A troubling online scam featuring fraudulent On-Running clearance sale promotions has emerged, heavily advertised across leading social media platforms through sponsored posts. Highly persuasive advertisements promise jaw-dropping discounts up to 90% off, but route victims to sophisticated imposter websites designed to steal money and personal data instead of deals. This article unravels how the elaborate fraud works, avoiding becoming victimized, and what to do if already scammed.
Scam Overview
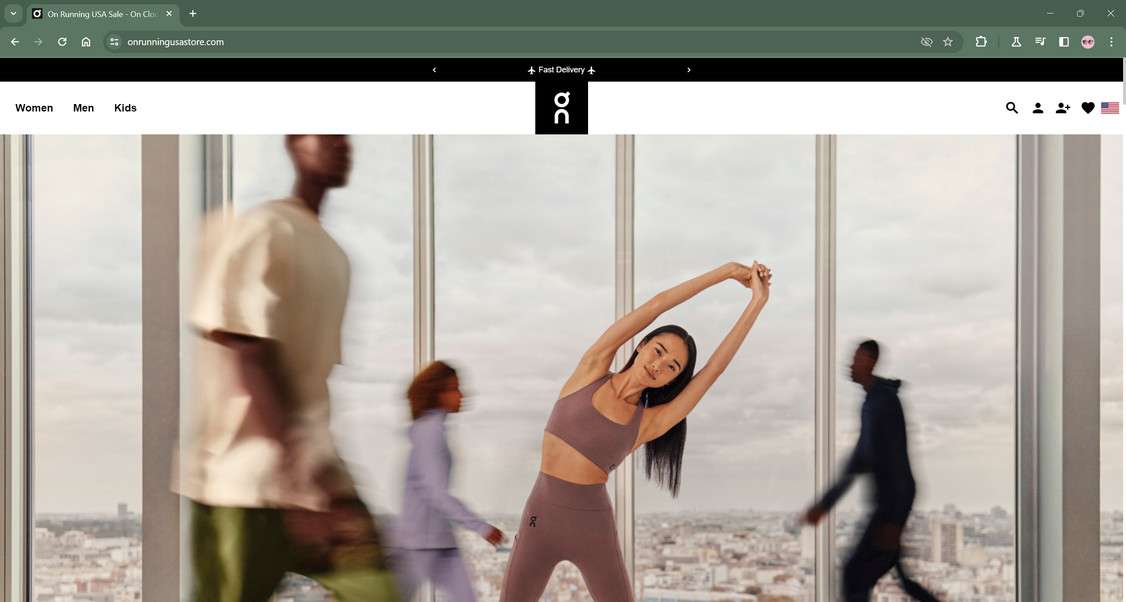
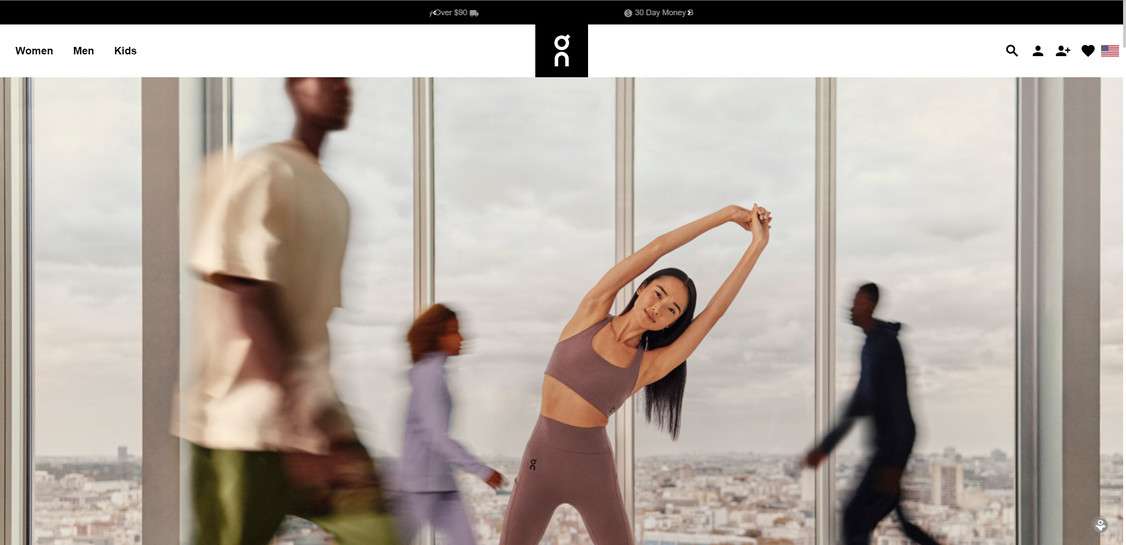
In recent years, a sharp escalation of social media advertisements touting remarkable On-Running discounts have saturated platforms like Facebook, Instagram and TikTok. The eye-catching posts display images of popular running shoe models like the Cloud strider and Cloudmonster marked down at unbelievable rates such as “Entire Store 80% Off!”
