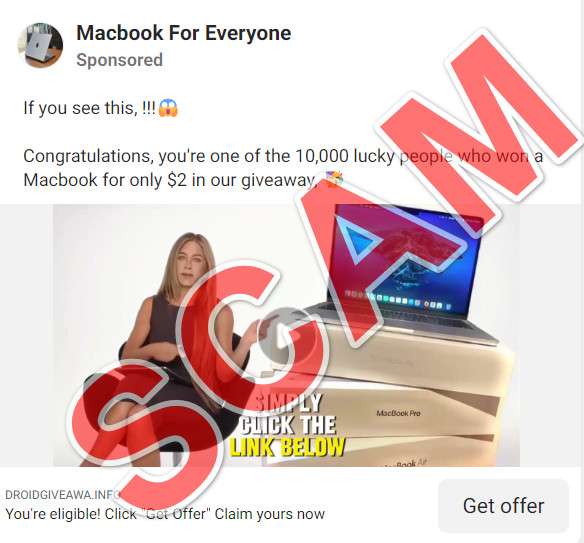
A fraudulent online campaign claiming beloved actress Jennifer Aniston is gifting free MacBook laptops has recently infiltrated social media through manipulated video ads and questionable website portals. However, the supposed giveaway actually intends stealing personal information and money rather than magnanimous charity. This article will break down exactly how the devious scam ensnares victims step-by-step alongside protection tips to avoid potential damages.
Overview of the Jennifer Aniston MacBook Giveaway Scam
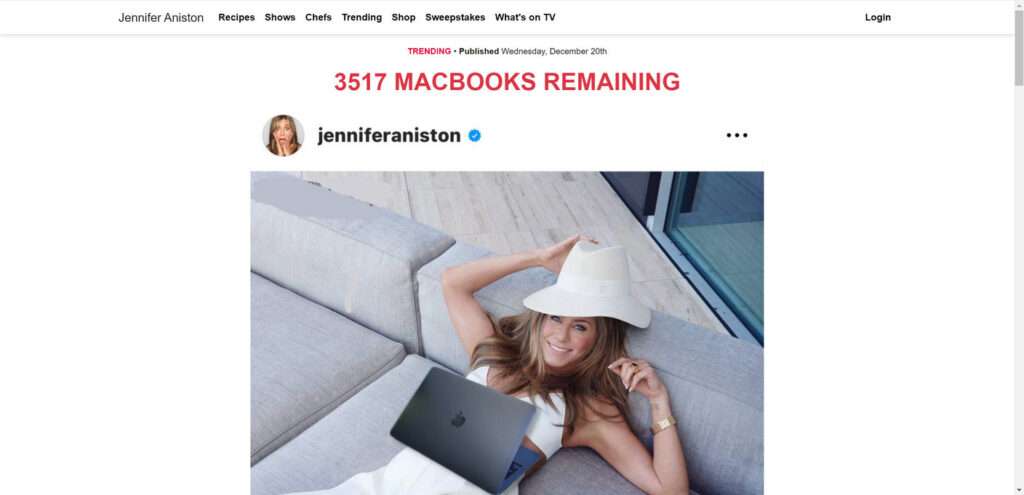
A fraudulent online campaign claiming universally-beloved comedy icon Jennifer Aniston has teamed up with Apple facilitating an epic giveaway gifting free MacBook laptops aims exploiting fans through deception and psychological manipulation rather than reasonable charity.
The scam commonly starts circulating via video advertisements run across social platforms like Instagram, Facebook and YouTube featuring deepfake AI footage realistically depicting Aniston endorsing the exclusive holiday promotion.
“Hey guys, Jennifer Aniston here with some exciting news!” the simulated ads show Aniston cheerfully sharing behind a MacBook bearing her branded logo. “To celebrate the holidays this year, I’ve partnered with Apple to give away THOUSANDS of the gorgeous rose gold MacBook Airs totally free!”
