The COVID-19 pandemic prompted the government to issue Economic Impact Payments (stimulus checks) to support citizens facing financial hardships. Now fraudsters exploit this relief aid via an IRS scam offering a fake “Third Round” of stimulus payments. This scam contacts victims via email and text to lure them to fake IRS sites stealing personal and banking information.
It is crucial to recognize signs of this scam and best response steps if compromised. This guide provides a detailed overview of the “Third Round Economic Impact Payments” ruse including how it ensnares victims and actions to minimize damages from surrendered data. Vigilance and awareness represent the best defenses against stimulus check-related frauds still plaguing relief efforts.
Overview of the “Third Round Economic Impact Payments” IRS Scam
This pervasive scam stems from actual pandemic relief programs issued in three rounds by the genuine IRS. The agency distributed Economic Impact Payments (EIPs) based on tax filer eligibility during 2020 and 2021.
Most citizens received accurate first and second round EIPs automatically from the IRS based on prior tax returns. Payments arrived via direct deposit or mailed checks without any additional action needed.
Now devious fraudsters have launched phishing campaigns pretending to issue a nonexistent “third round” of extra stimulus aid targeting struggling tax filers. The scams contact victims via:
- Emails pretending origin from IRS.gov addresses
- Text messages claiming association with IRS phone numbers
- Fake IRS websites mirroring legitimate site formats
These communications reference the victim’s “recent tax return filing” and claim inflated refunds or stimulus payments await issuance after following included links and inputting sensitive personal financial data.
Scam Email Example
A sample email reads:
“IRS
Dear Taxpayer,
After the last annual calculations of your fiscal activity, we have determined that you are eligible to receive a tax return of $976.00. In order for us to process the excess payment, please complete the Tax Return Form before December 5, 2023.”
This includes an embedded link to a fake web domain impersonating an official IRS portal.
Scam Text Example
Similarly deceptive SMS messages state:
“IRS: Our records indicate you qualify for an additional $895 Economic Impact Payment from your 2021 tax return data. Click here to confirm eligibility and add bank account information for direct deposit.”
The fraudulent links then redirect to convincing sham websites stealing entered financial account credentials and personal data.
Scam Website Example
These fake IRS domains feature:
- Official IRS seals/branding
- Realistic web interfaces mimicking IRS.gov
- SSL encryption icons to appear legitimate
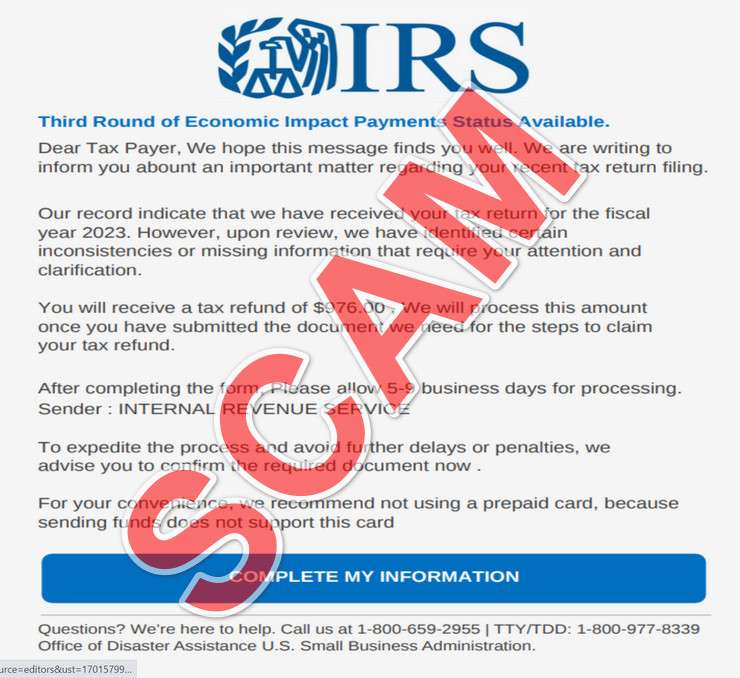
One live scam website currently displays:
“IRS
Third Round of Economic Impact Payments Status Available.
Dear Tax Payer, We hope this message finds you well. We are writing to inform you about an important matter regarding your recent tax return filing. Our records indicate that we have received your tax return for the fiscal inconsistencies or missing information that require your attention and clarification.
You will receive a tax refund of $976.00. We will process this amount once you have submitted the documents we need for the steps to claim your tax refund.
Sender: INTERNAL REVENUE SERVICE.
Get My Payment.”
This site prompts victims to click a “Get My Payment” button initiating requests for private financial data like bank accounts and Social Security Numbers under guises of identity confirmation and facilitating direct deposits.
How the “Third Round Economic Impact Payments” IRS Scam Works
The multi-stage IRS stimulus check scam unfolds as follows:
Stage 1 – Phishing Emails and Texts Go Out
Exploiting stolen taxpayer data (names, addresses, phone numbers) scammers send masses of emails and texts pretending to originate from IRS.gov email accounts and registered IRS phone lines.
