A fraudulent online campaign falsely claiming Apple is gifting free MacBook laptops to random social media users has infiltrated platforms through manipulated advertisements and questionable external websites. However, the supposed giveaway actually intends stealing personal information and money rather than reasonable contest generosity or inventory liquidation.
- Overview of the fake Apple MacBook Giveaway Scam
- How Users Get Deceived By Fake Apple MacBook Giveaways
- Spotting the MacBook Giveaway Scam Across Major Social Apps
- Red Flags Exposing the Fake MacBook Giveaway Websites
- What to Do If You Are A Victim of The Apple MacBook Giveaway Scam
- Spotting The Apple MacBook Promotion Scams
- Frequently Asked Questions About the Viral Fake Apple MacBook Giveaway
- The Bottom Line on Avoiding the MacBook Social Media Scam
This article exposes the deceitful scam strategies step-by-step alongside guidance protecting yourself from potential damages.
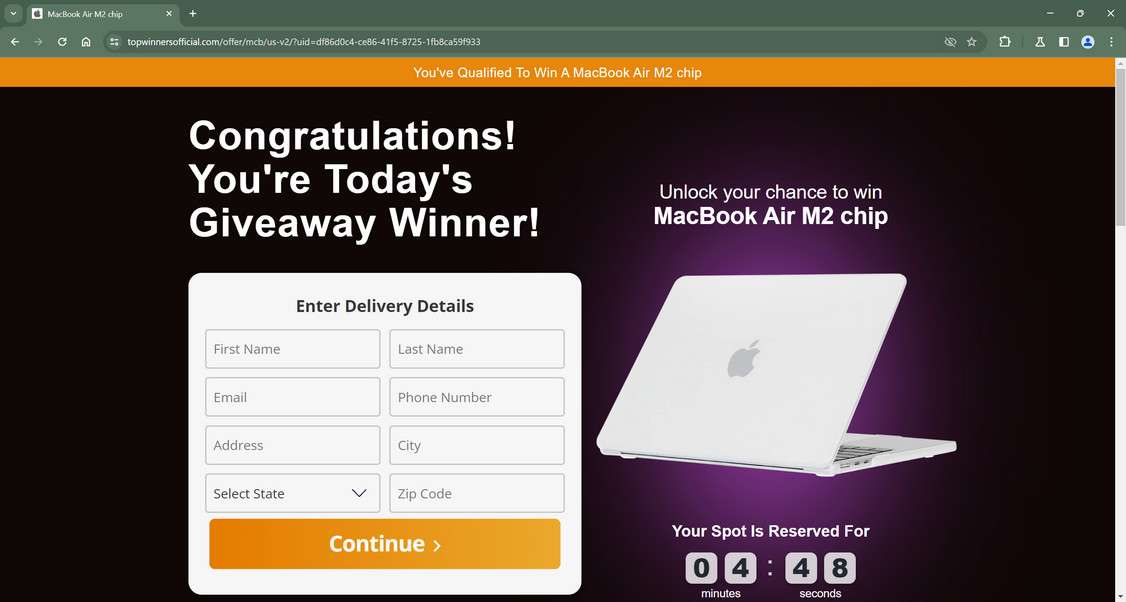
Overview of the fake Apple MacBook Giveaway Scam
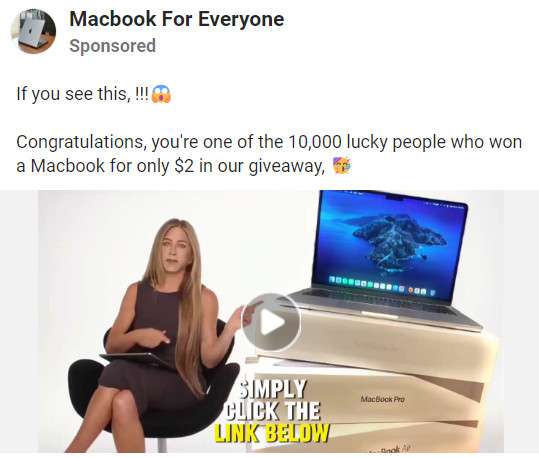
The increasingly common, yet fake, Apple MacBook giveaway scam starts by circulating online ads featuring exciting headlines like:
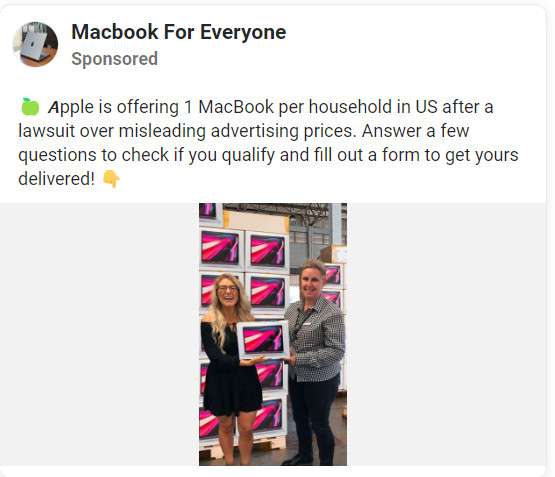
“Apple is offering 1 MacBook per household in US after a lawsuit over misleading advertising prices. Answer a few questions to check if you qualify and fill out a form to get yours delivered.”

Hopeful social media users then click embedded links or tap targeted advertisements expecting official Apple contest pages. However, redirects route victims through a series of elaborate external phishing websites like “inducive.info” and”topwinnersofficial.com” completely unassociated with Apple.