The fabricated Aniston representation urges viewers act fast clicking onscreen links claiming offer details revealing MacBook ownership pending only small $2 voucher fees.
“Meet our previous giveaway winners and learn how to participate yourself before remaining inventory runs out!” fake Aniston declares pointing at 11 smiling purported laptop recipients beside her. “Hurry and click below to take our eligibility quiz now because only limited supply still remains!”
Enticed social media users then click personalized tracking links expecting official Apple contest pages. However, redirects route victims through a series of external phishing websites like “jettrainingworld.com” completely unrelated to Apple or Ms. Aniston’s official businesses.
Deceptive portal pages feature familiar MacBook branding and imagery aiming to perpetuate initial perceptions around the free laptop giveaway rather than raising skepticism. Website headers exclaim:
“3499 Rose Gold MacBook Airs Still Available to Ship for Holiday Giveaway Participants – Meet Previous Winners!”
Sprinkled amid the hype, fake customer testimonials like Jordan Blum’s suspicious smiling review lend perceived credibility implying he successfully participated:
“I just got it and it is amazing! Can’t believe I got this for basically free! What a STEAL.”
But the manufactured social proof aims overcoming logic questioning how such contests reasonably sustain mass distribution thousand dollar devices requesting only couple dollar shipping in return.
In reality, buried terms and conditions eventually disclose victims submitting entry forms and processing fees actually consent steep recurring subscription charges exceeding $100 rather than securing free MacBook prizes.
The scam simply intends stealing money and information rather than reasonably gifting laptops worth over $1,000. By recognizing manipulative hooks early explaining unbelievable “free” gifts tied to respected brands require temporarily relinquishing sensitive identity data first, improved vigilance best avoids falling prey themselves.
How The Jennifer Aniston Fake MacBook Giveaway Fools Users
The fraudulent Jennifer Aniston MacBook giveaway conducts highly coordinated strategies luring victims systematically through the following deceptive process:
Step 1) Hook With Deepfake Video Content Impersonating Aniston
The scam starts by using AI deepfake videos to falsely portray Jennifer Aniston personally endorsing an extravagant holiday giveaway of free MacBook laptops to a select group of social media fans who enter in time. This familiar celebrity face grabs initial attention and triggers shares spreading wider reach.
Step 2) Direct Traffic Through Manipulative Intermediate Pages
Clicking on misleading video captions and embedded URL links reroutes viewers outside platforms to elaborate intermediate scam portal pages completely unassociated with Apple or the real Jennifer Aniston.
These showcase the Apple MacBook icon plus more AI-generated imagery of Aniston furthering initial impressions around the giveaway’s perceived legitimacy and exclusivity.
Step 3) Overcome Skepticism With Fake Social Proof
Sprinkled among portal pages, fake customer reviews and stock model images smiling beside shipped boxes build false social proof implying previous contest winners already successfully received expensive Apple laptops simply covering delivery fees.
“I just got it and it is amazing!” reads a suspicious account attributed to Jordan Blum. “What a STEAL.”
But the fabricated hype aims overcoming logic questioning how such contests reasonably sustain mass distribution thousand dollar devices requesting only couple dollar shipping in return.
Step 4) Pressure Victims Through Manipulative Psychology Triggers
The false scarcity, celebrity endorsement, urgency cues and social proof elements compel desired actions outside rational thought.
- “Hurry! Only 32 MacBooks left in stock for this exclusive Jennifer Aniston giveaway!”
- “Meet previous winners and learn how to participate before time runs out!”
Step 5) Covertly Acquire Financial Information and Personal Data
When visitors attempt securing devices through order forms, extensive personalized questionnaires conveniently require private input exceeding reasonable needs identifying shipping locations.
Step 6) Disclose the Real Monthly Subscription and Service Charges
Hidden fine print passages encased within lengthy website terms and conditions associated with giveaway order forms reveal victims actually consent steep recurring monthly subscription charges exceeding $100 rather than reasonable one-time product shipments.
