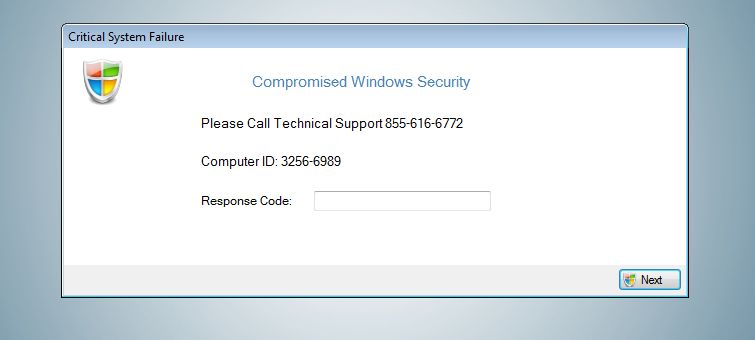
If you are seeing a Compromised Windows Security pop-up, asking you to call a support number, then your computer is infected with a Trojan horse (Rogue.Tech-Support-Scam).
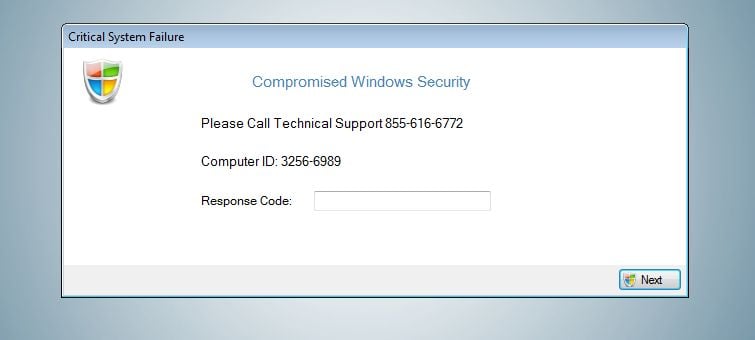
The Compromised Windows Security alert is shown in such a way as to trick the user into thinking their computer has crashed or that a virus has been detected on the computer. It does this to try and scare the infected user into calling one of the listed numbers (855-616-6772) in order to receive support. In reality, though, they will only be greeted with people who are trying to sell them unneeded support contracts and services.
The “Compromised Windows Security” pop-up ads are caused by a malicious program, which is typically bundled with other software that you can download for free from the Internet. When the malicious program is installed, an “Compromised Windows Security” alert will randomly pop-up.
The fake “Compromised Windows Security” pop-up will have this message:
Critical System Failure
Compromised Windows Security
Please Call Technical Support 855-616-6772
Computer ID: 3257-6989
Response Code:
As you can see, this program was created for the sole purpose of displaying fake Windows alerts in order to scare you into purchasing remote support services. If you are infected with this program, please ignore any alerts that are displayed and do not call the displayed number. To remove this Trojan and any related software, please use the removal guide below.
How to remove Compromised Windows Security pop-ups (Removal Guide)
This page is a comprehensive guide which will remove Compromised Windows Security pop-ups from Windows.
Please perform all the steps in the correct order. If you have any questions or doubt at any point, STOP and ask for our assistance.
To remove Compromised Windows Security pop-ups, follow these steps:
STEP 1: Use Rkill to terminate suspicious programs
STEP 2: Scan your computer with AdwCleaner
STEP 3: Scan your computer with Malwarebytes Anti-Malware
STEP 4: Scan your computer with HitmanPro
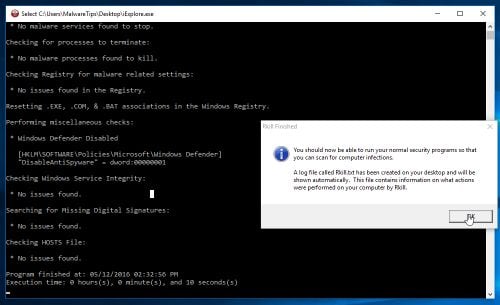
STEP 1: Use Rkill to terminate suspicious programs
RKill is a program that will attempt to terminate all malicious processes associated with this infection, so that we will be able to perform the next step without being interrupted by this malicious software. Because this utility will only stop the malicious process and does not delete any files, after running it you should not reboot your computer.
- You can download Rkill from the below link.
RKILL DOWNLOAD LINK (This link will open a new web page from where you can download “RKill”) - Double-click on Rkill utility to start this program.