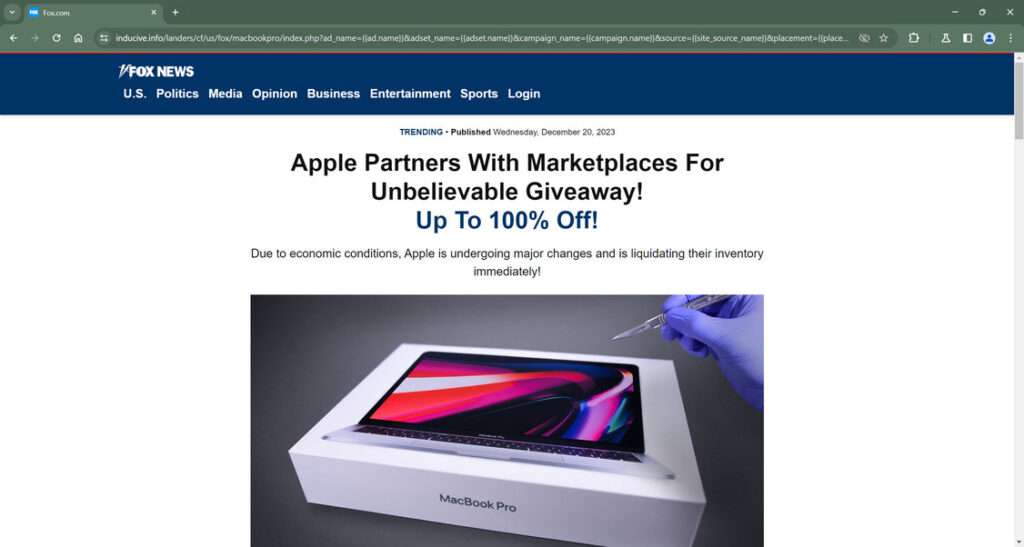
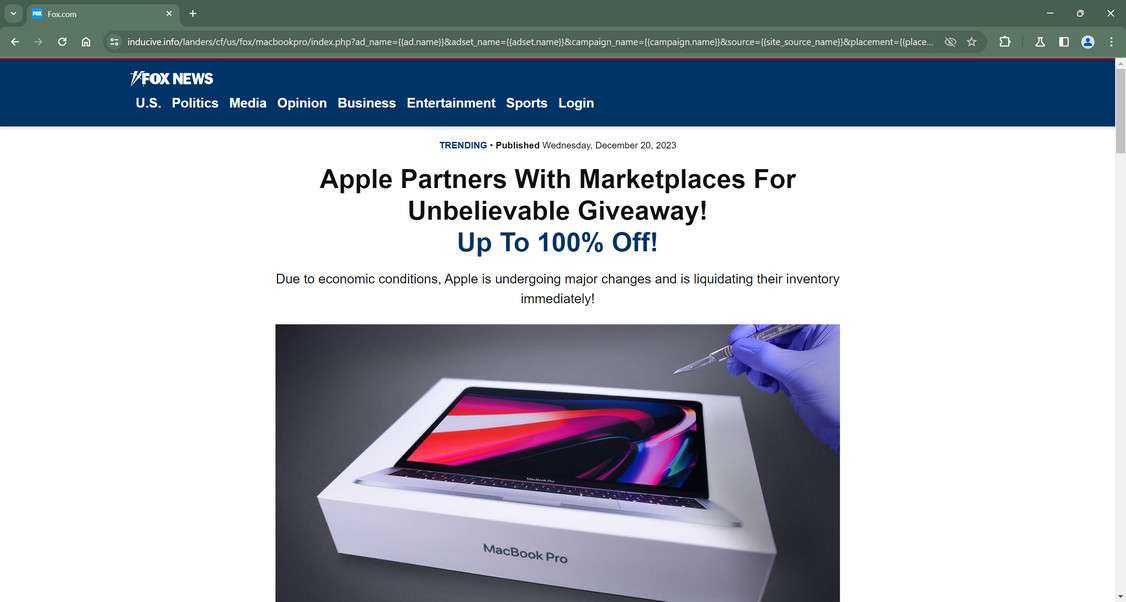
Decoy portal pages prominently display reputable news site logos like Fox, CNN or People Magazine alongside Apple imagery. This aims lending initial legitimacy justifying later requests for sensitive personal information rather than raising skepticism. Website headers blare:
“Apple Partners With Marketplaces For Unbelievable MacBook Giveaway! Up To 100% Off!”
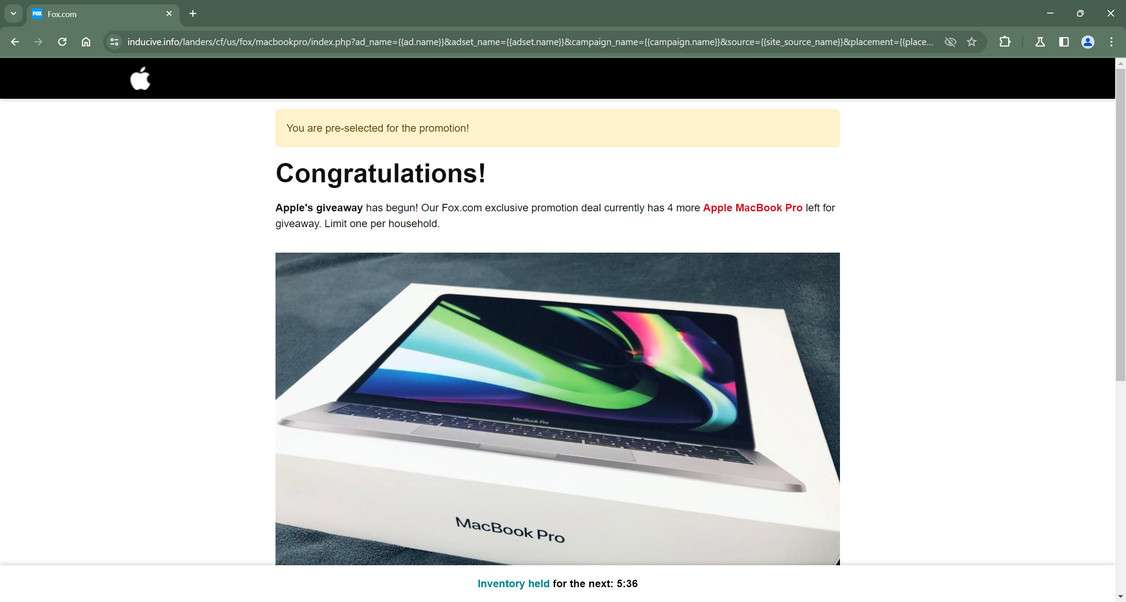
After scrolling through fake inventory liquidation cover stories and customer testimonials, visitors eventually reach customized order forms promising delivery of free laptops solely pending small $6.95 upfront shipping/handling fees.