In addition to implausible price-slashing claims, other attention-grabbing slogans also spark urgency with calls-to-action trying to whip shoppers into frenzies over perceived closing markdown events. “Final Days – Rock Bottom Prices!” and “All Stock Must Go!” exemplify psychological tactics fraudsters deploy, coercing hurried purchases before imagined inventory sells out from the thousands of deal-seekers also allegedly swarming sales.
However, keen shoppers who click on ads expecting authentic On-Running liquidations instead get deceptively rerouted to elaborate fake web stores carefully engineered to replicate the Swiss performance footwear brand’s actual online shop and promotions.
Behind the extensive artifice hides international cybercrime groups coordinating sophisticated fraudulent website networks designed to systematically target and dupe consumers through disseminating scam clearance event advertisements and funneling site traffic onto convincing yet entirely bogus platforms.
How the Scam Works
The crafty scam operations employ integrated strategies engaging both social engineering manipulation and technical infrastructure deception. By psychologically exploiting shopper biases through compelling ads then technologically deceiving visitors upon sham websites, this multifaceted fraud manages large-scale thievery from those fixated on promotions over legitimacy.
Step 1: Assembling Highly-Believable Fake On-Running Websites
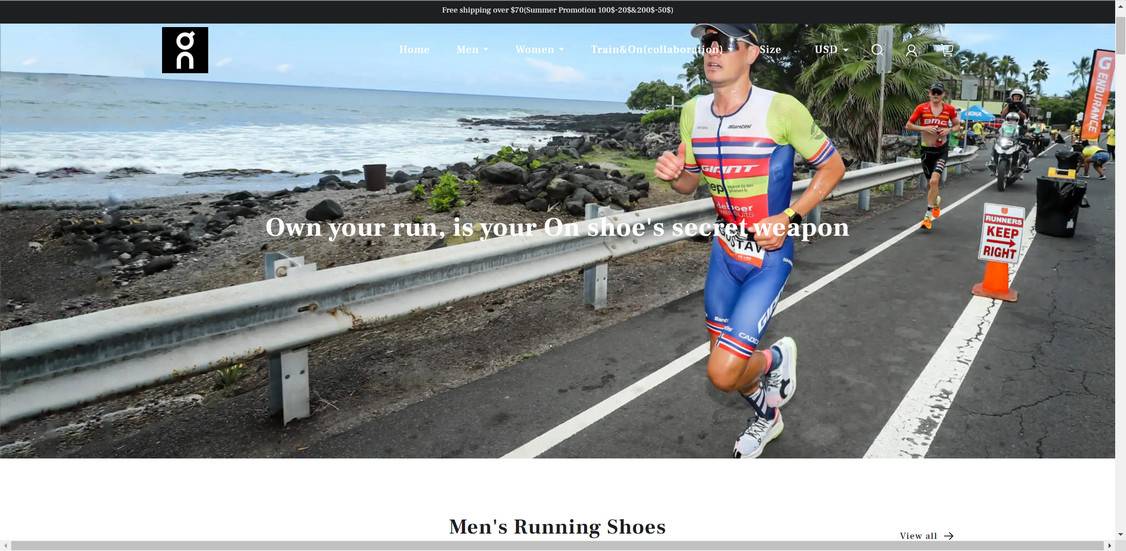
The core infrastructure enabling this vast scam involves reverse engineering and digitally counterfeiting the genuine brand’s websites through meticulous copying of multiple intricate elements including logo treatments, product galleries, visual layouts and even HTML code structures.