- RKill will now start working in the background, please be patient while this utiltiy looks for malicious process and tries to end them.
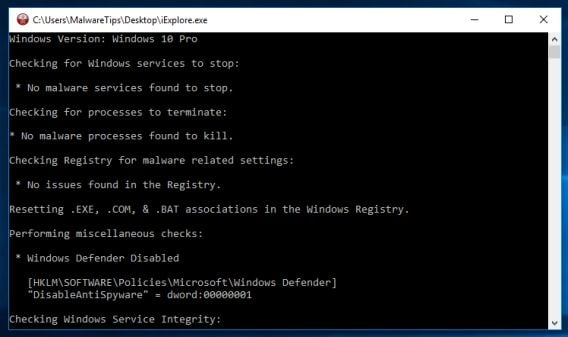
- When the Rkill tool has completed its task, it will generate a log. Do not reboot your computer after running RKill as the malware programs will start again.
STEP 2: Scan your computer with Malwarebytes Anti-Malware
Malwarebytes Anti-Malware is a powerful on-demand scanner which will remove the Compromised Windows Security pop-ups from your machine. It is important to note that Malwarebytes Anti-Malware will run alongside antivirus software without conflicts.
- You can download download Malwarebytes Anti-Malware from the below link.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK (This link will open a new web page from where you can download “Malwarebytes Anti-Malware”) - Once downloaded, close all programs, then double-click on the icon on your desktop named “mbam-setup” to start the installation of Malwarebytes Anti-Malware.

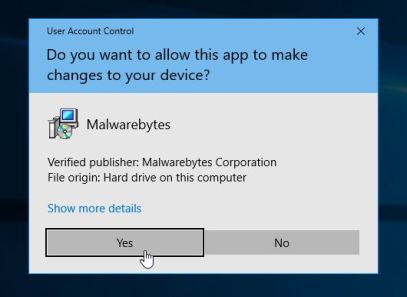
You may be presented with a User Account Control dialog asking you if you want to run this file. If this happens, you should click “Yes” to continue with the installation.
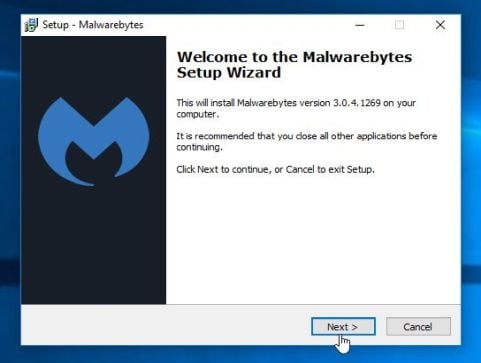
- When the installation begins, you will see the Malwarebytes Anti-Malware Setup Wizard which will guide you through the installation process.
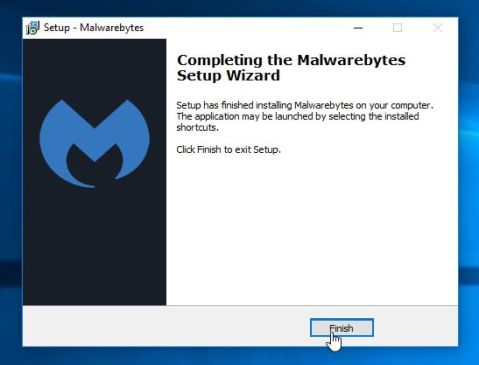
To install Malwarebytes Anti-Malware on your machine, keep following the prompts by clicking the “Next” button.
- Once installed, Malwarebytes Anti-Malware will automatically start and will update the antivirus database. To start a system scan you can click on the “Scan Now” button.
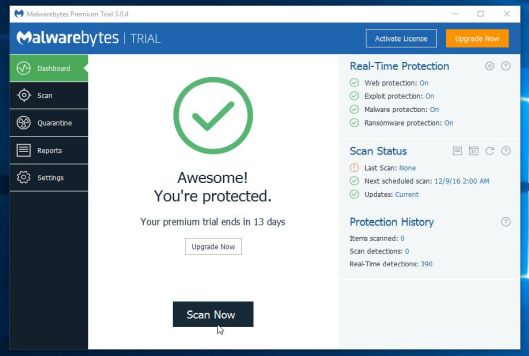
- Malwarebytes Anti-Malware will now start scanning your computer for the Compromised Windows Security malware. When Malwarebytes Anti-Malware is scanning it will look like the image below.
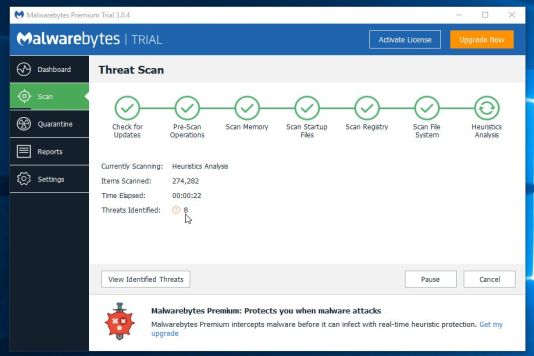
- When the scan has completed, you will be presented with a screen showing the malware infections that Malwarebytes Anti-Malware has detected. To remove the malicious programs that Malwarebytes Anti-malware has found, click on the “Remove Selected” button.
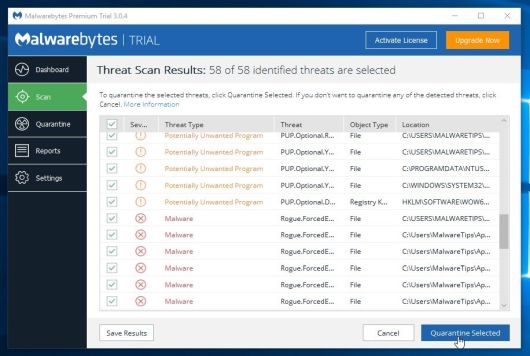
- Malwarebytes Anti-Malware will now quarantine all the malicious files and registry keys that it has found. When removing the files, Malwarebytes Anti-Malware may require a reboot in order to remove some of them. If it displays a message stating that it needs to reboot your computer, please allow it to do so.
STEP 3: Scan your computer with AdwCleaner
AdwCleaner is a free utility, which will scan your computer and web browser for the Compromised Windows Security redirect.
- You can download AdwCleaner from the below link.
ADWCLEANER DOWNLOAD LINK (This link will open a new web page from where you can download “AdwCleaner”) - Before starting AdwCleaner, close your web browser, then double-click on the AdwCleaner icon.