However, buried fine print passages encased within lengthy terms and conditions associated with order forms actually bind victims to expensive recurring monthly subscription charges exceeding $100 rather than one-time voucher payments expected.
In the end, high value Apple products are never dispatched to filling contest entries. But victims’ compromised information enables scammers inflicting financial damages through underground dark web data sale channels.
How Users Get Deceived By Fake Apple MacBook Giveaways
The fraudulent Apple MacBook giveaway conducts highly coordinated strategies luring victims systematically through the following deceptive process:
Step 1) Entice With Misleading Social Media Advertisements
The scam starts by circulating fake ads across social platforms urgently insisting Apple urgently liquidates inventory through unbelievable deals benefiting random followers upgrading devices essentially free.
Step 2) Build Believability Through Elaborate External Portal Pages
Clicking on social media links or videos reroutes viewers outside platforms to elaborate phishing portal pages like “foxlimiteds.com” impersonating trusted news brands. These feature Apple’s iconic logo and imagery while deploying additional manipulation triggers overcoming initial skepticism.
Step 3) Fabricate Urgent Situational Context Encouraging Hasty Actions
False inventory liquidation narratives lend believable context rationalizing extraordinary free device offers tied to reasonable request small $6.95 delivery reimbursements giving the deal perceived credibility.
Step 4) Pressure Users Through Social Proof and Scarcity Triggers
Fake customer reviews and claims of extreme limited supply bypass critical thinking and compel desired actions reactively seeking scarce free goods rather than questioning abnormalities.
Step 5) Discreetly Collect Financial Information and Personal Data
When visitors attempt securing devices through order forms, questions conveniently require private input they’d never normally provide random third-parties.
Step 6) Disclose Monthly Subscription and Service Charges Hidden in Fine Print
Buried terms and conditions disclosures reveal victims actually consent steep recurring monthly charges exceeding $100 rather than reasonable one-time product voucher costs estimated around $10.
Step 7) Continuously Profit From Stolen Data and Unauthorized Billing
With access to compromised confidential information, recurring credit charges activate alongside potentials for reselling data through unregulated dark web channels – each inflicting long-term damages through manipulation or identity theft.
In summary, the fake celebrity MacBook giveaway ensnares social media users through emotional manipulation, urgency triggers, and concealed terms disclosing alternative money-making objectives unrelated to reasonably donation expensive electronics.
Spotting the MacBook Giveaway Scam Across Major Social Apps
The supposed Apple MacBook giveaway flows through platforms like Facebook, Instagram and TikTok using manipulated content and psychological tactics deceiving users.
Let’s review what signals commonly expose the questionable laptop promotion on each network.
Facebook Tactics Exploiting the MacBook Giveaway
Exercise caution towards Facebook posts exhibiting these common deception indicators:
- Video ads using deepfake celebrity imagery endorsing massive but unlikely MacBook donations
- Links in unpaid posts and descriptions rerouting outside Facebook to unvetted domains
- Profiles spreading hype demonstrate very limited previous activities
- Hard-sell language pressures readers to share, click and act before purported deadlines
- Comment sections emphasize contest excitement rather than reasonably questioning abnormalities
For example, video spots insisting Jennifer Aniston helped secure Apple device gifts deserves reasonable skepticism before sharing or clicking.
Shady Instagram Approaches Promoting Fake MacBook Contests
Analyze these questionable Instagram elements connected to free MacBook offers:
- Deepfaked celebrities tagged endorsing unauthorized giveaways
- Captions URGE fast actions through risky external links to “claim” prizes
- Profiles discuss only contest details without expected personal sharing
- Suspicious visual filtering applied to imagery luring herd mentality
- Locations list foreign countries unrelated to known U.S. corporate operations
Specifically, any Instagram account using an edited video of Tim Cook promising to giveaway MacBooks deserves reasonable vetting before proceeding.