These communications use real historical EIP payment data to reference victims’ prior pandemic relief. Messages cite exact dollar figures received from earlier stimulus rounds before claiming additional payments await issuance.
This personalization makes the outreach appear credible and urgent. The texts and emails insist victims must click through to confirm eligibility and bank data to receive pending $500, $700 or $900 payments.
In other variations, scammers reference recent tax return figures or refund amounts expecting rather than stimulus checks specifically. All versions aim to project legitimacy via custom financial details.
Stage 2 – Redirects to Fake IRS Sites
Recipients who click embedded links get redirected to sophisticated fake IRS websites engineered to mirror legitimate IRS.gov interfaces. These fraudulent sites feature:
- Official government seals and IRS branding
- Believable URL names containing “IRS” acronyms
- Valid site encryption certifications and padlock security icons
The fake portals reinforce messaging around unclaimed tax refunds or pending stimulus checks requiring personal information “verification” before release.
Sites display pre-filled victim financial data like names, addresses and last four Social Security digits to instill further credibility that the IRS pre-populated these details from official records.
Stage 3 – Requests for Personal Financial Data
To “validate their identity” and process payments, the counterfeit IRS sites next prompt victims to enter a windfall of sensitive personal and financial information including:
- Full legal name
- Physical address
- Phone numbers
- Email addresses
- Social Security Number
- Bank account and routing numbers
- Credit/debit card numbers
- Driver’s license details
- Images of the license, bank cards or personal checks
Scammers capture all data entered on the fake portals for identity theft, bank account draining and credit card fraud.
Stage 4 – Account Fraud and Data Resale
With all the necessary account access details in hand, scammers quickly steal any available funds from victims’ connected bank/payment accounts. They transfer out balances via online banking withdrawals, mobile payment apps or fraudulent checks.
Swindlers also leverag3 stolen information to open illicit credit cards making unauthorized purchases. Or they sell complete identity records on the dark web fetching up to $1,000 per victim. This allows additional fraud by countless other scammers.
Meanwhile victims remain unaware of the theft until encountering account activity alerts or declined transactions from drained balances. At that point critical data and funds already shifted into criminal hands.
How to Identify the Fake IRS Stimulus Check Scam
As fraudsters exploit confusion around pandemic relief programs, it becomes critical to recognize key indicators of the IRS stimulus check scam. Watch for these signals:
Unsolicited Contacts Out of Nowhere
Legitimate IRS communications get mailed via USPS before deploying phone, email or text contact. Cold messages regarding surprise stimulus aid likely signal scams attempting urgent phishing.
Messages Threatening Loss of Funds
Real IRS documents avoid threatening tones. But scams insist acting immediately necessary to receive (nonexistent) pending aid payments before forfeiture. This pressures recipients to bypass scrutiny and hastily click included links.
Requests for Excessive Personal Data
While the real IRS requires current details like bank routing numbers facilitating direct deposit payments, scammers overtly over-request far more data than needed for verification only.
Watch for demands of scans/photos of private items like Social Security Cards, driver’s licenses or personal checks.
Mismatching Contact Details
Compare sender phone numbers, email addresses and domain names against legitimate published IRS ones. Any deviations signal scammers impersonating identities.
Search “IRS contacts” to reference genuine channels versus scam communications designed to spoof government affiliations.
Poor Spelling and Grammar
Official IRS messages pass extensive quality checks. Rampant typos, awkward phrasing like “Dear Tax Payer” or repeated unusual punctuation all betray scam attempts from non-native fraudsters.
Links Routing Outside .gov Websites
Real IRS portals always utilize .gov domains. But scammers redirect to fake lookalike sites they registered resembling IRS.gov interfaces.
Scrutinize links closely to spot subtle domain typosquatting or dominant usage of non-government extensions.
Catching even minor scam indicators promptly makes recipients less likely to click unsafe links and surrender account credentials or data to swindlers. Report all suspicious correspondence to antiphishing@irs.gov to ensure appropriate federal assessment of new fraud attempts.
What to Do If You Get Scammed by a Fake IRS Portal
If you shared financial or personal data on a website impersonating the IRS, you now face potential identity theft damages. But swift actions can help contain the fallout:
Step 1) Contact Banks and Credit Bureaus
Your first calls must go to all banks, credit card companies and lenders tied to accounts whose information got compromised.
Report fraud to halt usage of impact cards and linked payment apps. Dispute any recent unauthorized charges. For serious suspected identity theft, request replacement numbers associated with new accounts.
Additionally contact Equifax, TransUnion and Experien to institute credit freezes on new lending inquiries until identity verification gets strengthened by your providers. Freezes must get properly lifted once identity restoration finishes.
Step 2) Update Account Passwords and Security
Instantly change passwords and enable enhanced security (two-factor authentication) for associated email accounts and financial accounts online access.
Update account numbers if issued replacements cards. The added login precautions prevent criminals accessing accounts even with stolen password lists now circulating cyberspace.