Step 7) Profit Through Recurring Theft and Resold Data
Once scam operators possess compromised confidential information, recurring credit card charges activate alongside potentials reselling data through unregulated dark web channels inflicting additional long-term damages through identity theft. Either generates long-term financial injuries inflicted upon manipulation victims falling for fictional celebrity-fronted contests leaving them utterly empty-handed.
How to Spot the Jennifer Aniston free MacBook giveaway Across Social Media Apps
The supposed Jennifer Aniston free MacBook giveaway flows heavily through major social media channels like Facebook, Instagram and TikTok using manipulated video content and other deception tactics targeting users.
Let’s review what suspicious signals commonly expose the too-good-to-be-true laptop promotion on each platform.
Facebook Red Flags of the Celebrity MacBook Scam
Exercise caution towards Facebook posts exhibiting these common problems:
- Highly-produced video ads promising celebrity-gifted MacBooks
- Jennifer Aniston tagged in unauthorized posts from unverified accounts
- Links in descriptions route outside Facebook to unvetted domains
- Profiles spreading hype show limited histories beyond contest promotion
- Hard-selling language pressures users to click, share and act fast
- Comment sections emphasize giveaway participation, not scrutiny
Specifically, glossy video spots insisting Jennifer Aniston has gifted MacBook Airs to random followers deserves heavy skepticism vetting truthfulness.
Shady Instagram Tactics Used By MacBook Scammers
Analyze these questionable Instagram elements connected to supposed free MacBook offers:
- Jennifer Aniston tagged in photos/videos created by unknown third-party accounts without consent
- Links in bios and captions route traffic outside Instagram avoiding protections
- Profiles only discuss MacBook contest without wider personal sharing
- Suspicious edits like account holders inserted alongside devices
- Locations list foreign countries unrelated to known American residences
For example, a brand new Instagram profile for “JenniferAnistonRamirez” regularly posting about MacBook sweepstakes entry from Nigeria seems reasonably dubious.
Suspicious TikTok Videos Promoting The MacBook Scam
Scrutinize these indicators TikTok videos likely intend socially engineering increased MacBook scam participation:
- Footage starring Jennifer Aniston showing no verifiable origination details
- Links in captions conveniently divert traffic outside TikTok’s moderation reach
- Visually manipulated imagery like account holders posing with devices
- Uniformly positive comments focused exclusively on entering to win
- Strong calls-to-action incentivize reacting without proper vetting
When grand opportunities sacrificing little for substantial personal gain deserve deeper inspection before participation protecting oneself from preventable privacy damages. What seems too good be true often is. Apply reasoned skepticism.
Red Flags Exposing Fake Celebrity MacBook Promotion Sites
In coordination with manipulated social media posts, the celebrity laptop scam also leverages a network of deceitful external websites to help lend credibility justifying later requests for personal user information.
Let’s explore several consistent suspicious website patterns exposing the underlying scam despite convincing first impressions.
Co-opting Reputations of Trusted Brands Without Authorization
Rather than building sites credibility from scratch, fraudulent MacBook operators impersonate Apple’s iconic branding without legal rights or permissions. Logos, product images and even pricing copies real MacBook listings aiming to dupe visitors initially believing observation legitimate authorized retailer online storefronts.
Fabricating Celebrity Endorsement Quotes Supporting Scam Legitimacy
Another effective tactic giving the illusion of third-party endorsement involves crafting vivid celebrity quotes praising the epic giveaway values. But scrutinizing these message statements against credible media archives reveals no records correlating to actual endorsement press releases.
For example, sites proclaim:
“I absolutely love my rose gold MacBook Air for streaming ‘The Morning Show’ from anywhere!” says attributed Jennifer Aniston quote. “So excited watch fans unbox their very own new laptops TikTok this holiday season after entering our biggest tech giveaway ever!”