Manipulated TikTok Videos Driving Fake MacBook Hype
Apply extra scrutiny towards viral TikTok spots exhibiting these problems:
- Complex edits depicting Apple leadership endorsing massive but unlikely contests
- Links in captions route clicking traffic outside platform protections
- Uniformly positive comments focused exclusively on urgent participation
- Strong calls-to-action incentivize reacting without properly vetting
If you spot oddly persuasive videos diverting outside links or caution throws aside chasing extraordinary free gifts, trust instinct and independently verify authenticity.
Across all social channels, supposed celebrity and brand affiliated opportunities sacrificing little for substantial personal gain deserve deeper inspection before participation protecting oneself from preventable privacy damages. What seems too good often is until proven otherwise. Apply reasoned skepticism.
Red Flags Exposing the Fake MacBook Giveaway Websites
In coordination with manipulated social media posts, the celebrity laptop scam also leverages a network of deceitful external websites helping lend credibility and justifying later requests for sensitive personal user information.
Let’s review several consistent suspicious website patterns exposing the underlying scam despite convincing first impressions.
Co-opting Reputations of Trusted News Brands Without Consent
Rather than building sites credibility from scratch, fraudulent MacBook operators impersonate respected news authorities by featuring established media logos like Fox News, CNN or People Magazine without permission. This tactic eases initial skepticism by assuming previous journalistic review for authenticity.
Fabricating Situational Contexts Encouraging Desired Actions
Scammers interweave elaborate fake narratives around supply chain issues, discontinued products or settlement deals justifying extraordinary free device offers and reasonable requests for minor shipping reimbursements. But further scrutiny exposes contradictions challenging legitimacy.
Weaving Fake Social Proof Through Suspicious Customer Reviews
Sprinkled throughout the hype, suspicious accounts with very limited platform histories lend perceived credibility implying they successfully participated by securing heavily discounted or free MacBook laptops themselves already. But their manufactured advocacy aims lowering skepticism guards for improved scam conversion rates.
Burying FinancialTerms and Conditions in Fine Print
While prominent graphics prompt urgent participation scarcely reviewing rules, buried terms disclosures reveal victims registering for expensive $100+ monthly subscription charges rather than reasonable one-time coupon shipment fees securing “free” devices. This demonstrate intention eliciting finances deceptively versus transparency.
In summary, unbelievable holiday sweepstakes offers tied closely to respected brands require cautious inspection empowering individuals avoiding preventable privacy and financial damages. Look past emotional hooks and facades allowing objective logic reveal ulterior motives obscured from plain view by scammers.
What to Do If You Are A Victim of The Apple MacBook Giveaway Scam
If you now face unauthorized recurring charges or services after attempting questionable giveaways, immediately take action:
Step 1) Alert Financial Institutions About Detected Fraud
Contact banking providers regarding recent Apple scam discovery tied to unexpected account charges from organizations lacking proper authorization. Ask about fraud investigation and provisional reimbursements during disputes.
Step 2) Attempt Canceling Related Subscriptions
Collect customer service information from deceptive monthly billing statements. Call providers clearly revoking any past payment authorizations now aware those were obtained under false pretenses rather than reasonable giveaway terms pitched initially. Record confirmation details should charges persist.
Step 3) Enable Extra Account Protection Measures
Since compromised information retains lasting vulnerabilities, immediately update passwords and security answers while enabling robust multi-factor authentication across logins. Turn on credit monitoring alerting suspicious activities requiring quick intervention as well.
Step 4) Submit Actionable Complaint Reports to Relevant Fraud Agencies
File detailed reports about scam portals, product claims and damages incurred under false pretenses with both government and third-party consumer protection groups. Such filings support investigating repeat offenders warranting legal intervention assisting all negatively impacted victims.