Step 3) File an IRS Identity Theft Affidavit
Formally document the identity compromise by filing an official IRS Affidavit Form 14039.
Provide key details like:
- Contact information
- Compromised account identifiers
- Description of the scam attempt
- Any related law enforcement departments contacted
Submitting the affidavit flags your accounts and initiates an IRS investigation against the scammers.
Step 4) Monitor Accounts and Credit Reports
Carefully monitor bank statements, investment accounts and credit reports for signs of any additional fraud over the next 12 months.
Unapproved address changes, loans or card applications all signal continuing identity theft issues to address immediately with reporting and added fraud disputes.
Step 5) File a Local Police Report
File formal documentation about the identity compromise, scam incident and cybercrime category details with your local police department or county sheriff’s office. This aids three key imperatives:
- Prosecuting the offenders behind the scam attempt
- Disputing further fraudulent transactions/accounts
- Claiming any eligible insurance/reimbursements for losses
Bring all available scam evidence including emails, fake web screenshots and stolen payment confirmations. The documented case proves invaluable if damages escalate.
Step 6) Report Details to Antiphishing@IRS.gov
The IRS maintains a dedicated inbox allowing citizens to directly report phishing scams impersonating government entities. Details like scam website URLs, email/text origins and content can all contribute intelligence assisting investigations against fraudsters. Any information aids their enforcement initiatives tracking down cyber swindlers.
While falling victim to even sophisticated IRS scams can generate long-lasting account security headaches, fast post-scam mitigation steps minimize ongoing troubles emerging for impacted citizens. Never hesitate to report fake communication details directly to antiphishing@irs.gov as well. Maintaining open fraud information sharing channels with authorities creates the most effective pathway to apprehending prolific scam networks and ultimately reducing consumer dangers.
FAQ: The Fake “IRS Third Round Stimulus” Scam
With fraudsters leveraging confusion around relief programs, many questions surround the prevalent IRS stimulus check scam. These FAQs address the most common concerns.
How do scammers know my personal financial data to launch this scam?
Swindlers purchase stolen identity bundles illegally online containing names, addresses, bank details and past tax data. Others steal records from breached third-parties like tax prep firms or government entities. This data facilitates targeted payment scam attempts.
What are common forms of the IRS stimulus scam contact?
Most contact stems from:
- Emails pretending association with IRS.gov addresses
- Texts claiming to originate from IRS phone lines
- Fake IRS websites built to mimic legitimate portal interfaces
How can I determine real vs scam IRS letter, email or text?
Comparing sender details against published IRS contacts quickly reveals fakes. Search “IRS official email addresses” and “IRS phone numbers” to reference genuine channels.
Typos, grammatical errors and threatening urgent tones also betray scam attempts from non-native fraudsters.
What should I do if I shared bank details or personal info on a fake IRS site?
If compromised, immediately:
- Contact banks and credit bureaus to halt financial fraud
- Reset all account passwords and enable enhanced security
- File an IRS Identity Theft Affidavit (Form 14039)
- Monitor accounts closely for suspicious activities
- Report the scam attempt details to antiphishing@irs.gov
Rapid action contains damages from any surrendered account credentials or data. Formally documenting scam details with the IRS aids investigations in bringing cybercriminals to justice.
How can taxpayers avoid falling for IRS stimulus scams?
Hallmarks of fraudulent IRS stimulus check communications include:
- Unsolicited urgent threats demanding immediate data entry
- Requests to visit unofficial third-party phishing links
- Fake portals demanding uploads of private financial material like bank cards or Social Security cards
- Poor grammar/spelling throughout scam emails
Understanding these signals allows citizens to reliably detect and halt emerging stimulus check fraud attempts. Report all fake outreach attempts directly to antiphishing@irs.gov.
The Bottom Line on the IRS “Third Economic Impact Payment” Scam
This pervasive scam highlights pronounced vulnerabilities taxpayers face by failing to scrutinize unsolicited IRS payment communications. Fortunately awareness of common scam indicators coupled with caution surrounding any IRS outreach provides the most reliable defense.
Hallmarks of the fraudulent IRS stimulus check scam involve:
- Unsolicited emails/texts referencing tax history specifics
- Urgent threats of forfeiting funds if immediate action gets avoided
- Suspicious links routing to non-government web domains
- Fake portals requesting personal data upload
No legitimate IRS portal would demand uploading scans of private cards or licenses. Nor do refunds/stimulus checks hinge on following third-party website links requiring extensive personal data to unlock.
When in doubt, taxpayers should manually access IRS.gov to check individual payment statuses or call published IRS phone numbers to speak with representatives regarding any qualifying additional tax relief or stimulus eligibility.
Total avoidance of deception relies on recalling that vital government agencies would never threaten legal repercussions around aid eligibility. Nor would they operate domains outside of .gov and .us government website channels. As long as citizens remain thoughtful when scrutinizing unexpected financial outreach, the risk of surrendering hard-earned funds or personal data to scammers reduces significantly.










