A convincing new iPhone giveaway scam is making its way across social media by impersonating Hollywood stars Ashton Kutcher and Mila Kunis. This devious fraud starts with enticing ads across sites like Facebook, Instagram and TikTok featuring deepfake video footage of the couple announcing an exclusive chance for viewers to upgrade to the latest iPhone 15 for free. When ad clicks lead users to fake news articles and suverys, the scam culminates in demands for personal data and credit card information – not to ship free phones, but rather to trap victims into recurring monthly subscription fees billed without consent.
This article provides an in-depth look into how this celebrity-impersonation racket operates, including the manipulative psychological tactics used to socially engineer victims step-by-step through intrusive questionnaires, fake news reports, countdown timers and other persuasive traps carefully crafted to exploit excitement over the high-value phone offers.
Overview of the Enticing Yet Fake Ashton & Mila iPhone Giveaway
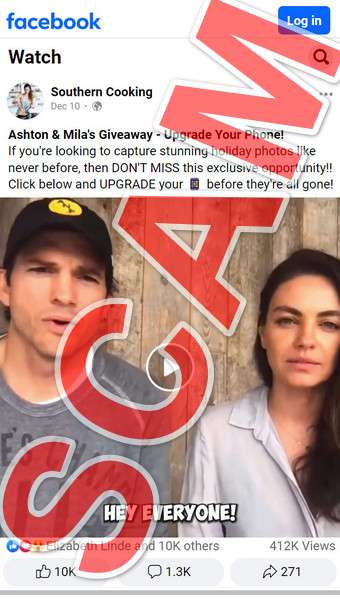
The too-good-to-be-true Ashton and Mila iPhone giveaway scam starts by hooking social media users through compelling video advertisements run across platforms like Facebook, TikTok and Instagram. These showcase deepfake-style footage depicting the famous actors enthusiastically endorsing an exclusive holiday contest promise upgrading old phones to Apple’s latest iPhone 15 Pro Max completely free.
In the deep fake videos, Ashton Kutcher urges viewers:
“Hello everyone! I’m Ashton Kutcher and this is Mila Kunis. If you are seeing this ad it’s because we are excited to tell you that we have started our annual holiday giveaway. Ever since I played Steve Jobs in a biopic back in 2015, we’ve had special access to the latest iPhones to gift some of our biggest supporters and fans once a year.”
Mila joins stating:
“That’s right! This year we are giving away the brand new iPhone 15 Pro Max to 1,000 lucky fans which makes it our biggest tech giveaway yet. And if you are seeing this ad it means we still have iPhones available!”
The celebrities detail viewers simply needing to click affiliated links and answer a few short questions to register for the drawing. Kutcher concludes enthusiastically:
“All you have to do is click the Get Offer button below and answer a few short questions to see if you qualify. So what are you waiting for? We can’t wait to connect with some of our amazing fans and upgrade your mobile experience this holiday season.”
When viewers click on the video captions or embedded links, they get rerouted outside social media to various scam portal websites like nyxperformancecavern.com, heliotropeagility.com, jettrainingworld.com, emeraldphysiqueworld.com harvestbeautyrepublic.com and checkoutprizewinner.com for example. These intermediate domains only exist to access payment and personal information through deceit.
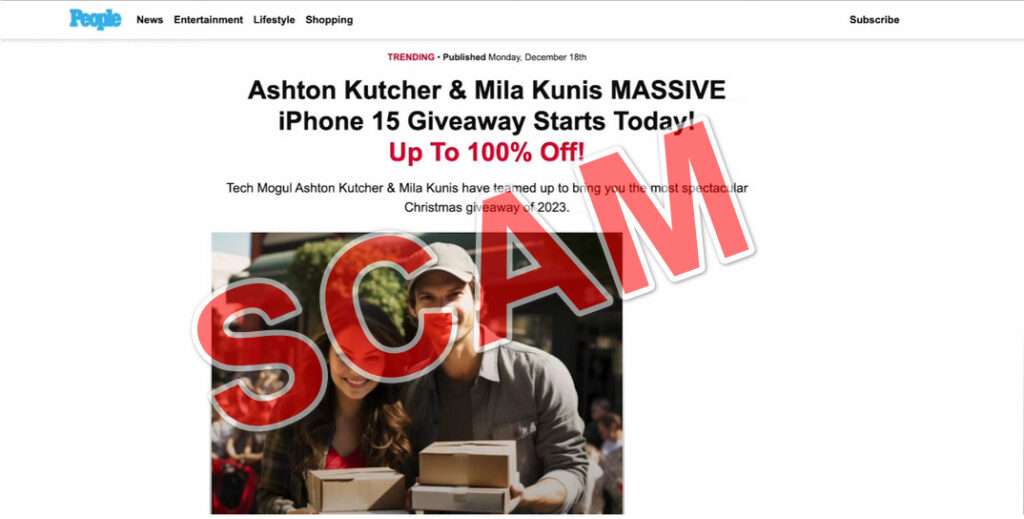
Upon arriving at the fraudulent contest homepage, participants read through false articles depicting the giveaway covered widely by CNN, FOX or People Magazine. Stock images show the two celebrities holding iPhones alongside logos from major outlets. This aims to overcome skepticism by mimicking legitimate news coverage.
