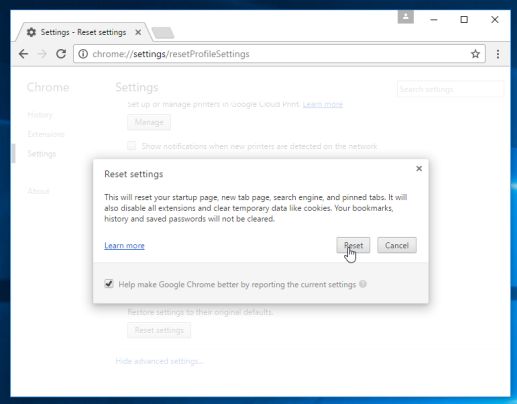
- A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue on with the reset process. To complete the restoration process, click on the Reset button.
Internet Explorer
- Open Internet Explorer, click on the “gear icon” in the upper right part of your browser, then click again on Internet Options.
![Click on the Gear Icon then on Internet Options [Image: Internet Options in Internet Explorer]](https://malwaretips.com/blogs/wp-content/uploads/2014/03/Internet-Options-Internet-Explorer.jpg)
- In the “Internet Options” dialog box, click on the “Advanced” tab, then click on the “Reset” button.
![In the Advanced tab click on the Reset button [Image: Reset Internet Explorer]](https://malwaretips.com/blogs/wp-content/uploads/2014/03/Reset-Internet-Explorer.jpg)
- In the “Reset Internet Explorer settings” section, select the “Delete personal settings” check box, then click on “Reset” button.
![Click on the Reset button to revert IE to its default settings [Image: Reset Internet Explorer to its default settings]](https://malwaretips.com/blogs/wp-content/uploads/2014/03/reset-button-Internet-Explorer.jpg)
- When Internet Explorer has completed its task, click on the “Close” button in the confirmation dialogue box. You will now need to close your browser, and then you can open Internet Explorer again.
![Click on the Close button [Image Reset Internet Explorer settings]](https://malwaretips.com/blogs/wp-content/uploads/2014/03/Close-button-Reset.jpg)
Mozilla Firefox
- In the upper-right corner of the Firefox window, click the Firefox menu button, then click on the “Help”
![Firefox Help button [Image: Firefox Help button]](https://malwaretips.com/blogs/wp-content/uploads/2014/04/Firefox-Help.png) button.
button.
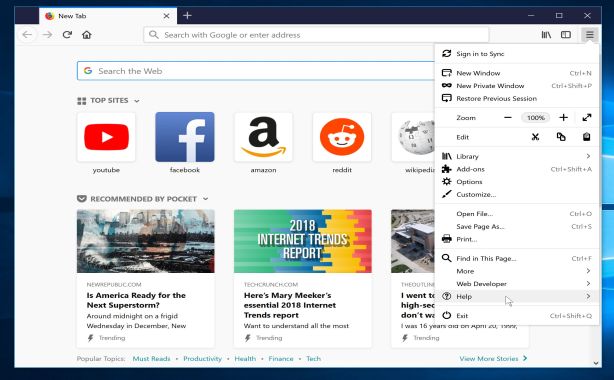
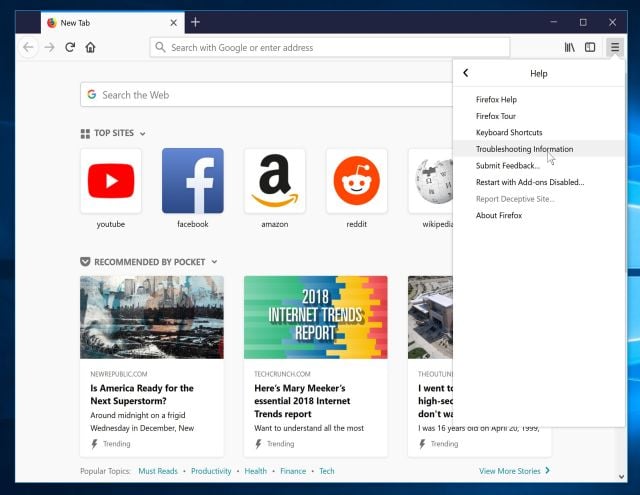
- From the Help menu, choose Troubleshooting Information.
If you’re unable to access the Help menu, type about:support in your address bar to bring up the Troubleshooting information page.
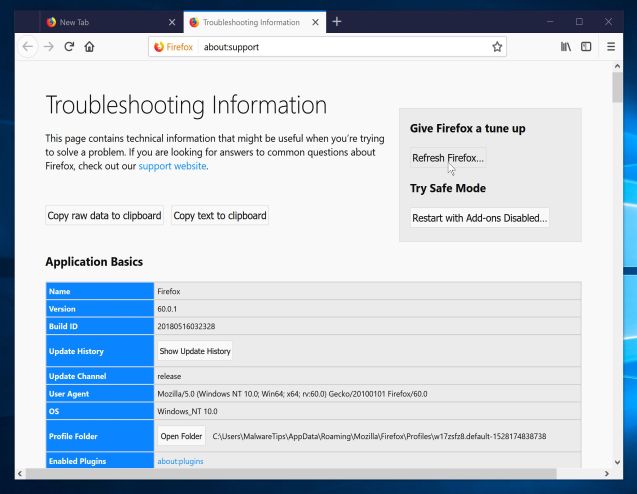
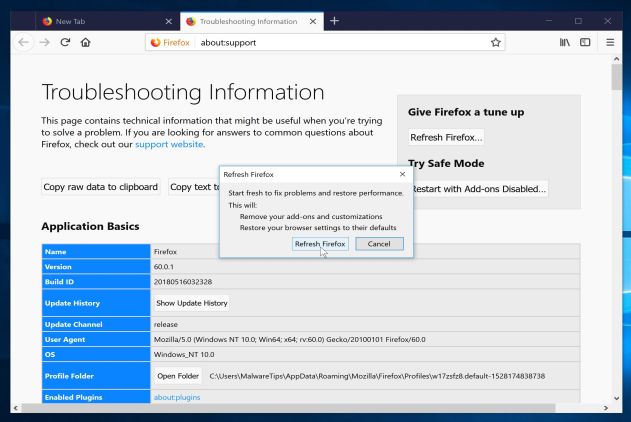
- Click the “Refresh Firefox” button in the upper-right corner of the “Troubleshooting Information” page.
- To continue, click on the “Refresh Firefox” button in the new confirmation window that opens.
- Firefox will close itself and will revert to its default settings. When it’s done, a window will list the information that was imported. Click on the “Finish“.