Spotting The Apple MacBook Promotion Scams
Several consistent red flags help reveal when a too-good-to-be-true viral MacBook deal likely intends facilitating financial theft rather than contest generosity:
1. Unauthorized Branding Use Without Attribution
- Real Apple giveaways appropriately credit company without using iconic logos deceitfully.
2. Situational Urgency Tactics Encouraging Haste
- Reasonable contests allow proper entry vetting rather than reactively chasing purportedly fleeting ultra-scarce free inventory.
3. Disproportionate Requested Fees
- $6.95 seems incommensurate reconciling “free” thousand dollar machine delivery logistics.
4. Comment Irregularities
- Suspicious profiles with limited activities uniformly praise giveaways rather than reasonably questioning abnormalities.
5. Restricted External Website Disclosures
- Obfuscated “terms and conditions” burying unrelated monthly charges suggest intention eliciting finances deceptively.
By recognizing these patterns early, individuals avoid compromising into preventable damages chasing unbelievable free gifts down detour paths ending exploitation rather than sincerity. Apply skepticism before acting.
Frequently Asked Questions About the Viral Fake Apple MacBook Giveaway
Find answers below to the most commonly searched questions regarding supposed Apple sponsored MacBook holiday giveaways promotions currently circulating social media and questionable external websites.
Is the Apple MacBook giveaway real or fake?
Despite advertisements featuring exciting inventory liquidation narratives and video footage seeming to show Apple leadership endorsing giveaways, the entire campaign constitutes an elaborate scam effort aiming to phish peoples’ credentials and finances rather than reasonably donate expensive technology free to random individuals.
No reputable evidence supports Apple facilitating any such laptop contests recently.
What techniques do MacBook scammers use to appear real?
This scam often utilizes manipulated “deepfake” style video content falsely depicting Apple executives like Tim Cook endorsing the giveaway. Additionally, elaborate external portal pages mimic news authority branding alongside urgency cues directed encouraging desired actions outside reasoned thought.
Dense terms and conditions disclosures also bury monthly subscription charges exceeding $100 rather than reasonably covering one-time product shipment costs estimated around $10.
Why would Apple randomly donate thousands of MacBooks?
No sensible reason explains a profitable company gifting total strangers thousand dollar laptops simply covering minor shipping logistics alone. It defies logical business assumptions.
While certainly possible someday, the existing fake viral MacBook contests instead represent third-party scam attempts trying to abuse public perceptions around large enterprises advancing personal agendas causing preventable harm.
What actually happens after attempting fake MacBook offers?
Despite flashy incentives promising free high-end Apple laptops to social media followers attempting order processes, victims never receive devices. However, buried terms reveal consenting signing up for expensive recurring monthly subscription charges exceeding $100 rather than reasonable single shipment fees.
What should MacBook scam victims do next?
Those discovering unauthorized charges or services appearing after attempting too good to be true corporate tech giveaways should first notify banks disputing transactions, shutdown compromised account access then report details to appropriate fraud reporting groups exposing shady business practices. Never assume automatic honesty around online free gift offers closely tied to unbelievable stories conveniently requiring temporarily relinquishing sensitive identity data or finances first without external validation. Such manipulation intends self-enrichment rather than goodwill.
Here is an alternate short version of The Bottom Line section for the article warning about the fake Apple MacBook giveaway scam:
The Bottom Line on Avoiding the MacBook Social Media Scam
The supposed Apple MacBook giveaway circulating online serves as the perfect reminder why remaining vigilant against unbelievable free gift offers tied too closely incredible stories involving respected brands works safer long run.
Always verify legitimacy through unbiased third-party confirmation before acting. And never relinquish sensitive personal information or data in exchange for extraordinary financial opportunities wrapped too perfectly almost be true while requiring little but luck in return. Such deception intends subtle self-enrichment rather than purely altruism.


![Remove Cfruoptimizek.today Pop-up Ads [Virus Removal Guide] 12 McAfee scam 4](https://malwaretips.com/blogs/wp-content/uploads/2023/08/McAfee-scam-4-290x290.jpg)