Headers blare: “Ashton Kutcher & Mila Kunis MASSIVE iPhone 15 Giveaway Starts Today! Up To 100% off! Tech Mogul Ashton Kutcher and Mila Kunis have teamed up to bring you the most spectacular giveaway of 2023”
After scrolling through fake celebrity and product reviews, users eventually reach customized order forms promising delivery of the free phones solely pending small upfront shipping/handling fees.
However hidden subscription clauses discreetly authorize recurring monthly charges rather than one-time payments estimated around $10 to cover contest prize delivery.
In the end, high value Apple products are obviously never dispatched to filling contest entries. But victims’ compromised information and access enables scammers inflicting financial damages through shady underground e-commerce channels thanks to unlocked access to credit cards, addresses and other sensitive credentials handed over trying to win a luxury device.
The bottom line when encountering celebrity-backed contests online: verify legitimacy first rather than compromising personal or financial information chasing products ultimately never received. Always read the fine print and externally validate authenticity through objective independent research before participation. Stay vigilant and think twice when unbelievable free gifts wrapped up neatly in feel good stories conveniently require providing sensitive credentials upfront first. It simply proves too risky in the long run.
How the Ashton & Mila iPhone Giveaway Scam Fools Social Media Users Step-by-Step
The Ashton & Mila fake iPhone giveaway employs specialized manipulation strategies luring victims systematically through the following process:
Step 1) Gain Attention With Deepfake Celebrity Endorsements
The cornerstone making the scam possible involves using AI to generate fake but convincing videos of the two celebrities enthusiastically promoting the holiday contest. Their fame and influence sparks initial interest redirecting fans to external promoting portal pages.
“If you are seeing this ad it’s because we are excited to tell you that we have started our annual holiday giveaway… All you have to do is click the Get Offer button below and answer a few short questions.” the simulated Ashton Kutcher urges.
Step 2) Build False Credibility Through Deceptive Website Design
Intermediate pages feature side-by-side logos from CNN, People Magazine and other reputable news/tech brands to make it seem these outlets have already validated the giveaway’s legitimacy through extensive coverage. This helps overcome skepticism.
Header read: “Ashton Kutcher & Mila Kunis MASSIVE iPhone 15 Giveaway Starts Today! Up To 100% Off!”
Step 3) Encourage Entry Attempts Through Psychological Triggers
Scarcity and urgency cues like ticking countdown timers and claims of limited supply strongly encourage users skipping proper vetting behaving reactively trying securing scarce free goods.
“And if you are seeing this ad it means we still have iPhones available. All you have to do is click the Get Offer button below and answer a few short questions.”
Step 4) Collect Personal Data Under Guise of Contest Entry
Multi-page questionnaires conveniently collect sensitive identity credentials like addresses and birth dates when users were supposedly just entering an iPhone drawing.
Buried terms and conditions discreetly secure rights marketing any submitted information to unverified third parties.
Step 5) Trap Victims With Fine Print Subscription and Service Terms
Hidden fine print clauses discreetly authorize recurring monthly subscription charges from partners when visitors submit entry forms seeking phones. These detail unwanted services costing up to $150 rather than one-time shipping fees expected under $10.
Step 6) Profit From Leaked Data and Unauthorized Financial Charges
With access to now compromised information, scammers can enact identity theft or sell details through black market data exchanges. They also stealthily siphon money long-term from attached payment sources on monthly schedules.
In summary, the celebrity couple iPhone scam ensnares social media users through emotional manipulation, web page tricks, urgent calls-to-action and concealed terms disclosing alternative money-making objectives. Maintaining vigilance when free gifts wrapped up neatly in feel good stories stars conveniently require providing sensitive personal financial information upfront is safest path forward.
How to Identify the Viral Ashton & Mila iPhone Scam on Top Social Media Apps
The fraudulent Ashton and Mila holiday iPhone giveaway campaign flows heavily through major social media channels like Facebook, Instagram and TikTok. The scam uses manipulated video content and other deception tactics targeting users across platforms.
Let’s review what suspicious signals commonly arise exposing the iPhone celebrity scam across each popular social app.