But misinforming visitors intends lowering guard requesting financial disclosures rather than transparency reasonably offering extravagant free gifts in exchange for little.
Burying Fine Print Legalese Detailing Recurring Account Charges
While flashy incentives prompt acting before thoroughly reviewing rules, buried terms and conditions passages disclose victims registering for expensive recurring monthly subscription charges rather than one-time coupon shipping fees securing “free” devices. This demonstrates intention eliciting finances deceptively versus giveaways.
Anonymizing Site Ownership Details Through Proxy Services
Finally, running themes across scam websites stay hiding the true controlling parties through obscuring domain registration data behind proxy site ownership protections rather than providing visible legitimate business details.
So while unbelievable holiday sweepstakes offers tied closely to respected celebrity status tempt likelihood engagement, applying extra scrutiny protects individuals from preventable privacy and financial damages. Remain empowered spotting past emotional hooks and facade obscuring ulterior motives.
What To Do If You Are Already A Victim of The Jennifer Aniston MacBook Scam
If you now face unauthorized recurring charges or services after attempting seemingly legitimate giveaways or free trials, here are proactive next steps:
Step 1 – Notify Financial Institutions Immediately of Detected Fraud
Contact any credit card, debit card or digital wallet providers tied to scam payments alerting them you discovered an appliance scam scheme falsely claiming celebrity endorsement used as pretext enabling undisclosed monthly account charges without consent. Inform them this violates expected giveaway terms outlined involving only reasonable one-time voucher shipment-related costs.
Ask urgently about launching fraud disputes and request provisional reimbursements until resolved. Supply details on the offending business names, domains or parent companies behind recurring charges. Follow their guidance strengthening cases demonstrating damages incurred under demonstrably deceptive pretenses.
Step 2 – Attempt Canceling All Related Subscription or Account Access
Collect customer service contact information from monthly billing statements tied to scam services and subscriptions. Call each provider clearly revoking any past payment authorization now aware those were based on false representations and predatory concealment rather than reasonable sweepstakes disclosure terms initially pitched. Record confirmation details should charges inexplicably continue.
Step 3 – Enable Extra Account Protection Measures
Since compromised sensitive information remains exploited repeatedly, immediately update passwords, security answers and enable stronger multi-factor authentication everywhere feasible across pertinent logins. Additionally, update contact email addresses and phone numbers previously provided fraudsters.
Turn on credit monitoring services alerting suspicious activities and consider proactive bureau notifyers or credit freezes as well limiting potential exacerbated cases identity theft result these data breaches.
Step 4 – Submit Actionable Complaint Reports to Relevant Fraud Agencies
File reports about all offending companies and scam portals with both government and third-party consumer protection groups like the Federal Trade Commission, FBI Cybercrime Division or Internet Crime Complaint Center documenting damages incurred under demonstrably false pretenses.
Such filings support investigating the broader interstate patterns of repeat offenders ultimately improving outcomes and recovery options for all negatively affected victims. The more meticulously detailed records submitted, the greater potentials agencies can assemble civil cases achieving criminal restitution. so collect and preserve all evidence exposing scam techniques, weblinks, names or contact points.
Red Flags Exposing The Jennifer Aniston MacBook Scam
Although highly convincing initially, several consistent suspicious signals help reveal when tech product celebrity giveaways truly intend facilitating malicious financial theft rather than reasonable community goodwill or marketing lead generations:
1. Unsubstantiated Celebrity Endorsement Claims
- Zero evidence across Jennifer Aniston’s publicist statements or her verified social media accounts exists confirming any affiliation with sponsoring free MacBook giveaways. Yet scam portals prominently declare her direct participation.
2. Urgency Tactics Incentivizing Haste Over Logic
- Pressure triggers like ticking countdowns and inventory scarcity claims stimulate emotional reactions bypassing critical due diligence.
3. Account Irregularities Among Key Promoters
- User profiles spreading viral contest promotions often demonstrate very limited previous platform activities bringing legitimacy doubts. Impossible volumes sharing from accounts created same day adds more questions.