If Windows prompts you as to whether or not you wish to run AdwCleaner, please allow it to run.
- When the AdwCleaner program will open, click on the “Scan” button as shown below.

AdwCleaner will now start to search for the Compromised Windows Security adware and other malicious programs. - To remove the malicious files that were detected in the previous step, please click on the “Clean” button.

- AdwCleaner will prompt you to save any open files or documents, as the program will need to reboot the computer to complete the cleaning process. Please do so, and then click on the “OK” button.

When your computer reboots and you are logged in, AdwCleaner will automatically open a log file that contains the files, registry keys, and programs that were removed from your computer. Please review this log file and then close the notepad window.
STEP 4: Scan your computer with HitmanPro
HitmanPro finds and removes malware, adware, bots, and other threats that even the best antivirus suite can oftentimes miss. It’s designed to run alongside your antivirus suite, firewall, and other security tools.
- You can download HitmanPro from the below link:
HITMANPRO DOWNLOAD LINK (This link will open a new web page from where you can download “HitmanPro”) - Double-click on the file named “HitmanPro.exe” (for 32-bit versions of Windows) or “HitmanPro_x64.exe” (for 64-bit versions of Windows).

Click on the “Next” button, to install HitmanPro on your computer.
- HitmanPro will now begin to scan your computer for malware.
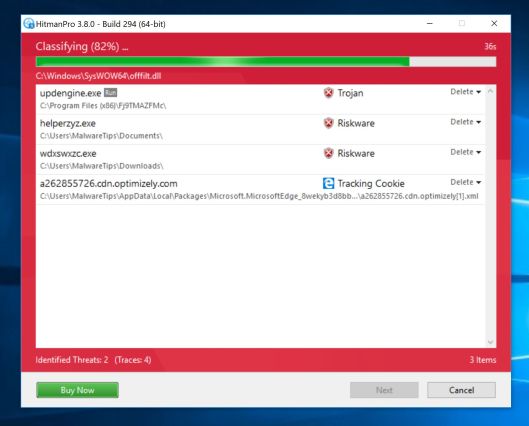
- When it has finished it will display a list of all the malware that the program found as shown in the image below. Click on the “Next” button, to remove malware.

- Click on the “Activate free license” button to begin the free 30 days trial, and remove all the malicious files from your computer.
Your computer should now be free of the Compromised Windows Security pop-ups. You can remove AdwCleaner from your machine, however we recommend that you keep Malwarebytes Anti-Malware and HitmanPro installed and perform regular computer scans.
If you are still experiencing problems while trying to remove Compromised Windows Security redirect from your machine, please start a new thread in our Malware Removal Assistance forum.

![Remove Loapneme.co.in Pop-up Ads [Virus Removal Guide] 4 McAfee scam 4](https://malwaretips.com/blogs/wp-content/uploads/2023/08/McAfee-scam-4-290x290.jpg)