Facebook Warning Signs of the iPhone Celebrity Scam
Watch for these Facebook-specific indicators that the Ashton & Mila iPhone promotion likely intends stealing data rather than contest generosity:
- Highly polished video advertisements seeming too perfect offering excessively generous free goods
- Content originates from accounts completely lacking official verification checkmarks
- Embedded links or captions route outside Facebook to unvetted external domains
- Behind-the-scenes pages display limited engagement history beyond similar viral contests
- Comments uniformly emphasize giveaway participation rather than reasonably questioning abnormalities
For example, an iPhone ad from an unverified Facebook Page named “Ashton Kutcher Fans” would arouse immediate suspicion of scam intentions.
Instagram Signals of the Ashton & Mila iPhone Scam
Analyze these signs on Instagram pointing to a potential iPhone scam campaign:
- Ashton or Mila tagged in photos/videos created by unknown third-party accounts
- Captions urging immediate action to win iPhones through external sites
- Profiles recently created or demonstrate atypical posting behavior
- Account locations list geographically dubious regions unrelated to U.S. ties
- Comments focused exclusively on giveaway participation with no authentic personal connections
An Instagram account with merely 3 previous posts now showcasing the iPhone giveaway based overseas deserves deeper inspection before proceeding.
Suspicious Ashton & Mila iPhone Scam Content on TikTok
Scrutinize these TikTok videos signals trying to socially engineer iPhone contest participation:
- Highly produced footage from accounts lacking any previous engagement
- Manipulated editing that inserts Ashton Kutcher and Mila Kunis without context
- Links in captions route clicking users outside TikTok avoiding internal protections
- Uniformly positive comments focused solely on hype urgently entering
When an account appears suddenly posting polished giveaway videos diverting external sites, it logically warrants skepticism.
In summary, fictitious celebrity iPhone deals thriving across social apps can successfully disguise ulterior motives through manipulated content and psychology. But recognizing consistent suspicious patterns helps reveal underlying scams attempting privacy intrusions rather than community goodwill.
Pinpointing Deceptive Ashton & Mila iPhone Giveaway Portal Sites
In coordination with manipulated social media posts, the celebrity iPhone scam also leverages a network of deceitful external websites to help lend credibility justifying requests for personal user information.
Let’s explore several consistent suspicious website patterns exposing the underlying scam despite initial convincing first impressions.
Deploying Reputable News Branding for Unearned Legitimacy
Rather than building sites credibility from scratch, fraudulent iPhone giveaways impersonate trusted news authorities by featuring established media logos like CNN, People Magazine or Fox News. This aims easing skepticism convincing visitors legitimate journalistic coverage already vetted the unbelievable promotion for authenticity.
Homepage headers deceptively announce:
“Ashton Kutcher & Mila Kunis Kick Off MASSIVE Holiday iPhone 15 Giveaway – Here’s How To Enter!”
Yet no actual affiliation exists.
Fabricating Celebrity Quotes Supporting the Scam
Another effective tactic giving the illusion of third-party endorsement involves crafting vivid celebrity quotes praising the epic giveaway. But Investigating these messages across credible media sources reveals no records correlating to actual statements released.
For example, sites proclaim Ashton boasting:
“We get thousands of free iPhones straight from Steve Jobs himself thanks to my acting role! So excited watch fans unbox brand new iPhone 15s on TikTok this holiday season after entering our biggest tech giveaway ever with Mila!”
But fabricated misinformation aims facilitating access finances rather than reasonably offering extravagant gifts requesting little return.
Burying Disclosing Terms About Recurring Account Charges
While flashy visuals prompt acting fast scarcely reviewing rules, buried terms disclosures reveal victims registering for recurring $100+ monthly subscription charges rather than one-time shipping transaction securing “free” devices. This demonstrate intention eliciting bank information under false pretenses rather than reasonably offering lavish gifts donation.
Obscuring Identity Information About Site Operators
Finally, running themes across tech scam websites stay hiding the true controlling parties through obscuring domain registration data, falsifying listed business addresses and providing only anonymous communication channels.
So while incredible holiday sweepstakes opportunities tied closely celebrity status seem highly enticing upfront, applying extra scrutiny protects individuals avoiding preventable financial damages going forward. Look past the emotional hooks and facades long enough allowing objective logic reveal what scammers intentionally try keeping obscured from plain view.
What to Do If You Are A Victim of The Ashton & Mila iPhone Scam
If you now face unauthorized recurring charges or services after entering personal information seeking a free iPhone giveaway, immediately take the following steps:
Step 1: Contact Banks and Payment Companies
Alert affected banking, credit institutions and digital wallet providers regarding recent fraud discovery requesting their assistance disputing charges from organizations with unauthorized access to payment methods. Monitor statements routinely ensuring no additional unusual charges surface from compromised data constantly at risk by unethical parties reselling access repeatedly through dark web channels.