Deceptively, the unlawful outlets closely mirror the authentic site’s appearance and functionality on surface levels. Yet subtly hidden issues scattered throughout the fake sites expose their false natures:
- Fabricated business credentials using counterfeit logos and stolen brand imagery
- No transparency surrounding mysterious owners actually operating the scam
- Missing “About Us” pages vaguely detailing company history or leadership profiles
- Suspicious domain names registered only weeks ago
- Prominent web elements like photos, videos and product descriptions plagiarized from lawful sites
Despite lacking legitimacy under stricter examination, these copycat websites still sufficiently mimic trusted companies for initial visitors to believe clearance sale claims highlighted in corresponding ads.
Step 2: Spreading Social Media Ads Promising Fake Markdowns
The core ploy preys on optimism by blasting social advertisements boasting unbelievable yet still tempting On-Running price cuts aiming to bait traffic onto counterfeit pages.
Both ad content structure and underlying promotion placement algorithms specifically target users displaying signals suggesting increased vulnerability towards taking scam bait based on revealed penchants for:
- Online shopping behaviors, particularly deal-seeking
- Running gear, especially niche brands denoting discretionary income
- Retail promotions including markdown events and clearance language
After enticing attention showcasing images of coveted shoes marked down 70%, persuasive slogans spark urgency to click before the last 10 remaining pairs sell out entirely. Countdown timers indicating 23 hours remaining piles on supplementary pressure for rushed decisions lacking rational scrutiny.
Unfortunately, psychological drives unconsciously justifying rapid purchase selections become craftily exploited against victims. Intermediary click funnels purposely obscuring final destinations prevent alarm until eventually landing upon counterfeited webpages.
Step 3: Stealing Shoppers’ Money and Private Information
Upon deceived visitors entering the convincingly spoofed platforms and excitedly compiling clearance merchandise into carts expecting to score temporary bargains, critical examination remains hindered until reaching final checkout confirmation screens.
Here the underhanded tactic pivots from subtle influence to outright extortion. Data input forms demand extensive personal and financial information from duped shoppers expecting deep discounts by acquiring:
- Full legal names, home addresses, phone numbers
- Complete payment card data including CCV codes
- Additional demographics like annual incomes or vehicle models
Yet after readily relinquishing intimate details anticipating shipping notifications for cheap Running shoes, crushing reality sets in through the following disappointing results:
- No products ship – By far the most frequent outcome involves payments successfully processing as orders quietly disappear.
- Faulty knockoffs sporadically arrive – Some customers obtain shoddily-made replicas with substandard materials unlike advertised merchandise.
- Used, defective or compromised goods appear – In rarer cases, items arrive clearly damaged, unsafe or used suggesting no intent behind real sales.
- Random improper items get sent – Some scam victims receive products utterly unrelated to anything ordered.
Even worse than losing money from illicit transactions, victims also now grapple with long-term threats of serious identity theft enabling criminals to legally open financial accounts or lines of credit using entirely falsified credentials but still attached to victims’ data profiles.
So through an ingenious blend of emotional manipulation theatrics and convincing fake website facades, multinational fraud syndicates manage large-scale theft from those distracted by remarkable savings over meticulously vetting legitimacy first.