4. External Website Links Rerouting Followers Through Unvetted Domains
- Intermediate redirects flowing outside legitimate social media platforms detach followers from internal moderation protections and ditch them into uncontrolled environments ideal for predatory scams wanting less screening accountability.
5. Mismatched Fine Print Terms Covering Monthly Subscriptions vs One-Time Voucher Payments
- Contradictory prize shipment and handling fees ranging from $2 to $150+ monthly smell like financial manipulation rather than reasonable disclosure.
6. Deliberately Obscured Domain Ownership and Operational Details
- WhoIs domain record lookups frequently reveal unrelated foreign-based shell company owners masking actual operational details through proxy registration services.
When celebrities magically announce extraordinary free gift opportunities tied closely incredible true stories conveniently requiring temporarily relinquishing sensitive identity data first, rational skepticism questions whether purely hearts desires motivating such grand generosity or ulterior motives focused self-enrichment. Maintain vigilant common-sense guardrails.
Frequently Asked Questions Regarding The Viral Jennifer Aniston MacBook Scam
Find answers below to the most commonly searched questions around supposed Jennifer Aniston sponsored MacBook holiday giveaways promotions currently circulating social media and questionable external websites.
Is the Jennifer Aniston MacBook Air giveaway real or fake?
Despite advertisements featuring convincing video footage seeming to portray Jennifer Aniston personally endorsing an extraordinary MacBook giveaway for fans, the entire campaign constitutes an elaborate scam aiming to phish peoples’ sensitive credentials and finances rather than reasonably donate expensive technology free.
No reputable evidence supports the famous actress has ever facilitated any such laptop contests.
What techniques do MacBook scammers use to appear real?
This scam often utilizes manipulated “deepfake” style video content falsely showing Jennifer Aniston endorsing the giveaway. Additionally, external portal pages mimic official Apple branding alongside urges creating urgency to compel desired actions outside reasoned thought.
Dense terms and conditions bury monthly subscription charges exceeding $100 rather than reasonably covering product shipment. And fake customer testimonials create “herd mentality” assumption it must prove legitimate if many others already participated successfully before.
Why would Jennifer Aniston randomly giveaway thousands of MacBooks?
No rational reason exists reasonably explaining why a celebrity would gift total strangers thousand dollar laptops simply for covering minor shipping and handling logistics alone. It defies logical assumptions.
While certainly possible in coordinated future marketing campaigns, supposed existing viral MacBook contests fronted by Ms. Aniston instead represent third-party scam attempts trying to abuse public goodwill towards subtly advancing personal agendas causing harm.
What happens when you attempt the MacBook offer?
Despite flashy incentives promising free MacBook laptops to lucky social media followers attempting order processes, victims never receive devices. However, buried terms disclose signing up for expensive recurring monthly subscription charges exceeding $100 rather than reasonable single shipment fees.
What should MacBook scam victims do next?
Those discovering unauthorized charges or services appearing after attempting too good to be true celebrity tech giveaways should first notify associated banking and credit sources disputing transactions, shutdown compromised account access then report details to appropriate government and consumer protection groups exposing shady business practices.
Conclusion
The supposed Jennifer Aniston-gifted MacBook giveaway sweeping social media demonstrates another cautionary example why reasonable skepticism remains so crucial navigating today’s riskier online waters promising extraordinary free gifts wrapped too perfectly almost be true.
What seems incredible likely is until proper independent verification completed first. Don’t compromise personal information or finances chasing irrational social media opportunities down rabbit holes detached from reality.
Apply critical thought before acting. And warn others similarly avoiding unnecessary troubles initially inspired by hope beyond reason. If extraordinary marketing gifted celebrities offerings appear flooding feeds, don’t assume automatic honesty or accuracy. Deductive logic and externally validated proof separates intents aimed self-enrichment from genuine goodwill.