Step 2: Attempt Canceling Related Subscriptions
Dig up customer service contact information from monthly billing statements tied to scam services fraudulently described securing free iPhones. Call providers and clearly revoke any consent accidentally given earlier applying for phone offers converts now obvious subscription cons. Record confirmation numbers and details discussed verifying cancellations go into effect so charges eventually terminate. Realize these groups already demonstrated untrustworthiness though, so verify against unexpected billing continuation.
Step 3: Enable Extra Account Protection Measures
Fraudsters in possession of any personally identifiable information continue capable of inflicting future financial damages. Immediately update account passwords, security questions and enable stronger dual-factor authentication everywhere feasible across pertinent logins. Update email addresses or phone numbers previously provided. Turn on real-time activity notifications so nothing unauthorized goes unnoticed. Consider credit monitoring services alerting unusual credit checks signalling problems requiring quick intervention limiting adverse impacts. Remain vigilant long-term since compromised data retains lasting risks.
Step 4: Report Violators to Relevant Fraud Agencies
Submit available scam website details along identities or addresses connected to unauthorized credit charges to both government and third-party fraud reporting groups like Federal Trade Commission. Provide investigators comprehensive documentation clearly demonstrating damages incurred from misrepresented offers and deceitful negative-option enrollment practices. Widespread incident reporting patterns allow agencies building cases against repeat offender organizations warranting legal intervention helping all past victims achieve financial restitution assisting recovery efforts.
Frequently Asked Questions About the Viral Ashton & Mila iPhone Giveaway Scam
Find answers below to the most commonly searched questions regarding the supposed Ashton Kutcher and Mila Kunis sponsored iPhone giveaway promotions currently circulating social media and questionable websites.
Is the Ashton & Mila iPhone giveaway real?
No. Despite advertisements featuring convincing footage of the celebrities announcing an exclusive holiday iPhone giveaway for fans, the entire campaign constitutes an elaborate scam aiming to steal personal information and money. No evidence supports the famous couple has facilitated any such contest.
How can you identify the Ashton iPhone scam online?
Warning signs include unverified social media posts, urgency cues pressing individuals act before thinking, external links routing to unrelated domains, unbelievable free offerings only requiring small upfront costs, praise-filled comments seeming artificially manufactured and behind-the-scenes account activities involving automation rather than legitimacy.
Why would Ashton Kutcher and Mila Kunis sponsor a massive iPhone giveaway?
No rational reason supports Hollywood stars randomly selecting social media fans receiving new $1000 phones simply covering shipping. While certainly possible someday in future, current viral iPhone giveaways represent third-party con attempts trying to falsely suggest celebrity advocacy encouraging followers relinquishing critical personal data assurances guard every day.
What do participants actually receive from the fake iPhone promotion?
Absolutely nothing tangible except potential loss of personal information and invasion of financial resources. The scam gives false promises of prized iPhone devices in order lure users into inputting sensitive credentials enabling recurring account charges exceeding $100+ monthly. Data breaches also allow fraudsters accessing additional underground activities with stolen identities.
What iPhone scam victims should immediately do next?
Contact associated banking and credit sources regarding recent discovery of fraud dispute unauthorized charges, shutdown compromised account access enacting new robust security protections. Report relevant details like offending business names/domains to government and consumer groups exposing patterns stopping continuous victimization others. And warn close friends about scam avoidance empowering wider community vigilance reasonable precautions increasingly risky digital age.
There is no need gambling personal information or data chasing after free gifts from celebrities online wrapped too perfectly almost be true. Verify legitimacy and remain cautiously optimistic avoiding next unnecessary troubles initially inspired by hope beyond reason.
The Bottom Line on Avoiding Celebrity Tech Giveaway Scams
The Ashton & Mila iPhone deal serves as the perfect reminder maintaining healthy skepticism whenever asked relinquishing sensitive information chasing free merchandise tied too closely incredible be true stories featuring famous faces conveniently requiring just small upfront payment first.
Verify legitimacy through independent research before acting. Review all terms and disclosures in full beforehand rather than hurriedly complying feeling pressured by visceral fear missing fleeting opportunity. Should clever scams still unfortunately succeed initally, act decisively contacting pertinent fraud resolution channels demanding assistance until achieving adequate restitution recovering hard-lost finances going forward.
Collective vigilance consumer protection support makes better decisions enabling safer online interactions decreasing these risks altogether. Don’t become the next victim simply hoping stroke good fortune fall one’s lap. Remain cautiously optimistic blessing others this holiday season rather than compromising own stability acting impulsively questionable free offers tied too closely incredible true tales conveniently requiring access finances first. It simply proves too risky long run.