How to Identify the Scam Websites
While counterfeit operations dedicate tremendous efforts making their duplicate On-Running websites convincingly mirror legitimate retailers, numerous subtle yet consistent signals across scam platforms allow smart shoppers to evade surrendering personal data or payments due to unbelievable price cut promotions.
Carefully dissecting website components and questioning the validity of steep discounts allows consumers to sidestep potential identity theft traps while seeking deals on performance running shoes and gear.
Auditing Domain Registrations and Histories
Responsible companies build online stores intending lengthy lifespans serving customers over many years. Hastily registered domains strongly indicate temporary sham operations looking to capitalize on markdown hype before discoveries expose their true intentions.
- Imposters often use near-identical names like “On–RunningShoes” or “OnruningStore” rather than official company URLs.
- Check whether domains were only registered in the past 1-6 months which warrants extreme caution over longer-established sites.
- Crooks frequently utilize proxy registration services hiding owners’ true identities as well which heightens suspicions of fraud.
Authentication of Advertised Discounts
Reputable retailers occasionally offer sales seeking liquidity from inventory overstocks or upon launching major new product lines. However, knowledgeable consumers know even popular shoe brands rarely reduce prices past 50-75% thresholds simultaneously across full catalog lines without valid explanations.
Thus view advertised website-wide discounts hitting 80% or 90% automatically with extreme suspicion regardless of company familiarity. Such deals likely indicate outright scam attempts more than authentic limited-time promotions.
Moreover, legitimate temporary markdowns get highlighted consistently across multiple official advertising channels including social media profiles, homepages and email listings.
Deals promoted exclusively through third party ads but omitting references on a brand’s primary e-commerce store signals likely bait claims without consistency.
Assessing Company Digital Presence
Unlike short-lived scam websites relying purely on mimicking visual aesthetics of trusted companies through stolen logos and product photos, legitimate corporations dedicate tremendous efforts building robust multimedia presences highlighting positive sentiment earned from years serving satisfied customer communities across various platforms.
Thus search rigorously for independent discourse and artifacts affirming high credibility through authentic reviews, testimonials and demonstrable press coverage. Lack of such confirming indicators reasonably warrants wariness over the business’ authenticity.
Verifying Company Contact Information
A quick check on supposedly provided location details and communication channels reveals actual legitimacy. Easily contact live personnel willing to openly share corporate backgrounds like executive leadership bios, physical addresses and other fundamental organization descriptors reputable enterprises willingly promote.
Unanswered calls and emails bounced back due to invented contact details provide obvious red flags over fabrication. Moreover, opaque organizations unwillingly sharing fundamental operational details outright signal sinister scams.
How to Spot the Fraudulent Social Media Ads
In tandem with engineering entirely fake ecommerce platforms impersonating authentic athletic shoe retailers, clearance scam operations also harness sponsored social media ads to attract target audiences onto their illicit websites by promoting unbelievable yet highly convincing markdowns up to 90% off.
Highly deceptive sponsored posts explicitly showcasing over the top sitewide discounts frequently blanket Facebook feeds, Instagram stories and TikTok streams with aims of deceiving passionate runners and dedicated sneakerheads. However, certain patterns across these advertisements expose their underlying deceitful intentions.
Demystifying Duplicitous On-Running Ads on Facebook
As the most expansive social media ecosystem allowing extensively customizable advertising capabilities, cunning Facebook scammers easily identify and target users displaying strong signals suggesting increased susceptibility towards taking promotional bait based on revealed passions for:
- Online shopping behaviors, especially seeking deals
- Running shoes and niche athletic brands
- Retail promotions including clearance language
Some common traits helping distinguish sham On-Running Facebook ads include:
- Exceptionally reduced prices like “Our Entire Inventory Now 80% Off!” trying to spark intense fear-of-missing major bargains
- Usage of urgency cues and limited-time claims of one-day only sales ending in hours
- Routing through multiple obscure shortened link redirects aiming to hide landing destinations
- URLs utilizing unrelated domain names failing to feature actual company references
- Repeated changes across ad account identities once users submit fraud reports
In summary, spotting emotional triggers, misleading links and occasional account churn patterns helps identify shady Facebook ads.
Spotting Fraudulent Instagram Ads
Successfully scamming Instagram feeds requires appeals directly through visual splendor showcasing beloved brands. But critical observers can still expose underlying deceptions:
- An overabundance of generic athletic stock photo usage hints at inability legally using official brand creative assets and intellectual property.
- Targeting strategies intensely focused on users fitting core runner demographics as well as general shoe enthusiasts greatly engaged with hashtags surrounding terms like #runners and #sneakers.
- Video clips relying on spliced user-generated content featuring real branded apparel edited with deceptive captions and artificial urgency soundtracks
- Accounts repeatedly modifying handles once disabled to sustain scam crusades under constantly resurrected identities
Effectively, awareness surrounding the immense difficulties scam operators face gaining legal branding usage rights can help identify signs of trademark and creative infringements.
Identifying Fictitious TikTok Ads
As TikTok rapidly emerges as a breakout force reshaping digital commerce through video-powered storefronts and influencer collaborations, clearance scam rings scramble desperately to shift operations towards exploiting the viral app for their profit models.
However persistent challenges plaguing fake TikTok ads for niche brands like On include:
- Legal barriers preventing usage of iconic logos or brand elements without risks of fast copyright crackdowns
- Difficulties establishing traction rapidly enough before inevitable account suspensions given strict platform policies
- Production hurdles generating short-form ads stylized effectively matching TikTok’s polished aesthetic expectations
Still while current volumes remain comparatively limited, expecting rapid adaptations across criminal innovation labs means staying vigilant towards subtle suspicious signals including:
- Low-quality content with sloppy edits or awkward sales pitches hinting at overseas origins
- Accounts rarely staying intact longer than weeks before removals and re-creations
- Poorly integrated urgency overlays as limited options exist tailoring organic branded video
With heightened awareness of key patterns clearance fraudsters deploy across top social networks, informed users and sharper personal judgment make spotting retail cons easier.
What to Do If Already Scammed By a Fake On-Running Website
For victims discovering online clearance sale scams, the harsh realizations induce feelings of exploitation by channels once considered trustworthy. But accepting quickly what transpired proves essential to rapidly protect assets before additional damages occur through identity theft pipelines.
If you entered payment or personal information into a fake On-Running website promoted through sponsored ads or imposter domains, begin securing your identity with these steps:
Step 1: Contact All Financial Institutions to Freeze Accounts
Since scammers possess your information now, call banking providers immediately regarding identity theft to entirely lock down accounts against criminals attempting to drain or leverage your credentials illegally for additional frauds.
Step 2: Closely Watch All Accounts
Carefully inspect financial statements and credit reports daily over upcoming weeks searching for unfamiliar account access, cash withdrawals, balance transfers or new accounts opened fraudulently using your stolen identity. Ensure also no services appear without approval.
Step 3: Lodge Fraud Reports On All Aspects
Submit complaints covering full scam details like website links, social media pages and ad accounts through public agencies like the FTC, BBB and IC3. Such filings help authorities piece together digital footprints stopping these crooks from deceiving others.
Step 4: Demand Reimbursements On All Unauthorized Charges
Contact all financial providers connected to scam transactions insisting they start disputes and chargebacks. Monitor claim statuses closely while providing updated letters continually until receiving favorable judgments before expiration periods pass, usually between 90-120 days.
Carefully following protective measures curtails damages from identity theft pipelines spawned from clearance cons. Staying alert with enhanced scrutiny across financial accounts over the next few months can ease much anxiety as authorities dismantle wider fraud rings.
Frequently Asked Questions
For online shoppers questioning the curious case of too-good-to-be-true On-Running deals promoted on social feeds, this FAQ presents simplified answers surrounding the rampant athletic shoe scam and the cunning tactics used by fraudsters to trick avid runners.
What makes the fraudulent On-Running promotions so deceptive?
Con artists build entire fake ecommerce stores flawlessly impersonating the real website by intricately counterfeiting elements like product catalogs, checkout flows, branding layouts and copyrighted logos to suspend visitor wariness over legitimacy. Targeted advertisements drive traffic by perfectly filtering users revealing shopping habits plus interests in running gear and clearance deals.
How do scammers mimic authentic On-Running branding so convincingly?
Fakers thoroughly reverse engineer and digitally replicate real assets like product photos, lifestyle videos, store interfaces and other intellectual property without legal usage rights. Some even scrape full site data points then reconstruct functional mirrors capable of bypassing coding authenticity checks integrated by genuine platforms.
Why advertise unbelievable discounts up to 90% off?
By promoting intentionally inflated yet still within reason clearance claims directly through advertisements laser targeted toward deal-seeking athlete demographics, scammers spark involuntary impulses to purchase from perceived scarcity that rationally overrides otherwise questionable reductions requiring further scrutiny.
Does merchandise shown in advertisements actually get sold at discounts on scam sites?
Absolutely not. All featured shoes, apparel and gear solely comprise images stolen from authentic brand catalogs merely depicting products. Beyond collecting payments and harvesting data at illicit checkouts, zero legitimate inventory or discounting capabilities exist since the entire presence constitutes a purely scam operation.
What typically happens after submitting data to counterfeit stores?
Most victims only experience payment theft as no goods ship after inputs enter wider criminal data pools. In rare cases, egregiously inferior knockoffs arrive months later, used merchandise gets shipped, or totally random objects send to loosely mimic orders. But overall buyers only face loss from the empty promises.
Can customers get scammed without even placing orders?
Yes. Merely accessing counterfeit sites risks device infections from embedded malware installing through shady redirects. Entering contact info like emails also flags victims for additional spam messages from broader underground fraud collectives seeking more data points.
How do retail cons actually manage to profit without selling any real products?
Direct profits come from stealing payments and sensitive personal finance details submitted at sham checkouts. Greater indirect gains flow from reselling data profile batches on darker web marketplaces frequented by shadier groups seeking detailed lists of shopper preferences and assets to craft targeted social engineering infiltration tactics and additional retail cons.
Who organizes elaborate clearance sale shams against global performance brands?
Highly sophisticated cybercrime teams in fraud hotspots like China specialize by mass counterfeiting entire online shopping ecosystems. By reverse engineering trusted retailers then duplicating at scale, coordinated networks manage to indirectly siphon assets back to ringleaders concealed internationally utilizing personas and money chains avoiding easy connections to crimes.
How long can these brand impersonation outlets operate undetected?
Weeks or months often pass before individual websites and accounts get discovered then blacklisted, often by consumer watchdog groups. However persistent operators proactively rotate site details, register new domains and launch rebuilt scams in recurring cycles while continually testing novel techniques to avoid detections.
Conclusion
In summary, counterfeit On-Running shopping websites promoted via social channels attempt large-scale credit card fraud and identity theft by scamming clearance fever. As global retail progressively shifts towards ecommerce, consumers must urgently learn precise mannerisms and discreet infrastructure empowering these scams to silently thrive in obscurity. But through raised public awareness surrounding cunning techniques fake promotions utilize plus enacting key protective safeguards when deal hunting, customers can help obstruct shameless criminals aiming to solely profit by deceiving families dreaming of attractive discounts.



![Remove Mornaces.com Pop-ups [Virus Removal Guide] 11 McAfee scam 4](https://malwaretips.com/blogs/wp-content/uploads/2023/08/McAfee-scam-4-290x290.jpg)